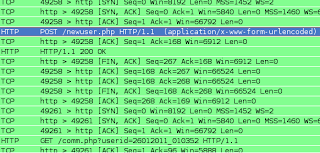
During the course of analysis to try to identify some interesting beaconing behaviors, I noticed some “low” and “slow” activity tied to a malware threat that didn’t have a whole lot of information documented in one place. I’ll try to tie it all together in this post. The beaconing activity is “low” in that very little network activity takes place (generally, saw a 108 byte request and only 260 bytes of response data), and “slow” in that the beacons are not very frequent or regular (though this may have to do with the uptime of the victim too). For example, I saw an exact 3-hour beacon followed by another over 15 hours later.
In the activity observed, I saw the requests going to:
aunznewl1.com, resolving to 199.71.212.157
aunznewl1.net, did not resolve
Note: It appears in most instances of the malware it tries to beacon to a .com / .net domain pair – but in the cases that I’ve seen only the .com is actually registered. I went ahead and registered the above .net domain and will monitor and update this post with any data I find.
URL paths:
/newuser.php
/comm.php?userid=XXXXXXXX_XXXXXX
Note: the user id appears to be a historical timestamp (DDMMYYYY_HHMMSS) from 2011, possibly related to the time of infection. The above two URL paths are quick and easy ways of identifying infections in your network – I didn’t see these patterns in EmergingThreats.
Doing Google searches for the above two domains does not reveal much of anything. However, there is some open-source information that can be pulled-in to tie this to an identified malware family:
To start with, there is a “Trojan.Win32.Generic” GFI Sandbox report that identifies HTTP beaconing to the domain pair thausyn2.com and thausyn2.net on the same IP above. Using the MD5 from this report, we can pull a VirusTotal report which shows it to be detected as a Trojan by 19/41 A/V vendors. Doing a bit more digging shows a few additional reports, for example a Malware-Control report from late June 2011 showing that the malware family is frequently classified as “Ambler” or “Amber” Trojan Spy variant – which can steal passwords and log key-strokes. This is an older malware family, and appears to have some ties to Russia. While it is an older malware family, this current variant shows that it is still in use and exhibits some different patterns possibly allowing infections to fly under the radar.
I downloaded a very recent version of malware from one of the involved domains, and it has very poor A/V detection:
MD5: 2936b54a55615ae85f585c3c6dc1f81b
V/T report: 4/43
The binary itself ends the file with a series of “PADDINGPADDINGXX” strings … which a quick Google shows some malware reports from Anubis. It appears to be an IRCbot used to further download other malware, such as the Ambler Trojan.
Combining open-source reports along with some DNS information provides this list of suspected domain infrastructure used to support this campaign:
aunznewl.com
aunznewl1.com
aunznewl2.com
aunznewl3.com
aunznewl4.com
thausyn.com
thausyn1.com
thausyn2.com
thausyn3.com
thaunzsyn.com
synworkd.com
dogaure.info
dogaure.com
dogaure.net
jokesd33.com
tredoz.com
bart165.info
lim5ff.com
buychau1.com
lakydogau.com
Note: some of the "older" domains used now appear to be re-purposed, for example:
jokesd33.com appears to be a possible work from home / mule scam.
Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Inscreva-se
Current Trojan Ambler Activity
Update with sinkhole results:
About 24 hrs later from registering the one Trojan Ambler .net domain mentioned below and monitoring the sinkhole, I only saw about a dozen infected unique client IPs "correctly" check-in. I did see a few other transactions, but the user-agent and behavior made it obvious that these weren't infections but were from other researchers stopping by (e.g., TrendMicro and Google). Not a huge botnet at all - it was interesting to see that all of the infections were from Australian hosts (iinet.net.au, exetel.com.au, tpgi.com.au, internode.com.au, telstra.net). It is interesting that this particular threat seems isolated to one particular region.
Original Post:
Obrigado por ler
Esta postagem foi útil??
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.