Since the announcement of the official availability of two Terraform providers for Zscaler’s flagship products (ZIA and ZPA), Zscaler has seen increased adoption among our customers and partners who want to take an infrastructure- as-code approach to automating their zero trust deployment and day-to-day operations.
Managing large-scale deployments can sometimes pose a challenge to an administrator's ability to ensure their configuration is consistent and follows best practices to prevent misconfigurations. Additionally, the introduction of errors, and time-consuming tasks in repeating the same deployment several times, may become a burden to small teams.
Traditionally, DevOps teams scale and manage their infrastructure by using Terraform modules, which are reusable components that allow the creation of logical abstraction on top of specific resource sets. The use of Terraform modules enables teams to group resources together and reuse them later, possibly many times, so that deployments can be made repeatable and consistent. By using Terraform modules, DevOps and platform teams can also create standardized deployments to ensure security best practices are being enforced across the organization’s cloud deployment, which prevents accidental misconfigurations.
Advantages of using Terraform Modules
There are several benefits of using Terraform modules, including:
- Code Reduction: The use of Terraform modules significantly reduces the amount of code an administrator needs to write and maintain across multicloud hybrid infrastructure.
- Consistency: Ensure consistency across the entire cloud configuration lifecycle starting from initial deployment to the ongoing management and scalability of a cloud environment. Administrators are then able to standardize their deployments and mitigate the risk of misconfigurations.
- Simplified management: Encapsulate complex components into individual units, which simplifies the process of managing the organization’s infrastructure.
Introducing Zscaler’s Terraform Modules
With the challenges of managing multicloud infrastructure and the benefits of using Terraform Modules in mind, Zscaler have released 13 Terraform modules which are currently available in the official Terraform registry portal.
These modules cover a wide range of functionalities: from VM deployments across various cloud providers like AWS, Azure, and GCP, to deployments in VMware and Docker. Additionally, they also include configurations for Azure Sentinel, specifically designed to enable Zscaler’s Nanolog Streaming Service log ingestion.
Each of Zscaler’s Terraform modules contain the standard Terraform input variable file tfvars, which allows administrators to manage variable assignments systematically in a file with the extension .tfvars. Although there are several ways to manage variables in Terraform, Zscaler has chosen the tfvars method, given its simplicity and effectiveness.
To make the use of these modules even simpler, Zscaler has packaged an interactive bash script within some of the Terraform modules, which abstracts the input values used in tfvars. The use of the bash script enables users who may not be familiar with Terraform to perform the desired deployment without direct interaction with the Terraform command lines or the HashiCorp Configuration Language (HCL).
Zscaler Private Access Terraform Modules
The Zscaler Private Access (ZPA) service enables organizations to provide access to internal applications and services while ensuring the security of their networks. It relies on Zscaler’s App Connectors to provide the secure authenticated interface between a customer’s servers and the ZPA cloud. Zscaler distributes a standard virtual machine (VM) image for deployment in enterprise data centers, including local private cloud environments such as VMware, or public cloud environments such as AWS, Azure and GCP. Additionally, Zscaler provides packages that can be installed on supported Linux distributions.
ZPA App Connectors use a specific construct named provisioning key, which is text string generated when onboarding new App Connectors. Each App Connector pair is placed within its own group called App Connector Group in the Zscaler Cloud.
Zscaler offers terraform modules to facilitate the scalable deployment of ZPA App Connectors. These modules are combined with the ZPA Terraform Provider, which enables administrators to perform a complete infrastructure onboarding on Day Zero, by automatically creating or reusing existing App Connector Groups and Provisioning Keys. The module also provides enough flexibility to allow users to scale by easily increasing the number of App Connectors depending on their type of deployment.
ZPA App Connector Docker Module
Zscaler and Siemens have partnered to help customers with Operational Technology (OT) infrastructures to accelerate their secure digital transformation initiatives. Through this partnership, customers are able to obtain Zscaler Remote Access for OT alongside Siemens’ flexible local processing platform SCALANCE LPE. The new solution enables customers to securely manage, control quality assurance, and analyze production OT infrastructures and their applications from any workplace, in any location.
The SCALANCE LPE-9000 (Local Processing Engine) is an industrial IoT (Internet of Things) device with a Linux Operating System. This device provides computing power for various applications in the network, and as a result you can use Docker to run your own applications.
The Zscaler App Connector has been implemented in the SCALANCE LPE as a Docker container.
In addition to the Siemens SCALANCE LPE, Zscaler has also certified the deployment of App Connectors on AXC F 3152 from Phoenix Contact, which is a 64-bit aRM based device for industrial form factor.
With that in mind, Zscaler has released a Terraform module to enable organizations to deploy App Connectors within Docker containers, so that the deployment can be scaled and repeated as many times as possible to quickly protect OT applications relying on this partnership.
ZPA Private Service Edge AWS Module
For organizations that want to quickly deploy ZPA Public Service Edge-like functionality in their environment, Zscaler has also released a ZPA Private Service Edge AWS and Azure Modules. By leveraging this module, administrators can quickly:
- Onboard their remote sites by implementing zero trust network access (ZTNA) for on-premises users.
- Ensure business continuity and continue access to critical apps during disaster events.
- Keep application data traffic local to help meet compliance and regulatory requirements.
ZPA Private Service Edge AWS Module
ZPA Private Service Edge Azurerm Module
Azure Sentinel and Zscaler Cloud NSS Terraform Modules
The Azure Sentinel and Zscaler Cloud NSS is a purpose-built terraform module designed to enable the integration with Zscaler Internet Access (NSS Cloud). The module can be used for setting up both production and proof of value (PoV) environments, and contains all necessary resources required to deploy Azure Sentinel, including Azure Sentinel workspaces, Log Analytics workspaces, Data Collection Endpoints, Data Collection Rules, and custom tables.
The module was also designed to automatically map the ZIA log data by using Kusto Query Language (KQL), which is a schema that tells Microsoft Sentinel how it should map the log data to different columns in the log table. Finally, the module supports the creation of custom tables for the following Zscaler's supported log ingestion types: Web, DNS, and Firewall logs.
Zscaler Cloud Connector Terraform Modules
Enabled by the Zero Trust Exchange, the Cloud Connector VMs extend Zscaler Internet Access (ZIA) and Zscaler Private Access (ZPA) capabilities to cloud native workloads, ensuring secure communication over any network.
With the Zscaler Zero Trust exchange, the communication may be from private workloads (IaaS/Physical DC) to public workloads (SaaS/Internet), or between private workloads (IaaS to IaaS, or Physical DC to IaaS).
Zscaler offers terraform modules to facilitate the scalable deployment of Cloud Connectors. Leveraging cloud native tools like Gateway Load Balancers, IAM Roles/Managed Identities and Secret Manager/Key Vaults, customers are able to securely automate horizontally scalable deployments with zero touch provisioning.
Zscaler Branch Connector Terraform Modules
Where Cloud Connector enables Workload Communications in public Clouds, Branch Connector facilitates the same functionality for bare metal hypervisors running in customer private branches and data centers like VMware ESXi and Linux KVM.
Getting Started with Zscaler Terraform Modules
To get started with one of the available Zscaler Terraform modules, you have two options:
- Use one of the examples available as a reference for your own Terraform code. Each module will provide several example folders with different deployment types.
- Clone the GitHub repository for the module you wish to deploy and use the interactive bash script.
Example Walkthrough - TFVARS
In this article we’ll show a single example of how you can easily deploy a Zscaler Private Access (ZPA) App Connector in AWS using the dedicated module. This module provides several deployment examples with a detailed README.md page where you can follow the step-by-step instructions.
Step 1: Authenticate to the Providers
There are several methods available to provide authentication credentials depending on the cloud provider module you decide to leverage. The most recommended way is via environment variables, so that credentials are not hard coded within the Terraform configuration file. Read the following documents for details on the authentication method of each provider.
- Zscaler Private Access Authentication Methods
- AWS Terraform Provider Authentication Methods
- Azure Terraform Provider Authentication Methods
Step 2: ZPA Specific Custom TFVARS file
Each example provides a TFVARs configuration file, which contains standard values, as well as values that can be customized to fit specific deployment needs.
1. By default, this module creates a new App Connector Group as well as a new Provisioning Key, which is deployed by the Zscaler Private Access Terraform Provider. The below example shows the variable input values to create these 2 constructs in the ZPA Cloud.
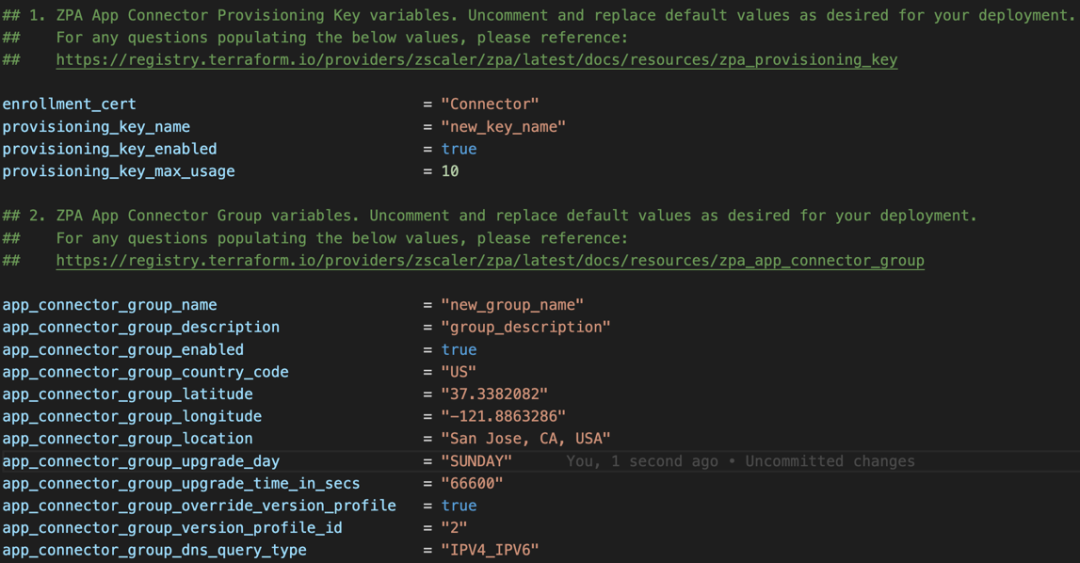
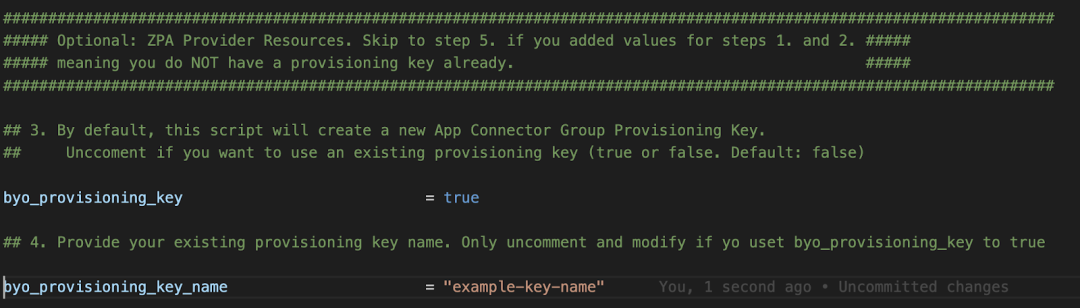
2. Optionally, if you already have an existing provisioning key, you can simply enable the corresponding variables identified by the byo (bring-your-own) prefix.
3. Notice that the provisioning key value is automatically passed to the App Connector VM(s) once the provisioning is complete, providing a complete zero touch experience.
Step 3: AWS Specific Custom TFVARS file
The second part is to customize the AWS specific variables.
1. Here you can choose your specific region as well as the AMI type to be used. By default, this module will deploy an App Connector using the Zscaler marketplace AMI; however, you can also choose to deploy the ZPA App Connector software in an Amazon Linux 2 instance by setting the variable use_zscaler_ami = false.
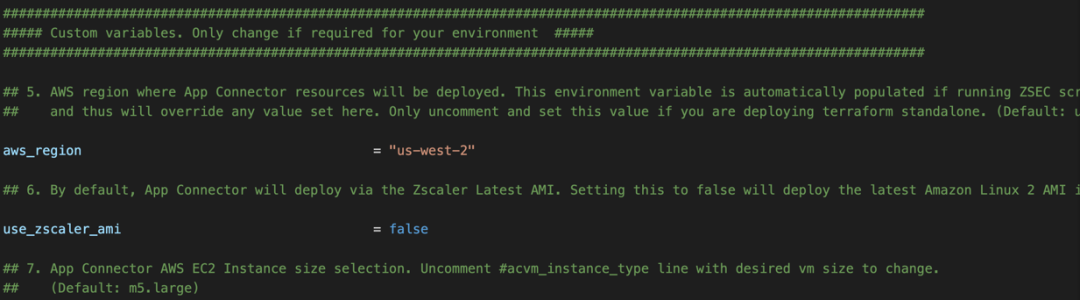
2. In this section you can choose the instance type, number of Availability zones, and number of App Connectors to be deployed. By default, the module will deploy a pair of m5.large instances unless explicitly defined otherwise.
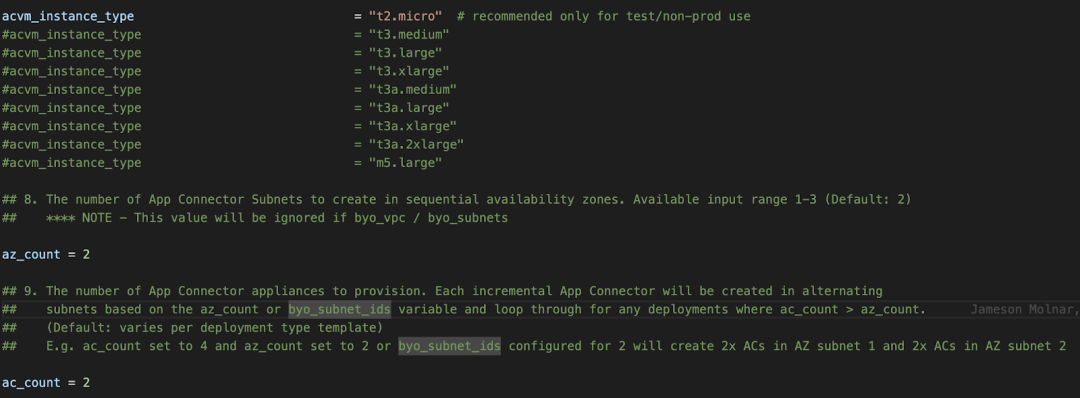
There are other variables that can be customized such as subnet, security groups, IAM roles etc.
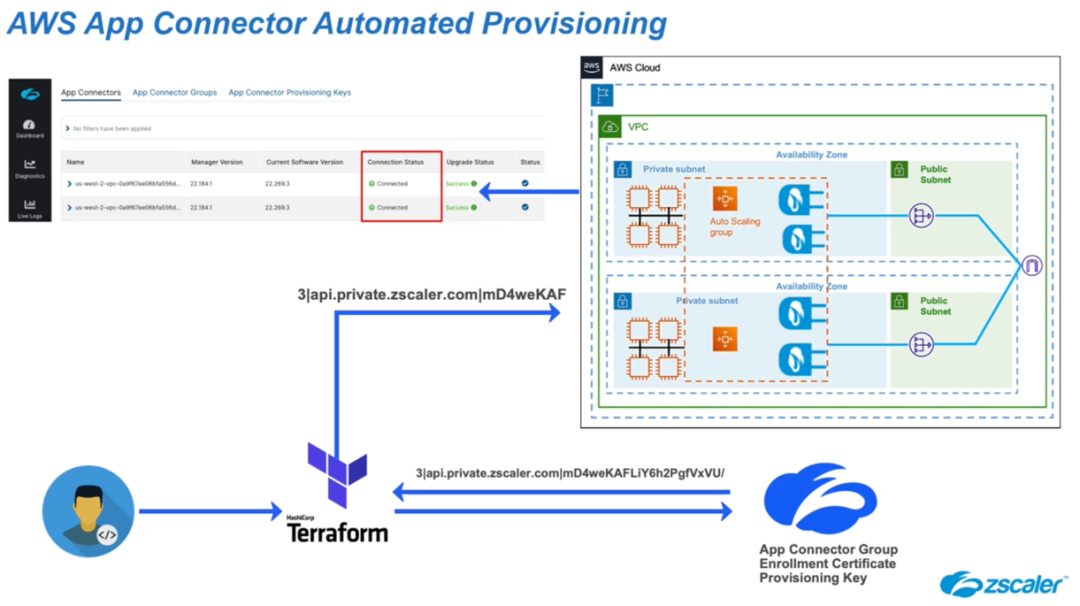
- Once the deployment is complete, the ZPA App Connectors are displayed in the Zscaler Private Access portal. Below is an illustrative diagram of a complete ZPA App Connector deployment using the ZPA App Connector AWS Module
To watch a complete demo of both deployment methods using TFVARs file and the interactive bash script, visit our Zenith Community portal here.
How to Contribute
Zscaler will continue to develop new modules and update existing ones covered in this article. Note however, that this is a community-based project, developed as a joint effort between Zscaler Technology Alliances architects, product specialists, and cloud architects; hence, provided AS-IS. Zscaler does not offer official support to these modules via its standard support channel. Contributions are welcome to the project(s) by opening a new pull request. For any issues encountered while using any of the modules, please open an issue via the appropriate GitHub repository.
Link to Resources
Are you interested in exploring the power of Zscaler and HashiCorp automation? Visit one of the links below and check out the available deployment options for each module. Also feel free to provide feedback and send us your questions either via GitHub issues or via your local Zscaler account team.
Terraform Modules
- ZPA App Connector AWS Module
- ZPA App Connector Azure Module
- ZPA App Connector GCP Module
- ZPA App Connector Docker Module
- Zscaler Cloud NSS and Azure Sentinel Terraform Module
- Zscaler Cloud Connector AWS Module
- Zscaler Cloud Connector Azure Module
- Zscaler Branch Connector VMware Module
- Zscaler Branch Connector Libvirt Module




