Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
S'abonner
CVE-2024-3661, a.k.a. TunnelVision, Exposes a VPN Bypass Vulnerability
*Updated on November 7, 2024: This blog was updated to reflect Zscaler patch information.
Introduction
On May 6, 2024, a researcher from Leviathan Security Group identified a new technique, termed as “TunnelVision”, that can bypass VPN encapsulation and enable attackers to send the traffic outside a VPN tunnel using the built-in features of Dynamic Host Configuration Protocol (DHCP). TunnelVision involves the routing of traffic without encryption through a VPN. This traffic can be directed by the attacker's configured DHCP server using option 121, ultimately being redirected to the internet via a side channel created by the attacker. The existing VPN tunnel remains intact, and the side channel created by the attacker cannot be detected by the existing VPN tunnel. CVE-2024-3661 has been assigned to this critical vulnerability.
Recommendations
For organizations
Zscaler ThreatLabz recommends organizations: enable DHCP snooping, ARP protections, and port security on switches used for communication. If feasible, ignore option 121 for the DHCP server when VPN is being used in the network.
Note: In some scenarios, completely ignoring option 121 may result in network connectivity issues.
For VPN providers
Zscaler ThreatLabz recommends VPN providers integrate network namespaces into operating systems where feasible.
Further Details
The content below elaborates on our recommendations for mitigating this vulnerability.
- DHCP Snooping: Enabling DHCP snooping on LAN switches helps prevent rogue DHCP servers and eliminates potentially harmful DHCP traffic. DHCP snooping allows network access only for clients with specified IP and/or MAC addresses. It also provides ARP security as a sub-feature, allowing precise control over permitted ARP packets within the network.
- Port Security: Network switches can be configured with port security, which enables you to limit the number of MAC addresses learned per port. This configuration ensures that the switch only forwards packets with recognized MAC addresses while discarding others. As a result, fake packets are effectively blocked from reaching the DHCP server.
- Ignoring DHCP Option 121: Another potential countermeasure is to disregard option 121 during VPN activation. DHCP option 121 typically adds classless route options, which specify a set of classless static routes for the client's routing table. However, it is important to note that ignoring these routes may disrupt network connectivity, despite the intended purpose of option 121.
Affected Operating Systems
This issue impacts operating systems following RFC specifications for DHCP clients and featuring DHCP option 121 route support.
Affected systems include:
- Windows
- Linux
- MacOS
- iOS
Notably, Android remains unaffected as it lacks support for DHCP option 121.
How It Works
The VPN client creates an encrypted version of the packet which is originally received from the file descriptor associated with its virtual network interface. It places this encrypted payload in the layer for its underlying VPN protocol, then uses that protocol to communicate with the VPN server.
Once a VPN client establishes a connection with a VPN server, it configures the host's settings to route traffic through the established tunnel.
DHCP provides time-based leases for IP addresses and sets the default gateway, which acts as the primary route to the internet or Domain Name System (DNS) servers. In 2002, RFC 3442 introduced option 121 for classless static routes, allowing administrators to add static routes with classless ranges to a client’s routing table.
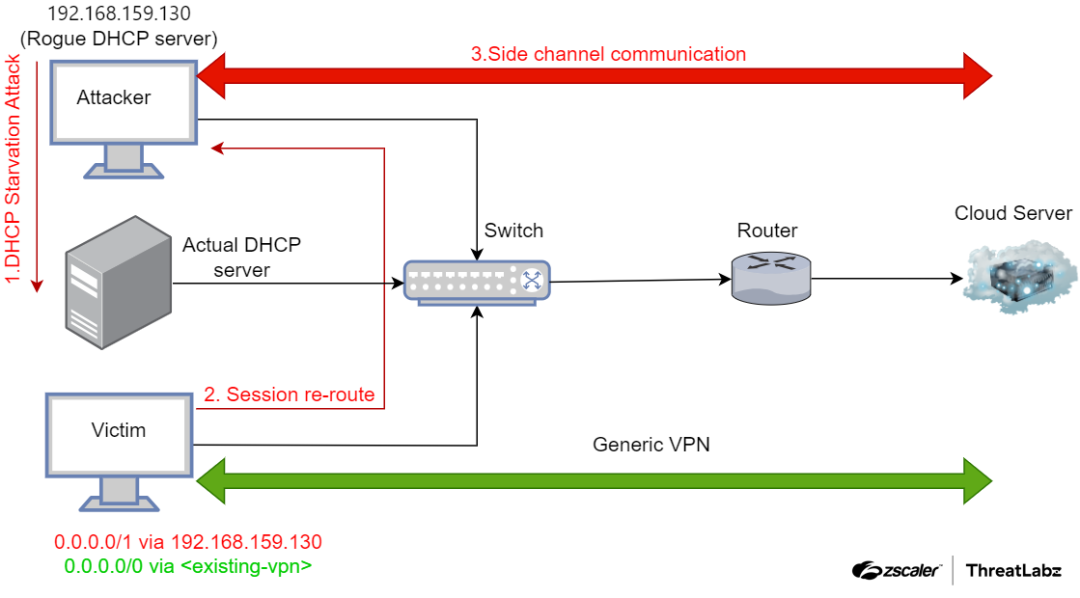
Figure 1: A depiction of how the attacker could use a DHCP starvation attack to create a side channel for communication, thereby rerouting legitimate traffic.
The attack steps are explained below:
- An attacker utilizes a DHCP starvation attack to flood the legitimate DHCP server with DHCP Discovery packets until all available addresses are exhausted. Subsequently, the attacker sets up a rogue DHCP server and sends incorrect network settings via new DHCP requests.
An attacker operates a DHCP server on the same network as a targeted VPN user and utilizes DHCP option 121, as depicted in the figure below, to configure a static route in the routing table. The attacker ensures that the preference of the configured static route is higher than that of the default route. Additionally, the attacker sets the DHCP configuration to use itself as the gateway, enabling the DHCP server to act as an Adversary-in-the-Middle (AiTM). This allows the attacker to intercept unencrypted traffic before forwarding it to the default gateway through traffic forwarding configuration.
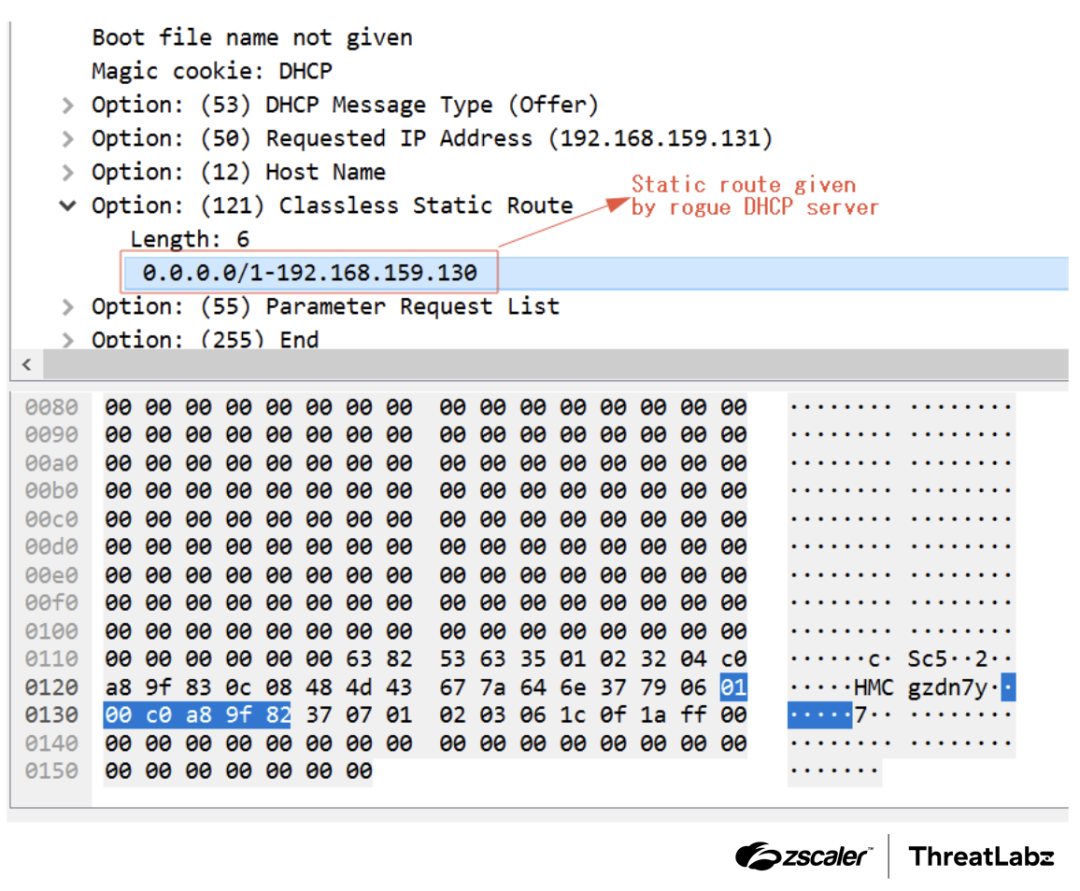
Figure 2: Packet indicating the usage of option 121 in the DHCP offer.
- An attacker establishes a side channel for communication and data transfer to their own controlled systems located outside the internet, bypassing the VPN tunnel. However, this bypassing of the VPN tunnel does not give any indication to the user's identity.
Zscaler Patches
Zscaler added protection for the following clients.
Windows client
Only Windows Client Connector devices running on route-based mode are impacted. Windows clients running Z-Tunnel 2.0 or the Packet Filter driver in Z-Tunnel 1.0 mode are not affected.
If your devices are running on route-based mode, Zscaler recommends migrating to packet filters.
To check if you are running on route-based mode:
- Navigate to your Client Connector Portal.
- Under the Administration section, inspect your forwarding profiles.
- If “Route Based” is selected for any of these that are actively being used by devices, then route-based mode is in effect. Please refer to Using the Windows Filter Driver for Zscaler Client Connector for detailed steps on migrating to packet filters.
If you have any questions about migrating to packet filtering, reach out to your Zscaler account team.
macOS client
All macOS clients are impacted. The macOS client uses a virtual network adapter within the operating system. As such, DHCP is utilized, and option 121 can be used to publish routes for the virtual network adapter.
Zscaler added protection against this vulnerability in the Zscaler Client Connector (version 4.2.0.282) for macOS clients on May 21, 2024.
Linux client
All Linux clients are impacted. The Linux client uses a virtual network adapter within the operating system. Consequently, DHCP is utilized, and option 121 can be used to publish routes to the virtual network adapter.
Zscaler added protection against this vulnerability for the following Linux clients:
- Zscaler Client Connector (1.5.1.25) on May 17, 2024
- Zscaler Client Connector (3.7.0.134) on June 6, 2024
iOS client
Not impacted.
Android client
Not impacted.
Conclusion
The TunnelVision vulnerability (CVE-2024-3661) exposes a method for attackers to bypass VPN encapsulation and redirect traffic outside the VPN tunnel. This technique involves using DHCP option 121 to route traffic without encryption through a VPN, ultimately sending it to the internet via a side channel created by the attacker. To mitigate this vulnerability, Zscaler ThreatLabz recommends organizations to implement DHCP snooping, ARP protections, and port security on switches. It is also advised to consider ignoring option 121 for the DHCP server when VPN is in use, although this may result in network connectivity issues in certain scenarios.
Cet article a-t-il été utile ?
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.



