Introduction
Zscaler ThreatLabZ recently came across a new wave of malicious documents evading automated analysis systems using a new technique. Malicious executables that leverage numerous techniques to detect the virtual environment and automated analysis systems are very common, but we are seeing an increasing trend of such techniques moving to the initial delivery vector (i.e. weaponized documents).
In this blog, we look at some of the anti-VM and anti-sandboxing techniques seen in the recent malicious documents including the newly added check of Microsoft Office RecentFiles count.
Weaponized Documents & anti-VM tricks
Malware authors leveraging documents with macros to download and install malware executable has been around for years; however, we are seeing a gradual evolution in these malicious documents making it harder for the security solutions to detect them proactively. ThreatLabZ has seen hundreds of new weaponized documents hit our sandbox on a regular basis:
Figure 1: New unique malicious documents
A macro is a piece of code, embedded inside Microsoft Office documents, written in a programming language known as Visual Basic for Applications (VBA). Microsoft Office's default security settings ensures that the macros are disabled by default; however, attackers are using clever social engineering tactics to lure the user into enabling the macros. Below are two recent examples:
Figure 2: Social engineering tactics to enable macro
Malware authors are also making the macro code highly obfuscated and difficult to detect by signature based systems. In addition to highly obfuscated macros, malware authors are using multiple techniques in macros to detect the virtual environment and automated analysis systems as seen below:
Check #1 - Look for standard virtual environment strings
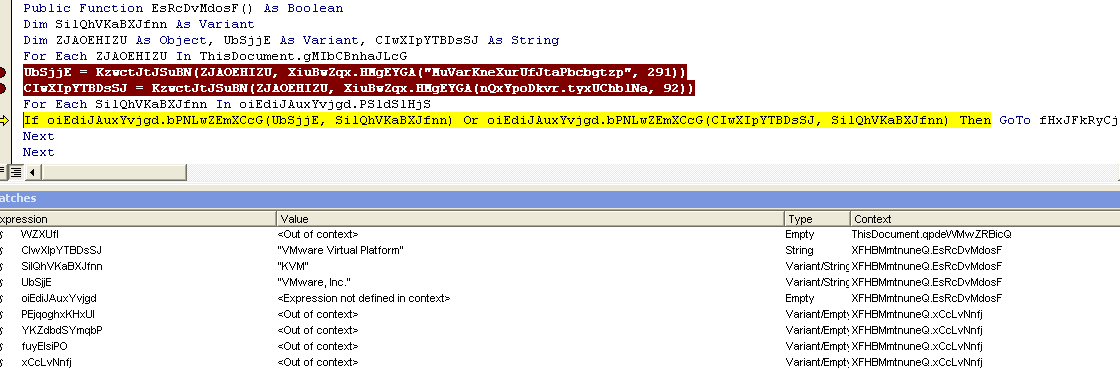
Figure 3: Virtual environment strings check
Check #2 - Windows Management Instrumentation (WMI) interface to identify virtual environment & automated analysis systems
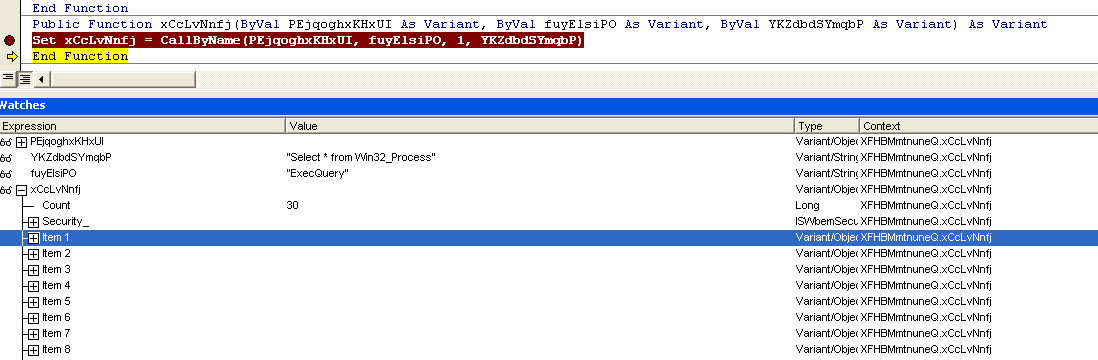
Figure 4: WMI interface to detect virtual environment & sandboxes
Check #3 - Look for presence of known analysis tools on the system
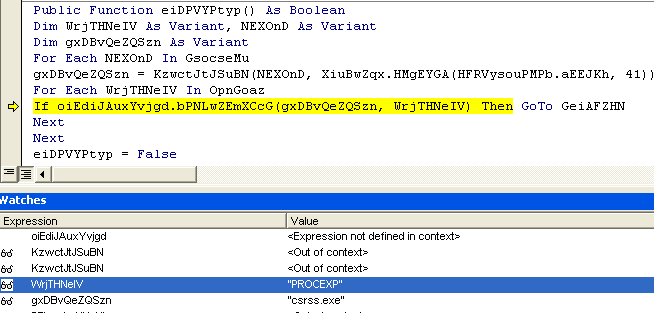
Figure 5: Check for malware analysis tools
If any of these anti-VM or anti-sandbox checks is positive then the VBA macro code execution terminates and the end malware payload does not get downloaded on the system shielding it from automated analysis and detection. Alternately, the malicious document will download and install a malware executable on the victim's system if all the anti-VM checks fail.
We have seen multiple malware families leveraging malicious documents as the initial delivery vector:
- Ransomware Trojans (e.g. CryptoWall, Locky, Cerber)
- Banking Trojans (e.g. Dridex)
- Backdoor Trojans (e.g. Matsnu, Kasidet)
- Infostealer Trojans (e.g. Fareit, VawTrak, Pony)
New anti-VM and anti-sandbox checks
In the last week of May, we started seeing a new wave of malicious documents leveraging two new techniques that prevents it from executing on many known sandbox solutions.
New Check #1 - Detect virtual environment via Office RecentFiles property
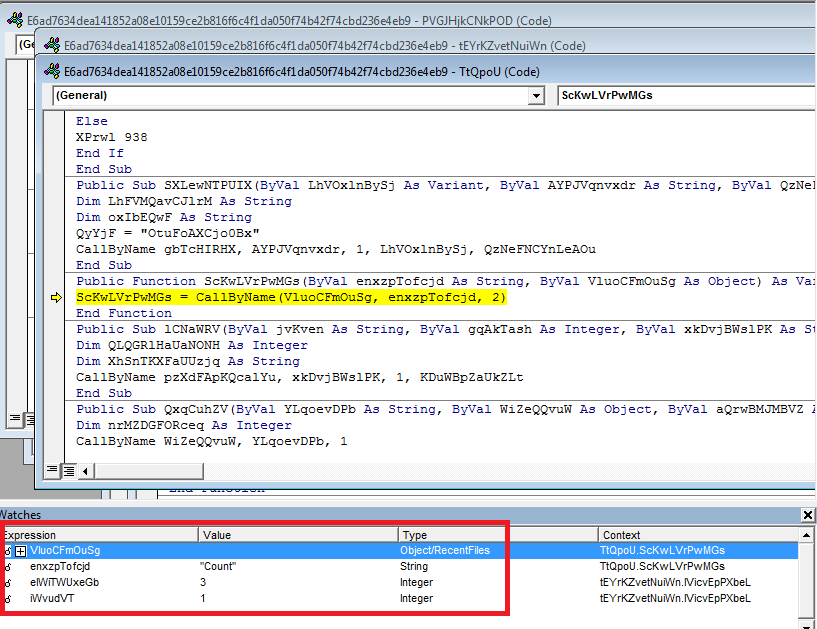
Figure 6: Microsoft Office RecentFiles property check
RecentFiles property returns a RecentFiles collection that represents the most recently accessed files. The macro code checks if the number of RecentFiles collection is less than a predefined threshold and terminates if true. Threshold value we have seen is 3 or higher.
The malware author makes an assumption here that most clean Virtual Environment snapshots will be taken after a fresh Microsoft Office install with probably one or two document files opened for testing the installation. Alternately, a standard user system with Office applications should have at least 3 or more recently accessed document files.
New Check #2 - Check for the external IP ownership
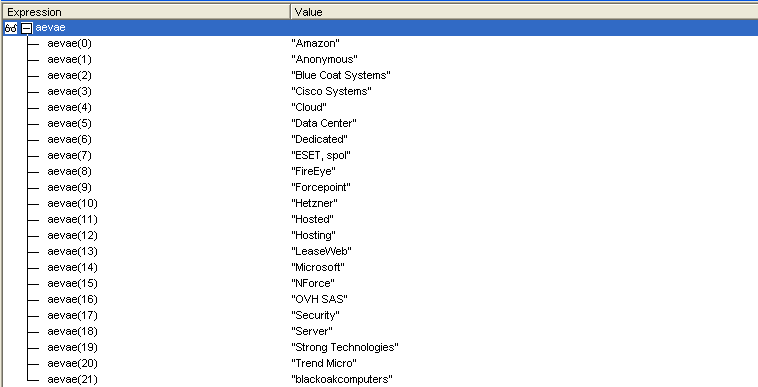
Figure 7: Check for security vendors, cloud & hosting services
Here the malware author is leveraging macro to get the external IP address of the victim's system by using the following maxmind GeoIP service API:
https://www.maxmind.com/geoip/v2.1/city/me
This API asks for user credentials but we did not see any hardcoded credential information being sent by the malicious document. The malware author is setting the UserAgent and Referer headers for this request to get the response without any authentication. We are still verifying if this is by design or if this is an authentication bypass issue for the API that is being exploited.
Figure 8: Maxmind API usage for external IP information
The response is then compared against a predetermined list of strings (Figure X) that includes multiple known security vendors & hosting services as well as generic strings to detect data centers, hosting services, cloud based security and hosting services ownership. The macro execution will terminate if maxmind's response for the external IP address matches any of these strings.
Upon successful checks, these new set of malicious documents were found to be downloading and installing Win32/Matsnu.Q Trojan from following URLs:
- arabtradenet[.]com/info/content.dat
- naivak[.]com/image/office14.ppb
Figure 9: Matsnu executable payload being downloaded
We also saw Nitol and Nymaim payloads subsequently being dropped by Matsnu Trojan.
Conclusion
Malicious documents with highly obfuscated macros have become an increasingly popular vector among cyber criminals to deliver malware executable payloads. By adding newer anti-VM and anti-analysis techniques to the malicious documents itself, the attackers are protecting the end executable payloads from being downloaded and detected by the automated analysis systems.
Zscaler ThreatLabZ will continue to monitor and ensure coverage against the evolving malicious document threat as well as subsequent malware executable payloads.
Research by: Deepen Desai, Nirmal Singh, Tarun Dewan











