A sandbox is a valuable tool in the ongoing battle against cybercriminals and bad actors are continually looking for ways to avoid detection. One of the newest ones we observed, Taurus, includes techniques to evade sandbox detection. Was this new malware able to go undetected by the Zscaler Cloud Sandbox? (Spoiler alert: It wasn't.)
Let's take a closer look at the Taurus stealer.
In early June 2020, we observed and began tracking a new malware campaign. During our research, we observed that the "Predator the Thief" cybercriminal group is behind the development of this stealer, named Taurus, and is selling it on dark forums for $100 or rebuilt with a new domain for $20.
The group selling Taurus claims that this stealer is capable of stealing passwords, cookies, and autofill forms along with the history of Chromium- and Gecko-based browsers. Taurus can also steal some popular cryptocurrency wallets, commonly used FTP clients credentials, and email clients credentials. This stealer also collects information, such as installed software and system configuration, and sends that information back to the attacker. Taurus is designed to not execute in countries within the Commonwealth of Independent States (CIS), which includes Azerbaijan, Armenia, Belarus, Georgia, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan, and Ukraine. (Turkmenistan and Ukraine are both unofficial members of the organization. Georgia was a member of the CIS but left the group in 2008.)
Infection cycle
_0.png)
Figure 1: Infection cycle of the Taurus campaign
Distribution method
While tracking the campaign, we noticed that attackers initiated this campaign by sending a spam mail to the victim containing a malicious attachment. Below are the details of the spam mail we observed:
From: "[email protected]"
Received: from daqrey.site (unknown [91.191.184.35])
Date: Fri, 5 Jun 2020 16:56:35
Subject: Penalty Charge Notice
Attachment: pay-violation1011066.doc
The attachment (pay-violation1011066.doc) contained malicious macro code to download further payloads.
Figure 2: The attached malicious doc asks users to enable a macro.
Installation
Once the document is opened, it prompts the user to enables the macro. Once the content is enabled, an AutoOpen() subroutine is called, which will run the malicious Visual Basic for Applications (VBA) macro wherein a PowerShell script is executed via BitsTransfer, downloads three different files of the Taurus Project from the Github site, then saves them in a Temp folder with predefined names.
Figure 3: The obfuscated VBA macro code
The macro contains the URL of the payload as a combination of the following obfuscations: Base64 encoded and reversed string.
Upon decrypting the obfuscated macro code, we see the PowerShell script, as shown in Figure 4.
Figure 4: The decrypted PowerShell script used to download the payload.
Further, these three files get downloaded from Github and dropped in the %Temp% directory. The three files are:
1. GeTNht.com → saved with the name “j2tyq.com” → Legitimate AutoIt3.exe
2. bAMI.com → saved with the name “st6zh” → Base64-encoded AutoIt script having certificate header
3. wsNcf.com → saved with the name “wsNcf.com” → Taurus Stealer
Here, PowerShell is using the Certutil.exe command to decode the payload and execute it on the victim's machine.
The Twitter handle @3xp0rt, which exposes documents from a Russian hacking forum, shows some of the claims of the Taurus project.
Figure 5: The Taurus project claims to have the stealing ability of malware.
The author claims that Taurus has the following stealing capabilities:
- Stealing cookies, Auto-form details, browsing history, and credit card information from Chromium- and Gecko-based browsers.
- Cookies and passwords from Microsoft Edge browsers.
- Credential stealing of some cryptocurrency wallets, including Electrum, MultiBit, Ethereum, Jaxx Liberty, Bytecoin, Atomic, and Exodus
- Stealing credential of FTP clients, including FileZilla, WinFTP, and WinSCP
- Stealing session files from applications, including Discord, Steam, Telegram, and Authy
- Stealing account information of the Battle.Net service
- Stealing Skype history
- Stealing credentials from NordVPN
- Stealing credentials from Pidgin, Psi+, and Psi
- Stealing credentials from Foxmail and Outlook
- Collects system information, such as system configuration and list of installed software.
Figure 6: The Taurus login panel.
The Taurus project has also built a dashboard where the attacker can keep an eye on the infection counts according to geolocations.
Figure 7: The Taurus dashboard to see infection count according to geolocation.
This dashboard also provides the attacker with the ability to customize the configuration of Taurus.
Figure 8: The attacker can update the configuration of Taurus in the dashboard.
Technical analysis of the payload
Once PowerShell downloads the three different files from the GitHub repository, it uses the utility “Certutil.exe” to decode the payload. Out of three downloaded files, the first one is an AutoIT interpreter that is used to run the decoded AutoIT script. Then, Certutil.exe decrypts the second file, which is a Base64-encoded AutoIT file having a certificate as a header. This AutoIT file will decrypt the third file, which is the Taurus Stealer.
After deobfuscating the AutoIT script, we noticed that it has multiple anti-sandbox techniques. It checks for the Sleep patch in the sandbox using the GetTickCount function.
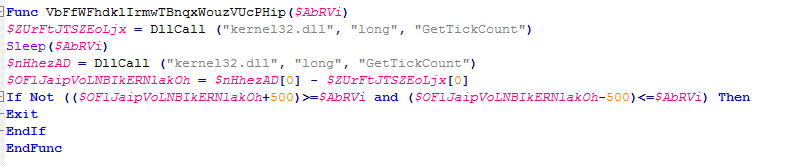
Figure 9: The anti-sandbox patch with the GetTickCount API.
It also checks for the existence of specific files, the computer name, and internet connectivity using the Ping function.
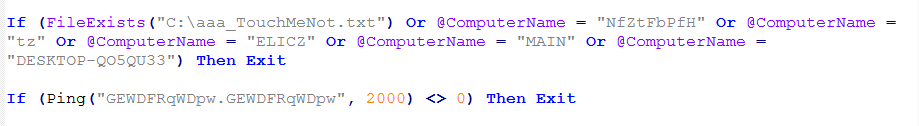
Figure 10: Taurus performs multiple checks for files, the computer name, and internet connectivity.
Finally, the AutoIT script reads and decodes the wsNcf.com file, then loads the deobfuscated shellcode for injecting the decoded payload into dllhost.exe.
Figure 11: Building a path for dllhost.exe.
Figure 12 shows details of the deobsfucated shellcode, which will inject the payload.
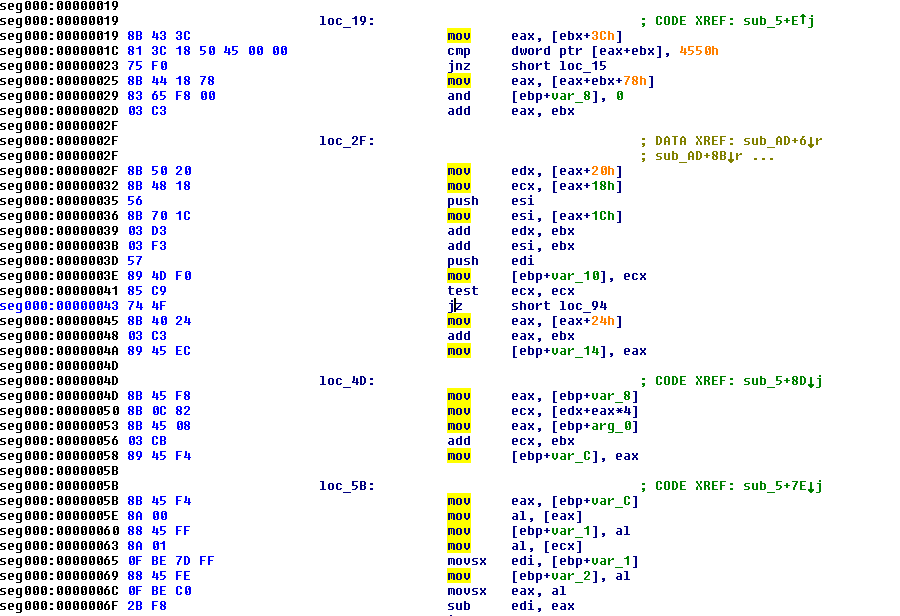
Figure 12: The shellcode checking for the executable to inject in the dllhost.exe.
Before starting the actual activity of the stealer, the malicious program is started by loading configuration into memory step by step.
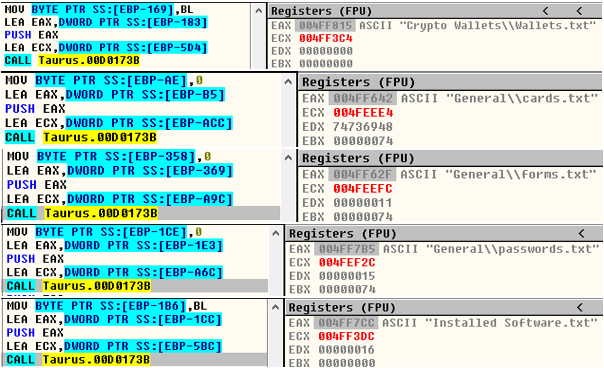
Figure 13: Storing config into memory.
We have successfully been able to see the further activity of the malicious program, which is the actual purpose of this malware—stealing.
Figure 14 shows the system information being fetched by the stealer.
Figure 14: The system information fetched by the stealer.
Fileless approach
While disassembling the code, we figured out that all the stolen data is being sent as a Zip file. Interesting part is that malware allocates a memory space for the Zip file and embeds the Zip file directly to the request data.
Figure 15: All the stolen data is put into a Zip file.
Network Communication
After zipping all the stolen data, the malicious program tries to send that data to a Command and Control (C&C) server after building the URL at run time, which is also pre-defined in the malicious program (Ofcourse XORed).
Figure 16: The URL building to send the stolen data to the C&C.
URL pattern: http://
Cloud Sandbox detection
We have analyzed the sample in the Zscaler Cloud Sandbox and successfully detected the malware.
Figure 17: The Zscaler Cloud Sandbox successfully detected the malware.
Conclusion
We are actively monitoring for new threats in the Zscaler cloud to protect our customers. We have added details of this malware to our threat library.
VBA - https://threatlibrary.zscaler.com/threats/3e4e094a-66e1-407a-8b42-7a683a54bfb1/
EXE - https://threatlibrary.zscaler.com/threats/b26933a4-31f8-4618-a6cf-775f8a383116/
MITRE ATT&CK TTP Mapping
|
T1064 |
Macros in document used for code execution. |
|
T1086 |
PowerShell commands to execute payloads |
|
T1132 |
Data Encoding |
|
T1020 |
Automated Exfiltration |
|
T1003 |
Credential Dumping |
|
T1503 |
Credentials from Web Browser |
|
T1539 |
Steal Web Session Cookie |
|
T1106 |
Execution through API |
|
T1518 |
Software Discovery |
Indicators of Compromise (IOCs)
ECCD93CFA03A1F1F4B2AF649ADCCEB97 - Doc file
3E08E18CCC55B17EEAEEDF3864ABCA78 - Encrypted AutoIT script
221BBAC7C895453E973E47F9BCE5BFDC - Encrypted Taurus Stealer
5E3EA2152589DF8AE64BA4CBB0B2BD3B - Decrypted Taurus Stealer
CnC:
bit-browser[.]gq
Atest001[.]website
Panel
64.225.22[.]106/#/login
















