Windows 8 is HOT!
Security researchers are busy finding Windows 8 vulnerabilities while users are figuring out how to find the restart button in the new interface UI.
Windows 8 is definitely one of the big targets for hackers in 2013 based on McAfee 2013 Threats Predictions report. Currently, more than 60% of malware samples are packed by PE packers. What is a packer? A packer is a type of archive tool that compresses and encrypts other executable files in a disk and restores the original executable images when the packed files are loaded into memory. However, we can’t jump to the conclusion that every packed file is malicious. Some commercial packer vendors offer packers to protect applications against Reverse Engineering (RE), by putting the content of those applications into a strong protection “shell”.
A packed file is a type of archived file, but packed and regular archives are quite different. Users have to extract an archived file onto a hard disk before they can access the contents. On the other hand, a PE packed file is normally unpacked in memory. There are many archived files, such as zipped files, in Windows OS folders. So how many of them are packed? In this post, I will share my findings on searching for packed files in the Windows 8 OS.
The tools I am using here are PEiD and ExeInfo, two popular packer detectors. 1,832 signatures were picked from PEiD v0.93, and 3,281 rules from ExeInfo. The packer signature database of PEiD is a subset of that of ExeInfo. I also removed some non-packer rules from ExeInfo. As usual, I chose REer's favorite folder, \Windows\System32, as the testing folder. First, I scanned that folder with PEiD, and received a couple of packer detection results. Among them, the signatures for "Armadillov1xxv2xx" and "Armadillov171" triggered false positives. Those signatures search for the following binary strings from OEP respectively. In this case, you can ignore them.
Armadillov1xxv2xx
55 8B EC 53 8B 5D 08 56 8B 75 0C 57 8B 7D 10 85 F6
Armadillov171
55 8B EC 6A FF 68 ?? ?? ?? ?? 68 ?? ?? ?? ?? 64 A1
I also found that ExeInfo itself was packed by the UPX packer.
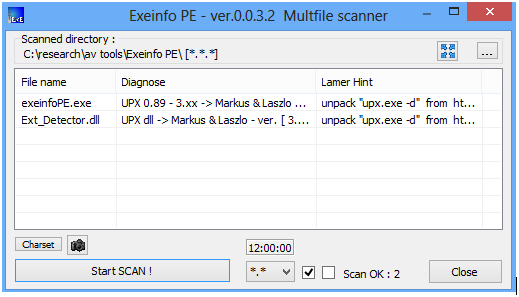
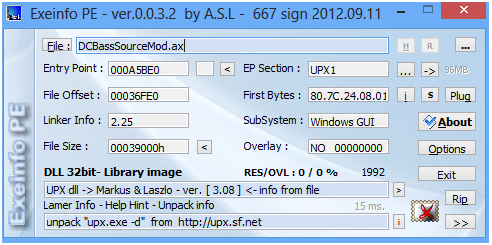
Here we identified the first low-hanging fruit: \system\SysWOW64\DCBassSourceMod.ax, which is an audio decoder file. It's section names show that it is UPX packed, but PEiD detected it as ACProtector packed. ExeInfo did a better job: it caught that file as UPX packed.
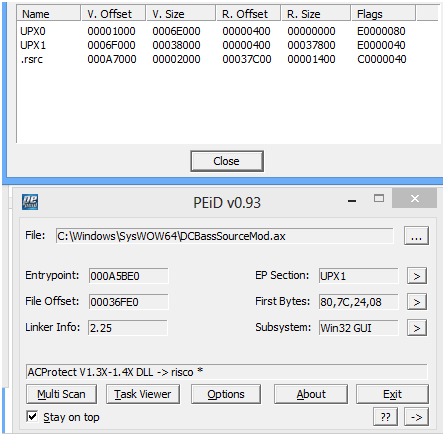
Next, the "Petitev14" signature detected quite a few files as Petite packer. They are all located in the \system32\SysWOW64 folder. Interestingly, most of their PE section names are empty. How odd!
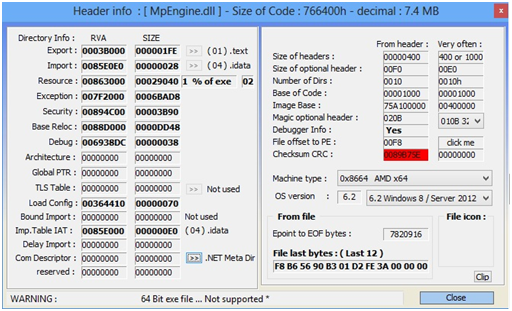
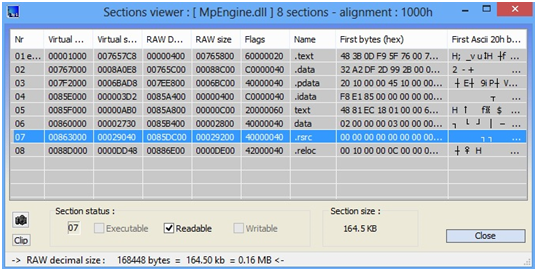
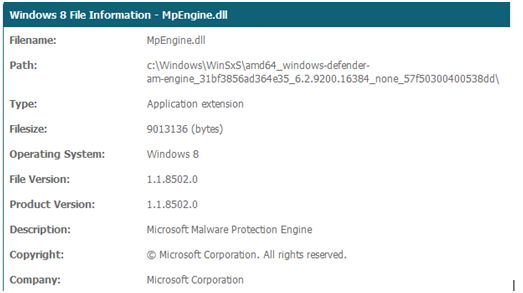
I saved the best to for last! Here comes Microsoft Malware Protection Engine (mpengine.dll)
The website shows thefiledb.com
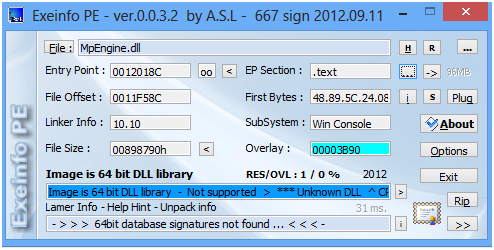
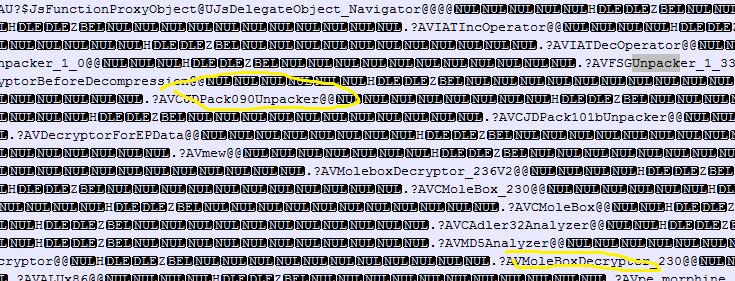
PEiD detected mpengine.dll as being packed with "nSpackV2xLiuXingPing" and ExeInfo failed on it. However, it appears to me that this file was maybe packed by a customized version of ACProtector (correct me if wrong). By extracting all strings from this file, you will have a big picture of how many packers MpEngine can handle with.
Last but not the least, a couple of additional files from different vendors are also packed. UPX is still one of the most popular packers.


Next, the "Petitev14" signature detected quite a few files as Petite packer. They are all located in the \system32\SysWOW64 folder. Interestingly, most of their PE section names are empty. How odd!

I saved the best to for last! Here comes Microsoft Malware Protection Engine (mpengine.dll)



The website shows thefiledb.com

PEiD detected mpengine.dll as being packed with "nSpackV2xLiuXingPing" and ExeInfo failed on it. However, it appears to me that this file was maybe packed by a customized version of ACProtector (correct me if wrong). By extracting all strings from this file, you will have a big picture of how many packers MpEngine can handle with.

Last but not the least, a couple of additional files from different vendors are also packed. UPX is still one of the most popular packers.
|
File name
|
Packer name
|
Vendor name
|
|
AdobeUpdateManager.exe
|
PECompact
|
Adobe
|
|
HD-adb
|
Generic packer
|
BlueStacks
|
|
Uninstall.exe
|
UPX
|
Intel
|
|
RedEye.dll
|
ASProtector
|
Lenovo
|
|
Sgtool.dll
|
UPX
|
Sougou input
|
|
DivFix++.exe
|
UPX
|
Win8codecs
|
|
Wincon.sfx
|
UPX
|
WinRAR
|





