Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Coverage Advisory for CVE-2023-50164: Apache Struts Path Traversal and File Upload Vulnerability
Introduction
On December 7, the Apache Software Foundation released Apache Struts versions 6.3.0.2 and 2.5.33 to address a critical vulnerability currently identified as CVE-2023-50164, which is a path traversal flaw allowing a malicious file to be uploaded and potentially lead to Remote Code Execution (RCE) on affected versions of Apache Struts.
Recommendations
Zscaler ThreatLabz recommends users on Apache Struts software upgrade to versions Struts 2.5.33, Struts 6.3.0.2, or higher to avoid this vulnerability.
Affected Versions
The following versions of Apache Struts are affected by the vulnerability and should update immediately:
- Struts 2.0.0 - Struts 2.3.37 (EOL)
- Struts 2.5.0 - Struts 2.5.32
- Struts 6.0.0 - Struts 6.3.0
Background
CVE-2023-50164 is a path traversal flaw that allows a remote attacker to upload malicious files to vulnerable servers. After successful exploitation, an attacker can achieve Remote Code Execution (RCE) on the target server. An attacker exploiting such a vulnerability can access, upload, or modify important files, steal sensitive information, disrupt critical services, or move laterally on the breached network.
CISA released an alert to upgrade to the latest version of Apache Struts for protection from this vulnerability.
According to the Shadowserver scanning platform, some threat actors may have started exploiting publicly exposed vulnerable Apache Struts servers. In addition, a post by Akamai indicates that attackers may be adding new arguments and modifying a publicly available Proof-of-Concept (PoC) to further exploit CVE-2023-50164.
How It Works
The attacker accesses a vulnerable version of Apache Struts to send an HTTP POST request to upload a malicious file.
In the POST request, the attacker uploads a file with malicious content using the 'Upload' parameter name (instead of 'upload'). Within the same request, the attacker adds another parameter named 'uploadFileName' (instead of 'UploadFileName').
The sample below is a condensed example of a request.
name="Upload"; filename="arbitrary.txt"
…
PK.........B.W............ ...META-INF/......PK..............PK.........B.W................META-INF/MANIFEST.MF.M..LK-..
K-*....R0.3..r.JM,IM.u..
....Y*h..&e&.i.r.r..PK.....97...6...PK.........8.W................webshell.jspmQ.N.0....c...5...1&.HL....4e`.Pj)....;.\Y...............tc[.3.&?e....A|.m..(............;.T.w...=:...D..n{o{O..M.......L_...Gx1..TJ.....m!v.U.u`.w.....V.+. .P....j:Ez.q..%:,.(.t..A..+..(7...C...
r.....?.t..yX...j*..!o....c~.
[email protected])........'.!..8..)..PK....=n........PK...........B.W............ .................META-INF/....PK...........B.W...97...6.................=...META-INF/MANIFEST.MFPK...........8.W..=n..........................webshell.jspPK....................
------WebKitFormBoundaryp72D9I30enbR6scA
Content-Disposition: form-data; name="uploadFileName"
../../opt/tomcat/webapps/webshell.war
------WebKitFormBoundaryp72D9I30enbR6scA--The 'uploadFileName' parameter contains path traversal characters (../), which manipulate the filename present in the ‘Upload’ parameter, allowing an attacker to bypass the built-in check – effectively evading the getCanonicalName method (a method used to truncate '/' & '\' characters in the filename) — and leave the path traversal payload in the final filename. From here, the file (with the malicious payload) is uploaded to the attacker’s chosen directory.
If the file contains WebShell code, the attacker can escalate access to the vulnerable server, leading to RCE and ultimately gaining access to the target server.
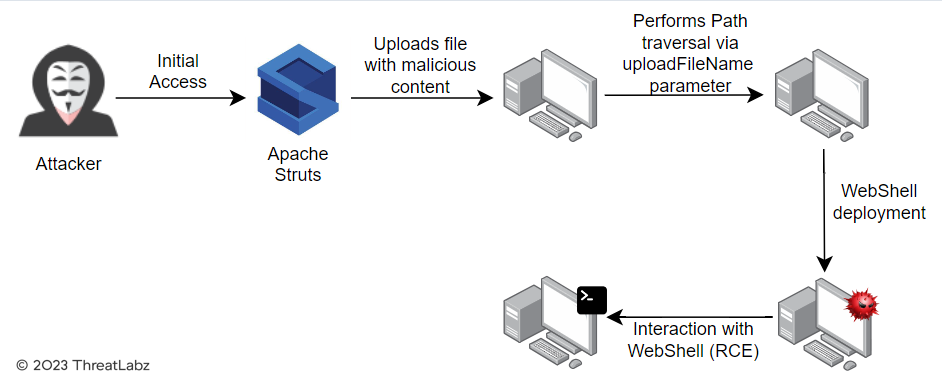
Figure 1: The attack chain depicting an attacker exploiting CVE-2023-50164.
Zscaler Best Practices
- Safeguard crown jewel applications by limiting lateral movement using Zscaler Private Access™ with application security modules turned on.
- Route all server traffic through Zscaler Private Access™ with additional application security module enabled and Zscaler Internet Access™, which provides visibility to identify and stop malicious activity from compromised systems/servers.
- Turn on Zscaler Advanced Threat Protection™ to block all known command-and-control domains — thereby adding another layer of protection if an attacker exploits this vulnerability to implant malware.
- Extend command-and-control (C2) protection to all ports and protocols with the Zscaler Cloud Firewall™ (Cloud IPS module), including emerging C2 destinations. Doing so provides additional protection if the attacker exploits this vulnerability to implant malware.
- Use Zscaler Cloud Sandbox™ to prevent unknown malware from being delivered as part of a second-stage payload.
- Inspect all TLS/SSL traffic and restrict traffic to the critical infrastructure from the allowed list of known-good destinations.
Conclusion
Addressing CVE-2023-50164 is crucial for protecting the digital security of Apache Struts systems and users. By manipulating file upload parameters, uploading malicious files, and achieving RCE on the target server, an attacker can take control — stealing sensitive information, leading to severe disruptions for impacted systems and users. To mitigate this risk, upgrade vulnerable Apache Struts software systems to Struts 2.5.33, Struts 6.3.0.2, or higher.
Zscaler Coverage
The Zscaler ThreatLabz team has deployed protection for the CVE.
Zscaler Advanced Threat Protection
- HTML.EXPLOIT.CVE-2023-50164
Zscaler Private Access AppProtection
- Local File Inclusion: 930100 - Path Traversal Attack (/../) - Encoded Payload
- Local File Inclusion: 930110 - Path Traversal Attack (/../) - Decoded Payload
Details related to these signatures can be found in the Zscaler Threat Library.
¿Este post ha sido útil?
Descargo de responsabilidad: Esta entrada de blog ha sido creada por Zscaler con fines únicamente informativos y se proporciona "tal cual" sin ninguna garantía de exactitud, integridad o fiabilidad. Zscaler no asume ninguna responsabilidad por cualquier error u omisión o por cualquier acción tomada en base a la información proporcionada. Cualquier sitio web de terceros o recursos vinculados en esta entrada del blog se proporcionan solo por conveniencia, y Zscaler no es responsable de su contenido o prácticas. Todo el contenido está sujeto a cambios sin previo aviso. Al acceder a este blog, usted acepta estos términos y reconoce su exclusiva responsabilidad de verificar y utilizar la información según convenga a sus necesidades.
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Al enviar el formulario, acepta nuestra política de privacidad.



