/ What Is Double Extortion Ransomware?
What Is Double Extortion Ransomware?
Double extortion ransomware is a type of cyberattack in which threat actors exfiltrate a victim’s sensitive data in addition to encrypting it, giving the criminal additional leverage to collect ransom payments. A typical ransomware attack will only encrypt a victim’s data. The additional threat of exfiltration makes this attack especially dangerous for organizations in all industries.

What Happens During a Double Extortion Attack?
In a double extortion ransomware attack, a ransomware operator gains access to a victim’s network using any of a variety of established methods and threat vectors. The operator then performs network discovery to locate and secure access to high-value assets from across the network and connected endpoints, and then exfiltrate them to the operator's own storage network.
After spreading laterally throughout the network, the threat actor encrypts the data and demands a ransom. If the ransom is not paid, the criminals will often sell the stolen data or publish it in public blogs and online forums.
How Do Attackers Gain Access?
Attackers have long-established methods of gaining access to organizations’ private systems or endpoints, and typically, those uses for carrying out double extortion are no different:
- Phishing
- Malware
- Vulnerability exploits
- Brute-forcing an RDP server
- Stolen credentials
Bad actors have now been targeting sensitive data for decades, particularly in highly regulated verticals such as healthcare, finance, and the public sector. Because of the reputational fallout that comes from these attacks, more and more CISOs are prioritizing vulnerability management, attack surface management, and access control with zero trust—but more on that later.
Attack Sequence of Double Extortion Ransomware
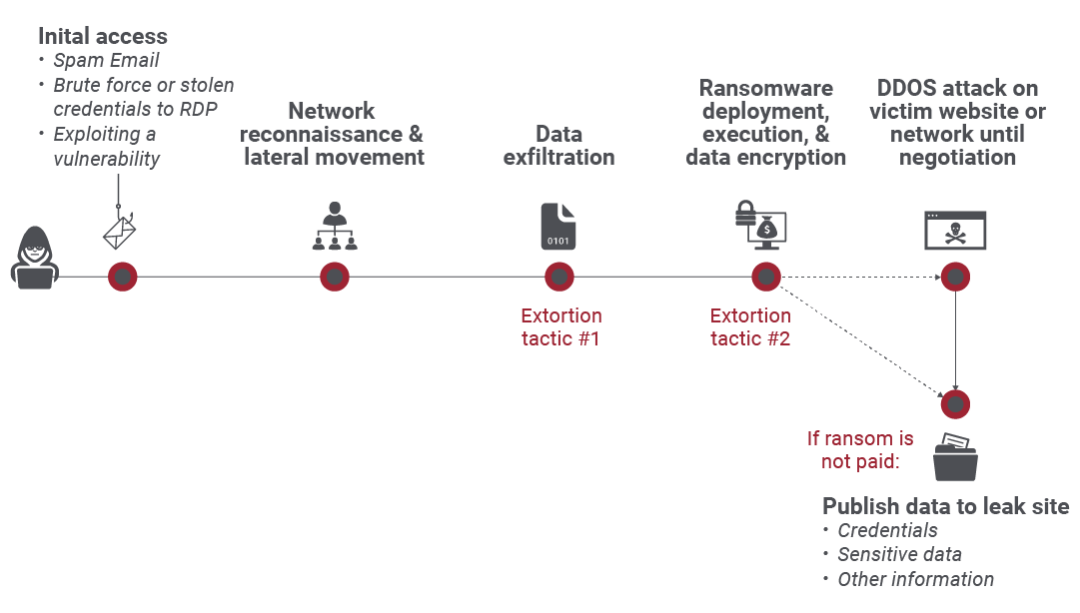
The double extortion ransomware kill chain is only slightly different from that of typical ransomware. With double extortion, attackers carry out two separate methods of attack within a single perpetration. Here is the kill chain:
- Initial access: In this phase, the attacker is able to break into a user’s or organizations’ systems by using one of the methods listed above.
- Network recon and lateral movement: The bad actor surveys the security landscape to see where they may be detected. Once they have free rein across resources, the attacker moves throughout different parts of the network.
- Data exfiltration (Extortion tactic #1): In the first step of double extortion, data is removed from the device, but not yet held for ransom. To that end, the user is also not yet notified of their data being held hostage.
- Ransomware deployment (Extortion tactic #2): This stage takes place during all ransomware attacks. The ransomware is deployed and executed, and the data is encrypted.
- DDoS attack on site or network: At this point, the attack is in full force. The user is notified of the attack on their system, and they’re given instructions to pay a ransom in order to get their data back.
This lethal sequence of attack makes double extortion ransomware one of the most feared threats in all of cybersecurity. But how did it come to be? How have these attacks wreaked havoc on organizations as of late? Let’s take a look.
The Origins of Double Extortion Ransomware
Ransomware has been around in some form for decades, beginning with the 1989 AIDS trojan, or PC Cyborg virus. Distributed via floppy disks, the AIDS trojan directed its victims to mail $189 to a post office box in Panama to regain access to their systems.
More than 30 years later, the advent of cryptocurrencies has made tracking of payments more difficult for law enforcement, but cybersecurity teams have improved their backup and security policies to aid in decryption. In 2019, a criminal organization called TA2102 used the Maze ransomware to perpetrate the first high-profile double extortion ransomware attack when they infiltrated security staffing company Allied Universal.
Instead of simply encrypting the firm’s data, TA2102 exfiltrated it and threatened to publish the stolen information online unless Allied paid a ransom of US$2.3 million in bitcoin. This meant that even if Allied had been able to restore their network and data, they would still suffer a severe data breach unless they paid up.
Since then, double extortion ransomware incidents have become more popular and complex. In 2020 alone, at least 15 ransomware families using the technique perpetrated 1,200 incidents, resulting in many high-visibility data leaks.
To add to that, ransomware attacks in general have become larger, more frequent, and easier to perpetrate. Affiliate networks now can purchase ransomware as a service (RaaS) over the dark web as well as use high-impact techniques, such as exploiting vulnerabilities in the software supply chain, to maximize their returns.
Recent High-Profile Examples
One of the highest profile cases of double extortion arrived in May 2021 with the attack on the Colonial Pipeline, which at the time carried 45% of the supply of gasoline and jet fuel for the US East Coast. Attackers from the ransomware family DarkSide stole 100 GB of data, forcing the Colonial Pipeline company to pay an estimated $5 million in bitcoin to regain control and restore services.
Around the same time, attackers from the Russian-based Conti ransomware gang hit Ireland’s Health Service Executive system and demanded a $20 million ransom for the return of patient data. Later that same month, JBS S.A., the world’s largest meat producer, was forced to temporarily shut down operations when ransomware group REvil infiltrated its network, exfiltrated its data, and held it hostage for an $11 million ransom in bitcoin.
Most Popular Double Extortion Ransomware
Since late 2019, the following ransomware families have been the most active in executing double extortion ransomware attacks. Several of these groups have disbanded and changed their names following high-profile attacks:
- DarkSide
- Egregor
- Conti
- DoppelPaymer / BitPaymer
- REvil / Sodinokibi
- Avaddon
- Ragnar Locker
- Maze
How to Prevent Double Extortion Ransomware Attacks
Double extortion ransomware attacks are insidious and costly. Attacks have increased dramatically in part because companies have been willing to give in to ransom demands as criminals have gotten more persistent and aggressive. However, there are still steps you can take to protect your company and its information.
Adopt a Zero Trust Security Policy
A key defense against a cybercriminal accessing your network, especially in light of the steady increase of processing in the cloud, is to adopt a policy of zero trust, or least-privileged access. Zero trust means that no user or application should be inherently trusted. Rather, everything is assumed to be hostile until it has been authenticated and authorized. Access is granted based on user identity and context, and even then, only to a minimal set of resources.
A zero trust architecture for ransomware defense relies on three principles:
- Minimize the attack surface: Make users and applications invisible to the internet by securing access behind a proxy-based brokered exchange. If applications can’t be discovered, there’s no attack surface to exploit.
- Eliminate lateral movement: Hackers can only encrypt or steal data they can see. Microsegmentation techniques reduce data exposure and therefore minimize damage. In an ideal zero trust deployment, organizations use a proxy-based architecture to connect authenticated users directly to applications without ever exposing the network. Organizations may also deploy deception technologies to lure and expose attackers.
- Fully inspect for effective threat and data loss prevention: Inspect all traffic, both encrypted and unencrypted, entering and leaving your organization. This eliminates blind spots and maximizes your chances of keeping attackers out and sensitive data in.
Tips to Stay Protected from Double Extortion Ransomware
In addition to adopting a zero trust philosophy, cybersecurity teams should implement these policies to further reduce the attack surface and mitigate the ransomware threat:
- Enforce a consistent security policy to prevent initial compromise. With a distributed workforce, it's important to implement a secure access service edge (SASE) architecture that provides authentication and enforces consistent security policy no matter where users are working.
- Deploy inline data loss prevention. Prevent exfiltration of sensitive information and keep data leak sites to a minimum with trust-based data loss prevention tools and policies to thwart double extortion techniques.
- Keep software and training up to date. Apply software security patches and conduct regular security awareness employee training to reduce vulnerabilities that can be exploited by cybercriminals.
- Have a response plan. Prepare for the worst with cyber insurance, a data backup plan, and a response plan as part of your overall business continuity and disaster recovery program.
The Zscaler Zero Trust Exchange
Zscaler has the industry’s most comprehensive ransomware protection for your network and cloud, with protections across the ransomware attack sequence, including initial compromise, lateral movement, and data exfiltration.
Zscaler monitors 400 billion transactions per day during peak periods across its global platform, blocking threats and sharing threat intelligence with customers around the world to facilitate zero trust security. We partner with leading security providers to ensure you have coordinated visibility and response capabilities across your entire security ecosystem.