Ransomware is used widely in cyberattacks to disrupt the victim's organization. Over the last two years, many attackers have evolved their ransomware tactics to include data exfiltration. This tactic is known as "double-extortion": attackers demand ransom for the data decryption in addition to the ransom to prevent public release of the stolen data. ThreatLabz monitors these threat actors and analyzes the attack sequences of double extortion attacks. AtomSilo is a new player on the scene, and in this blog, we'll break down the details of their attacks.
Introduction
AtomSilo ransomware emerged around September 2021, with their tactics including exfiltrating and publishing their first victim's data.
We'll break down one of their attacks, which started with initial access through exploiting a vulnerability in Atlassian’s Confluence collaboration software. The ransomware operators planted a back door using legitimate software via a dll side loading technique. The backdoor allowed remote code execution of Windows Shell commands through WMI (Windows Management Interface), which operators exploited using compromised administrative accounts before dropping AtomSilo.
Technical Analysis
The AtomSilo payload is 64-bit and packed with a modified UPX packer. Once executed, it enumerates each drive and drops a ransom note in each folder except the few listed in Table1. The ransom note is named “README-FILE-{COMPUTER_Name}-{DateTime}.hta”.
Figure 1: AtomSilo ransom note
It enumerates each file and encrypts all folders and files EXCEPT those that contain the below names:
| Folder name | File name |
|---|---|
| Boot | autorun.inf |
| Windows | index.html |
| Windows.old | boot.ini |
| Tor Browser | bootfont.bin |
| Internet Explorer | bootsect.bak |
| bootmgr | |
| Opera | bootmgr.efi |
| Opera Software | bootmgfw.efi |
| Mozilla | desktop.ini |
| Mozilla Firefox | iconcache.db |
| $recycle.Bin | ntldr |
| ProgramData | ntuser.dat |
| All Users | ntuser.dat.log |
| #recycle | |
| thumbs.db | |
| ntuser.ini |
Table1: List of files and folders
It also does not encrypt files with the following extensions:
| .hta | .idx |
| .hlp | .ini |
| .html | .sys |
| .icl | .cab |
| .exe | .spl |
| .icns | .cur |
| .dll | .ocx |
| .ico | .cpl |
| .cpl | .drv |
Table2: List of extensions
File Encryption
Ransomware appends “.atomsilo” extensions to files after encryption. Ransomware uses “CreateFileMappingA” and “MapViewOfFile” APIs to map the file in memory and moves the pointer to the start of the mapped file. AtomSilo uses XOR and AES Encryption algorithms to encrypt files. It generates AES round keys using the “AESKEYGENASSIST” instruction as shown in the below figure.
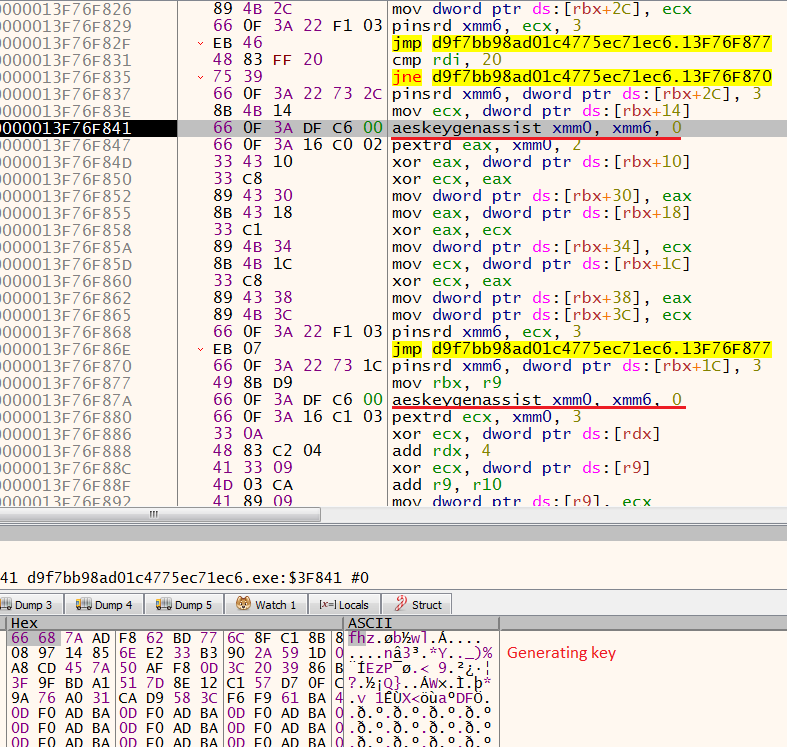
Figure 2: AtomSilo generates encryption keys using AESKEYGENASSIST
The encryption key is 240 bytes. The first 32 bytes are randomly generated by the payload, and other 208 bytes are generated using the “AESKEYGENASSIST” instruction. In the file , it takes 16 bytes of plain text and does XOR as a first stage encryption. Then, it encrypts it with 14 rounds of AES encryption. It uses “AESENC” instruction for the first 13 rounds and the last round uses “AESENCLAST” instruction.
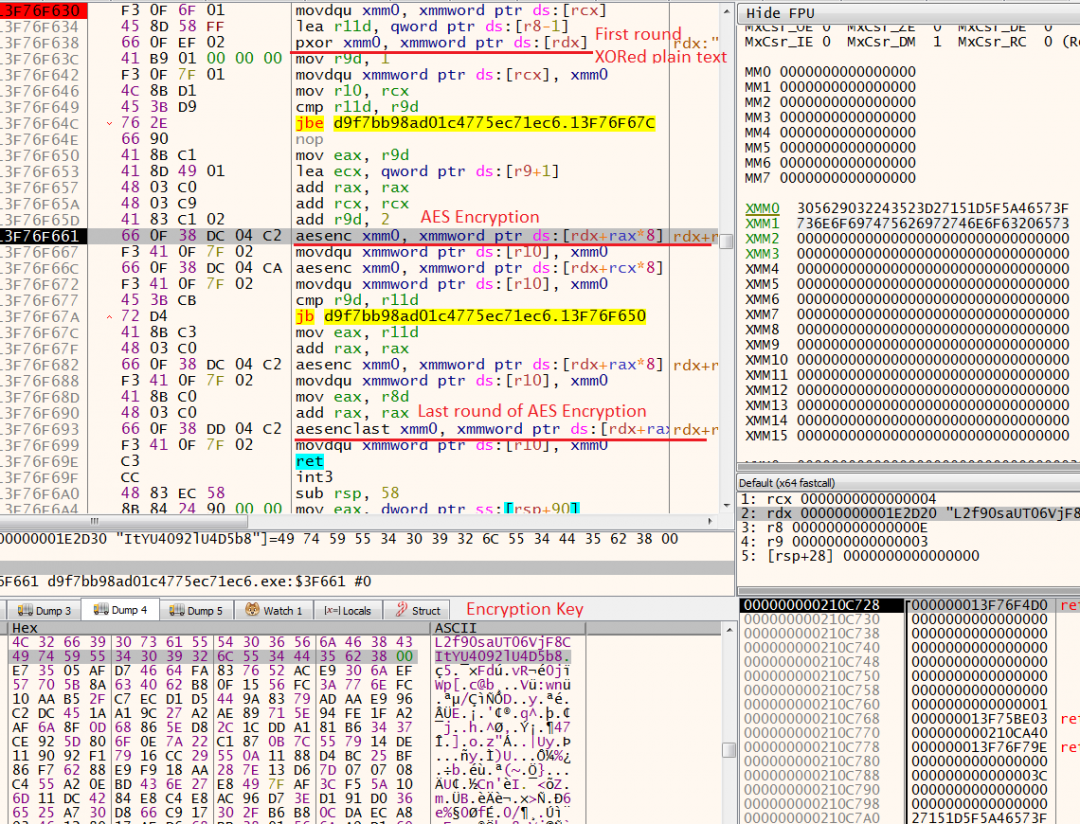
Figure 3: Encrypting data using AES algorithm
It encrypts chunks of the file, not the complete file. It encrypts the first 16 bytes, leaves the next 32 bytes as-is, encrypts the next 16 bytes, and so on. The below screenshot shows the comparison of the normal file and encrypted file, where we can see that chunks of files are not encrypted. The encryption key and other information are encrypted and appended at the end of the encrypted file.
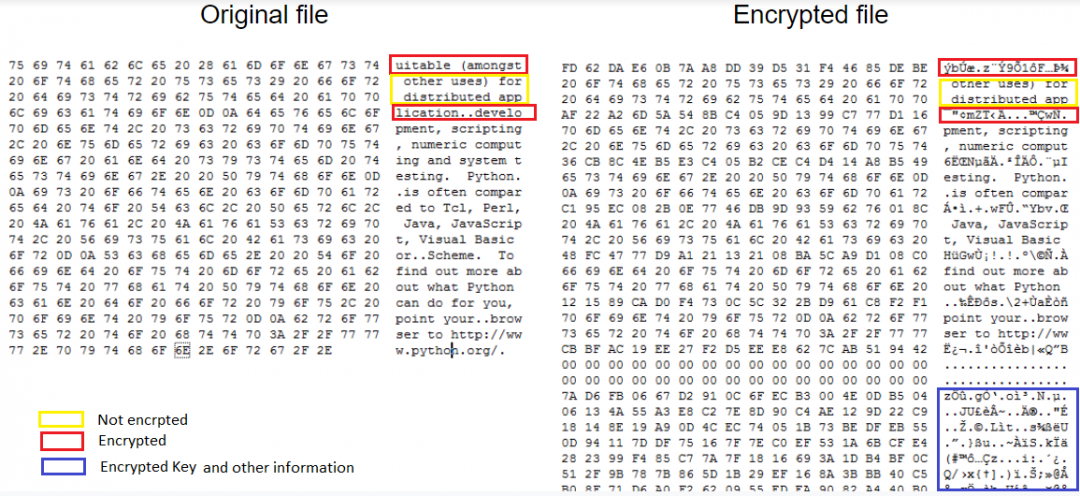
Figure 4: Original vs Encrypted file
Data Leak site
According to their leak sites, AtomSilo actors won't attack the following types of organizations:
- Hospitals.
- Critical infrastructure facilities (nuclear power plants, power plants, water treatment facilities).
- Oil and gas industry (pipelines, oil refineries).
- Educational unit.
- Non-profit companies.
They also promise to provide free decryption if the victim company is on the above list.
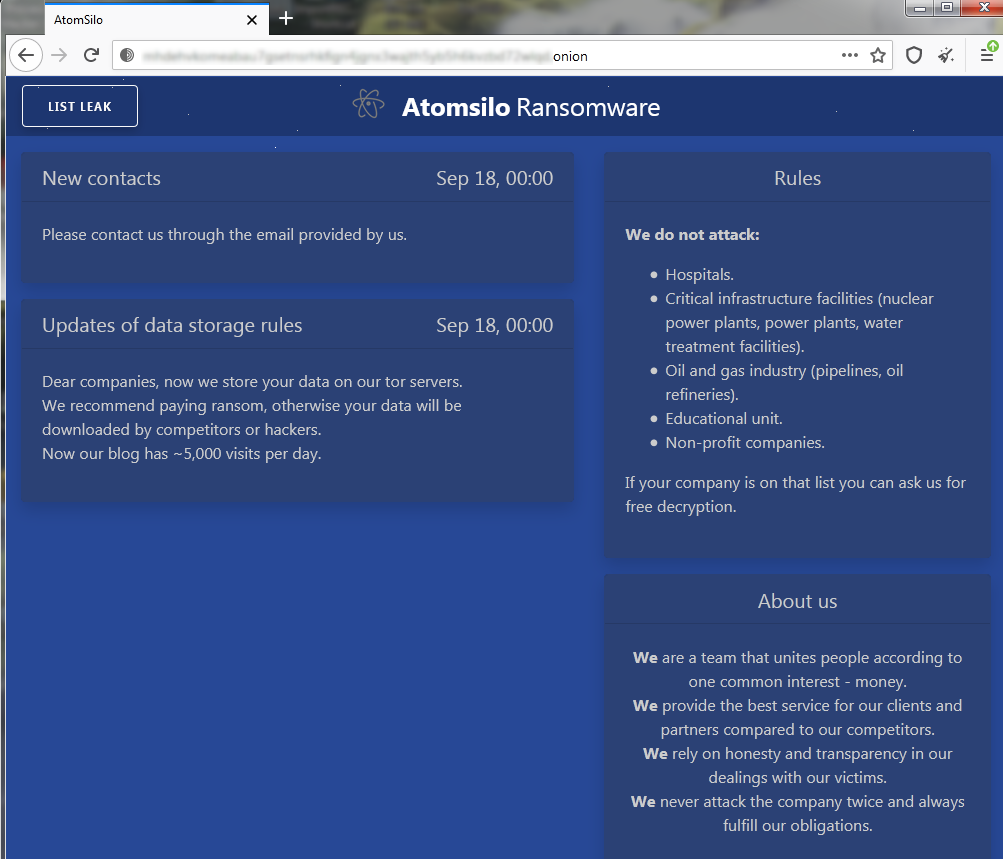
Figure 5: Data leak site
The first data leak was from a Brazilian Pharmaceutical company. AtomSilo published around 900 GB data as shown in the below screenshot:
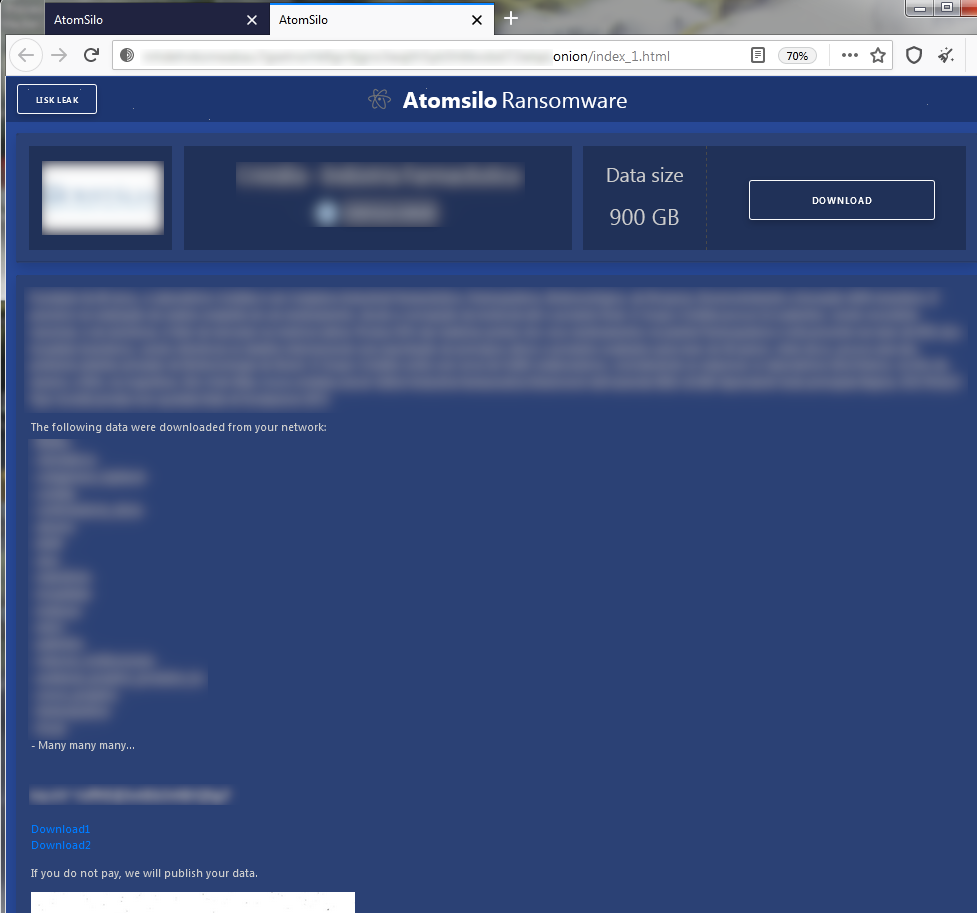
Figure 6: Victim data published on data leak site
Cloud Sandbox Detection
Figure 7: Zscaler Cloud Sandbox detection of AtomSilo ransomware
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels.
IOC
Md5
04a8307259478245cbae49940b6d655a








