Background
A cybersecurity advisory was released by the Federal Bureau of Investigation (FBI) related to a DarkSide ransomware infection targeting manufacturing, legal, insurance, healthcare and energy sectors. In May 2021, the FBI received notification that the ransomware variant DarkSide had infected a critical infrastructure company. The attack was confirmed to have been waged against Colonial Pipeline, the largest fuel distributor in the United States.
What is the issue?
DarkSide was first spotted in August 2020. It is distributed through weak or compromised credentials of Virtual Desktop Infrastructure (VDI) or RDP connections. It encrypts files and appends the extension “.{random 6 alphanumeric/numeric characters}.” It uses a combination of RSA and SALSA20 algorithms to encrypt files. DarkSide has impacted numerous organizations across various sectors including manufacturing, legal, insurance, healthcare, and energy.
DarkSide uses double extortion tactics by exfiltrating data and threatening to publish it to the internet in addition to encrypting files. Double extortion has been an increasing tactic among ransomware operators since late 2019.
What systems are impacted?
All machines running Windows and Linux operating systems.
What can you do to protect yourself?
We recommend making periodic backups of all the important data and keeping those backups isolated off the network. It is equally important to have updated security software and the latest software patches applied to the endpoints. Remote Desktop service access should always be restricted, or it should be turned off if not used. As always, avoid opening suspicious emails containing attachments or links that come from any unknown sources. Disable macros in Office programs. Do not enable them unless it is essential to do so. Enable multi-factor authentication (MFA) across both business and personal email accounts to thwart most credential harvesting attacks.
Zero Trust architecture and policy are essential to mitigating the success and damage of ransomware attacks. We recommend using context-based identity and policy enforcement to control and monitor access to the internet and applications. We suggest connecting users and entities directly to applications rather than to a network to eliminate lateral movement. Additionally, we recommend using in-line data loss prevention to further protect against data exfiltration.
Zscaler coverage
- Advanced Threat Protection
Win32.Ransom.Darkside
Win32.Ransom.Darkside.LZ
PS.Downloader.CobaltStrike.LZ
VBA.Downloader.Zloader.LZ
Win32.Trojan.KillAck.LZ
- Malware Protection
W32/Trojan.FPNR-9260
W32/Trojan.UJXE-8785
W32/Trojan.VSDP-0799
W32/Trojan.WEVK-1365
W32/Trojan.WQLB-0241
- Advanced Cloud Sandbox
Gen:Trojan.Heur.PT.OmZ@BSEA3vk
TR/Agent.Wzlfi
TR/Crypt.XPACK.Gen
TR/Redcap.Vzchu
Details related to these threat signatures can be found in the Zscaler Threat Library.
Our Cloud Sandbox Report for DarkSide ransomware executable can be seen in Figure 1.
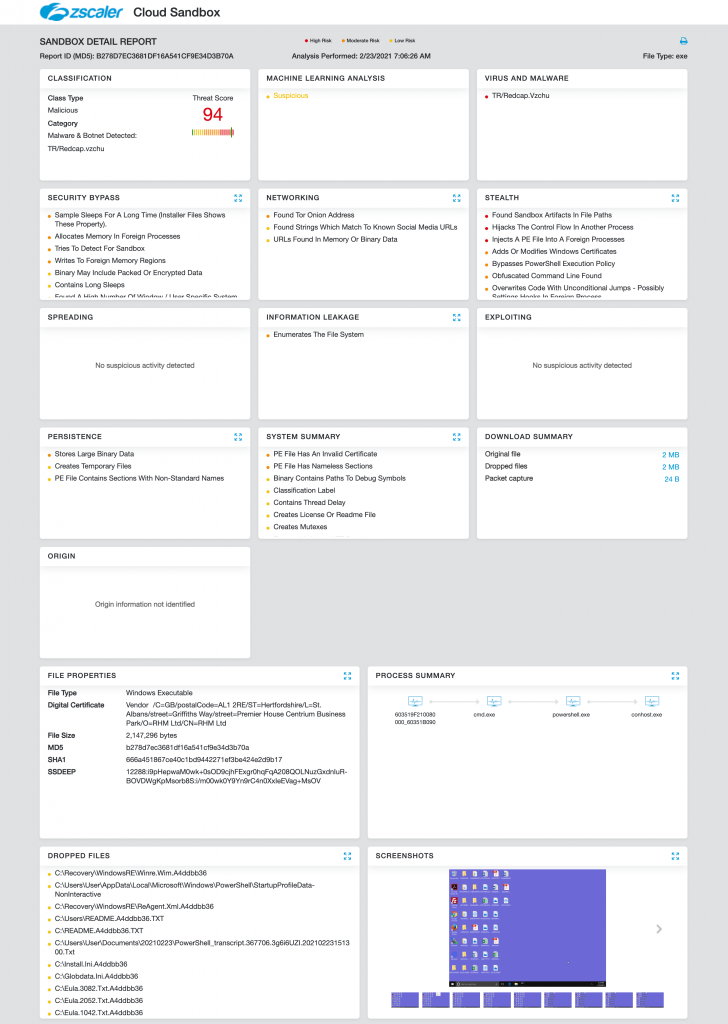
Fig 1: Cloud Sandbox Report for DarkSide Ransomware
The Zscaler Cloud Sandbox provides proactive coverage against advanced threats such as ransomware and banker trojans. The Zscaler ThreatLabZ team is also actively monitoring DarkSide, CobaltStrike and Zloader malware families and ensuring coverage for all the latest IOCs associated with these malware.
Reference




