/ What Is a Software-Defined Perimeter?
What Is a Software-Defined Perimeter?

How Did the SDP Come to Be?
First conceptualized by the Defense Information Systems Agency (DISA) in 2007, SDPs are built on a need-to-know model with trust that is constantly monitored and adapted based on a range of criteria. They make application infrastructure invisible to the internet, reducing the attack surface from network-based attacks (DDoS, ransomware, malware, server scanning, etc.).
The Cloud Security Alliance (CSA) took interest in the concept and began developing the SDP framework in its early stages. In 2011, while SDP was still a new concept, Google became an early adopter with the development of its own SDP solution, Google BeyondCorp. Today, organizations adopting SDP are modernizing their endpoint, cloud, and application security—especially amid the shift to work-from-anywhere.
What Is the Purpose of SDP?
In today’s hybrid world, a traditional hardware-defined network perimeter designed for a corporate office is no longer viable. An SDP not only reduces the risk to endpoints that connect from anywhere, but also—with the help of an SDP controller—distributes network resources more evenly. Because these resources are defined on an individual basis, access control is centralized as well as simplified, ensuring secure access throughout your entire organization.
The internet has become the enterprise network, and on-premises solutions can’t establish secure network connections—especially with the advent of BYOD—leaving the door open for hackers and unauthorized users. A properly implemented SDP model grants users access based on the principle of least privilege, similar to microsegmentation. This makes it more difficult for bad actors who have gained network access to move laterally.
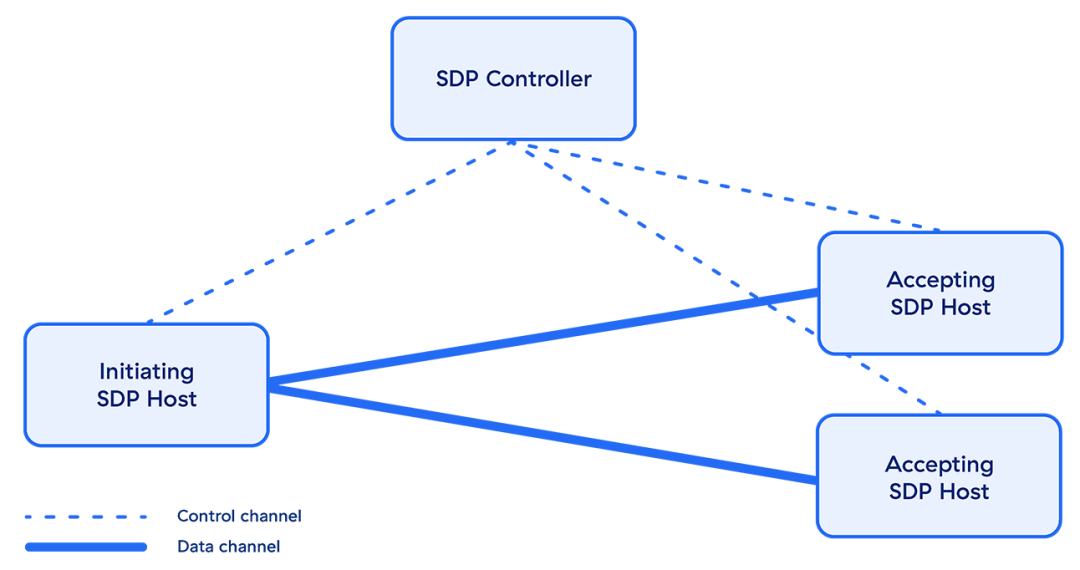
How Does SDP Work?
SDP takes a different approach compared to traditional network-based security. Instead of focusing on securing the network, SDP focuses on securing the user, the application, and the connectivity in between. Four core principles differentiate SDP technologies:
- Trust is never implicit: Traditional network security offers users excessive trust. With an SDP, trust must be earned. Namely, SDPs only grant application access to users who are authenticated and specifically authorized to use that app. Furthermore, authorized users are only granted access to the application, not the network.
- No inbound connections: Unlike a virtual private network (VPN), which listens for inbound connections, SDPs receive no inbound connections. By responding with outbound-only connections, SDPs keep network and application infrastructure invisible or cloaked to the internet and therefore impossible to attack.
- Application segmentation, not network segmentation: In the past, organizations had to perform complex network segmentation to prevent a user (or an infection) from moving laterally across the network. This worked well enough, but it was never granular and required constant maintenance. SDP provides native application segmentation that can control access down to a one-to-one basis, resulting in far more granular segmentation that’s much easier for your IT team to manage.
- Secure internet leverage: With users everywhere and applications moving outside your data center, your organization needs to shift away from a network-centric focus. You need to shift security to where your users are, and this means leveraging the internet as your new corporate network. SDP is focused on securing user-to-application connections over the internet rather than securing users’ access to your network.
From an architectural standpoint, SDP differs fundamentally from network-centric solutions. SDPs eliminate the enterprise overhead of deploying and managing appliances. Adopting an SDP architecture also simplifies your inbound stack by cutting reliance on VPNs, DDoS protection, global load balancing, and firewall appliances.
SDP Use Cases
While SDP has many use cases, many organizations choose to start in one of the following four areas:
Finding a VPN Alternative
Organizations are looking to reduce or eliminate usage of VPNs because they hamper user experience, introduce security risk, and are difficult to manage. SDPs directly address these notorious VPN issues by improving remote access capability. In fact, Cybersecurity Insiders says that 41% of organizations are looking to reevaluate their secure access infrastructure and consider SDP, with the majority of those requiring a hybrid IT deployment and a quarter implementing SaaS.
Securing Multicloud Access
Many organizations leverage a multicloud model by, for example, combining Workday and Microsoft 365 as well as infrastructure services from AWS and Azure. They may also use a cloud platform for development, cloud storage, and more. The need to secure these environments leads organizations to SDP because of their ability to secure connections based on policy, no matter where users connect from or where applications are hosted.
Reducing Third-Party Risk
Most third-party users receive overprivileged access, which creates a security gap for the enterprise. SDPs significantly reduce third-party risk by ensuring external users never gain access to the network and that authorized users only have access to applications they’re permitted to use.
Accelerating M&A Integration
With traditional mergers and acquisitions, IT integration can span years as organizations converge networks and deal with overlapping IP addresses—incredibly complex processes. An SDP simplifies the process, slashing the time required to ensure a successful M&A and providing immediate value to the business.
SDP and Zero Trust Network Access (ZTNA)
The ZTNA model has become a well-known security framework, but many people don’t realize that it was based on the same principles as SDP. In fact, ZTNA uses SDP principles and functionality. With both methods, there’s no internal network, and users are only allowed to access resources if the context behind the request (user, device, identity, etc.) is correct.
To help organizations achieve such a high level of security, vendors are promising a ZTNA framework that can keep your organization’s resources secure. But many of these frameworks are simply a cloud security platform force-fit on top of legacy appliances—or worse, they’re designed by networking vendors who glue on a security module in an effort to enter the security space.
These platforms don’t offer the scalability, flexibility, and—above all—security that a platform built in the cloud, for the cloud, can offer.
Zscaler, SDP, and ZTNA
The Zscaler Zero Trust Exchange™ includes Zscaler Private Access™ (ZPA), the industry’s only next-generation SDP/ZTNA platform. ZPA redefines private app connectivity and security for today’s hybrid workforce by applying the principles of least-privilege, which gives users secure, direct connectivity to private applications running on-premises or in the public cloud while eliminating unauthorized access and lateral movement.
Zscaler Private Access gives your organization the power to:
- Boost hybrid workforce productivity with fast, seamless access to private apps whether your users are at home, in the office, or anywhere else
- Mitigate the risk of a data breaches by making applications invisible to attackers while enforcing least-privileged access, effectively minimizing your attack surface and eliminating lateral movement
- Stop the most advanced adversaries with first-of-its-kind private app protection that minimizes the risk of compromised users and active attackers
- Extend zero trust security across apps, workloads, and IoT with the world’s most complete ZTNA platform that brings least-privileged access to private apps, workloads, and OT/IIoT devices
- Reduce operational complexity with a cloud native platform that eliminates legacy VPNs that are difficult to scale, manage, and configure in a cloud-first world



