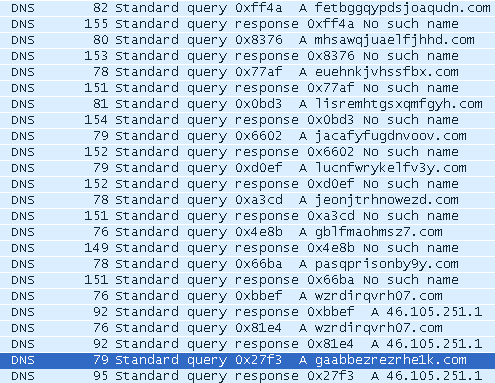
In our recent post covering CVE-2015-0311, two of the Command and Control (C&C) domains used in the Domain Generation Algorithm (DGA), mapped back to the same Server IP address - 46.105.251.1. They were also using the same nameservers for resolution:
To recap, we saw the initial binary was executed via the CVE-2015-0311 exploit, which then attempted resolution of multiple domains that were generated through a DGA:
Taking a closer look at these domains, we noticed that they share some commonalities, specifically their nameservers and IPs:
Taking a look at other domains registered around that time via "Domain Context" by 'yingw90@yahoo.com' and also utilizing "regway.com" for resolution, we find the following 39 domains:
aslfnsdifhsfdsa.com
avzxpjvrndi6g.com
bnxjgqotkqaftj.com
cavnplxhlwjzld.com
dtnvleoidsncuz7i.com
ggrdyqtlgdbpkkjf0e.com
gqzrdawmmvaalpevd0.com
grqtnsmqveprdc8f.com
jacafyfugdnvoov.com
jdioermutrealo.com
jxouhxclhzdlwa1d.com
jzkebkiznfttde.com
kdioqw873-kioas.com
koslnotreamouyer.com
krbewsoiitaciki2s.com
mcoihsopejaue.com
mlhxqydhcjqvei.com
nertafopadertam.com
noieutrabchpowewa.com
nwlxjqxstxclgngbw7.com
nyrtazolas.com
piragikolos.com
pndrdbgijushci.com
qhmbdzygdevxk0m.com
qvllupuqjknz5.com
roppsanaukpovtrwl.com
rwermezqpnf4.com
tuchrtwsabl7b.com
uowcvvknkrtipj.com
vsdylqjfrdqaxzyd.com
vucjunrhckgaiyae.com
vxmsrlsanrcilyb7o.com
vxuiweipowe92j.com
xgihfqovzurg8.com
xmoqu38hasdf0opw.com
xqirefjyjkcn7u.com
yoksfffhvizk8z.com
yyfaimjmocdu.com
zmbkfrdpnaec.com
Looking at the same time period for domains registered through "Domain Context", using "Privacy Protect", and using "regway.com" for resolution, we find an additional 32 domains, which also seem to fit the general theme of a DGA:
394iopwekmcopw.com
agdedopribili.com
asop83uyteramxop.com
balamodaevi.com
cawnqrvbmfgfysdb.com
deertraefople.com
gpsnypbnygqidxj.com
gurtgusinoi.com
gypqlkwgkmzapx33.com
iludyamdostaetsya.com
iqjlyjxplidpbbpuh.com
istinuskazat.com
itdlwcwonkhjrxlzuh.com
jddhbxrssjgqlsr.com
jyjhsvgkpeni0g.com
kbazarnomuondnu.com
kosnetsyanetolko.com
muzhikgusei.com
nabarishispeshil.com
neochenvezhlivo.com
predlinnoihvorostinoi.com
prodavatipravdu.com
retravopoytem.com
sokgtxioqzxvuksf1.com
tamgusyam.com
tuzlynlyvrbrdhrpx.com
vpsbxfdyphdykmlct.com
xnanomailing.com
yamuzhikainevenu.com
ytpliogapddu5.com
zhcjrjolbeuiylkyzx.com
zoidpyjhij36.com
The vast majority of these domains were resolving to Bedep's C&C servers. The following is a POST request to a C&C server from a Bedep infected system containing base64 encoded data:
However, some of the domains are being used in other seemingly unrelated malicious campaigns. For example the domain 'xmoqu38hasdf0opw.com' was identifed by Kafeine as hosting a Reveton ransom page.
Other domains being used to monetize Bedep infections via click fraud include:
394iopwekmcopw.com/ads.php
394iopwekmcopw.com/r.php?key=41c7eed67784325bb935f2b6543ff37d
asop83uyteramxop.com/ads.php?sid=1910
asop83uyteramxop.com/r.php?key=c8a0293dce08d582ca645449d849543d
koslnotreamouyer.com/ads.php?sid=1905
koslnotreamouyer.com/r.php?key=666fe962677224b1799919a70c7c2c9e
And the following domains are intermediaries hosting encrypted files:
kosnetsyanetolko.com/slwsbpetw.eqmh
kdioqw873-kioas.com/asdfsfsdf1.php
nertafopadertam.com/2/showthread.php
nyrtazolas.com/1/search.php
piragikolos.com/asdfsfsdf1.php
Unfortunately, there are several different IPs in use on various ASNs:
- ns1.regway.com
- ns2.regway.com
To recap, we saw the initial binary was executed via the CVE-2015-0311 exploit, which then attempted resolution of multiple domains that were generated through a DGA:
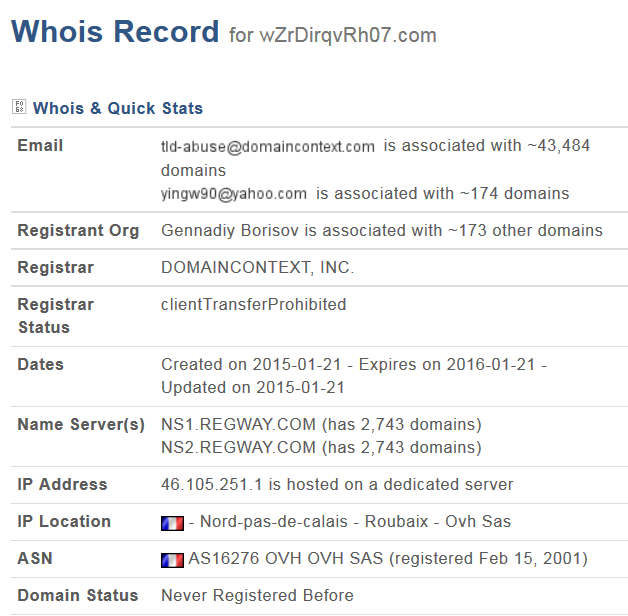
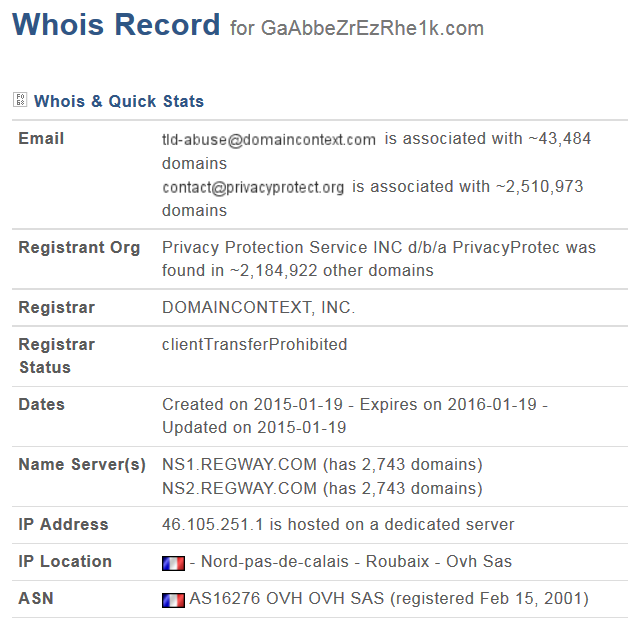
Below is partial whois information for the two domains that resolved at that time:
Taking a closer look at these domains, we noticed that they share some commonalities, specifically their nameservers and IPs:
| Domain | IP | Observed Method | Registrar | Creation Date | Contact | Nameserver(s) |
|---|---|---|---|---|---|---|
| gaabbezrezrhe1k.com | 46.105.251.1 | POST / | domaincontext | 2015-01-19 | contact @privacyprotect.org | ns1.regway.com, ns2.regway.com |
| wzrdirqvrh07.com | 46.105.251.1 | POST / | domaincontext | 2015-01-21 | yingw90 @yahoo.com | ns1.regway.com, ns2.regway.com |
Taking a look at other domains registered around that time via "Domain Context" by 'yingw90@yahoo.com' and also utilizing "regway.com" for resolution, we find the following 39 domains:
aslfnsdifhsfdsa.com
avzxpjvrndi6g.com
bnxjgqotkqaftj.com
cavnplxhlwjzld.com
dtnvleoidsncuz7i.com
ggrdyqtlgdbpkkjf0e.com
gqzrdawmmvaalpevd0.com
grqtnsmqveprdc8f.com
jacafyfugdnvoov.com
jdioermutrealo.com
jxouhxclhzdlwa1d.com
jzkebkiznfttde.com
kdioqw873-kioas.com
koslnotreamouyer.com
krbewsoiitaciki2s.com
mcoihsopejaue.com
mlhxqydhcjqvei.com
nertafopadertam.com
noieutrabchpowewa.com
nwlxjqxstxclgngbw7.com
nyrtazolas.com
piragikolos.com
pndrdbgijushci.com
qhmbdzygdevxk0m.com
qvllupuqjknz5.com
roppsanaukpovtrwl.com
rwermezqpnf4.com
tuchrtwsabl7b.com
uowcvvknkrtipj.com
vsdylqjfrdqaxzyd.com
vucjunrhckgaiyae.com
vxmsrlsanrcilyb7o.com
vxuiweipowe92j.com
xgihfqovzurg8.com
xmoqu38hasdf0opw.com
xqirefjyjkcn7u.com
yoksfffhvizk8z.com
yyfaimjmocdu.com
zmbkfrdpnaec.com
Looking at the same time period for domains registered through "Domain Context", using "Privacy Protect", and using "regway.com" for resolution, we find an additional 32 domains, which also seem to fit the general theme of a DGA:
394iopwekmcopw.com
agdedopribili.com
asop83uyteramxop.com
balamodaevi.com
cawnqrvbmfgfysdb.com
deertraefople.com
gpsnypbnygqidxj.com
gurtgusinoi.com
gypqlkwgkmzapx33.com
iludyamdostaetsya.com
iqjlyjxplidpbbpuh.com
istinuskazat.com
itdlwcwonkhjrxlzuh.com
jddhbxrssjgqlsr.com
jyjhsvgkpeni0g.com
kbazarnomuondnu.com
kosnetsyanetolko.com
muzhikgusei.com
nabarishispeshil.com
neochenvezhlivo.com
predlinnoihvorostinoi.com
prodavatipravdu.com
retravopoytem.com
sokgtxioqzxvuksf1.com
tamgusyam.com
tuzlynlyvrbrdhrpx.com
vpsbxfdyphdykmlct.com
xnanomailing.com
yamuzhikainevenu.com
ytpliogapddu5.com
zhcjrjolbeuiylkyzx.com
zoidpyjhij36.com
The vast majority of these domains were resolving to Bedep's C&C servers. The following is a POST request to a C&C server from a Bedep infected system containing base64 encoded data:
However, some of the domains are being used in other seemingly unrelated malicious campaigns. For example the domain 'xmoqu38hasdf0opw.com' was identifed by Kafeine as hosting a Reveton ransom page.
Other domains being used to monetize Bedep infections via click fraud include:
394iopwekmcopw.com/ads.php
394iopwekmcopw.com/r.php?key=41c7eed67784325bb935f2b6543ff37d
asop83uyteramxop.com/ads.php?sid=1910
asop83uyteramxop.com/r.php?key=c8a0293dce08d582ca645449d849543d
koslnotreamouyer.com/ads.php?sid=1905
koslnotreamouyer.com/r.php?key=666fe962677224b1799919a70c7c2c9e
And the following domains are intermediaries hosting encrypted files:
kosnetsyanetolko.com/slwsbpetw.eqmh
kdioqw873-kioas.com/asdfsfsdf1.php
nertafopadertam.com/2/showthread.php
nyrtazolas.com/1/search.php
piragikolos.com/asdfsfsdf1.php
Unfortunately, there are several different IPs in use on various ASNs:
| IP | Netblock | ASN |
|---|---|---|
| 46.105.251.1 | 46.105.0.0/16 OVH ISPOVH_65488197 OVH Static IP | AS16276 |
| 5.135.16.201 | 5.135.0.0/16AS16276FR-OVH-20120706 OVH SAS | AS16276 |
| 94.23.204.16 | 94.23.0.0/16 OVH ISPOVH OVH SAS Dedicated Servers | AS16276 |
| 5.196.196.149 | 5.196.196.0/22AS197890FR-OVH-20120823 OVH SAS | AS16276 |
| 46.105.251.0 | 46.105.0.0/16 OVH ISPOVH_65488197 OVH Static IP | AS16276 |
| 37.187.76.177 | 37.187.0.0/16 OVHOVH OVH SAS Dedicated servers | AS16276 |
| 206.222.13.164 | 206.222.0.0/19 RR-RC-Enet-ColumbusEE3-DOM | AS10297 |
| 23.105.135.219 | 23.105.128.0/1923.104.0.0/13Route for Nobis Technology Group, LLCNETBLK-NOBIS-TECHNOLOGY-GROUP-18 | AS15003 |
| 23.105.135.218 | 23.105.128.0/1923.104.0.0/13Route for Nobis Technology Group, LLCNETBLK-NOBIS-TECHNOLOGY-GROUP-18 | AS15003 |
| 151.80.95.8 | 151.80.0.0/16151.80.0.0/17 OVHIUNET-BNET80 OVH SAS | AS1267 |
| 80.82.70.104 | 80.82.70.0/24 AS29073 Route objectNL-ECATEL-20100816 Ecatel LTD | AS29073 |
| 79.143.82.203 | 79.143.80.0/22Redstation LimitedRSDEDI-KBPNNOIL Dedicated Server Hosting | AS35662 |
| 79.143.80.42 | 79.143.80.0/2279.143.80.0/24Proxy-registered route objectRSDEDI-IBOBAPEP Dedicated Server Hosting | AS35662 |
| 217.23.12.145 | 217.23.0.0/20WORLDSTREAM-BLK-217-23-0-0WORLDSTREAM WorldStream IPv4.19 | AS49981 |
| 173.224.126.29 | 173.224.112.0/20Hosting Solutions InternationalHSI-3 | AS30083 |
| 173.224.126.19 | 173.224.112.0/20Hosting Solutions InternationalHSI-3 | AS30083 |
| 50.30.36.1 | 50.30.32.0/20Hosting Solutions InternationalHSI-4 | AS30083 |
| 209.239.115.228 | 209.239.112.0/20209.239.115.0/24Proxy-registered routeHSI-2 | AS30083 |