/ Was versteht man unter Secure Access Service Edge (SASE)?
Was versteht man unter Secure Access Service Edge (SASE)?
Was versteht man unter SASE?
SASE steht für SecureAccessServiceEdge, eine Kategorie, die erstmals 2019 im Gartner-Bericht „The Future of Network Security is in the Cloud“ eingeführt wurde und WAN mit Netzwerksicherheit kombiniert. So profitieren Unternehmen u. a. von mehr Agilität, besserer und zuverlässigerer Netzwerkleistung sowie mehr Transparenz und Kontrolle in heterogenen IT-Umgebungen.
Im Unterschied zu SASE bezeichnet der ebenfalls von Gartner geprägte Begriff der Security Service Edge (SSE) diejenigen Funktionen einer SASE-Cloud-Plattform, die sich unmittelbar auf die Bereitstellung der Sicherheit beziehen.
Wie funktioniert SASE?
Eine SASE-Architektur kombiniert ein softwaredefiniertes Wide Area Network (SD-WAN) oder ein anderes WAN mit verschiedenen Sicherheitsfunktionen (u. a. Cloud Access Security Broker oder Malware-Abwehr) zum Schutz Ihres gesamten Netzwerk-Traffics.
Ältere Prüf- und Verifizierungsverfahren wie die Weiterleitung des Datenverkehrs über einen MPLS-Dienst (Multiprotocol Label Switching) an Firewalls in Ihrem Rechenzentrum sind nur dann effektiv, wenn sich auch Ihre User am gleichen Standort befinden.Diese Methode, den Traffic von Remote-Usern zur Überprüfung ans Rechenzentrum weiterzuleiten und dann wieder zurückzuschicken, wird auch als „Hairpinning“ bezeichnet. Mittlerweile befinden sich jedoch so viele User im Homeoffice bzw. an anderen Remote-Standorten, dass dieses Verfahren sowohl der Produktivität als auch der User Experience abträglich ist.
SASE unterscheidet sich von Einzellösungen und anderen Verfahren der Netzwerksicherheit insofern, als es gleichermaßen sicher wie direkt ist. Anstatt sich auf die Sicherheit des Rechenzentrums zu verlassen, wird der Datenverkehr der Anwendergeräte hier an einem nahegelegenen Point of Presence (POP) überprüft und von dort aus an sein Ziel weitergeleitet. Das ermöglicht einen effizienteren Anwendungs- und Datenzugriff und ist somit die deutlich bessere Alternative für den Schutz dezentraler Belegschaften und Clouddaten.
Ist SASE nur ein Buzzword?
Das SASE-Framework erregte einiges Aufsehen bei Serviceanbietern und Fachmedien. Am überzeugendsten ist allerdings der Grundgedanke, der hinter dem Hype steckt – nämlich die Erkenntnis, dass Sicherheits- und Netzwerkarchitekturen, die in Rechenzentren verankert sind, in der heutigen Zeit nicht mehr ausreichen. Diese Aussage ist nicht einfach ein Werbespruch, sondern eine Einsicht, die sich in der Branche weitgehend unumstritten durchgesetzt hat.
Worin liegt also der konkrete Mehrwert einer SASE-Lösung gegenüber herkömmlicher unternehmensfähiger Netzwerksicherheit, bei der Zweigstellen durch private Netzwerke verbunden werden und Traffic über Secure Web Gateways und Firewalls geroutet wird?
Gartner merkt an, dass herkömmliche Modelle, bei denen Netzwerkverbindungen und Sicherheitsrichtlinien zentral über das Rechenzentrum verwaltet werden, längst nicht mehr zeitgemäß sind. Stattdessen müsse der Fokus auf Useridentitäten und Geräten liegen. „In einem heutigen Cloud-zentrierten digitalen Unternehmen sind User, Geräte und die Anwendungen, auf die sie sicher zugreifen müssen, überall verteilt“, heißt es in dem Bericht.
Workflows, Traffic-Muster und Anwendungsfälle sind heute ganz anders als zu der Zeit, als Hub-and-Spoke-Netzwerke konzipiert wurden. Das hat folgende Gründe:
- Heutzutage läuft mehr Benutzer-Traffic in Cloud-Dienste als in Rechenzentren
- Mehr Arbeit wird außerhalb als innerhalb des Netzwerks verrichtet
- Mittlerweile werden mehr Workloads in Clouds als in Rechenzentren ausgeführt.
- Es werden mehr SaaS-Anwendungen als lokal gehostete verwendet
- In Cloud-Diensten werden mehr sensible Daten als im Unternehmensnetzwerk gespeichert
Komponenten des SASE-Modells
SASE setzt sich aus sechs wesentlichen funktionalen bzw. technologischen Elementen zusammen:
1. Softwaredefiniertes Wide Area Network (SD-WAN)
Bei SD-WAN handelt es sich um eine Overlay-Architektur, die die Komplexität verringert und die User Experience optimiert. Dazu wird für den Datenverkehr immer die beste Route ins Internet, zu cloudbasierten Anwendungen bzw. zum Rechenzentrum ausgewählt. Dadurch wird ebenfalls die Bereitstellung neuer Apps und Services sowie die standortübergreifende Richtlinienverwaltung erleichtert.
2. Secure Web Gateway (SWG)
SWGs verhindern, dass Traffic ungeprüft aus dem Internet ins interne Unternehmensnetzwerk gelangt. Dadurch schützen Sie Ihre Mitarbeiter und User vor dem Zugriff auf bzw. Infektionen durch schädlichen Web-Traffic, Websites mit Sicherheitslücken, über das Internet übertragene Viren, Malware und Cyberbedrohungen.
3. Cloud Access Security Broker (CASB)
CASBs gewährleisten die sichere Nutzung Cloud-basierter Anwendungen und Services, um Datenlecks, Malware-Infektionen, Verstöße gegen aufsichtsrechtliche Vorschriften und mangelnde Transparenz zu verhindern. Sie schützen Anwendungen, die in privaten oder öffentlichen Clouds (IaaS) gehostet oder auch als Software-as-a-Service (SaaS) bereitgestellt werden.
4. Firewall as a Service (FWaaS)
FWaaS ermöglicht den Umstieg von physischen Firewall-Appliances auf Cloud-Firewalls, die erweiterte L7/NGFW-Funktionen (Level 7/Next-Generation Firewall) bereitstellen können. Dazu zählen URL-Filterung und andere Zugriffskontrollen, Schutz vor komplexen Bedrohungen, Eindringschutzsysteme und DNS-Sicherheit.
5. Zero Trust Network Access (ZTNA)
ZTNA-Lösungen ermöglichen Remote-Usern sicheren Zugriff auf interne Apps. Im Zero-Trust-Modell wird keine Entität automatisch als vertrauenswürdig eingestuft. Basierend auf granularen Richtlinien werden Zugriffsberechtigungen immer nach dem Prinzip der minimalen Rechtevergabe gewährt. Remote-User profitieren so von sicheren Verbindungen zu privaten Anwendungen, ohne Zugang zum Netzwerk zu erhalten. Umgekehrt werden Anwendungen niemals im Internet exponiert
6. Zentrale Verwaltung
Durch die Verwaltung des gesamten Funktionsumfangs über eine einzige Konsole können viele Herausforderungen rund um Änderungskontrolle, Patch-Management, Koordinierung von Ausfallzeiten und Richtlinienverwaltung vermieden werden. Richtlinien lassen sich unternehmensweit unabhängig vom Standort der User konsistent durchsetzen.
3 Vorteile von SASE
Wie können Unternehmen in der heutigen Zeit Zugriffskontrollen und Sicherheitsrichtlinien durchsetzen? Eine herkömmliche On-Premise-Netzwerkinfrastruktur ist den aktuellen Herausforderungen nicht gewachsen. Stattdessen empfiehlt sich der Umstieg auf eine Cloud-basierte SASE-Plattform, die WAN-Funktionen (SD-WAN) mit umfassenden Sicherheitsservices kombiniert. Das SASE-Modell bietet erhebliche Vorteile für Unternehmen, die im Rahmen der digitalen Transformation von der Mobilität und den neuen Möglichkeiten von Cloud-Services profitieren möchten.
1. Reduzierte Kosten und Komplexität der IT
Organisationen wollen sicheren Zugriff auf Cloud-Dienste ermöglichen, Remote-User und -Geräte schützen und Sicherheitslücken schließen. Zu diesem Zweck nutzen sie zahlreiche Sicherheitslösungen, die einen erheblichen Kosten- und Verwaltungsaufwand verursachen. Zudem ist dieses Modell der lokalen Netzwerksicherheit in der digitalen Welt schlichtweg ineffektiv.
Anstatt ein neues Problem mit einem veralteten Konzept lösen zu wollen, stellt SASE das Sicherheitsmodell einfach auf den Kopf. Statt wie früher den Netzwerkperimeter abzusichern, gewährleistet SASE standortunabhängig den Schutz von Usern und anderen Entitäten. SASE basiert auf dem Konzept des Edgecomputing, also der Verarbeitung von Daten in möglichst großer Nähe zu den Personen und Systemen, die sie benötigen. Entsprechend werden Sicherheits- und Zugriffslösungen nahe am User bereitgestellt. Verbindungen zu Anwendungen und Services werden anhand der unternehmensspezifischen Sicherheitsrichtlinien dynamisch zugelassen oder abgelehnt.
2. Schnelle, nahtlose Anwendererfahrung
Solange die User im Netzwerk angemeldet waren und die IT für die Verwaltung von Anwendungen und Infrastruktur verantwortlich zeichnete, waren Anwendererfahrungen einfach kontrollier- und berechenbar. Heutzutage arbeiten Unternehmen zwar zunehmend mit distribuierten Multicloud-Umgebungen, verbinden User jedoch zur Gewährleistung der Sicherheit weiterhin über VPNs mit dem Netzwerk. VPNs beeinträchtigen nicht nur die User Experience, sondern exponieren auch IP-Adressen im Internet. Dadurch vergrößert sich die Angriffsfläche des Unternehmens.
SASE bewirkt genau das Gegenteil, nämlich eine Optimierung der Anwendererfahrung. Gemäß diesem Modell werden Sicherheitsrichtlinien möglichst nahe an der Entität durchgesetzt, die abgesichert werden soll. Statt den User-Traffic zur Sicherheitslösung weiterzuleiten, wird die Sicherheitslösung also in User-Nähe bereitgestellt. SASE ist auf den Schutz von Cloud-Umgebungen ausgelegt. Unternehmen profitieren insbesondere von der intelligenten Verwaltung von Verbindungen an Internetknoten in Echtzeit sowie der Optimierung latenzarmer Direktverbindungen zu Cloud-basierten Anwendungen und Services.
3. Weniger Risiko
Als Cloud-native Lösung ist SASE eigens darauf ausgelegt, Unternehmen bei der Bewältigung der spezifischen Risiken zu unterstützen, die sich aus der neuen Realität geografisch verteilter User und dezentral bereitgestellter Anwendungen ergeben. Sicherheit – insbesondere Schutz vor Bedrohungen und Data Loss Prevention (DLP) – wird nun als Kernkomponente des Konnektivitätsmodells definiert. Dadurch lässt sich gewährleisten, dass alle Verbindungen überprüft und abgesichert werden – und zwar unabhängig von Standort, Anwendung und Verschlüsselung.
Als Schlüsselkomponente des SASE-Frameworks gewährleistet Zero Trust Network Access (ZTNA) sicheren Anwendungszugriff für mobile User, Remote-Mitarbeiter und Zweigstellen und eliminiert sowohl die externe Angriffsfläche als auch das Risiko lateraler Bewegungen im Netzwerk.
Warum ist SASE erforderlich?
Im Zuge der digitalen Transformation sind mehr Agilität und Skalierbarkeit, reduzierte Komplexität und optimierte Sicherheit unverzichtbar geworden. Darüber hinaus müssen moderne Unternehmen eine erstklassige Anwendererfahrung gewährleisten – unabhängig davon, wo sich die User befinden.
Aus den folgenden vier Gründen ist SASE mittlerweile nicht mehr nur eine praktische Ergänzung, sondern ein absolutes Must-have:
- SASE passt sich Unternehmen an: Wenn ein Unternehmen wächst, müssen das Netzwerk und die Sicherheitsmaßnahmen in der Lage sein, die daraus resultierende steigende Nachfrage und wachsende Ansprüche zu bewältigen. Dank des Cloud-basierten Modells von SASE entsprechen Netzwerk und Sicherheitsmaßnahmen automatisch den aktuellen Unternehmensanforderungen.
- SASE ist ideal für standortunabhängiges Arbeiten geeignet: Ältere Hub-and-Spoke-Architekturen können Remote-Mitarbeitern nicht die Bandbreite bieten, die sie benötigen, um flexibel und produktiv zu sein. SASE hingegen ist dafür optimal geeignet und gewährleistet darüber hinaus, dass für alle User und Geräte an allen Standorten dieselben Sicherheitsmaßnahmen bereitgestellt werden wie in der Unternehmenszentrale.
- SASE wehrt auch die neuesten Cyberbedrohungen ab: Sicherheitsteams sind ununterbrochen in Alarmbereitschaft und schützen Unternehmen vor sich ständig weiterentwickelnden Bedrohungen. Durch die herausragende Sicherheit und einfache Verwaltung von SASE sind diese Teams in der Lage, komplexe Bedrohungen abzuwehren – egal, wo diese auftreten.
- SASE als Grundlage für die IoT-Einführung: Das Internet der Dinge ist für Unternehmen auf der ganzen Welt von unschätzbarem Nutzen. Um jedoch IoT-Technologien und -Funktionen effektiv einsetzen zu können, ist eine solide Plattform erforderlich, auf der ein IoT-Ökosystem aufgebaut werden kann. Mit SASE können Unternehmen ihre IoT-Ziele mit beispielloser Konnektivität und Sicherheit erreichen.
All dies hat Anbieter von Networking- und Sicherheitslösungen dazu veranlasst, eigene Versionen einer SASE-Architektur zu entwerfen. Viele dieser Anbieter behaupten, ihr Produkt sei Cloud-basiert, doch tatsächlich handelt es sich meist nur um eine Cloud-Plattform, die auf Legacy-Hardware aufsetzt.
Lediglich ein Anbieter ist in der Lage ein wirklich Cloud-basiertes SASE-Modell bereitstellen. Woran liegt das? Wir haben unsere Plattform in der Cloud und für die Cloud entwickelt.
Zscaler SASE
Die Zscaler Zero Trust Exchange™ ist unsere SASE-Lösung und bietet ein schnelles, flexibles, einfaches und sicheres Modell für die Verbindung von Usern und Geräten. Als automatischer, in der Cloud bereitgestellter Service lässt sich unsere global verteilte Plattform einfach implementieren und verwalten. User werden immer auf dem kürzesten Pfad mit den benötigten Anwendungen verbunden.
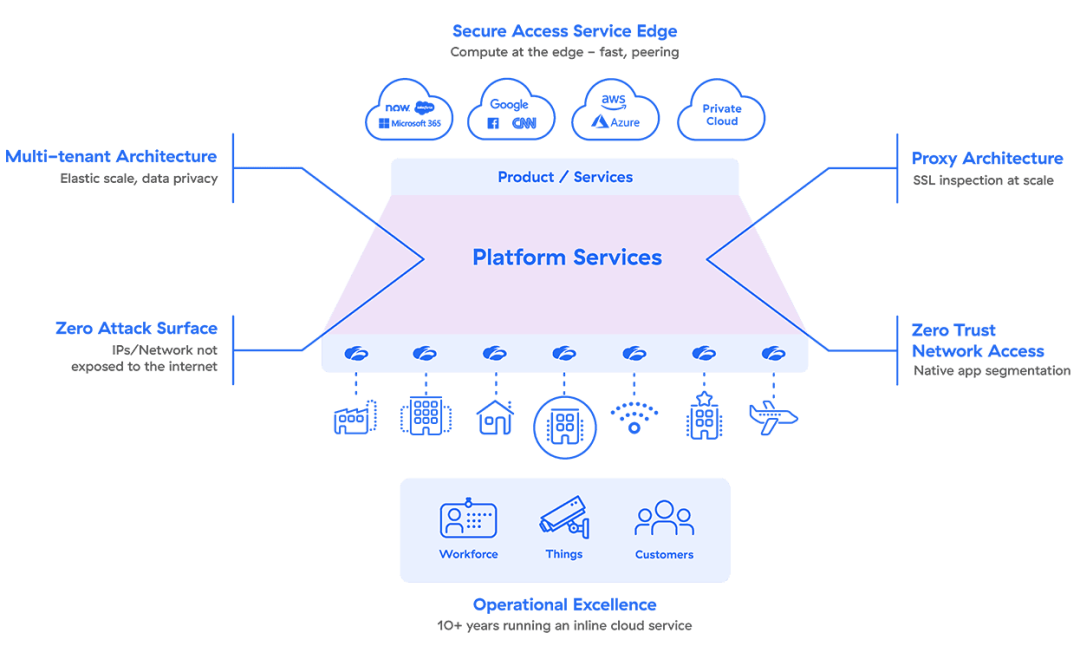
Alleinstellungsmerkmale der SASE-Lösung von Zscaler:
- Eine native, mehrinstanzenfähige Cloud-Architektur, die sich bei Bedarf dynamisch skalieren lässt
- Proxy-basierte Architektur für vollständige Überprüfung von verschlüsseltem Traffic in großem Maßstab
- Verlagerung von Sicherheit und Richtlinien in die Nähe des Users zur Vermeidung von unnötigem Backhauling
- Zero Trust Network Access (ZTNA) mit Zugriffsbeschränkungen und nativer Anwendungssegmentierung
- Keinerlei Angriffsfläche, wodurch gezielte Angriffe verhindert werden, da Quellnetzwerke und Identitäten nicht im Internet offengelegt sind
Durch Peering mit Hunderten von Partnern in großen Internetknoten weltweit bietet die Zero Trust Exchange optimale Performance und Zuverlässigkeit.



