Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
S'abonner
Job scams impersonate companies still hiring following tech layoffs
Introduction
In the midst of significant layoffs hitting the previously immune tech industry, scammers have mobilized and doubled down on targeting job seekers with various employment scams. Stealing personal information and extorting victims for money, these scams leverage fake job postings, sites or portals, and forms, wrapped in social engineering to attract job seekers.
The Zscaler ThreatLabz team observed multiple suspicious job portals and surveys used by attackers to solicit information from job seekers under the guise of employment application forms. The attackers may advertise jobs online, sometimes setting up fake websites, or look for targets on social media to steal money and personal information.
Key Takeaways
- Threat actors masquerade as recruiters from specific companies, primarily located in the US and Canada.
- Malicious new domains are registered on hosting providers like Namecheap.
- Attackers scrape and reuse the contents of real job postings from public sites like SmartRecruiters and LinkedIn to convince applicants the post is legitimate.
- Fake application forms steal sensitive personal information from victims and may be sold, used for fraud, and to further target and extort victims.
- Newly Registered Domains (NRD) are commonly used by threat actors and these have suspicious Top-Level Domains (TLDs) such as .online, .work, .live, etc. typically followed by the name of the actual hiring organization the attackers are impersonating.
Threat Campaign Analysis
Our researchers discovered an active scam where the threat actor(s) positioned themselves as Zscaler recruiters targeting job seekers on LinkedIn.

Fig 1 - Shows a LinkedIn message phishing for victims with a fake Zscaler job link and reference code
This fake listing was created by a scammer from an active Zscaler job posting listed on SmartRecuiters, however the attackers made one change, lowering the years of experience requirement to attract more potential victims. For an unsuspecting candidate, this common outreach tactic may feel familiar and the copied job posting appears like a legitimate position.
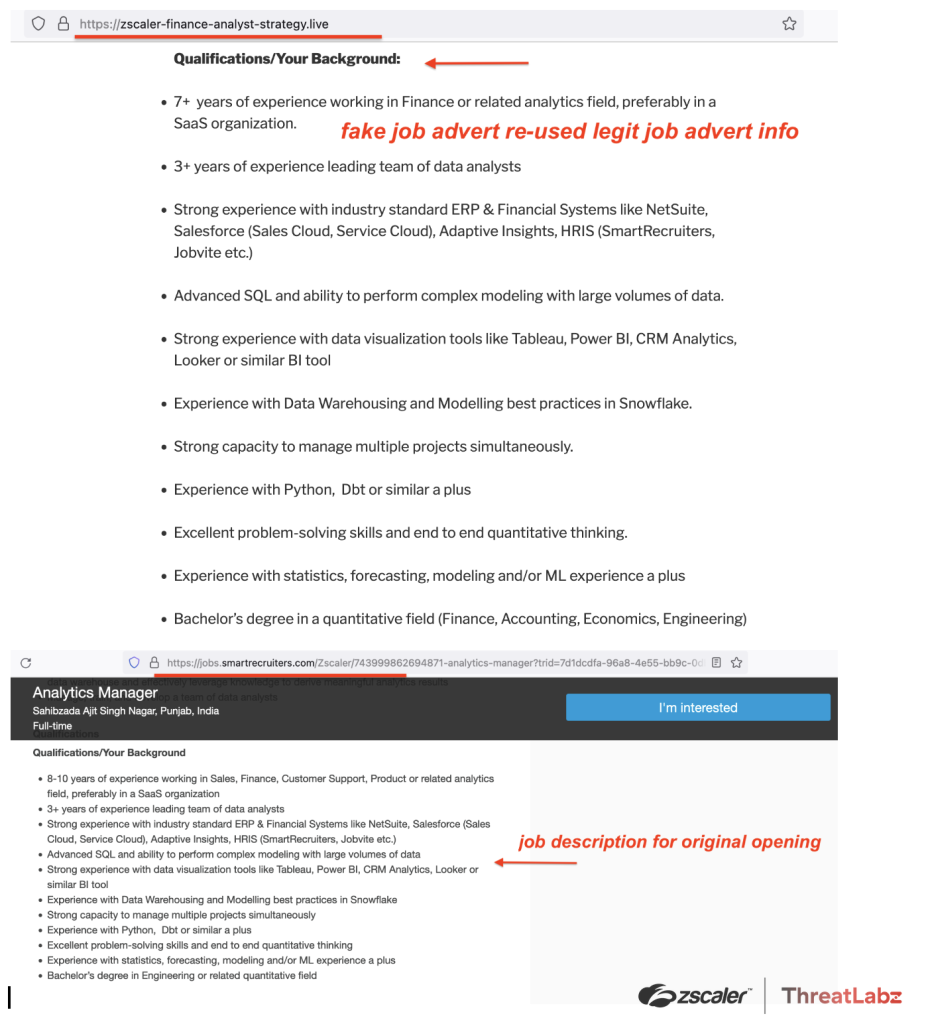
Fig 2 - Fake job post copied from an actual Zscaler listing on SmartRecruiters
To apply for the fake job shown above, applicants are prompted to fill out a questionnaire that requests personal information, job role related information, and compensation information.

Fig 3 - Landing page of the application questionnaire.
As a final step of the questionnaire, the victim is prompted to verify identification by uploading a copy of their State ID, Drivers License, Residential Permit, or Passport. Collecting this document along with the victim's other personal information may enable the scammers to impersonate the victim committing identity theft and fraud, or sell the information to other scammers.
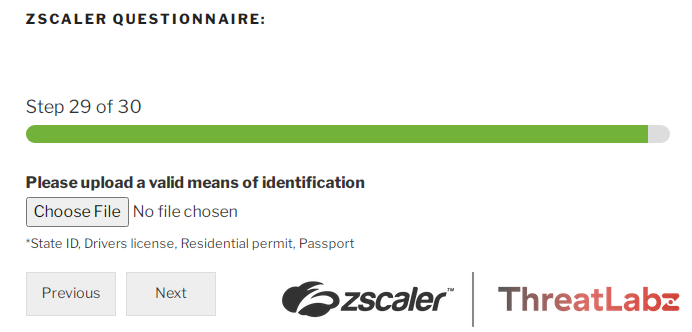
Fig 4 - Final step of fake job questionnaire asking the victim for a copy of an official document containing Personally Identifiable Information (PII)
After submitting the completed questionnaire, a confirmation message is displayed indicating the victim will be contacted via text message or email in 1-3 days for next steps in the application process.
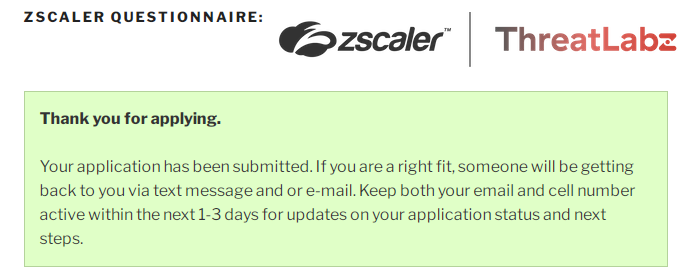
Fig 5 - Submission confirmation message displayed after completion of the fake job offer questionnaire
Once the submission has been received by the scammers, they reach out using email to schedule a fake interview using Skype or a chat application, as shown in the screenshot below.
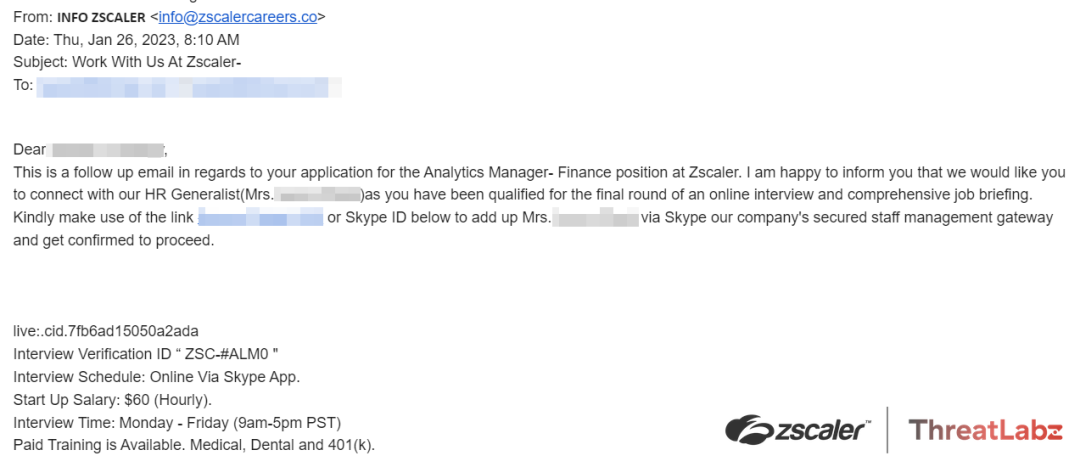
Fig 6 - Malicious email impersonating a Zscaler recruiter scheduling aSkype interview with the victim
Note that the Skype invitation provided in the email shows a profile photo of an actual Zscaler recruiter.

Fig 7 - Malicious Skype invitation using a real profile picture to impersonate an actual Zscaler recruiter
Following the fake interview, candidates may receive a fake job offer and be routed through a fake onboarding process. As a final step, victims may be asked to pay for shipping the IT hardware equipment they will need for the remote position or payments for onboarding training. Scammers may also ask for Social Security numbers and bank account information for depositing paychecks.
Infrastructure Analysis
The malicious site observed in this threat campaign contained currently inactive code to validate credit card details, a feature that may be used once a victim falls for the initial attack.
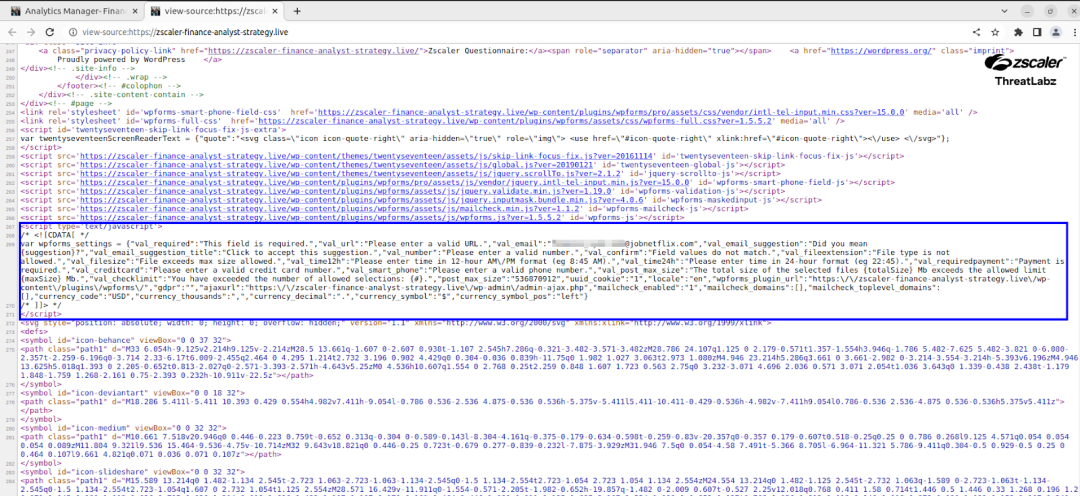
Fig 8 - Source code showing commented-out credit card validation element
The malicious domain used in this scam - zscaler-finance-analyst-strategy[.]live, was created on 23-Jan-2022, a Newly Registered Domain at the time of technical analysis by Threatlabz researchers on 24-Jan-2022, following an observed attack one day after the domain was created.
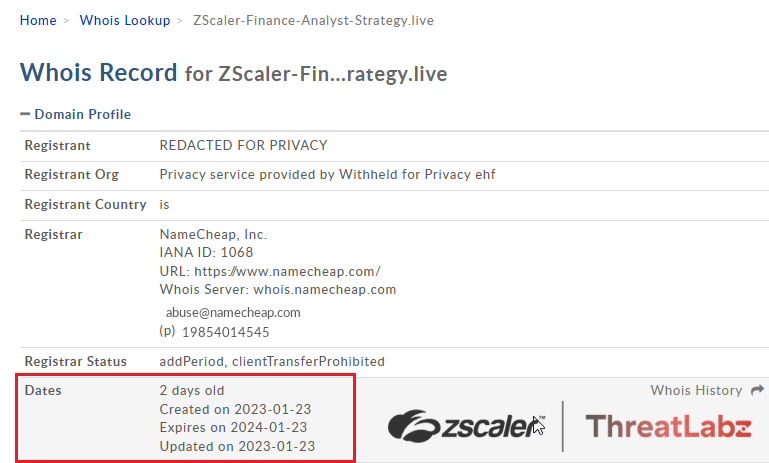
Fig 9 - Registration details showing the site used in this scam was a Newly Registered Domain at the time of analysis
A script found in the site’s code contained an email address impersonating a Netflix recruiter with domain jobnetflix[.]com.
Conducting a pivot search on this email address, researchers discovered the following two additional fake job postings leveraged by the same unauthorized email account:
- UX designer (REMOTE) ZUORA SOFTWARE
- Project Administrator Construction, New Equipment KONE OYJ
A complete list of domains previously linked to the same threat actor(s) are listed in the IOCs section at the end of this article.
While investigating this campaign, ThreatLabz researchers also observed several other suspicious newly-registered sites portraying job portals or advertising fake job openings.
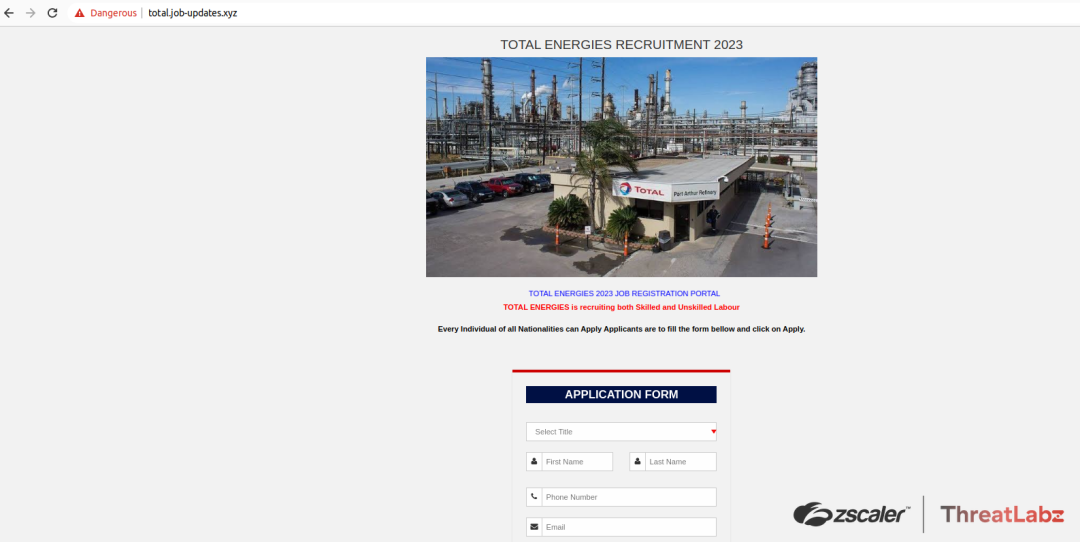
Fig 10 - Fake Total Energies recruitment scam page
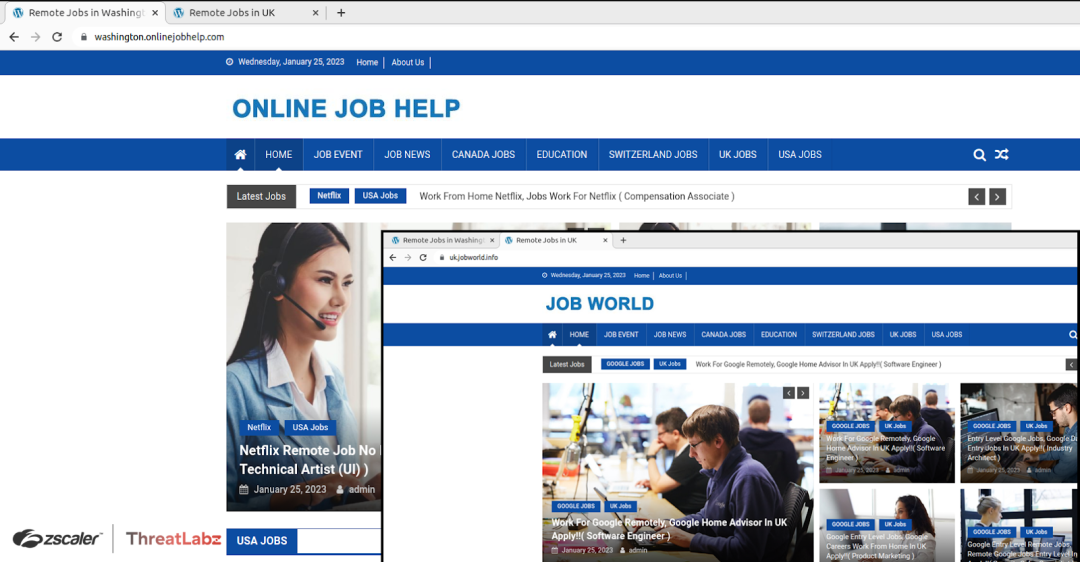
Fig 11 - Malicious job portal with fake or stolen job listings
Best Practices To Safeguard Against Attacks
- Ask for a direct link to the company’s job posting and reach out to the company directly using contact information you gather from the company website to verify the credibility of a job posting. Search for job postings across legitimate job sites. Only submit online applications to authentic verified sites.
- Do not engage in communication with any un-official email address or respond to a text or phone number without verifying legitimate company affiliation for the recruiter and confirming via email communication that they have a corporate email address.If you’re not familiar with the company, search its name with the word “scam” or “fraud.” You may find stories from others who have been targeted.
- Look for telltale signs of a possible scam like emails from personal email addresses or email addresses not affiliated with the company, grammar and spelling mistakes, interviews conducted solely via email or online chat, salaries out of line with industry norms, and requests for financial information or other personal information.
- Never make any type of payment for an application or job offer. Genuine organizations will never ask you for any type of payment to apply or accept a job offer. Likewise, legitimate recruitment agencies and placement firms are almost always compensated for sourced candidates by the companies they serve. Any request for payment should automatically raise a red flag that you are likely dealing with a scammer.
- Only use HTTPS/secure connections when visiting job postings.
- Ensure your operating system and web browser always have the latest security patches installed.
Indicators Of Compromise (IOCs)
Domains used to masquerade as Zscaler
zscaler-finance-analyst-strategy[.]live
zscalercareers[.]co
Previous domains used by the same threat actor(s)
zuora-ux-designer-a83637.ingress-erytho.easywp[.]com
submit-application[.]us
global-application[.]us
careers-firstenergycorp[.]online
career-conagragroup[.]live
canadiantire[.]work
interview-petsmart[.]online
hire-weston[.]com
career-petsmart[.]com
intellectsoftcareer[.]com
Cet article a-t-il été utile ?
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.




