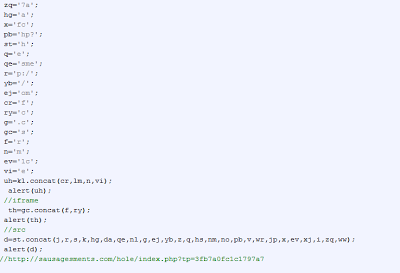
Interestingly, attackers are not only using heavy obfuscation but they also hide the obfuscated Iframes inside HTML body tags. Here is the source of the infected website page which I analyzed this morning:
The heavily obfuscated code has been injected in the HTML body tag. You need to format the code and do some manual analysis to find the malicious URL. In order to do so, you can follow the trick mentioned in my earlier blog for de-obfuscating the malicious content. The formatted code looks like:
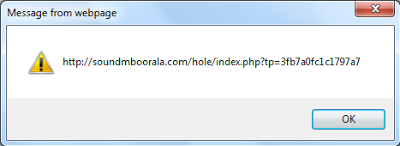
Basically, the above malicious code creates two Iframes pointing to two different malicious websites serving Blackhole exploit kit code. To decode, insert an “alert()” function as described in an earlier blog where it concatenates the various strings. You can then see the malicious URL’s, such as:
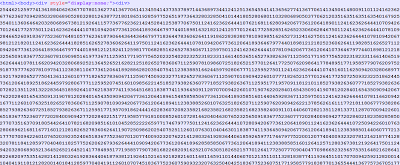
The URL syntax “/index.php?tp=” suggests that the links are related to Blackhole exploit kit. Once visited, the malicious websites return heavily obfuscated exploit code which exploits different vulnerabilities and downloads malicious binaries. Here is what the exploit code looks like:
The above code exploits various older vulnerabilities. Due to the obfuscation used in both the Iframe and exploit, overall AV detection remains very poor. Here is the VirusTotal result for the exploit code. This example shows that the Blackhole exploit kit continues to evolve with different tricks and obfuscation techniques.
Definitely Badhole!!!
Umesh