This was originally published on LinkedIn on October 13, 2020,
Did you leave the window open? Lock the door? The invitations to cyberattacks are there. And bad actors can see them. But can you?
Few enterprises have a solid grasp of their own vulnerability to cyberattacks. Attackers seek entrance in the form of enterprise IP addresses and namespaces exposed to the open internet. Each of those exposed addresses represents a metaphorical door into your corporate network and systems, and threat actors quickly identify which of those metaphorical doors aren't locked. (Of course, once through the door, the hackers have run of the corporate house.)
Traditional network security attempts to address those vulnerabilities by "listening" to inbound connections to identify incoming threats.
There's a frustrating irony to this: This “listening” approach to network security exposes yet more IP addresses and namespaces to the outside (read: hostile) world. This leaves servers vulnerable to attack and exposes your internal applications, data, systems, resources, and other proprietary assets.
Enterprise IT leads have a responsibility to understand the extent of their own exposure and then mitigate the risk associated with that vulnerability. CISOs must be able to answer the question "How many doors did I leave open?" Or perhaps more appropriately, "How many of those doors can bad actors see?"
There hasn't been a constructive way to measure an organization's vulnerability to attack from outside. Until now.
At this week's Zscaler CXO Summit, I had the privilege to demo Zscaler's Internet Attack Surface Analysis Tool. The Internet Attack Surface Analysis Tool is free and available now on the Zscaler website.
The Internet Attack Surface Analysis Tool assesses and then quantifies an organization's network exposure risk. In this way, it conceptualizes an organization's attack surface, giving IT leads information to reduce risk.
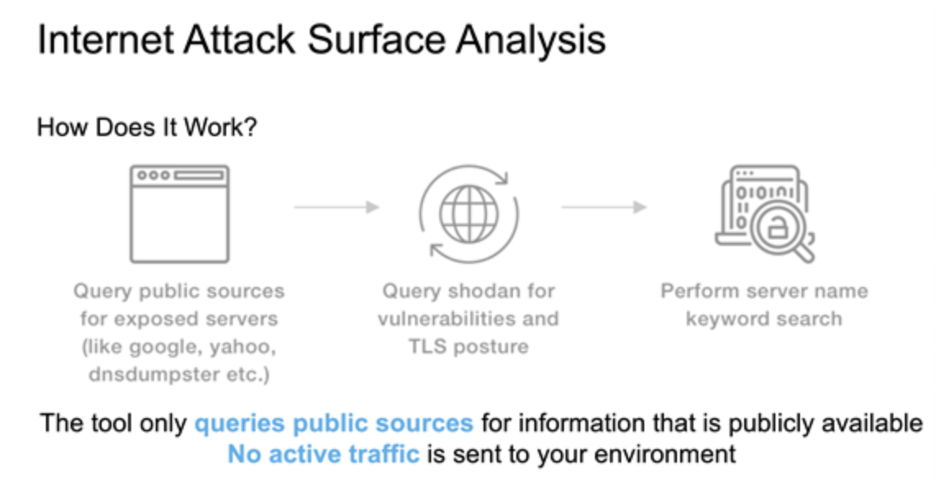
A few important caveats:
- The Internet Attack Surface Analysis Tool performs its analysis functions without actively scanning or connecting to a customer’s network(s).
- It queries only passively available information sources.
- Zscaler validates all scan requests to ensure that users can only scan their own organization.
The Internet Attack Surface Analysis Tool does more than "count doors." It performs a comprehensive network exposure audit, identifying:
- Known vulnerabilities: These are security flaws with known exploits and represent a huge risk to enterprise cybersecurity.
- SSL/TLS risks: Systems with outdated encryption protocols are tempting attack targets for hackers.
- Exposed servers: Servers that are open to the internet are an entry point for threat actors seeking to move east/west within a corporate network perimeter.
- Namespace exposure: Keywords associated with a namespace divulge information about applications and systems, and represent an unintended (and often overlooked) risk to the company.
- Public cloud instances: When not closely managed, public cloud instances associated with an organization can become an attack vector. Companies with active "shadow IT" efforts are particularly vulnerable.
The Internet Attack Surface Analysis Tool produces an extensive report that quantifies an organization's attack surface based on the assessment criteria above, as well as several other performance and exposure metrics. It also recommends detailed mitigation strategies for each risk measurement. Let's look at a snippet of an example output report:
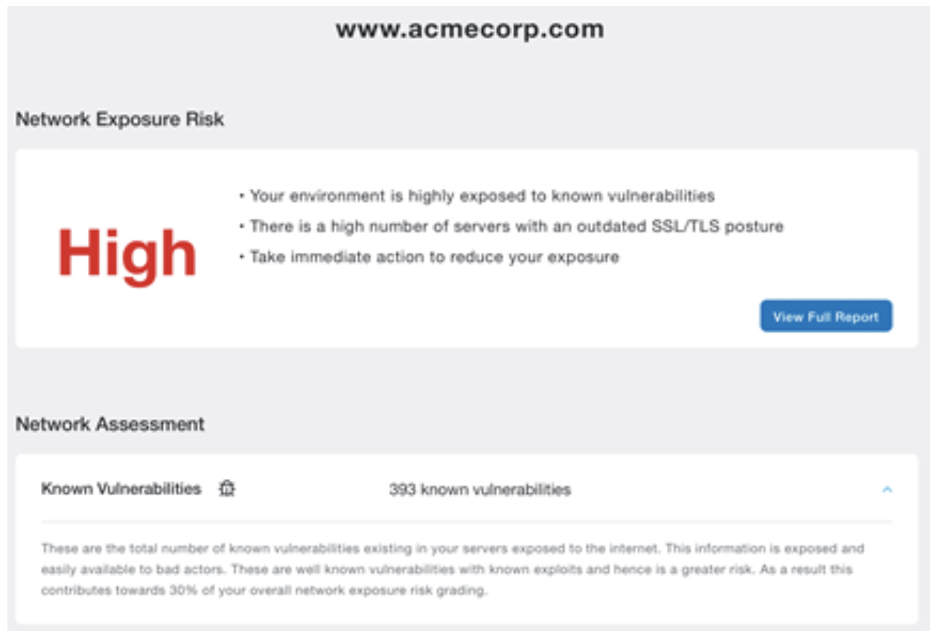
This is a real-world example from an assessment performed on an anonymized Fortune 500 company. "Acme Corp." is vulnerable to attack. It has a sizable attackable surface area and a dangerous network exposure risk. The assessment calls out Acme's out-of-date encryption protocols. But of particular note are the "Known Vulnerabilities" to critically severe threats: Acme Corp. has not kept up with its security patching.
Hackers attack what they can see. Connectivity shouldn’t require exposure, yet it does when enterprises connect outdated legacy network architectures to the internet. Connectivity must be inside-out, not outside-in. Cloud-based ZTNA/SASE solutions, such as the Zscaler Zero Trust Exchange platform, employ the internet to supplant perimeter-based security, enabling (and more importantly, securing) direct, one-to-one connectivity between user and resource. It's a model that secures the way people actually work and obscures corporate systems from the outside world.
The Internet Attack Surface Analysis Tool identifies enterprise vulnerabilities. But it's only a first step toward strengthening an enterprise's threat posture. The object lesson here is embodied in Acme Corp. After its Zscaler-enabled digital transformation, Acme Corp. re-ran its Internet Attack Surface Analysis Tool assessment. The result? A “LOW” risk assessment and a greatly reduced attack surface.
Watch my CXO Summit innovation showcase presentation here. And learn more about the Internet Attack Surface Analysis Tool here.
Patrick Foxhoven is the Chief Information Officer and EVP Emerging Technologies at Zscaler.






