Online streaming of sporting events has increased since the Rio 2016 Olympics. The Olympics is a very popular event attracting billions of viewers across the globe -- and between cord-cutting and COVID-19, more viewers streamed the recent Summer Olympic games than ever before. Most of the streaming transactions observed by the Zscaler ThreatLabz team were from the United States and Europe, with Germany and France leading in transactions. Within the Asia Pacific countries, India and Japan led the way. The importance and popularity of the event makes it a target for cyberattacks, with threat actors installing malicious software from ransomware to coin miners.
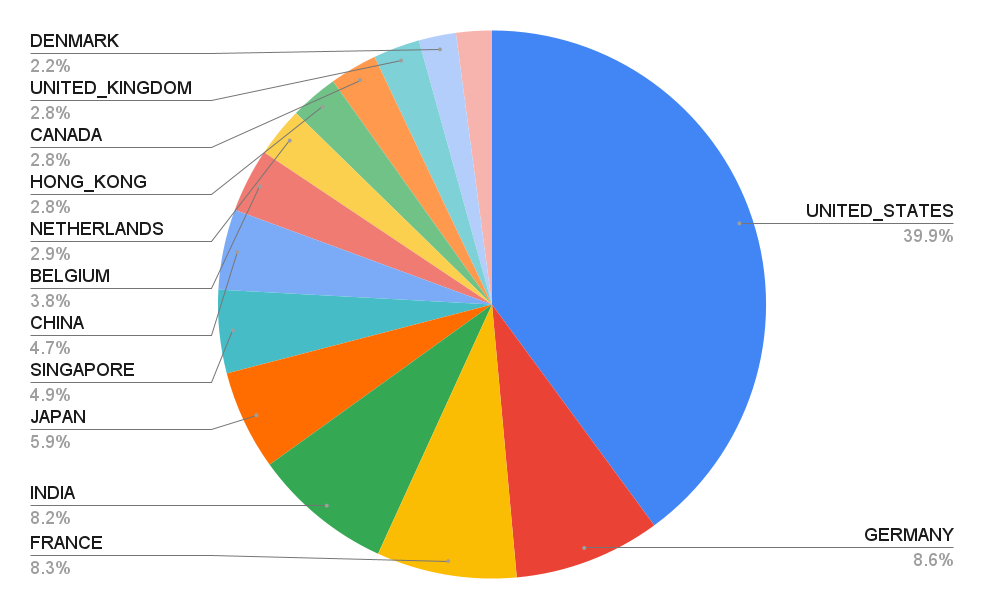
Streaming transaction by country (top 15)
Zscaler ThreatLabz is always on the lookout for threat actors trying to take advantage of major world news and events. For example, during the Rio 2016 Olympics, we observed exploit kit traffic originating from compromised sites that redirect users to various payloads. We have seen hits for RIG EK dropping Qakbot and Neutrino EK dropping CryptXXX. At the peak of the COVID-19 panic in 2020, we saw threat actors using newly registered domains (NRDs) to target users.
During the Tokyo Summer Olympics 2020, we saw fake streaming sites trying to steal and scam users and adware activity redirecting users to install irrelevant browser extensions like YourStreamSearch—a known browser hijacker. We have also seen activity from OlympicDestroyer, a malware that drops credential stealers onto the target machine.
Fake/Suspicious streaming sites requesting for payment
ThreatLabz observed multiple instances of suspicious streaming services. These streaming websites are not associated with legitimate Olympic streaming providers. Instead, the websites claim to provide free access and then request payment credentials from customers. The sites often reuse a template that we’ve seen for many current events, including NBA, Olympic, and football events.
In the screenshot below, we can see a fake streaming site claiming to provide unlimited access for free.
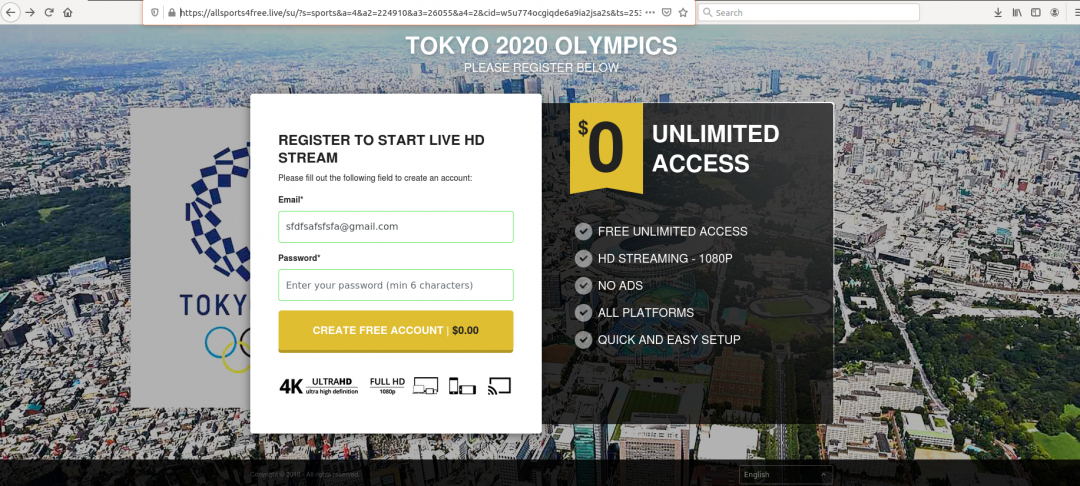
Fake streaming site

Registration form
Once the user completes the registration, they are directed to the payment portal. In the screenshot below, we can see the payment portal requesting user payment details.
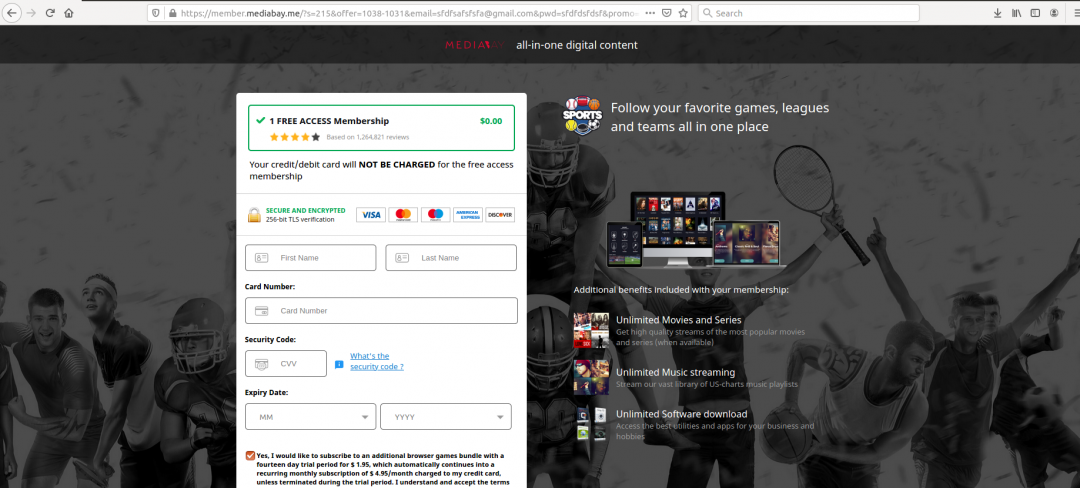
Fake payment portal
Adware activity:
We have seen Olympic-themed adware that claims to offer free streaming services but instead redirects users to unrelated sites for betting, auto trading, etc. We have seen cases where users are redirected to install adware in the form of browser extensions and fake software updaters. In the case below, we can see olympicstreams[.]me redirecting users to install the YourStreamSearch browser extension. YourStreamSearch is a known browser hijacker that recommends ads based on search history
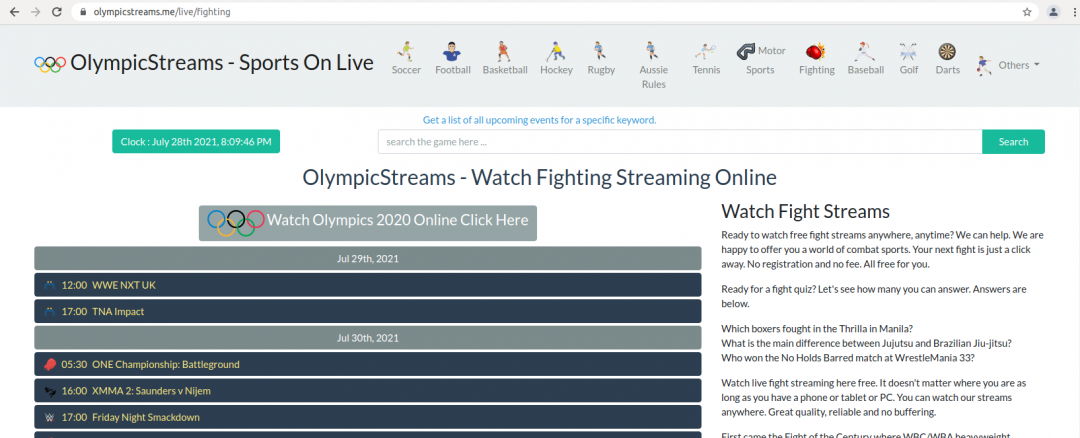
Site offering Olympics 2020 streaming
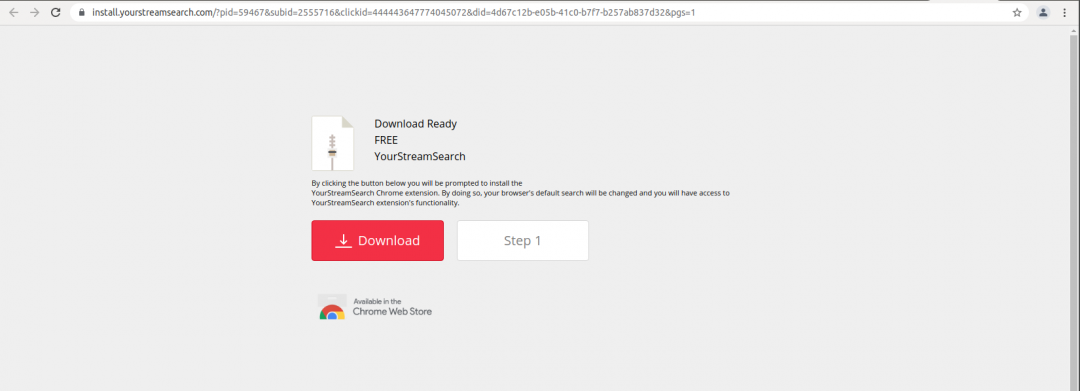
Redirect to YourStreamSearch browser extension
OlympicDestroyer
OlympicDestroyer is a sophisticated malware that was first observed during the 2018 Winter Olympics in South Korea. The malware compromised the official Olympics website. This affected the sale of tickets. At its core, OlympicDestroyer is a worm that spreads using Windows network shares. The malware drops multiple files onto the victim machine. These files are embedded as resources and obfuscated. The files try to steal browser and system credentials.
An interesting behavior of this dropper is that it can generate different binaries based on the credentials it obtains. This has resulted in many variations of samples accomplishing the same task. In addition to credential harvesting, the malware also tries to disable the target machine by using cmd.exe to disable backups, edit boot policies, and delete event logs, among other fun things that make it difficult to recover the machine.
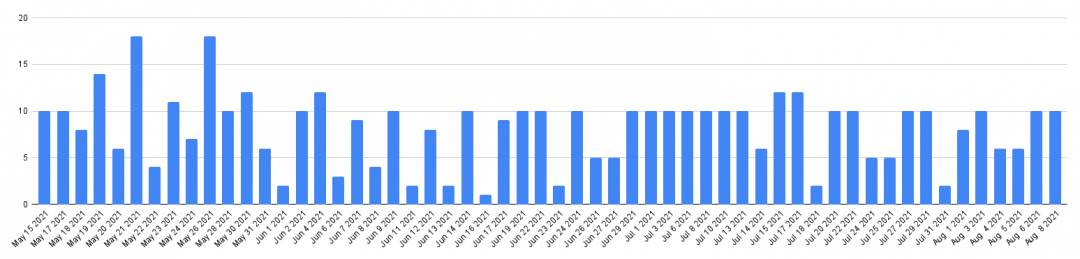
Hits for OlympicDestroyer
The FBI Cyber Division has released an advisory warning users about threat actors attempting to disrupt the event using DDoS, insider threats, ransomware, social engineering, and phishing campaigns. The advisory describes best practices and guidelines for work from home environment and general user awareness.
Suggested guidelines to protect against these attacks:
- Update VPNs, network infrastructure devices, and devices used for remote work environments.
- If possible, enable multi-factor authentication on all VPN connections.
- Verify the source of emails with “too good to be true” deals. Be wary of any suspicious attachments.
- Avoid unofficial mobile application stores.
- Verify the authenticity of the URL or website address before clicking on a link.
- Stay away from emailed invoices - this is often a social engineering technique used by cybercriminals.
- Use two-factor authentication whenever possible, especially on sensitive accounts such as those used for banking
- Always ensure that your operating system and web browser have the latest security patches installed.
- Backup your documents and media files - this is extremely important with ransomware infections.





