Now that private apps are moving to public clouds, and users are accessing them from locations all around the world, on a variety of devices, the classic perimeter has changed. You'll probably hear a lot of vendors at RSA 2020 say that the perimeter is gone, but we believe it has expanded—it's everywhere your users and apps connect. Security teams must now look at ways to provide secure access to apps across hybrid environments—and ensure that data remains protected as they do so—without getting in the way of transformation and without introducing risk.
But if this is the goal, and it’s well known that the majority (98 percent) of security attacks come from the internet, why do teams continue to expose their apps to the internet?
The truth is probably rooted in a bit of history as well as a bit of reality.
“Come find me”
Security teams have spent millions of dollars on traditional security infrastructures to “protect the network.” So, of course, it’s frustrating and a bit disheartening to realize that the network security tools they purchased for protection are actually broadcasting the location of their apps. Yikes.
The truth is that legacy architectures were designed to connect a user to a network. To do so, organizations must provide an entry point for network access to take place. This entry point is discoverable by not only the remote users who need access but also cybercriminals scanning the internet for attack vectors.
VPNs, for example, force user traffic to be backhauled to a data center through a VPN inbound gateway stack to get onto the network. And virtual firewalls spun up in a limited number of public cloud locations listen for calls from remote users. In both cases, this inbound allowance is where the risk is introduced. It’s essentially a beacon that tells enemy ships to “come find me.” And the more firewalls you have, the more beacons there are telling criminals where to go.
Such beacons are opening organizations up to a greater number of ransomware attacks.
Go invisible
We get it. Making your network and its apps invisible is easier said than done, and it requires a different approach to connectivity. In the end, it comes down to having the right solution in place to enable the business. This is why companies are adopting cloud-delivered zero trust network access (ZTNA) services. These services are part of a larger platform that Gartner calls secure access service edge (SASE), which is designed to bring application connectivity to the edge in a way that is secure, highly available, and fast for users.
ZTNA allows teams to connect authorized users to apps running in any environment, without ever having to be placed on the network. By taking the network out of the equation, there is no longer any need to bring the user onto it. If there is no need to bring anyone onto it, then you don’t have to expose the network to the internet just to provide connectivity to the apps running on it.
You can see a high-level, side-by-side comparison of legacy approaches (VPN and Virtual Firewalls) vs. a purpose-built cloud service (ZTNA).
Figure 1. Legacy approaches vs. ZTNA
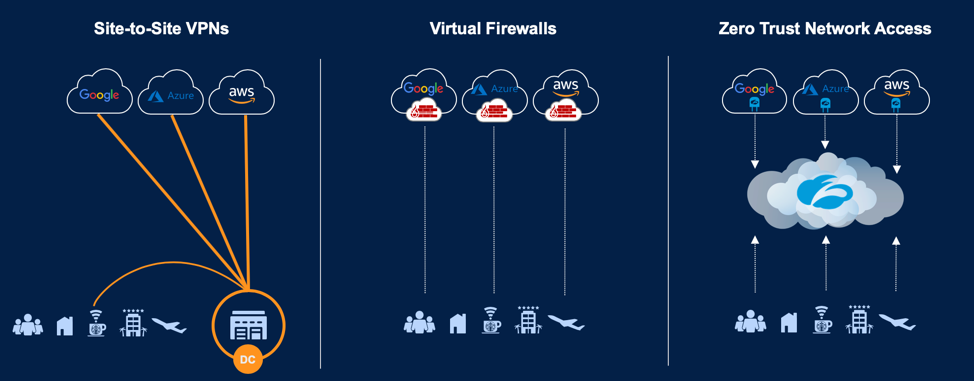
We’ve worked with leading global organizations, including Kering, BBC, National Oilwell Varco, Koch Industries, Paychex, MAN Energy Solutions, and more, to protect their data by making their apps completely invisible to the internet. Instead of allowing inbound connections to the corporate network, our cloud provides access to apps based on policies and by brokering a TLS-encrypted connection between a specific authorized user and a specific sanctioned application within our cloud service over the internet. This “outbound only” concept allows our customers to eliminate the attack surface.
_______________________________________
Pro tip: You can’t protect what you can’t see either. This is why we also give our customers the ability to shine a light on previously unknown apps so they can apply policies and further reduce their attack surface. In short, we provide a black cloud to mask your known apps, and a flashlight for the undiscovered apps lurking in the dark.
_______________________________________
In the end, the bad guys can’t scan for your servers, can’t get access to your network, nor can they DDoS your applications (they don’t even know an application exists). They move on. The good guys are able to protect the company’s data without having to worry about battling the next ransomware attack or denial-of-service attempt. And, they’re empowered to help enable the business to transform.
Sounds like my kind of story.
Eliminate your attack surface
This isn’t some kind of dark magic. It’s a real solution to a real problem. Want to learn more? Then stop by the Zscaler booth (#1143 in South Hall) at the upcoming RSA 2020, which will be held at the Moscone Center in San Francisco from February 24–28. There, you can talk to me or other experts who can explain ZTNA and other concepts and show how you can employ these solutions in your organization.
At our booth, we will also be hosting our “attack surface challenge” — give it a shot to be eligible for some cool prizes. Visit our website to learn more about what Zscaler has in store for RSA. I look forward to seeing you there.
Christopher Hines is the Head of Product Marketing for Zscaler Private Access and Z App.






