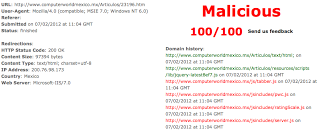
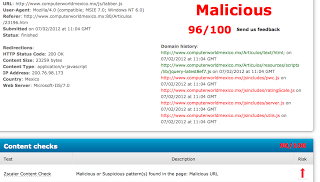
We were alerted to this from a customer reporting that Zscaler was blocking pages on www.computerworldmexico.mx
And as evidence of this, was our Zulu report - which when we looked at it showed that the page itself did not have any malicious content / reason
But the site's own internal JS files were being flagged as malicious, e.g., tabber.js as a result of Zscaler's threat fingerprinting.
Looking at the JS files, there was the addition of obfuscated JS at the end of the flagged files:
The JS makes use of the DOM to avoid automated deobfuscation, e.g., JSUnpack failed for me. Deobfuscating, shows a number of things
- For one, the author of the malware used Windows (you can see the carriage-return newlines as ctrl-v ctrl-M in my vi editor)
- The malicious JS utilizes the setTimeout function, so that the malicious injection only occurs after being on the page for 500 miiliseconds - which can help evade rapid, automated analysis of pages
- The malicious JS injects an IFrame using a domain generation algorithm (DGA) based on time (changes about every 40,000 milliseconds or so)
Looping through the DGA, these are some of the domains:
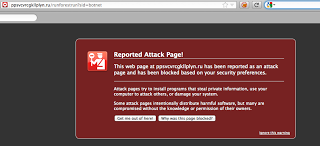
ppsvcvrcgkllplyn.ru
ruhctasjmpqbyvhm.ru
bdvkpbuldslsapeb.ru
eilqnjkoytyjuchn.ru
npxsiiwpxqqiihmo.ru
qtmyeslmsoxkjbku.ru
adbjjkquyyhyqknf.ru
ciqmhuwgvfsxdtrw.ru
mocrafrewsdjztbj.ru
otruvbidvikzhlop.ru
yafzvancybuwmnno.ru
yafzvancybuwmnno.ru
bhujzorkulhkpwob.ru
lohnrnnpvvtxedfl.ru
ntvrnrdpyoadopbo.ru
wakvnkyzkyietkdr.ru
zfyafrjmmajqfvbh.ru
jnlkttkruqsdjqlx.ru
lsbppxhgckolsnap.ru
vznrahwzgntmfcqk.ru
xeeypppxswpquvrf.ru
inqgvoeohpcsfxmn.ru
ksgmckchdppqeicu.ru
uyrorwlibbjeasoq.ru
uyrorwlibbjeasoq.ru
wejungvnykczyjam.ru
Many of the pages are already blocked by Google SafeBrowsing:
Looks like this is all tied to an on-going campaign from mid/late June (e.g., Pastebin paste with some of the domains on June 21) and an earlier blogpost suggesting that these compromises came from the Plesk File Manager.