Protecting critical business data requires two things:
- An understanding of where sensitive data resides.
- Comprehensive context of data, so you have knowledge of the possible paths that allow access to this particular data.
However, cloud environments present a unique challenge to security teams. In the cloud, data can reside in any of the hundreds of cloud native data services such as databases, object storage, attached and detached disks (ebs-volumes), and more. In addition, access to critical data may be cleared in trivial and non-trivial forms, each presenting its own hurdle to detect and mitigate.
For example, data can be found in S3 buckets, where a single configuration opens the bucket to the public. The data could also be in a cloud native DB service, such as AWS RDS, and access is cleared through IAM roles that may be over-permissive and over-privileged.
As a result, data protection in the cloud requires the identification and classification of data; assessment of its exposure through access/attack path analysis, and continuous monitoring of such attempts by any bad actors. To achieve this, threat intelligence is required, along with a deep integration of solutions, including Data Loss Protection (DLP) and a Cloud Native Application Protection Platform (CNAPP). These solutions must all speak the cloud language, be aware of all the cloud-specific data stores, and be able to prioritize exposure based on true risk derived from the data.
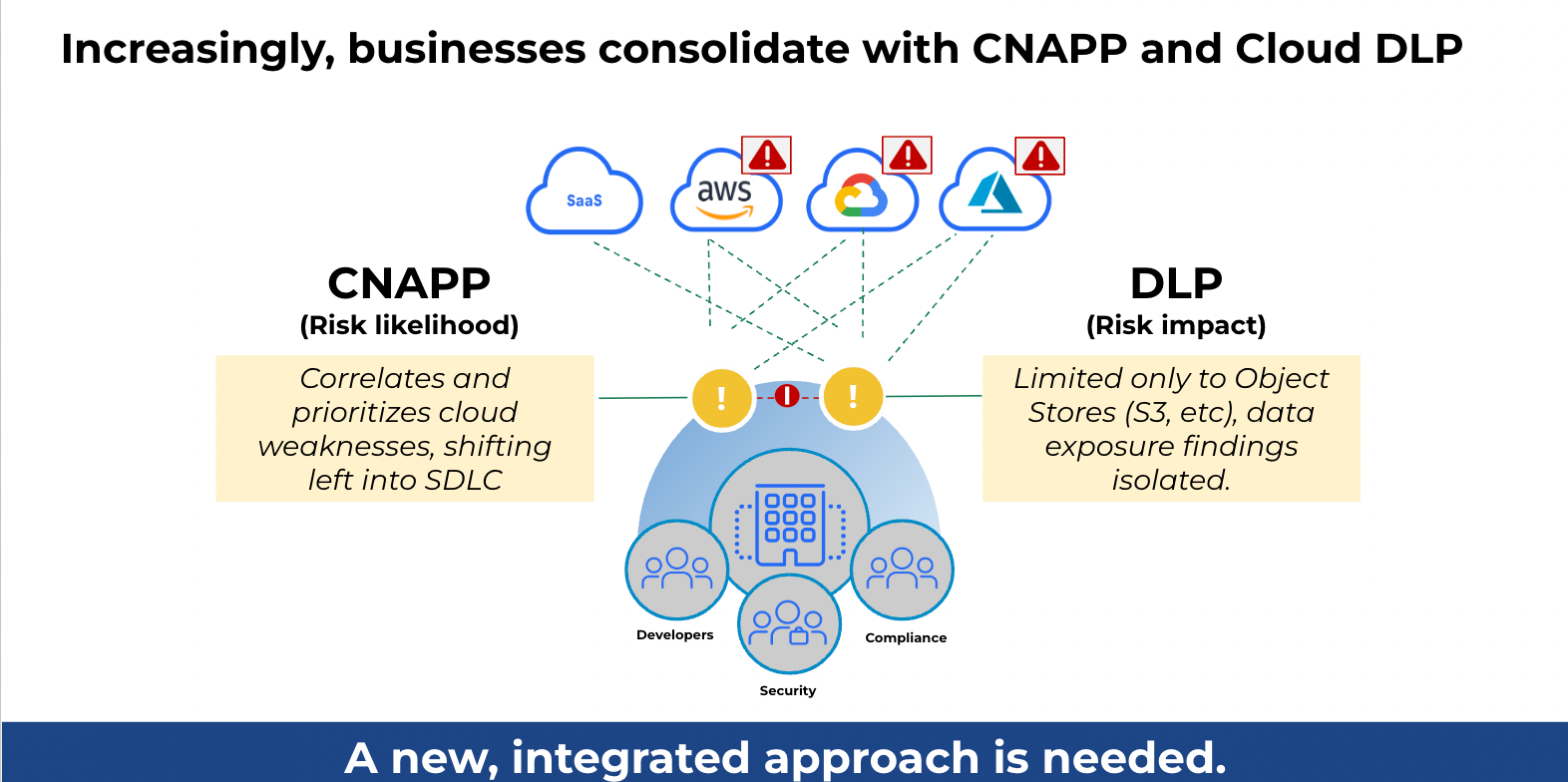
In the following section, we describe the journey of a security admin responding to a malicious actor scanning a cloud asset. We demonstrate how through the combination of cloud-focused DLP, vulnerability scanning, and permission analysis, the security team is able to identify a real “show stopper” and mitigate what could have been a compromise of business-critical PII data.
PII data leakage through vulnerable instance and detached disk
In the following use case, we describe how Zscaler Posture Control, our CNAPP solution, —integrated with DLP and ThreatLabz threat intelligence—empowers the security admin to respond and mitigate a critical attack that could have resulted in theft of sensitive PII data, residing on a stale disk inside an AWS account.
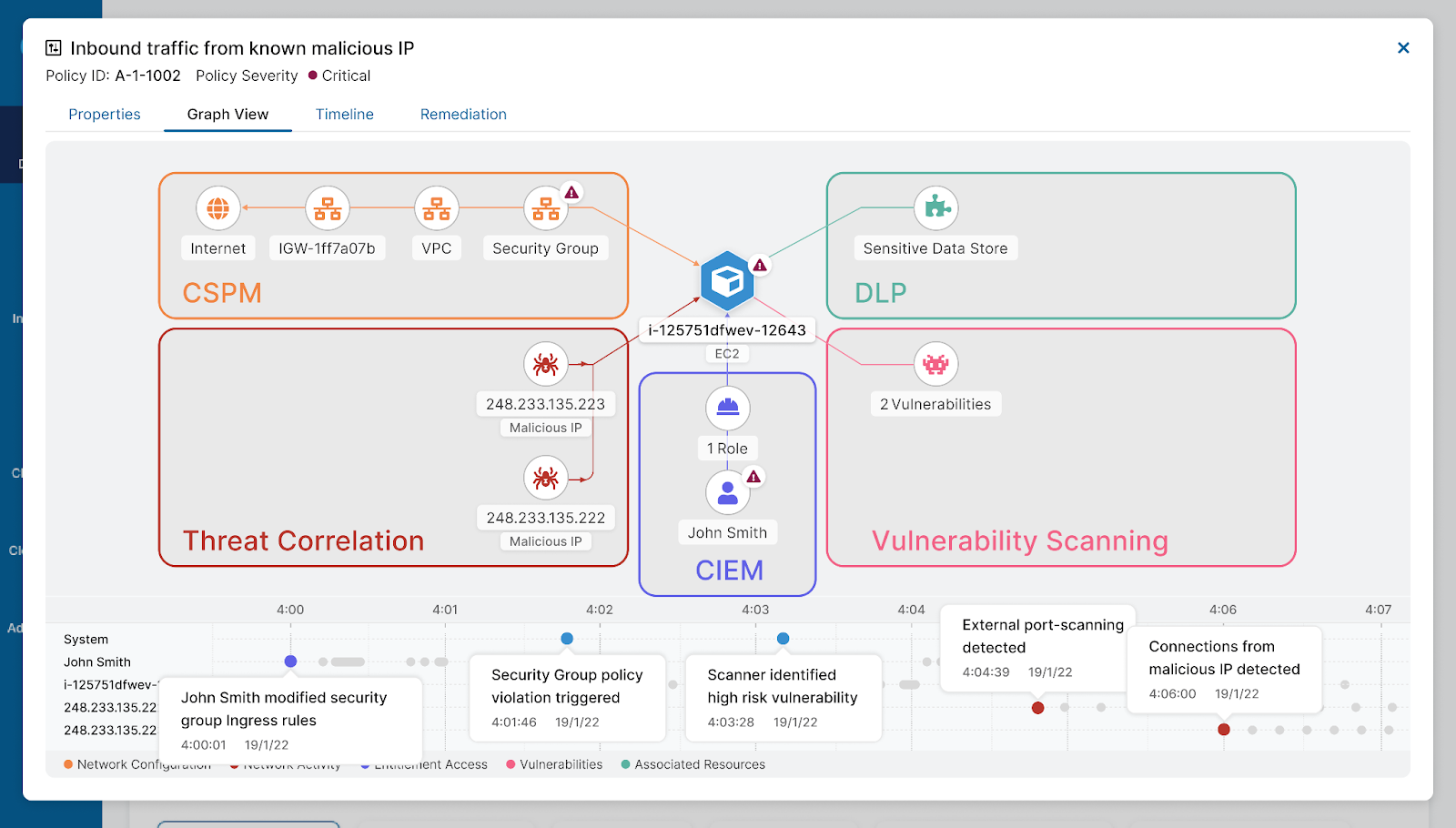
The trigger
As Posture Control continuously monitors the network traffic directed to our customers' workloads, enriched with ThreatLabz intelligence, the system raises an incident where one of the externally facing EC2 instances is seeing an increased volume of scanning by IPs that are classified as malicious.
In the wild, externally facing instances are constantly scanned from various sources across the internet. From the security team’s perspective, context on the source of the scanning—as well as the target's risk—is essential to prioritize and mitigate.
The source context
ThreatLabz provides the context regarding the source of the scanning. It indicates these IPs are currently involved in known attacks. Hence, this event needs to be investigated. At this phase, the focus of the investigation is to assess the risk exposure of the scanned assets.
Zscaler Posture Control risk assessment - target context
Posture Control enriches the context of the event with the following data points:
- The instance is exposing a vulnerable application library
- It is assigned with a ComputeAdmin role that allows the instance access to all disks in the account
- There is a stale disk in this AWS account that was once attached to a production instance and contains a DB copy. This copy contains business-critical data as well as PII data
Given all that, from the attacker's perspective, the malicious actor could easily see that the instance runs an exploitable application. Post exploitation, the attacker would immediately obtain the ComputeAdmin role’s credentials and begin moving laterally across the assets in the AWS account. Using AWS CLI native commands—such as describe-volumes and attach-volume—an attacker can attach any volume to the compromised instance and scan its content, discovering the DB Copy, and exfiltrating it unnoticed.
Containment and mitigation
This complete view of the intention to exploit, as well as the critical potential damage, enabled the security team to raise a show stopper alert. With that context, they can mitigate the attack in various points, as provided by Posture Control:
- Limit network exposure of the instance
- Patch the application
- Reassign the instance with a role, according to the principle of least privilege
Conclusions
Security teams are often under significant loads of events to be investigated, exposure to be sealed and vulnerabilities to be mitigated. Without context, correlation, and true risk scoring, fatigued teams are missing the most critical data exposure risk. In addition, in the more complex exposure cases, they would not know how to correctly respond without impacting the business.
Posture Control’s integration to DLP and ThreatLabz not only allows gathering of all the important data points, but it helps correlate and prioritize risk, with the combination of thereof. This integration provides the ability to understand the cloud, understand the data, and identify any malicious attempt via industry-leading threat intelligence.
For more information, please check out our launch blog and on-demand launch webinar.
If you’re interested in learning more about Posture Control, we have a free cloud security risk assessment here.