/ What Is Deception Technology?
What Is Deception Technology?
Why Is Deception Technology Important?
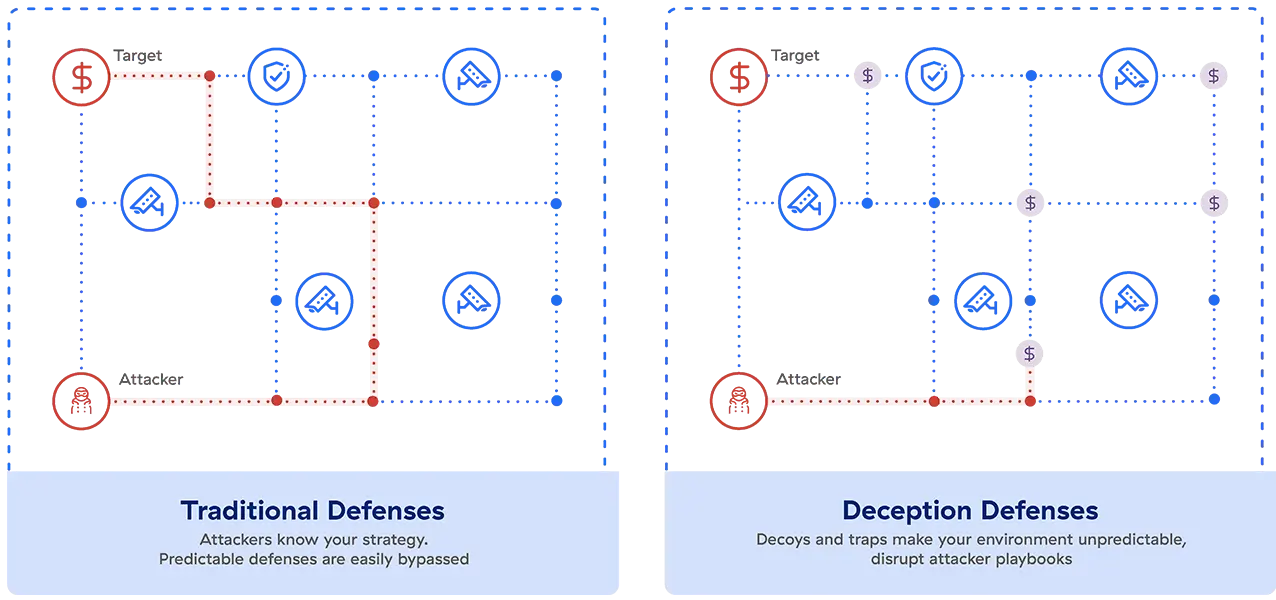
No matter how good your perimeter defenses are, there is always a chance cybercriminals will infiltrate your network. Deception technology will make them waste their time exploring worthless planted assets while you bait them into a trap. Once they reveal their presence, you get an early indicator of their behavior and can gain intelligence to use against them.
Modern-day deception technology defenses borrow heavily from military deception principles employed by the likes of Chanakya, Sun Tzu, Napoleon, and Genghis Khan to conquer continents through deceit, camouflage, and subterfuge. In the context of cybersecurity, defenders use decoys and lures to mislead attackers into believing they have a foothold in the network and revealing themselves.
Benefits of Deception Technology
Overall, the biggest benefit of deception is that it puts the burden of success on the attacker instead of the defender. Once you've populated your network with decoys, adversaries need to carry out a flawless attack, without falling for a single fake asset, misdirect, or trap, to succeed. You win if they make any mistakes.
Let's look at five concrete benefits of deception that make this possible.
1. Improved Threat Detection
If you place detection classes on a scale of accuracy, there are two extremes:
- Signature-based detection, which is highly accurate but very threat-specific
- Behavior analysis/heuristics, which have broad threat coverage, but are prone to false positives
Deception alerts are the best of both worlds: highly accurate with broad threat coverage.
2. Business Risk Awareness
Most security controls don't account for current business risks—your antivirus doesn't know you’re going through a merger. Deception, however, can be intrinsically aligned with them. For example, if you're launching a new product, you can create deception measures around that launch, aligning security controls tightly to areas where you perceive risk.
3. Greater Coverage
Deception can be applied broadly across your organization, including in environments that are often blind spots. Deception can detect threats at the perimeter, on endpoints, in the network, in Active Directory, and throughout application layers, as well as cover often neglected environments like SCADA/ICS, IoT, and the cloud.
Unlike point solutions, deception also covers the entire kill chain, from pre-attack reconnaissance to exploitation, privilege escalation, lateral movement, and data loss.
4. Extremely Low False Positives
False positives can leave any security team exhausted. Deception inherently produces very few—nobody but an attacker should have any reason to interact with a decoy. Beyond that, the alerts provide context around an attacker’s intent.
Most behavior analysis uses machine learning to flag anomalies from a baseline, which tends to create false positives. Deception establishes a zero-activity baseline (so any activity at all warrants investigation) and gives detailed indicators of compromise.
5. Orchestrated Response
Orchestrated/Automated response is most useful when the trigger event is 100% certain. Even then, such alerts don’t usually need orchestration because the products that generate them already handle remediation (e.g., antivirus quarantine).
Deception alerts are highly certain and contextual, so you can orchestrate more complex scenarios (e.g., decoy credentials redirect to a decoy environment and are blocked in the real environment) or target specific applications (e.g., an account accessing a decoy SWIFT banking server gets blocked in the real SWIFT server).
How Deception Technology Works
Modern deception technology uses active defense techniques to make your network a hostile environment for attackers. Similar to honeypots (more on these shortly), today's deception technology populates your network with fake resources that look like production assets, but that no legitimate user ever needs to access. Then, it leverages deception-based alerts to detect malicious activity, generate threat intelligence, stop lateral movement, and orchestrate threat response and containment, all without human supervision.
Modern deception platforms follow a proactive, low false-positive detection model. Deep analytics target the human intent behind an attack, adapting to new threats before they occur, and delivering orchestration and automation of response actions. Since deception defenses don't depend on signatures or heuristics for detection, they can cover virtually any attack vector and detect virtually any attack—including advanced persistent threats (APTs), zero-day threats, reconnaissance, lateral movement, fileless attacks, social engineering, man-in-the-middle attacks, and ransomware—in real time.
Once you've identified an attacker on your network, you can manipulate the deception environment in real time based on your knowledge of the attack. Here are some possible situations:
- Manipulate the attacker by generating or removing deceptive assets.
- Generate network traffic, alerts, or error messages to encourage specific attacker behavior.
- Implement session hijacking tools to cloud or distort attacker perceptions of the environment.
- Create situations that force an attacker to disclose information about who they are and where they come from to circumvent perceived obstacles.
Deception does more than make cyberattackers jump through extra hoops. It takes advantage of the fact that most attackers don't know everything about the environment they're trying to infiltrate and therefore can't tell what's real. This fundamentally reverses the power dynamics between attackers and defenders, giving you concrete perspective on what bad actors want, why they want it, and how they plan to get it.
Modern Deception Technology vs. Honeypots
The first tool of information security deception, the honeypot, appeared several decades ago and is still in use today. Honeypots are unprotected but monitored assets designed to attract attackers who have breached a network. Once the honeypot is accessed, security operations teams can act to gain intelligence on the attacker or shut the attack down.
Older deception technologies like honeypots, honey credentials, and such are essentially reactive, static techniques. They can fall out of date quickly and can't keep up with changing attacker tactics, making it easier for attackers to evade detection and dwell in the network. Honeypots and honeynets accessible to the internet can result in many false positives if the technology can't differentiate between broad scanning activities and targeted reconnaissance.
Challenges of Legacy Detection Technology
Cyber deception methods operate on the assumption that an attacker has already circumvented your perimeter cybersecurity and accessed your network, endpoints, operating systems, and applications. Other threat detection methods are designed to alert security teams to threats, but fall short against today’s sophisticated attacks.
Legacy detection tools such as firewalls and endpoint detection, each designed for a specific type of security (network, application, endpoint, IoT devices, etc.), often work in isolation from each other. This presents several problems:
- Low-fidelity alerts because these tools can only see their specific slice of the security infrastructure without context.
- Longer investigation time as security analysts must pivot between multiple tools to uncover the attack sequence and scope of damage.
- High false positive rates, causing alert fatigue. A 2021 survey by ESG found that 45% of alerts from respondents' web application and API security tools were false positives.
Additionally, many existing detection technologies fare much better against malware than against human-driven attacks, be they external or insider threats. Advanced malicious actors, much more sophisticated than petty hackers, are adept at imitating legitimate users' behaviors to stay undetected. When facing deception platforms, however, these actors reveal themselves as soon as they interact with a decoy.
Deception Use Cases
What Types of Threats Can Deception Technology Detect?
You can use deception technology to detect threats across the kill chain, from reconnaissance through data theft. There are three broad categories of use case:
- Perimeter deception defense: It’s usually not feasible to monitor all incoming traffic for potential threats. Setting up deceptive public-facing assets can simplify this problem and give you actionable intel on who is targeting you.
- Network deception defense: Planting decoys in places an attacker might peruse, but that legitimate users would never need to access, can identify an attack in progress.
- Endpoint deception defense: To an attacker, endpoint decoys look like valuable assets ripe for exfiltration. Monitoring these assets can detect suspicious behavior as well as behavior that would be the norm on the network but has no legitimate place on a particular endpoint at a particular time.
Should Your Organization Use Deception?
Until more recently, the industry widely assumed that deception was mainly useful for organizations with highly mature cybersecurity functions. However, mid-market and smaller organizations can see major benefits from the technology, too. Deception is becoming a mainstream capability across all shapes and sizes.
Large, Mature Organizations
Forward-leaning, big-budget organizations with well-developed security functions use deception to optimize their threat detection, internal threat intelligence creation, and response capabilities.
These organizations look to detect more advanced threats with deception and leverage low false-positive alerts for proactive threat hunting or integrated response through their existing enforcement technologies. This market segment has led the way for deception being more broadly adopted.
Mid-Market and Smaller Organizations
Mid-market CISOs and lean security teams at smaller organizations work with smaller budgets but still often deal with big threats and risk, such as compliance concerns. These organizations may have at least basic security hygiene established, but they need to be able to detect more serious threats. They need something that is:
- Fast to spin up, offering a quick win today
- Easy to use and low-maintenance, suited to a small internal security team
- Not a point solution, since there's too little budget for multiple technologies
- Equipped for wide coverage, including areas like the cloud and IoT
Deception checks all these boxes, letting these organizations hold their own against more advanced, targeted threats.
Zscaler: Deception with a Zero Trust Architecture
No one cybersecurity technique or policy is 100% effective at stopping attackers. For maximum protection, you need multiple technologies that work together and share information. The idea is to minimize your attack surface and speed up your ability to remediate incidents.
One of the most powerful combinations is the integration of deception technology with zero trust security. Zero trust assumes that every access or user request is hostile until both the user's identity and the context of the request are authenticated and authorized, granting access only to the minimum required resources—a concept known as "least privilege access."
Deception decoys act as tripwires in a zero trust environment, detecting compromised users or lateral movement across the network. Any lateral movement is tracked in a secure, isolated environment, alerting you to which type of asset the attacker is interested in, slowing them down, and allowing security teams to monitor their tactics, techniques, and procedures (TTPs).
Zscaler Deception integrates deception with zero trust, tracking the full attack sequence and initiating automated response actions across the Zscaler Zero Trust Exchange platform.
Active Defense with the MITRE Engage Framework
MITRE Engage is a trusted industry framework for discussing and planning adversary engagement, deception, and denial activities based on adversary behavior observed in the real world. MITRE's matrix serves as an objective and leading-edge guide to how your organization can best deploy deception and adversary engagement tactics as part of your overall zero trust security strategy.
Zscaler is proud to partner with MITRE on the Engage framework. Click here to learn more.



