The federal government has taken on the task of transforming its cybersecurity approach to Zero Trust. This transformation is uniquely challenging for the largest government agency, the Department of Defense (DoD).
To undergo this behemoth of a task, DoD has approached each Zero Trust pillar's capabilities and timeline with a mix of strategic, tactical, and operational focus. Moreover, DoD purposefully drafted its Zero Trust Strategy and Zero Trust Reference Architecture (ZTRA) with enough flexibility to enable each MILDEP, and their sub-organizations, to fail fast, pivot to what works for their environment, and fulfill the mission put forth in DoD's Zero Trust strategy.
Under this modernized cybersecurity banner, the world has acknowledged that more and more, access control evolves. It decouples itself from the network and requires seamless, automated enforcement across the enterprise—in order to support DoD's operational requirements that traverse persistent and episodic network terrains.
Alright. What changed? Because 'Evolved' is a loaded word.
Short answer: Technology.
From the era of Operation Buckshot Yankee leading to Zero Trust, DoD's cybersecurity mission has always been about securing data via network-centricity. However, single-purpose siloed solutions supported this mission with limited cross-platform and architectural integration functionality—propagated by a family of systems TTP for isolated and disjointed mission sets. This situation inadvertently spawned a multi-verse of vendor variants of the same product while vendors capitalized on per-user/per-device cost models. While this is not a referendum on hardware and appliances, there's no denying: Cloud-native technologies augment hardware platforms and leverage API integrations to enhance operations, automate at scale, and secure hardware and software on-prem and in the cloud. Just as important, cloud-native technologies secure hardware and software on-prem and in the cloud, and the data that flows through them, executing on the new focus in a Zero Trust world.
Ok. Tell me you've read DoD's Zero Trust Strategy without telling me you've read DoD's Zero Trust Strategy.
Short answer: Maturity.
Solutions/tools brought to the DoD for inclusion in the reference architecture need the maturity to deliver. The DoD is not a place to incubate good ideas.
Too obvious, right? Well, the finer detail in any maturity model is not on the capability itself but on the sets and reps, stress tests, and scrutiny put on the capability before placing it into DoD's hands. A LOT of capabilities out there will be able to (air quote) meet DoD's ZT Capability and Activity requirements - but will they be able to do it globally? Will they be already vetted to accomplish an ATO? Or have the organizational expertise to assist? Will they be able to be leveraged for more than ONE use case? Will they be able to lower security and operational risk? Or be more secure or faster than alternatives? These capability characteristics hide in plain sight within every ZT activity requirement and should be validated realistically.
Using cloud-native integrations and automation, DoD can improve security and operational efficiency and expedite fielding new technologies, like a Capability Exercise (CAPEX) but one that can be conducted globally. Cloud benefits overlap with DoD's Zero Trust, Cloud CONUS/OCONUS, and C-JADC2 strategic visions to support multi-domain operations, especially cyber, across the enterprise to tactical environments to conduct full spectrum warfare regardless of whoever has administrative control over the network terrain.
I’m following along. What’s Zscaler's place in this ZT wicked problem?
Short Answer: Automate, integrate, and unify security everywhere.
Zscaler integrates with capabilities across our partner ecosystem to provide best-of-breed proven solutions to natively unify threat intelligence, security posture, and policies across pillars - not only networks or domains. Like the Visibility & Analytics and Automation & Orchestration pillars, Zscaler's capabilities crosscut each DoD Zero Trust pillar's family capabilities within the DoD's warfighting apparatus while providing consistent best-of-breed security services. This matured 'Zero Trust JTF' empowered by technology and API integrations allows the DoD to cut to the BLUF: "Technology is not the challenge; siloed, immature technologies are."
Below is a view of Zscaler's alignment to each of the DoD's Zero Trust seven pillar activities, resulting in a cross-pillar integration that enhances each pillar's cybersecurity mission readiness and visibility to automate, integrate, and unify security and optimize access control.
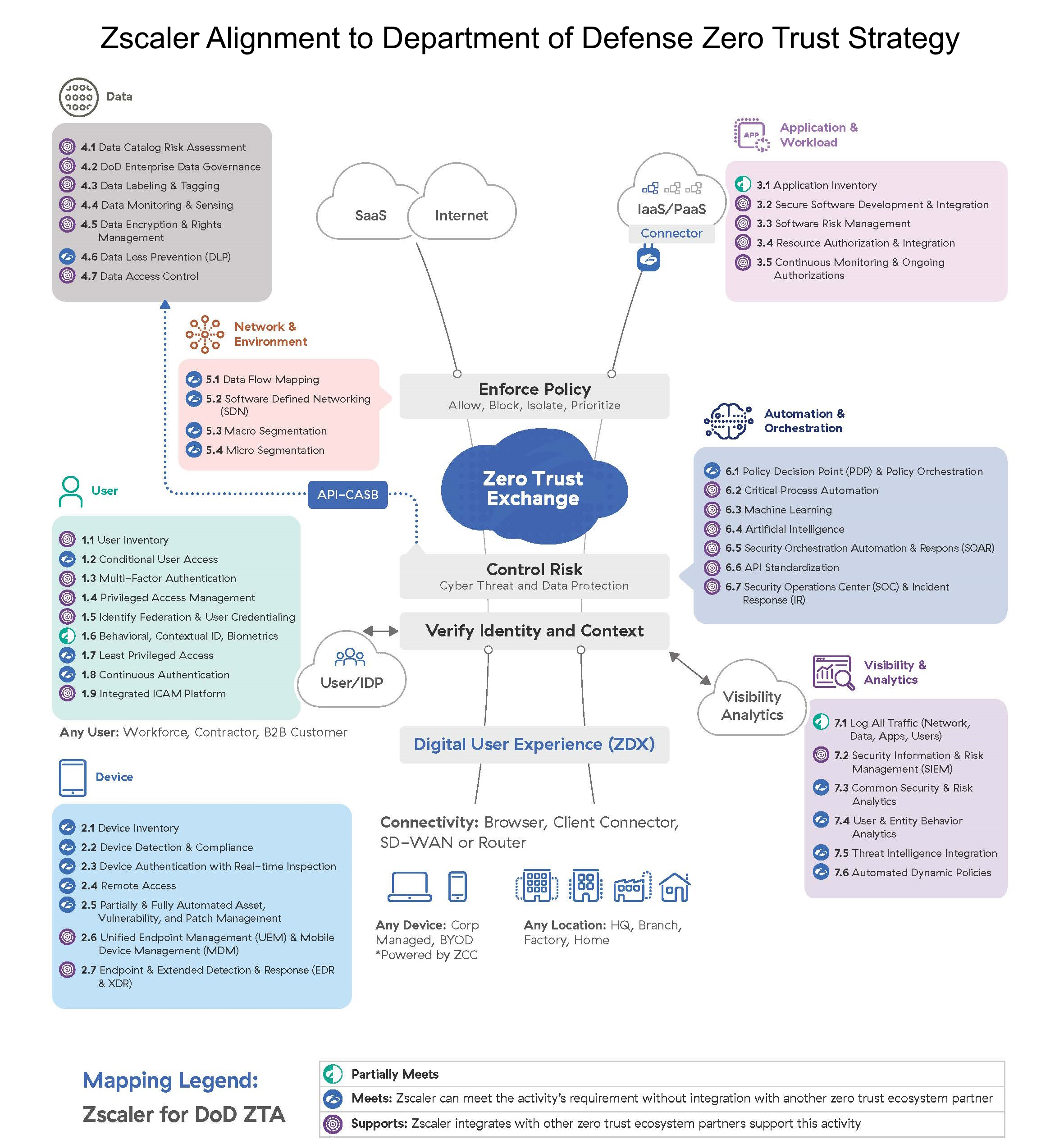
Over 6,000 commercial, federal, and defense agencies trust Zscaler as their foundational ZTA capability to "prep the battlefield" for their Zero Trust implementation and secure over 40 million concurrent users globally. With over 130 technology partner integrations and Open APIs, empower Commanders with a true cloud-native technology platform founded in encrypted secure access, scalability, and API integrations that deliver, integrate, and achieve most of DoD's Zero Trust capabilities…again, thousands of organizations have accomplished this granular sophistication in their production environments, impacting their bottom lines and our national security.
We invite you to visit Zscaler at TechNet Augusta 2023 to meet with our zero trust experts and see a full mapping of the Zero Trust Exchange to the DoD Zero Trust Strategy. Browse our event page here for more details about our booth, exclusive AFCEA chapter course, networking receptions, and to book a meeting.
For more information about how we serve the Federal government with our FedRAMP high and moderate as well as DoD IL5 authorized solutions, visit our Federal page.




