Empower your organization with a zero trust architecture
Secure
Minimize business risk with protection against cyberthreats and data loss.
Simplify
Lower costs and complexity by eliminating point solutions and reducing overhead.
Transform
Increase business agility with cloud native zero trust networking for users, workloads, and branches.
Architecture Matters
The business world has changed
Traditional network and security models were built for a time before today’s revolutionary technologies. The below tools drive digital transformation and enable organizations to become more agile and competitive, but they call for a new approach to networking and security.
Mobility
Cloud
IoT/OT
AI/ML
Digital transformation requires a zero trust architecture

Traditional network and firewall architectures impede transformation
A trusted network connects users, sites, and apps, and is defended by a security perimeter. Trying to accommodate cloud services and other trends by extending the network perimeter to them is risky, expensive, and harms user experiences.
Zero trust architecture enables transformation
Zero trust means retiring network-centric approaches. A purpose-built cloud serves as an intelligent switchboard that uses business policies to determine who can access what—anywhere and over any network. This approach is more secure, saves money, and improves user experiences.
The Problem
Firewall and VPN architectures increase risk
Organizations worldwide have spent billions on firewalls and VPNs, yet breaches are increasing. The problem is simple: trying to protect a hub-and-spoke network with perimeter-based security tools fails to stop breaches across all four stages of the attack chain.

Attackers find you
All IPs are vulnerable—even those of firewalls, which are supposed to protect you.
They compromise you
Attackers exploit vulnerabilities to establish a beachhead in your network.
They move laterally
One infected machine compromises your entire network.
They steal your data
Sensitive data across applications, servers, and entire networks is lost.
Platform Overview
The Zscaler Zero Trust Exchange™ is a comprehensive, integrated platform that enables zero trust security and network transformation for all users, workloads, IoT/OT, and B2B partners.
Based on the zero trust principle of least-privileged access, our unique proxy architecture enables full TLS/SSL inspection at scale. One-to-one connections are brokered between users and applications based on identity, context, and business policies.
Benefits
Reduce risk across all four stages of the attack chain
Minimize the attack surface
Hide applications behind the Zero Trust Exchange, making them invisible to the internet.
Prevent compromise
Inspect all traffic, including encrypted traffic, and block threats in real time.
Eliminate lateral movement
Connect authorized entities (such as users) directly to apps, not to the network.
Stop data loss
Automatically identify and protect sensitive data in motion, at rest, and in use.
Our Zero Trust Approach
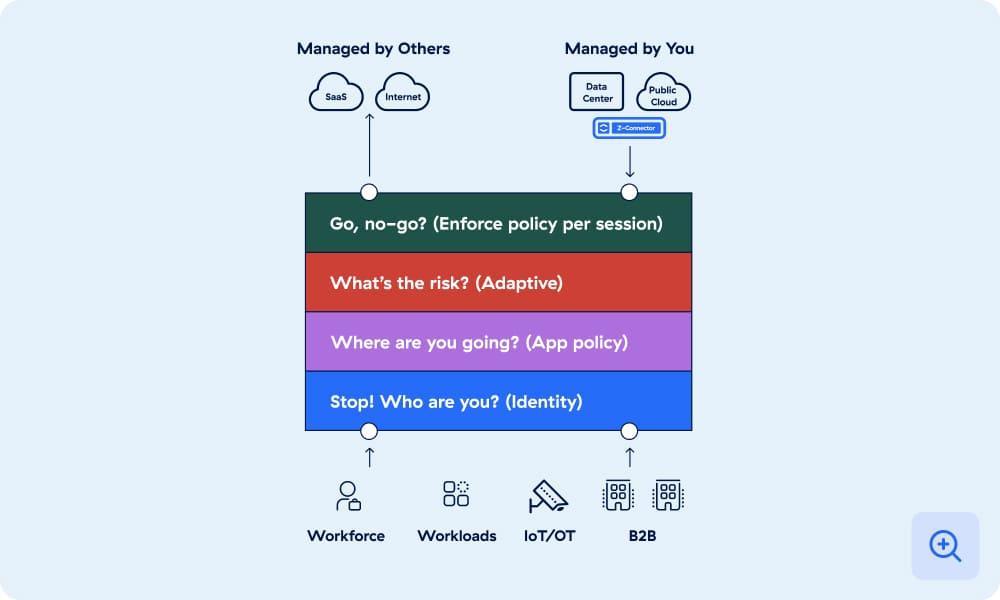
Verify identity
Verify whoever or whatever is attempting to gain access. The platform confirms user, device, or workload identity through integrations with third-party identity providers.

Determine destination
Identify where the connection is going—to a webpage, SaaS app, private app, or anywhere else—and ensure the destination is known and understood.

Assess risk
Use AI to determine risk based on context, considering factors like user behavior, device posture, destination and content, third-party intel, and more than 500 trillion daily signals.
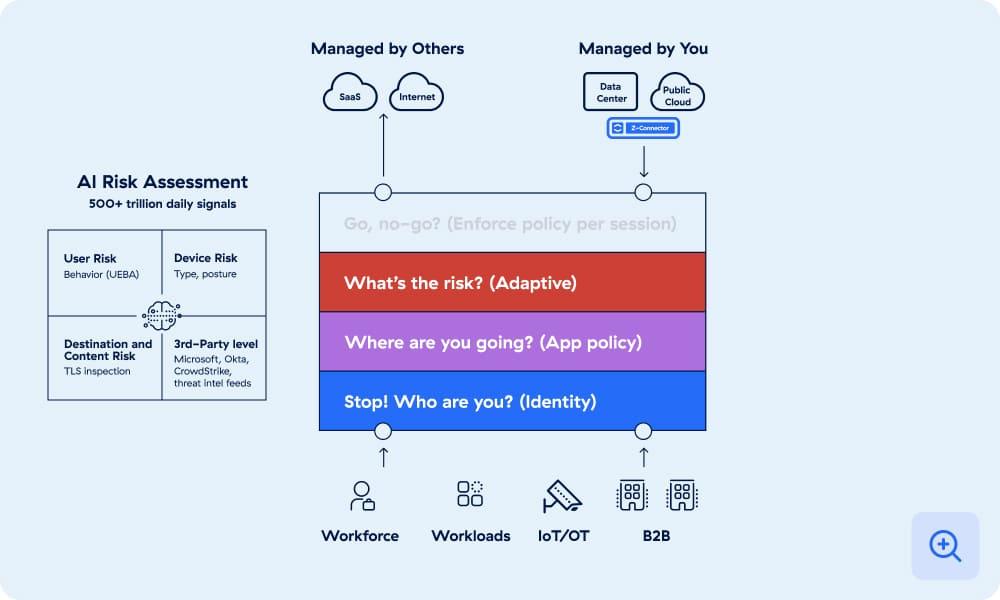
Enforce policy
Determine whether to grant access, block it, isolate, deceive, or do something else. The platform enforces policy in real time, on a per-session basis for each request.
“Zero Trust, from Theory to Practice” three-part webinar series
Master the zero trust model and become a zero trust ambassador at your organization.
Use cases
Secure every step of your transformation journey

Empower your people with fast, secure, and reliable access to the internet, SaaS, and private apps.

Secure your workload communications and protect data at rest within your clouds/SaaS apps.

Gain IoT device discovery, zero trust connectivity for IoT/OT, and privileged remote access to OT.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
Zero Trust + AI
Leadership and advantage in AI
The Zero Trust Exchange uses AI/ML to deliver the most effective cyberthreat and data protection, along with automation and productivity gains.

Recognition
The universally recognized leader in zero trust
500B+
160+ DCs
>70 NPS
9B+
500T+
400+
~45%
Leader
NASDAQ-100
Request a demo
Let our experts show you how the Zero Trust Exchange can empower your security strategy and transform the way you do business.














