Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
Rapport ThreatLabz : 87,2 % des menaces sont diffusées via des canaux chiffrés
Le chiffrement est la norme par défaut pour la communication en ligne, la quasi-totalité du trafic Web étant protégée par des protocoles sécurisés tels que TLS/SSL. Pourtant, alors que le chiffrement se généralise de jour en jour, les hackers disposent de plus en plus d’opportunités d’exploiter les canaux chiffrés.
Le même chiffrement qui protège les activités légitimes sert également de canal pour les activités malveillantes. Les hackers utilisent les canaux chiffrés pour contourner les défenses traditionnelles, dissimulant des malwares, des campagnes de phishing, du cryptomining/cryptojacking et des vols de données au sein du trafic chiffré.
Le rapport Zscaler ThreatLabz 2024 sur les attaques chiffrées examine ce paysage de menaces en constante évolution, sur la base d’une analyse complète de milliards de menaces diffusées via HTTPS et bloquées par le cloud Zscaler. Le rapport met en évidence les tendances les plus récentes, les principales catégories de menaces, les cibles les plus courantes des attaques chiffrées et d’autres informations sur la manière dont les hackers exploitent le trafic chiffré.
5 conclusions essentielles sur les attaques chiffrées
L’équipe de recherche ThreatLabz a analysé 32,1 milliards d’attaques chiffrées bloquées par le cloud Zscaler entre octobre 2023 et septembre 2024 afin d’identifier et comprendre les derniers modèles de menaces. Vous trouverez ci-dessous le sous-ensemble de résultats qui suit met en évidence certaines des tendances et cibles les plus importantes.
- Une croissance régulière des attaques chiffrées a été observée : le cloud Zscaler a bloqué un volume sans précédent d’attaques intégrées dans le trafic TLS/SSL au cours de la période d’analyse. Les menaces chiffrées représentaient 87,2 % de toutes les attaques bloquées, ce qui représente une hausse de 10,3 % d’une année sur l’autre des attaques chiffrées et reflète le recours croissant au chiffrement par les hackers pour dissimuler leurs activités malveillantes.
- Les malwares dominent le paysage : les malwares demeurent la menace chiffrée la plus répandue, avec 86,5 % des attaques bloquées. Cette tendance met en évidence l’adaptation des tactiques de malware que les hackers exploitent pour prospérer dans les canaux chiffrés en utilisant le chiffrement pour masquer les payloads et échapper aux mesures de sécurité et de détection traditionnelles.
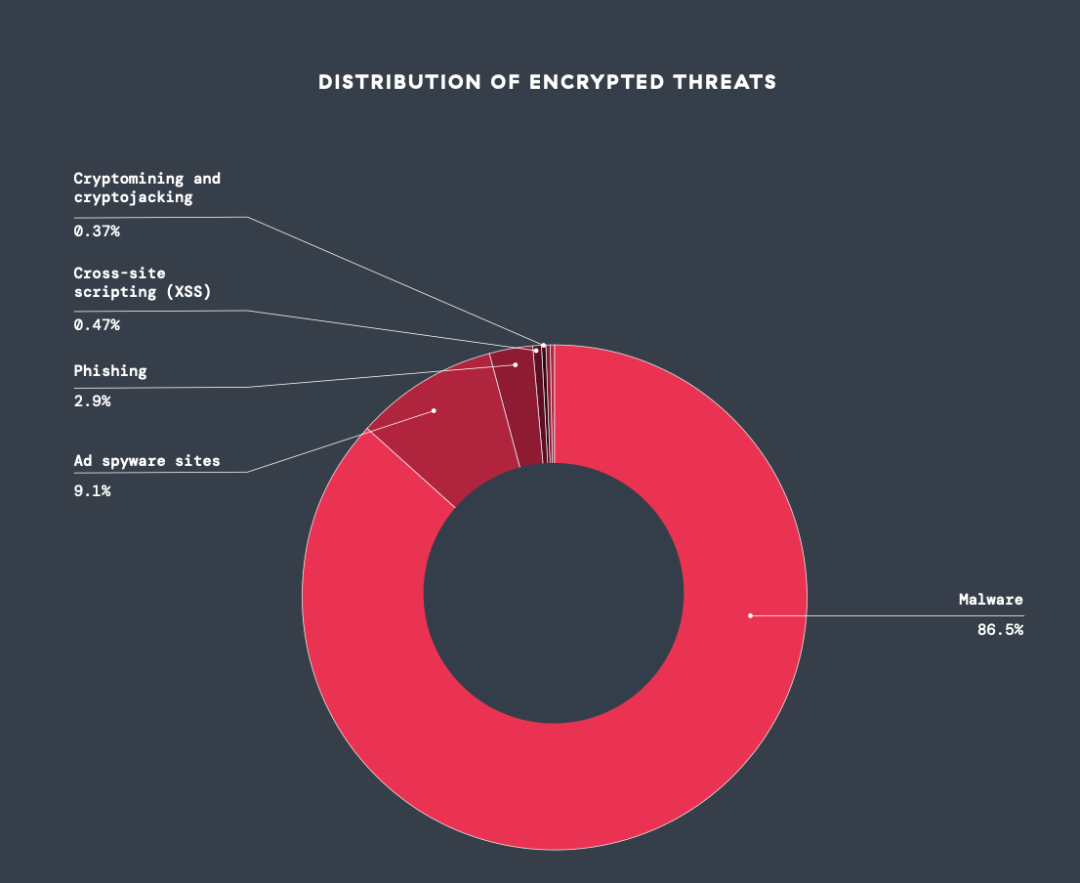 Illustration 1 : Principales catégories de menaces observées
Illustration 1 : Principales catégories de menaces observées - Le cryptomining/cryptojacking, les scripts intersites et les menaces de phishing déferlent : le cryptomining/cryptojacking et les scripts intersites (XSS) figurent parmi les menaces chiffrées qui connaissent la croissance la plus rapide, avec des hausses respectives de 122,9 % et 110,2 % d’une année sur l’autre, tandis que le phishing a enregistré une augmentation notable de 34,1 %. Il se peut que ces pics aient été alimentés par l’utilisation croissante des technologies d’IA générative, qui facilitent la création de scripts de cryptomining avancés, l’automatisation de scripts XSS malveillants et l’exécution de campagnes de phishing particulièrement convaincantes.
- Le secteur de la production industrielle arrive en tête de la liste des secteurs les plus touchés : les secteurs de la production industrielle, de la technologie et des services ont été les plus ciblés, le secteur de la production industrielle ayant enduré 13,5 milliards de tentatives d’attaques chiffrées entre octobre 2023 et septembre 2024.
- Les États-Unis et l’Inde restent les principales cibles : ayant subi 11 milliards (États-Unis) et 5,4 milliards (Inde) d’attaques chiffrées au cours de la période d’analyse de ThreatLabz, les États-Unis et l’Inde conservent leur position de pays les plus ciblés, suivis par la France, le Royaume-Uni et l’Australie.
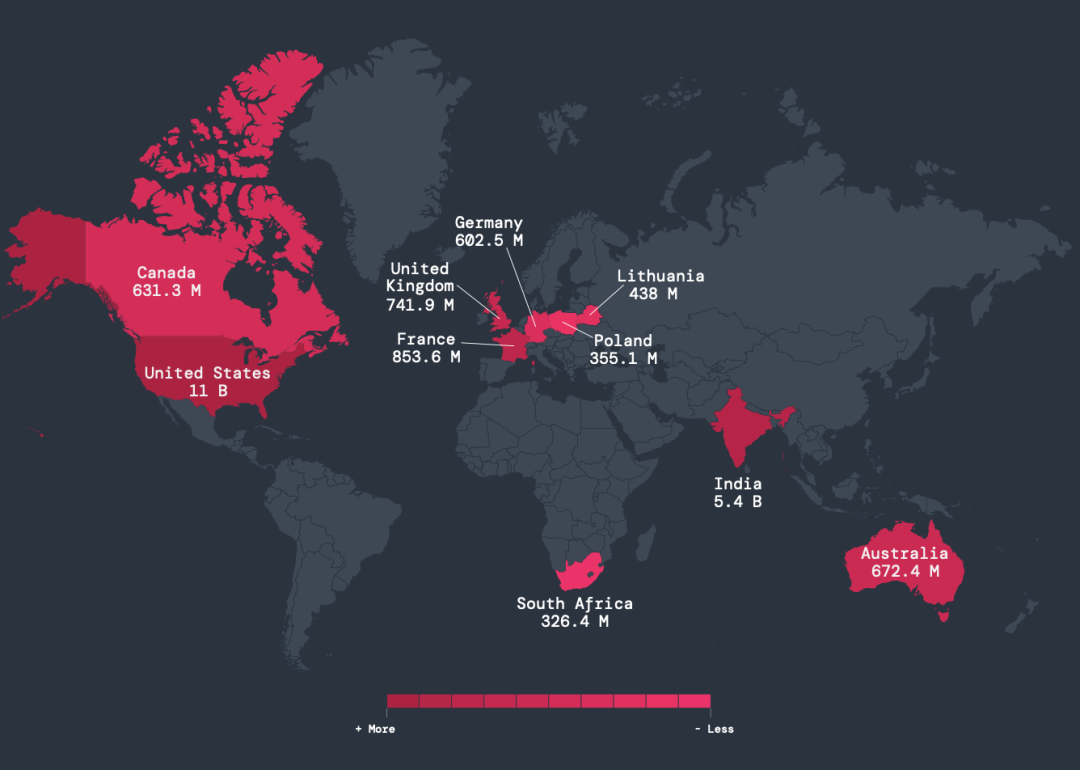
Illustration 2 : Cartographie des pays qui subissent le plus d’attaques chiffrées
Évolution des tendances en matière d’attaques chiffrées
ThreatLabz a découvert de nombreuses tendances marquantes concernant l’évolution des attaques chiffrées, depuis des hackers qui exploitent des canaux de chiffrement pour exfiltrer des données sensibles jusqu’à des méthodes de type AiTM (Adversary-in-the-Middle) utilisant des outils avancés et le chiffrement TLS/SSL pour créer des campagnes de phishing presque indétectables. Le rapport propose des exemples de chacune de ces tendances.
ThreatLabz a examiné en détail une tendance notable, à savoir l’utilisation abusive croissante des services cloud par des groupes de menaces persistantes avancées (APT). En se fondant dans le trafic légitime des services cloud, les groupes APT peuvent profiter de l’utilisation par défaut du chiffrement TLS/SSL pour les aider à échapper aux contrôles de sécurité du réseau. ThreatLabz se penche sur cette tendance et fournit une analyse détaillée qui comprend les éléments suivants :
- Principaux groupes APT qui exploitent les services cloud
- 10 principaux services cloud exploités
- Principaux services exploités pour la diffusion de payloads
- Tactiques les plus courantes utilisées pour exploiter les services cloud
Comment Zscaler neutralise les menaces chiffrées
Zscaler Zero Trust Exchange fournit une solution puissante pour neutraliser les menaces chiffrées, en commençant par éliminer les angles morts grâce à ses capacités d’inspection TLS/SSL et ses défenses optimisées par l’IA. Voici comment Zscaler s’attaque aux menaces chiffrées à chaque étape d’une attaque.
Minimiser la surface d’attaque
Les connexions chiffrées non vérifiées, telles que celles qui transitent par des VPN ou des workloads exposés, peuvent étendre la surface d’attaque et permettre aux hackers de se dissimuler à la vue de tous. Zscaler élimine ce risque et la surface d’attaque en gardant les applications et les services invisibles sur Internet. Cette approche empêche les menaces chiffrées d’atteindre les applications et systèmes critiques, fournissant une protection proactive qui ne repose pas sur un accès réseau partagé.
Empêcher la compromission initiale
Zscaler Internet Access™ (ZIA) effectue une inspection TLS/SSL complète pour vérifier chaque connexion et arrêter les menaces cachées sans sacrifier les performances. Les fonctionnalités d’inspection de ZIA s’appuient sur une analyse optimisée par l’IA et une détection inline pour identifier et bloquer rapidement les menaces sophistiquées cachées dans le trafic chiffré. Cette approche élimine le besoin d’appliances physiques traditionnelles, gourmandes en ressources, ce qui permet aux entreprises de gérer aisément la croissance du trafic chiffré sans perturbation.
Éliminer le mouvement latéral
Les hackers cherchent souvent à se déplacer latéralement au sein des réseaux dès qu’ils y ont accédé. Zscaler les en empêche grâce à une segmentation Zero Trust et à des politiques contextuelles optimisées par l’IA, fournies par Zscaler Private Access™ (ZPA). ZPA applique des contrôles d’accès granulaires, limitant l’accès des utilisateurs à des applications spécifiques en fonction de l’identité, du contexte et de la politique. Cette solution remplace la segmentation complexe du réseau basée sur des règles par un contrôle d’accès simplifié et basé sur l’identité. De plus, Zscaler utilise une technologie de tromperie, en installant des leurres pour détecter et contrecarrer les tentatives de déplacement latéral au sein du trafic chiffré.
Bloquer les rappels de commande et de contrôle
Les malwares s’appuient souvent sur des canaux chiffrés pour communiquer avec des serveurs C2, ce qui permet aux hackers d’exécuter des commandes, de télécharger de nouveaux malwares ou d’exfiltrer des données sensibles. ZIA inspecte le trafic chiffré sortant et entrant pour interrompre les communications C2. Les outils de protection contre la perte de données optimisés par l’IA de Zscaler détectent et bloquent le trafic malveillant, empêchant l’exfiltration de données sensibles et les rappels C2 chiffrés de compromettre le réseau.
Étude de cas : Découvrez comment Wipro a bloqué 8,2 millions de menaces chiffrées en un trimestre grâce à Zscaler
En remplaçant les pare-feu et les VPN traditionnels par Zscaler, Wipro a renforcé ses défenses avec l’inspection TLS/SSL inline de tout le trafic Internet et SaaS visant à détecter et à bloquer les menaces chiffrées. Lisez le témoignage de ce client ici.
Importance d’une inspection TLS/SSL complète
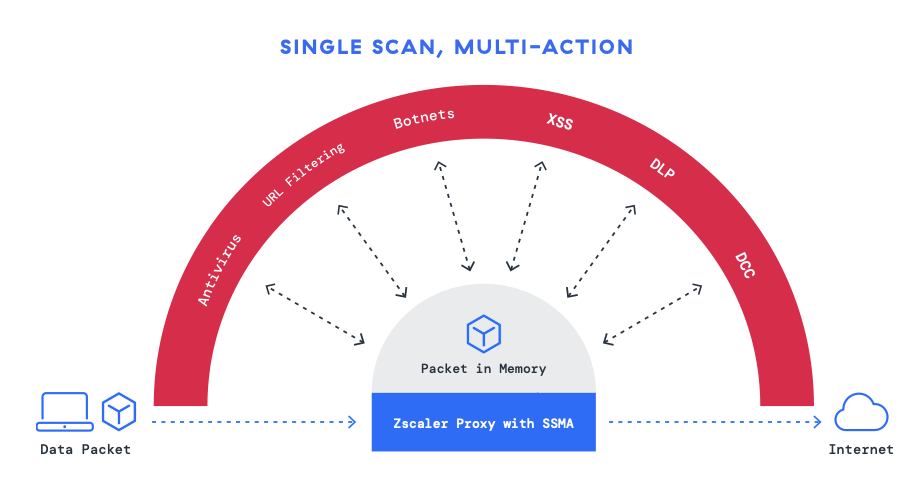
La défense de Zscaler contre les menaces chiffrées repose sur sa capacité d’inspection TLS/SSL complète, rendue possible par une architecture évolutive basée sur un proxy. Contrairement aux solutions matérielles traditionnelles qui obligent les entreprises à faire des compromis entre sécurité et rapidité, l’approche cloud native de Zscaler permet aux entreprises d’inspecter intégralement le trafic à grande échelle grâce à son moteur Single-Scan, Multi-Action, une fonctionnalité unique qui traite le trafic une seule fois et applique plusieurs contrôles de sécurité simultanément. Cela permet aux entreprises de :
- Inspecter 100 % du trafic chiffré : contrairement aux solutions qui n’inspectent qu’une fraction du trafic chiffré en raison de contraintes matérielles, l’architecture cloud native de Zscaler garantit que chaque paquet est inspecté sans exception.
- Effectuer des contrôles de sécurité avancés en couche : les contrôles de sécurité optimisés par l’IA inline détectent et bloquent les menaces incorporées dans le trafic chiffré.
- Maintenir de hautes performances : l’architecture de Zscaler élimine les goulots d’étranglement généralement associés aux appliances matérielles.
Garder une longueur d’avance sur les menaces chiffrées
Les conclusions du rapport ThreatLabz 2024 sur les attaques chiffrées montrent clairement que les acteurs malveillants évoluent constamment à l’aide des technologies de chiffrement et d’IA pour échapper à la détection et maximiser leur impact.
Immergez-vous dans les dernières recherches et apprenez-en davantage sur la façon de garder une longueur d’avance sur les menaces chiffrées. Le rapport complet propose les thématiques suivantes :
- Analyse approfondie : conclusions détaillées et études de cas sur la manière dont les hackers exploitent le chiffrement
- Perspectives 2025 : informations d’experts sur l’évolution du paysage des menaces chiffrées.
- Bonnes pratiques applicables : liste de contrôle pratique pour améliorer vos défenses contre les attaques chiffrées
Protégez votre entreprise contre les menaces chiffrées. Téléchargez votre exemplaire du rapport dès aujourd’hui.
Cet article a-t-il été utile ?
Clause de non-responsabilité : Cet article de blog a été créé par Zscaler à des fins d’information uniquement et est fourni « en l’état » sans aucune garantie d’exactitude, d’exhaustivité ou de fiabilité. Zscaler n’assume aucune responsabilité pour toute erreur ou omission ou pour toute action prise sur la base des informations fournies. Tous les sites Web ou ressources de tiers liés à cet artcile de blog sont fournis pour des raisons de commodité uniquement, et Zscaler n’est pas responsable de leur contenu ni de leurs pratiques. Tout le contenu peut être modifié sans préavis. En accédant à ce blog, vous acceptez ces conditions et reconnaissez qu’il est de votre responsabilité de vérifier et d’utiliser les informations en fonction de vos besoins.
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.



