In fast-evolving distributed digital environments, staying ahead of the curve is no longer an option: it’s a necessity. With cyberthreats and attack vectors multiplying every day, businesses must understand and minimize their external attack surfaces. Enter external attack surface management (EASM)—a formidable tool against cyberthreats.
EASM is a proactive approach to security—get ahead, stay ahead
Whatever the type of security incident, the first step is always about discovery. Threat actors are always looking for ways and means to infiltrate and steal information, and it starts with knowing where the weak links are.
Sometimes, especially in the midst of digital transformation, unknown asset sprawl makes it challenging for large, complex organizations themselves to understand where their vulnerabilities might be. In the past, we’ve offered customers our internet attack surface report—a comprehensive, point-in-time assessment that helps them see where their apps are distributed and better understand their exposed domain names, IPs, public cloud footprint, and more.
Now, we’re excited to bring these capabilities as a standalone, web-based, automated external attack surface analysis tool to help customers not only understand their exposure to internet-facing threats in near-real time and trends over time, but also assess the severity of their vulnerabilities and continuously map them directly to their application assets and servers.
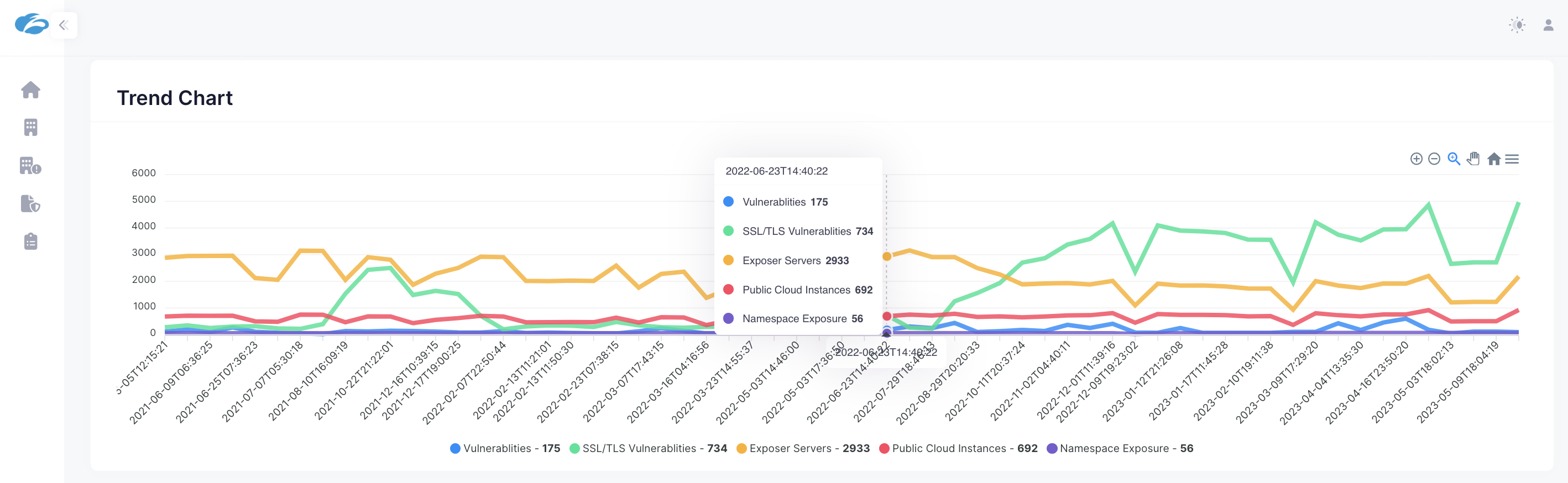
Trend chart of vulnerabilities to external threats as shown by Zscaler’s External Attack Surface Management Tool
The larger your attack surface, the greater your risk
Digital expansion can increase your external attack surface, and with it, your vulnerability to cyberthreats. This includes but is not limited to shadow IT, public cloud web apps, increased usage of open source code, unsecured servers running RDP/VNC/SSH/Telnet/SNMP, IoT systems with legacy services, TLS/SSL misconfigurations, and vulnerable remote access systems like VPNs. Traditional security tools often fall short in identifying these weak points across today’s vast, complex digital environments.
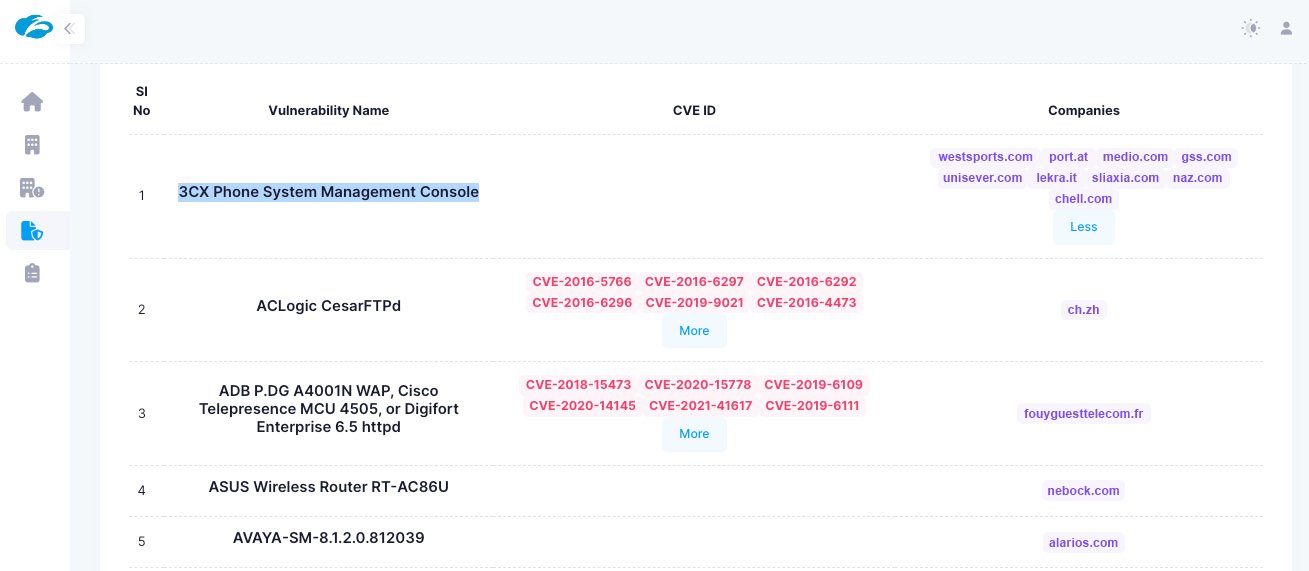
Combining the broad Open Source Intelligence (OSINT) provided by Zscaler EASM with deep threat intel from Zscaler ThreatLabz, vulnerabilities can be found before they’re even disclosed as CVEs in NIST’s National Vulnerability Database (NVD). Leveraging the world's largest inline security cloud, the Zscaler Zero Trust Exchange can identify and fingerprint emerging threats in a small subset of customers and extend protection to all customers. As a real-world example of this “cloud effect,” when Zscaler identified a weakness in the 3CX phone system, we scanned customers the same day to determine if they had internet-facing systems susceptible to this exploit—all before it was assigned a CVE by MITRE.
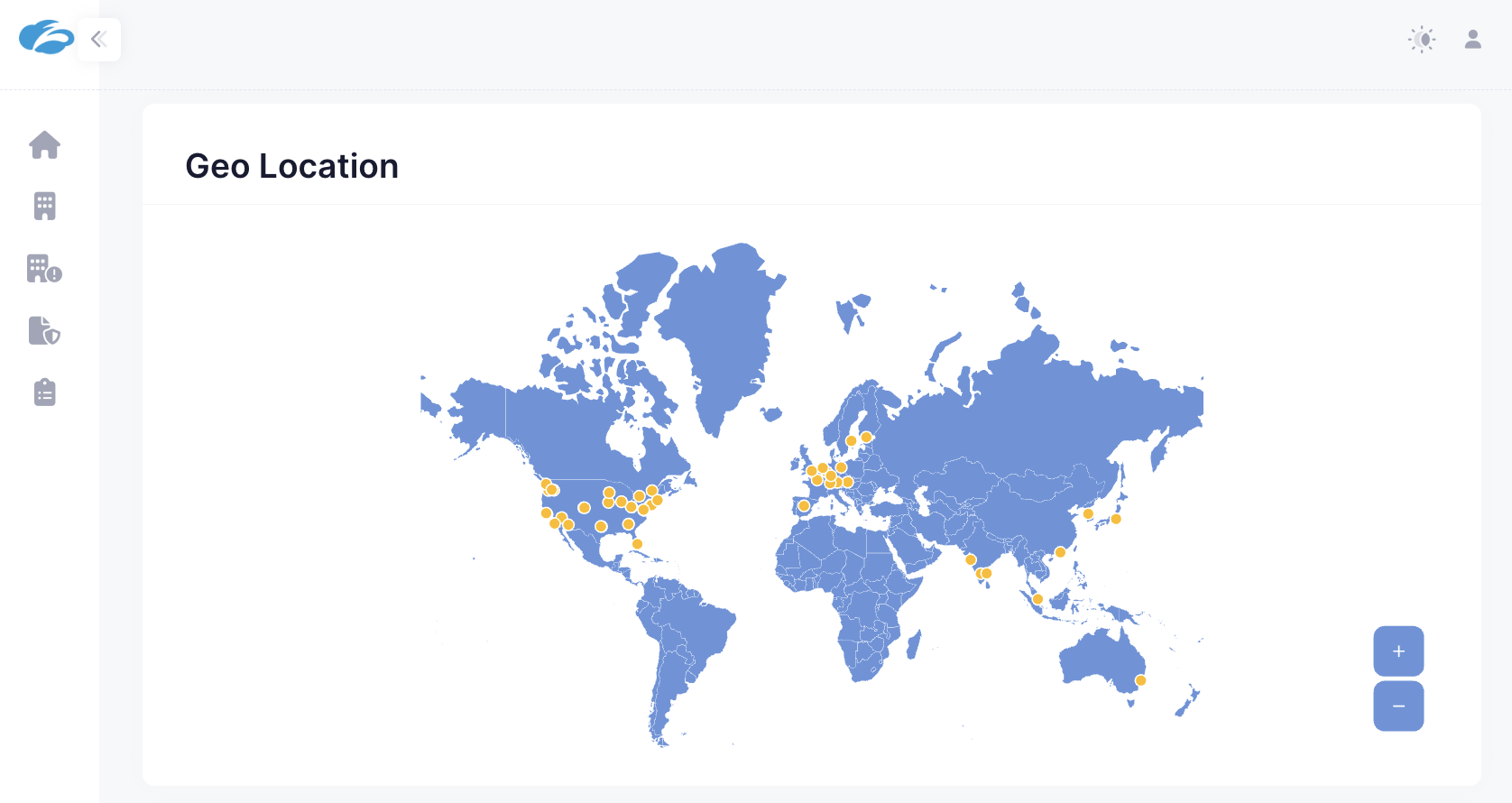
Visualize exposure across your attack surface
The Zscaler EASM web portal displays your organization’s attack surface in an intuitive dashboard, enabling you to quickly access key information such as assets by geographical location.
Why is EASM gaining momentum now?
The NIST CSF published in 2014 identified the need to discover unknown assets as a critical first action, but need didn’t immediately translate to demand. So why is EASM getting attention now?
- Tools by various category names have been in use for digital footprinting over the last 5+ years
- Port and vulnerability scanners, OSINT search engines (e.g., Shodan)
- ASM coalesced over the last 3 years, with EASM emerging as a subcategory in 2021
- Recent advancements in asset discovery prioritization have helped create actionable findings
- Forrester reports that, on average, organizations find 30% more assets than they expected when using EASM tools
- EASM is now an established market—Gartner named attack surface expansion the #1 trend in their Top Security and Risk Management Trends for 2022
Ultimately, EASM is evolving into a capability that will be absorbed into larger security platforms, such as the Zscaler Zero Trust Exchange, to enable integrated actions such as holistic risk quantification, threat hunting, and remediation
Why are Zscaler and EASM better together?
Exposure remediation: The straightforward answer to protecting discovered assets is to make them invisible externally. After all, if they can’t be seen, they can’t be attacked. For years, Zscaler has been helping customers achieve this with an elegant solution called Zscaler Private Access (ZPA) for seamless and secure access to sensitive apps. Pairing EASM findings with ZPA is an effective tactic for securing OS and applications even when they cannot be patched due to numerous factors, such as being EOL, fragile to change, or having uptime requirements.
Zero trust project hygiene: A critical phase of zero trust network access (ZTNA) projects is to validate that legacy systems (e.g., VPN concentrators) are retired post ZTNA adoption. EASM provides a continuous view of the internet-facing landscape to ensure that these assets are decommissioned to minimize the attack surface, realizing the full benefits of zero trust.
Broad risk management: EASM acts as a feeder to the multifaceted Zscaler Risk360, where signals from across all threat origins (internal/external surfaces, inline traffic, out-of-band APIs, and more) are aggregated in a single view, together with guided investigative workflows and prioritized actions to prevent likely breaches.
Competitive advantage: Armed with insights from your EASM, you can stay ahead of evolving threats and assure your clients about the safety of their data. Additionally, this is a potent tool for automating a portion of the footwork for performing due diligence as part of M&A.
Take your security strategy to the next level with EASM
Understand your external attack surface like never before, and take control of your digital footprint. Our team is ready to help you get started.
Zscaler EASM is offered today with limited availability and is expected to become generally available soon. Until then, please request your EASM report through your Zscaler account team.




