Blog da Zscaler
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Inscreva-se
Filial zero trust: diga adeus à movimentação lateral de ameaças
A rede crescente e a expansão da segurança
As arquiteturas de rede legadas foram projetadas para um mundo onde seus funcionários estavam todos em escritórios e seus aplicativos estavam em data centers. Construímos e otimizamos redes privadas para conectar filiais e data centers usando tecnologias como MPLS e VPNs site a site e, mais recentemente, SD-WAN, e protegemos o perímetro com firewalls; tudo dentro da rede era confiável e tudo fora era não confiável.
À medida que os aplicativos migraram para a nuvem e as organizações se tornaram mais distribuídas, simplesmente estendemos essa rede para locais remotos, parceiros e a nuvem. Essas redes continuaram a ter muita confiança implícita. Tentativas de segmentar essas redes usando firewalls só contribuíram para uma proliferação infinita de firewalls, projetos de segmentação sem fim e uma explosão de custos e complexidade, deixando as equipes de infraestrutura com escassez de recursos.
A SD-WAN tradicional facilita ataques de ransomware
Embora essas arquiteturas de rede legadas tenham facilitado a comunicação entre usuários, dispositivos e cargas de trabalho, elas também estão facilitando a movimentação lateral de ameaças. Um único dispositivo infectado em uma filial pode alcançar e infectar seus aplicativos mais importantes no data center ou na nuvem. Essa é uma das principais formas de disseminação de ataques de ransomware. De acordo com o Relatório de ransomware de 2024 da ThreatLabz, vimos um aumento de 58% no número de empresas extorquidas somente no ano passado, com pagamentos recordes atingindo US$ 75 milhões. Os ataques de ransomware continuam a aumentar por um motivo simples: as SD-WANs legadas expandem sua superfície de ataque e permitem a movimentação lateral.
Continuar usando arquiteturas legadas em um mundo moderno não apenas aumenta os custos e a complexidade, mas também deixa você vulnerável.
Filial zero trust: sem movimentação lateral, sem firewalls
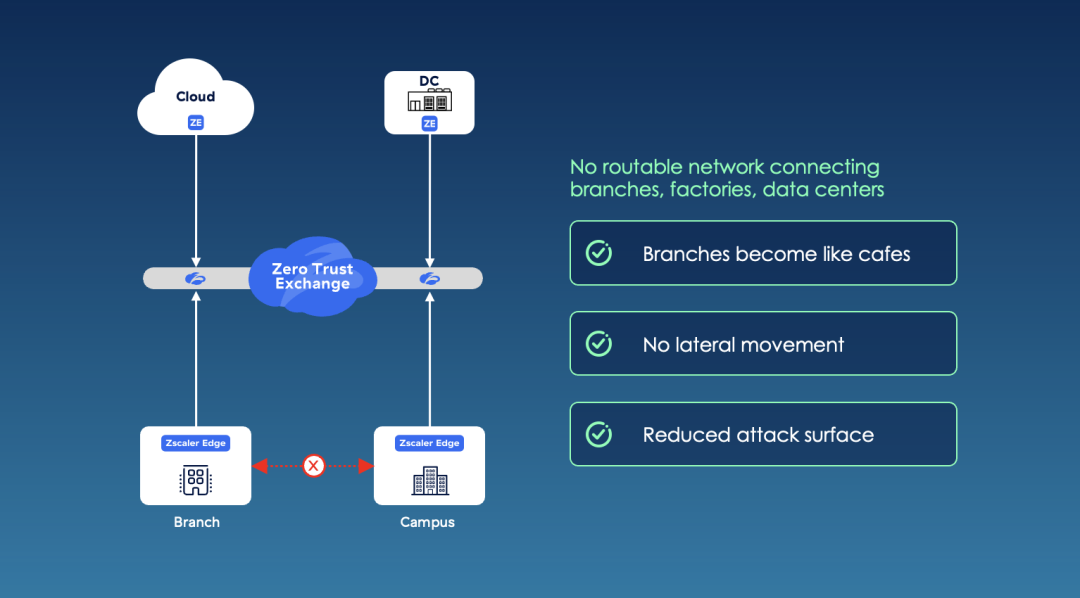
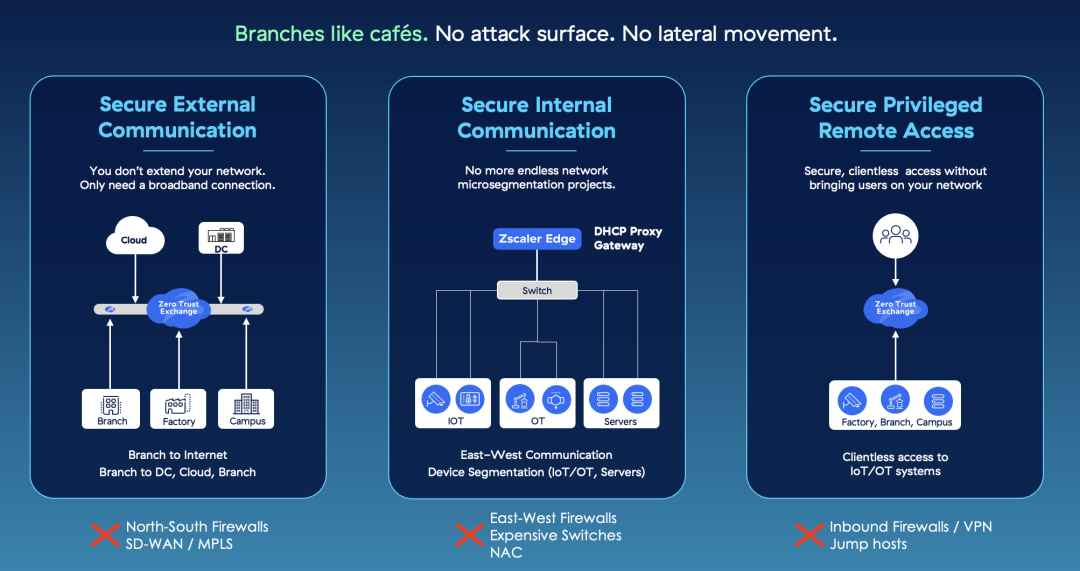
Com uma arquitetura de filial zero trust, você não precisa estender sua rede para todos os lugares: suas filiais se tornam similares a cafeterias. Os usuários, dispositivos e aplicativos se comunicam por meio da Zero Trust Exchange, utilizando qualquer conexão de banda larga ou rede móvel. Não há portas abertas escutando conexões de VPN que os invasores possam explorar. Um dispositivo em um local não pode verificar a rede para encontrar dispositivos e aplicativos em outros locais. Sem uma rede roteável plana, você não precisa de firewalls em cada filial.
A filial zero trust é possível graças a três inovações principais da Zscaler. Primeiro, a SD-WAN zero trust da Zscaler substitui sua SD-WAN tradicional, MPLS ou VPNs site a site e facilita comunicações seguras de entrada e saída de sua filial. Usando um dispositivo Zscaler Edge que encerra e gerencia diretamente suas conexões com o ISP, a SD-WAN zero trust otimiza o desempenho do aplicativo e fornece proteção total contra ameaças cibernéticas e dados para todo o tráfego de usuários, dispositivos e servidores da filial. Com três dispositivos físicos (ZT 400, ZT 600 e ZT 800) e um dispositivo virtual (ZT VM), as organizações podem conectar uma variedade de filiais, campi, fábricas e data centers à Zero Trust Exchange.
Temos o prazer de anunciar novos dispositivos Zsaler Edge compatível com rede móvel 5G, como uma conexão do ISP primária ou de backup, para proteger locais adicionais, como caixas eletrônicos, escritórios de campo e lojas de varejo. Além disso, estamos também anunciando dispositivos com maior capacidade de processamento que serão compatíveis com até 5 Gbps de throughput criptografado para permitir múltiplas conexões de fibra gigabit operando em modo ativo-ativo.
A SD-WAN zero trust garante que as ameaças não possam se mover lateralmente entre os locais. Nos locais, as inovações da Zscaler em segmentação de dispositivos zero trust ajudam você a segmentar ainda mais cada dispositivo em uma rede individual, eliminando a necessidade de firewalls leste-oeste, NAC e switches proprietários caros. Implantável em horas, essa solução inovadora descobre, identifica e segmenta cada dispositivo (até mesmo sistemas OT legados) e elimina toda movimentação lateral dentro do local.
Outro fator de risco significativo para a movimentação lateral de ameaças é o acesso de fornecedores e prestadores de serviço terceirizados a sistemas e servidores de OT. Tradicionalmente, isso exigia uma conexão de rede ou uma VPN que traria dispositivos não gerenciados/desconhecidos em sua rede com acesso direto aos seus ativos críticos. O acesso remoto privilegiado da Zscaler fornece uma abordagem mais segura que não requer uma conexão de rede entre terceiros e sua infraestrutura. Usando o acesso baseado em navegador sem cliente e tecnologia de streaming de pixel com controle de teclado e mouse, você pode permitir que técnicos remotos acessem com segurança seus sistemas de OT, com supervisão completa, gravação de sessão e controles de sandbox de arquivo, para ajudar a minimizar o risco para suas fábricas e garantir a segurança do pessoal.
Reduza custos e melhore a segurança
Uma arquitetura de filial semelhante a cafeteria tem muitos benefícios para equipes de infraestrutura e usuários finais.
Menor custo: como você não estende sua rede para todos os lugares, sua infraestrutura e custo reduzem significativamente. Você não precisa proteger cada filial com firewalls, assim como não protege a rede doméstica de cada funcionário. Você elimina a complexidade de roteamento e o gerenciamento de políticas de firewall.
Melhor segurança: o ransomware não pode se mover lateralmente entre locais ou mesmo entre dispositivos no mesmo local. Além disso, sua superfície de ataque diminui: as filiais não são mais alvos eficazes. A Zero Trust Exchange fornece proteção completa contra ameaças cibernéticas e dados, garantindo que os dispositivos não conversem com sites de comando e controle conhecidos ou exfiltrem dados por canais como DNS.
Melhor experiência do usuário: como você não precisa mais fazer retorno do tráfego pelo seu data center para inspeção de segurança, os aplicativos se tornam mais rápidos e os usuários têm uma experiência melhor e mais consistente no escritório e em casa. Você também elimina compensações de desempenho e segurança: todo o tráfego, incluindo tráfego criptografado em TLS, pode ser inspecionado na Zero Trust Exchange sem penalidades de desempenho.
A filial zero trust da Zscaler não apenas simplifica a arquitetura da sua filial, cortando os custos de infraestrutura em até 50%, mas também melhora o desempenho e oferece uma experiência de usuário excepcional. E o melhor de tudo, com uma arquitetura zero trust, ela elimina a movimentação lateral de ameaças e interrompe ataques de ransomware em andamento.
Saiba mais sobre as inovações da filial zero trust em nossa página de recursos de lançamento.
Esta postagem foi útil??
Receba as últimas atualizações do blog da Zscaler na sua caixa de entrada
Ao enviar o formulário, você concorda com nossa política de privacidade.




