Recently, the Zscaler ThreatLabZ team came across a nasty piece of malware hosted on a fake MMS website called mmsprivate[.]site. The site lures victims with what seem to be private photos, inviting them to take a closer look. Upon accepting the offer, victims fall prey to a malicious Android Package (APK) that downloads onto their phones. The malware disguises itself as Сooбщениe, which translated to english means Messages, and performs its malicious functionality by exploiting Android AccessibilityService, which assists those with disabilities in using Android devices and apps. It then hides itself in order to spy on its victims.
The variant we are analyzing shows some similar traits, with a few modifications, to malware named RuMMS, which was initially reported by FireEye researchers back in 2016. This new version includes various enhancements, so we have dubbed it RuMMS v2.0.
App Details
App name: Сooбщениe
Hash: c1f80e88a0470711cac720a66747665e
Package Name: ru.row.glass
Detailed Description
Download and installation
The malware is spreading through the site url:mmsprivate[.]site/feel/, and was most likely shared via SMS or email. As soon as the link is clicked, the spyware lures the victim to click a button that leads to the dropping of the malicious APK. The content hosted on the URL is in Russian. You can view the translation in the screenshot below:
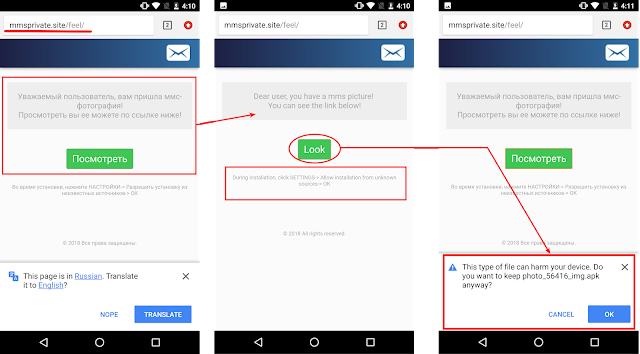 |
| Fig 1: Initial URL leading to the APK download |
The APK is from an unknown source and, since Android systems do not allow direct-install, leads the victim via simple clicks to enabling the "Unknown Sources" option to install the malicious app. Each step is shown below starting from left to right.
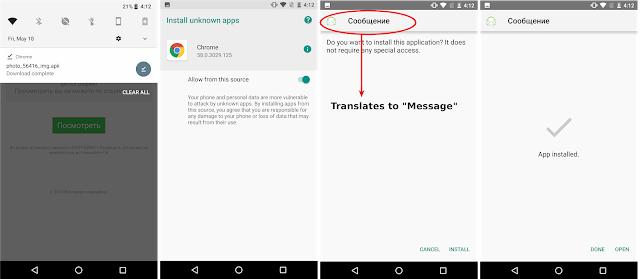 |
| Fig 2: Install from Unknown Sources |
Enabling AccessibilityService
Once installation is complete, the app masks itself as a messaging app (see the icon below). Upon first use, the app redirects the victim to enable Android AccessibilityService. Once enabled, the app disappears from the home screen.
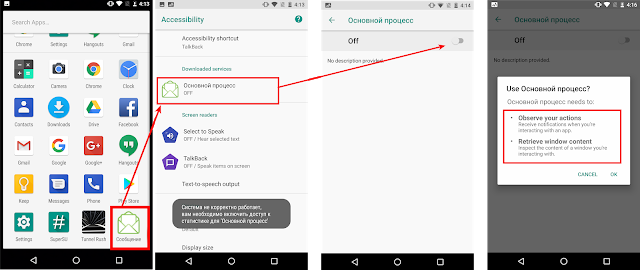 |
| Fig 3: Enabling AccessibilityService |
If the victim does not enable AccessibilityService, the spyware will continuously appear on the screen (see the second screen in the above snapshot) to encourage the victim to enable the service.
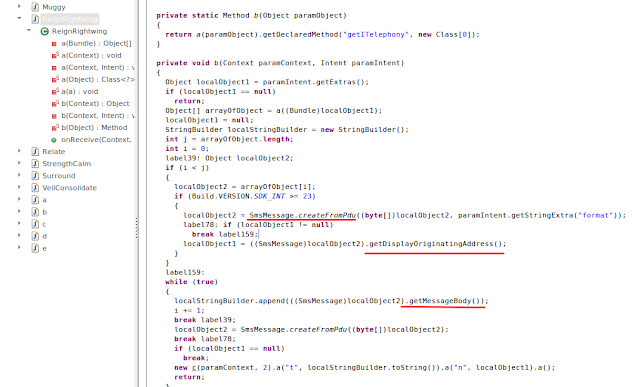
Once AccessibilityService is enabled, the spyware goes into action to make the SMS app the default messaging app. It does this by using the functionality of AccessibilityService to automatically choose “Yes” when asked to confirm the app as the default messaging choice, as shown in the below screenshot. Users will not be able to see this message box because the choice is made for them.
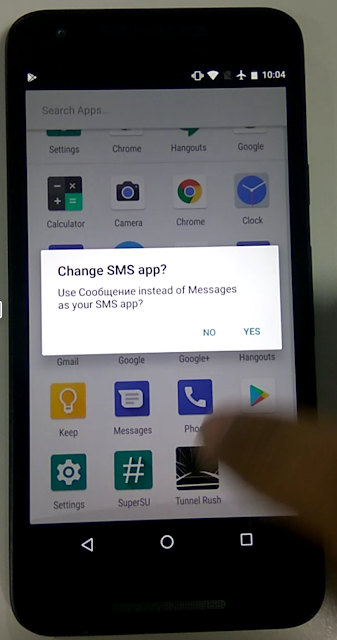 |
| Fig 4: Accessibility Service in action |
Communication
Our investigation showed that once the initial setup is done, the malware starts sending details to a command-and-control (C&C) server. The C&C details were hardcoded. Requests and responses from the C&C were encoded using Base64. The screenshot below shows the decode values being sent and received:
 |
| Fig 5: First request |
The above screenshot shows details of a victim's device being sent to a C&C. The C&C replied with command "40" and the names of apps. We noticed that command "40" was used for disabling the apps.
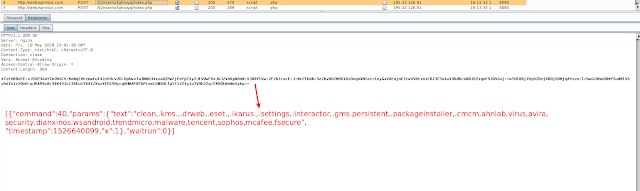 |
| Fig 6: Initial response |
In this instance, the list of apps to be disabled contained well-known antivirus (AV) apps, including:
- Trend Micro
- Dr. Web
- AhnLab
- Avira
- Sophos
- McAfee
- F-Secure
The malware makes sure that all of these AVs, if present, remain inoperable. As soon as a victim tries to open one of these apps, the malware abruptly closes it. It behaved similarly with an app from a well-known Russian bank, Sber Bank. The malware did not allow any Sber Bank apps to open.
SMS: Sending and stealing
The spyware waits for commands from the C&C server and accordingly exhibits its functionality. As in the case below, we found that command number "11" was used for sending SMS messages to any desired number with the body of the SMS instructed by C&C
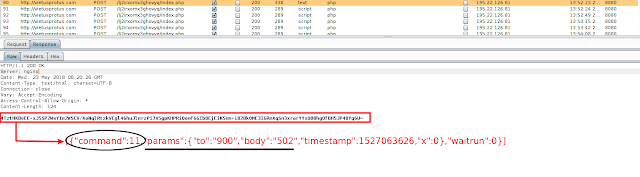 |
| Fig 7: Response containing SMS command |
Upon further analysis, we also found the spyware to be stealing SMS messages from the victim's device. This functionality could also be used to steal bank-related one-time-password codes and other relevant information. The screenshot below shows this functionality in action:
 |
| Fig 8: Stealing SMS messages |
Stealing Contacts
The malware is also able to steal contacts from the victim's device. We believe this functionality is used to further spread the malware with a well-known technique called SMS-Phishing (or SMiShing).
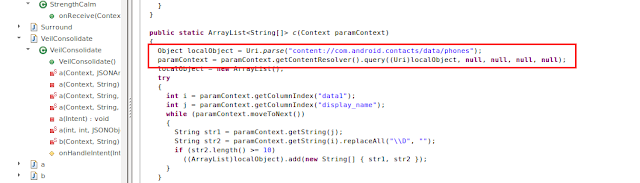 |
| Fig 9: The app stealing contacts |
Calling
The malware also has calling functionality. In the example below, the number to be called was sent from the C&C server in the encoded manner seen here.
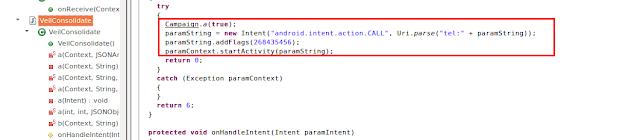 |
| Fig 10: Calling functionality |
One of the more interesting things we noticed was the way the malware was being distributed. Every time we visited the link, we were presented with a new malicious app exhibiting the same behavior explained above but with different app name, different package name, and even signed with a different Android certificate. We also found that apps had different C&C servers with the pattern http://<domain-name>.com/<random-chars>/index.php. We noticed the below mentioned domain names in association with the C&C servers:
| Sr # | Domain Name | # of apps contacted |
| 1 | sisirplus[.]com | 172 |
| 2 | vietusprotus[.]com | 50 |
| 3 | glowbobget[.]com | 45 |
| 4 | hellowopung[.]com | 102 |
| 5 | quostpeopls[.]com | 24 |
| 6 | bannerincbest[.]com | 102 |
| 7 | campuphome[.]com | 9 |
| 8 | wewelowertick[.]com | 3 |
| 9 | bigslogous[.]com | 25 |
| 10 | zavannerweb[.]com | 55 |
Conclusion
A new and improved RuMMS is back in full force as RuMMS v2.0 with enhancements and updated features. In the last 10 days of May 2018, the Zscaler ThreatlabZ team uncovered 580+ similar apps making the rounds in the wild. It is always advisable to stay clear of unknown links. Do not trust any suspicious-looking URLs received either in SMS messages or emails, and only download apps from official app stores.
Zscaler customers are protected from such types of attacks at multiple security levels.
Below is the sha256 hash list of recent samples found in last week. The complete list of 580+ apps can be found here.
| 2cc08d98b2bc11047791e722c2f0e7639f4c5772cda0fb5ecabec1b55914a3c2 |
| 6ec7fba253b76d3b8090a98c6e87c662af8bcda1694a617cce7db59feb08e6f1 |
| 96a8393e583ff1a12df458534790dfd2551861a4fd600f741e36023682d9d9be |
| 1092d809488da433c5d5433a4a1efdc2e32445637e44b6dc77b7fa0e4d536c43 |
| 762c5d1b1b95c46aa6727a49ae27e2b19863d406da2091e50ffe13c79211ffac |
| af6773b1dcec3c3a1d05964ed9d245c2271e96835ffbe3fc543912dc602a64f9 |
| cfc50b2e3da760a2369dbb5bf45fc8d3cdc37a2ad020084aafe2acb53d8603d6 |
| 707456abf552e13ba4ece378d0a7a672bd8fbc22185a478478c81fc7e5c96ce9 |
| a8352f93f7c23953a6deeace67205216c1d37d7f8f6207147d7b93cf272fca9c |
| 751f1ed896639b62e433fcbce5d87b1baeb7a5a82c3a855d30fa4c4c8dddfd81 |
| a1ff7ca12de6cbf36a67aa10ee95202f0c37b8b953f916e9f1780a10042e36af |
| 4a429aae275be2e06ce751537deae327ba377e2e96fc040611f910957b64fcf5 |
| 83728b3d17974df0ac424845668496a2bbf6eaa166e899ef2bf842dae2359bf6 |
| be4ceb20c9ddf2ddba90988a41ee68f43f205860d9a66d5ac8da500f55fb9d21 |
| 09aefb181d949be189a580e5415b74f372d61a13edd86930e6aa0046231813fe |
| b5a7683172d38220c4d179c525b9dd8ffaa28b6b5cb9c1b45bac7a72327b7da6 |
| 383ddecdcdbe2e43035e34307a026e66f79e0b5556f231684db876b3104f0e10 |
| d6f172b04d2e4d1eb7d5e58b16d9768cfe59c32d987ca9b4534e9cf859cce8f4 |
| f18f523d581acb3136e85cb7b2a056f88e48f2d1dfe21f003ef3f12269e470e1 |
| 47e105ef7874e30903d6edadeaa5c2731280663f48c7fb5004cc7668a3ac2a81 |
| d3ca7e61067f527f7cefdddabb0b770ae8ad6d38a89b0f0bccbed995893cea19 |
| 1c66a552c0090f81f7b2ce11c8974bbd2aea75afc1092ad5e8d6f8a1ccf416f3 |
| 21569d8d302180098231efa76482c5a673f344cba8b4654130fada58aad7e62f |
| f2c1b8bd0777cd69329fe22fec8519d810e41b000b92ee13de5629dcd3e875ad |
| 98ab7f612c7a1dc3fd44fbd045a6cf21d8c9240dbad08f847423df5f22d7b460 |
| 758fbbd8a142933f9c5a9866ea7b7c26789da293c93ec3223f5661f62939325c |
| 0b246a1ba24761fb4d6f105d210af9e9c2507b475f13084780a7f9e8145a91a6 |
| eb607863d2e6a56a53893d4c6253896f3e7ab229a75ad29b32762f27bbd398e5 |
| 642be174b9ad9d14b4079472d0a641b9c73f6eb3d8a40152025d438619e22ad5 |
| bd800b6cc3ea900aa111c88adcffca2b31f8c47e00928df985d62bf4cc0daf2d |
| 6858491a04ba906f912d0baf86b37e8ef42c63c505e0db3ffffdf5b543e0c829 |
| 2518d9deb54ed0fa373b0b22a16da5b7a8f02502470987aeeba34398e083c15c |
| f0dabdc7f4364e810e1870afccfd6af14f844f494cd9026879dc2b3becdba8a7 |
| 5e4f663d867ab14c7a2ad6e5f35aa315e34ea0e01c50dbb8d63667c405437e1c |
| 389393e8642e61e8f884ae288be53b71aa9ff5846c5760d013e57c6843e14440 |
| 2dfa3d51b031976f8418d8f7d05f8fa803b937cfc6711f9d4ffeca45ca3db0a5 |
| b4dd995909b8f99d2b519d347c27386b0bfa434332eb7b0c7483a10f0d1d864c |
| f260bb6965405aac4a79de75650f184911185c34e27cc43d27c88efca86ab712 |
| bf170d05c2ae2738ae298b851390eca2bed6fb6db729e3150d3809179c02bec7 |
| e191bc75a21a613232cf5cff2f4874106f3cd64f867b5096b193a7fcf9dc74c4 |
| 88b1fc39c3e89e790fa7fdba78516ac52b489209e9fb38c39aac416f53fdde90 |
| 64647593a8cdfba26a39441cdf49216fbb687652f490cbed230ebc2061aa6b17 |
| 027c3f91df5b5f413c4ce117d4e1a4eb33c050a4be96a0385e8a4cc1c445c027 |
| ee996791fcabcc88d1bc082060a9989fdb1b7079c2e66583002443ac43da87ec |
| a97e2e39a29ebd7ace2895621a6cf2f4a53990d55752816957034b916a149a31 |
| c170ee01c009f4d1a960f6dca3edd2d96fd4e31fad29b7bac248314947d09d1d |
| b0d4b92653518def16f6b08739cf47ba463a6a18f6c7c85ace7be9d6f4145084 |
| 7cffccf41385f1c82c5383a68d79999a1ff506b403cbb00879351bb247a09371 |
| 59746db01df4c33edebf4b4b6cfb44d297cde45f23ec6678ef0f2ca15b40d6e9 |
| b2a940600d50d862f539eead80d636b556d32aabc462156fe8b29d44c3337ab8 |
| 8e839d560f08ae14d5ca457ace9735419e8d5e06f8c30febb48d2997145ff1b6 |
| 5bbecc8c2eaea918ce06e37fa8fda338861662d682cfa43e26ebca6c1075114d |
| d186eaaf72c80289e755ab20a604e4ff20dc98349dfb56206848a4ec79d9388f |
| cc978d00329bbb2c2bf60055d5762dd7b407f44b8df2a31f0d1e54a0958271d8 |
| d507332483bb124158b2b02bf0f3d7b07977bf7fa1c34df5a1b001979a2e2a66 |
| 65d34b945cccd91ce48eb77458768aba34be86be9372f36162e6d42198416775 |
| bce3428913c048d7f8114d07fffacecb7273d65a41e0c7b8bff3f63abb1913b1 |
| a801e38fb832b7f4f9713fb4fbb35f4c5de156c5787718d7fdbe636499e99cf0 |
| 048e3bc98ae1d8ac57eb5e55c5b2cbc6661a77992650a10e35a5d0fbbc1227cf |
| cbb5b11f0e934e8e13c1590c5868dce72f1a364ab32e7ba408f2ad9fa8d5145b |
| d1259c1461d71e238ac9984baf96b94c2c145a820ea44d487b6f2fc4e196ef70 |
| 09ead1fcde087a14da07d58b8db8bed1b18e08701ee4ee300d2af3dbe1a6bd55 |
| a36e780153fb6c26e28ab5cb4c51ebfeb6dd1e04ec6f4489d9ea67c710015b74 |
| 71567ed7c3c0b14a09b5cbd712fcdc777a6bb5d0685c24cccc82e1d1ac3d5d3f |
| 319246f91aff8b444037474ce845cc51785b160a2b650a54cfbe402621598de5 |
| c14c22ddb3d492ef6b40afb3918a97a4b9a8def4dfb6dc944bcdb476e347f1a5 |
| 790654bcb118cf14a6ffcb82a73d18620ab1a993f570d6186f3a1571b6d2b2e8 |
| 04ae5d0126670a8a1eab95373e39db662c921ee468ea7d842d9f894e3d1270c6 |
| f7cb9474374badcc8881bd5c48ff9d0ac3149de053d93abc9a1cad45c319ad04 |
| bb58e7eb3aa7f212c4d8a4bab1dbd086b8d5621441f50b774d6550b811978897 |
| 2202684f0ff5b627baa8473f2068ee3b1d976d7d860f9c188a9178253d356cb3 |
| d130b94a85a8ded1f52469b68977f601617bd536df34c279d37674b03119eb9c |
| 359f8c5ced61249c52655de6ff263c76878c15be12577a920d667f4dcf52e033 |
| b51a6a66778db92878578f3e45cba90fcdb64ca8ece738053b399430bde9e94c |
| 0da9e58ce9b435726f691e869e3efa8f331a8fc2c877c0cee48430837685ec0e |
| f2176c17ee41cb242db184db275d782293e1a71b7d19fd160d56872b17c75096 |
| c9bfea7a58aa8a3b60198832d891622da61d48ace0d97d42aa5616c76382b828 |
| 8d7bfebd2a5255b4caeff9b0f4e76c62336cf15bd6a860fc77cdd9f36d01c340 |
| d717066af883382082fe4672fbc38cc87b52046207f7570f523225f64abe4a25 |
| d14542d7d725a7854433d53fc21447931f54d28858f2847c8db6f19de43d2b81 |
| edb2edbed8bedb3ef25e131e5ea6ed415bae66799323761f113a8a86c2b935fa |
| 41df2e51a18c37acf0564f54ccd2e06ea62122c29a1d705cf1e2a4c31338a2f1 |
| 6e3b96097a635992b10bc51ff5cd72d0cf5b09aaceeeafd3b3ca84d744706ce0 |
| 565c9f86c8c4692a1ca018dd0b0b9cf91c54bdb320172214efa4abac2954e075 |
| 2f9137c1c1e31a7e58a6ad469bd7c268e3a5cd5582e6f930944580a8b1ff827a |
| d1df4dbc7333e4ec1948a0ea180227ed9439aabb78e49bd30d41c86ed901bda1 |
| c28ce42efe922a393eedd3b398dd8a6465d08e40c9dddcf170e6eae7d349c196 |
| 1945682074a418ca389dbc5e69660c7bc0a236fcf90bb8f90c7aa5e03a029d03 |
| 3d344839de28dcbd9101059d2c1dd66aa14e1aceb68f528177f9fe6cd1051419 |
| 79ac737775f6e568bfc62b4e1bde90c615e1e9d41604a4f68d889a7352b5a359 |
| 51ee98b8e02cf3a81a85fd98c8ff9dded3e1b22abee12b308abd2f3aedfda6d7 |
| b0bd2ce89516c6e83a0cffd10db0bb371e84de902c7e91be342353bcae147e90 |
| 94536a9c413b0577f7a81bd6a782e308d40d2f3563f3b6b25f295ae256c074f0 |
| 600b931a3106c63dc29324aa40dbc75c17ccac0ddbbf44c4c657682dadf9c3d5 |
| 0c38da53878c2cbf18edbbd080d8f4b3f9973c16244a2f80c3c74c415fcb5694 |
| af9d21489a18c551a2eaf4f4b7917539bab44547b38f2f0a7348e2b645fcca8e |
| 85f4189eb0f0b6ce91e4d7f93e1e6bec98c4b27950c2b86a5e8f8e05b0e69aac |
| 9ff6093319e604690b114f853df4c708e214e65407962ac37299490d5202023e |
| 4dfc360fdb55e74f7108daefb7e5becc6790510854bba92e83e1eddc2f16e86b |
| 8089f7ea0c96dc24457d9643097a9632c94f9a26bdf8fc6523a5aad555cc4513 |
| 60231f05a17ca19d8a51c5450cebf7bb1a1bc2464cb88a2530bd933c88f1420c |
| 614fcccaf4f988743897200cf0e4330f8878f64ecb395f322b7174f89c08522e |
| a6649912c00dc0f501aeabad050620101ab31ce9088201fe6cf065988b269fe3 |
| d5600a87602f0b268dd04436676229ba146dd01571c19678fb6214826101ce11 |
| 998b7c089ac7441697284bc09024acfcc3e0ea835549e2d9d926f24595ee2f42 |
| 1661346435dbd53231d06ff769bfe58020bdb124208dc7b67b5fae1f3059342a |
| 3ae5dc40e3d4a575762da2d053f38ac82fb2e90fe3beb5292267f85d07b3044b |
| 01e1d9835d4447987c9758c18a02b3348b7feb5fef6be284081d71760786e217 |
| e41636b8f0972afd36d4f3764775d7f5c861147d770ea9a6ea5d723033ba4ad3 |
| 51b97227a6c0866af7a01a7dde873626506f724dad2d555cfba0d5c79b8c9d00 |
| ed2007c3b031391c1ff9117e3f166ebf2b34a4dd3045ca1f4de4251bad88e5a2 |
| e2f6a49245ce98bad73877cc9b5ba71c141c6cd6f16d2147b800744d485d513f |
| 72d1b44ca07b64f608cf5ea4ae28a0b501ad646e071cfea0782186458efe9326 |






