Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
S'abonner
Coverage Advisory for CVE-2023-34362 MOVEit Transfer Vulnerabilities
Updated Security Advisory - June 22, 2023
Progress Software disclosed one more critical vulnerability CVE-2023-35708 with CVSS Base Score 9.8 in its MOVEit Transfer application on 15th June 2023. An unauthenticated remote attacker could exploit the vulnerable version of MOVEit Transfer that could lead to escalated privileges and potential unauthorized access in the environment. An adversary can steal or modify data upon successful exploitation of the SQL injection vulnerability, CVE-2023-35708.
Progress software had patched a similar vulnerability CVE-2023-34362 and CVE-2023-35036 recently in the MOVEit transfer application. At the moment, whether this vulnerability, CVE-2023-35708, is exploited in the wild or not is yet to be confirmed, but it is highly likely to be exploited by threat actors.
For immediate remediation of all the recent 3 MOVEit Transfer vulnerabilities, disable all HTTP and HTTPs traffic to your MOVEit Transfer environment until the latest patch with the fixes applied.
The organizations that applied the patch for the vulnerability CVE-2023-34362 and CVE-2023-35708 are still vulnerable to CVE-2023-35708. The vulnerability affects MOVEit Transfer before versions released before 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), 2023.0.3 (15.0.3). It is important for organizations to apply the latest security patches released by the Progress software mentioned here.
Zscaler Coverage:
Zscaler’s ThreatLabZ team has deployed protection as mentioned below:
Zscaler Private Access AppProtection:
- Progress MOVEit Transfer SILCertToUser or UserCheckClientCert SQL Injection (CVE-2023-35036 or CVE-2023-35708): 6000667
Updated Security Advisory - June 21, 2023
Progress Software disclosed a new vulnerability CVE-2023-35036 in its MOVEit Transfer application on 12th June 2023. An unauthenticated remote attacker could exploit the latest release of MOVEit Transfer to steal or modify data by exploiting the SQL injection vulnerability known as CVE-2023-35036. Currently, there is no evidence of real-world attacks.
Progress software had patched a similar vulnerability CVE-2023-34362 recently in the MOVEit transfer application. At the moment, whether this vulnerability, CVE-2023-35036, is exploited in the wild or not is yet to be confirmed, but it is highly likely to be exploited by threat actors.
The organizations that applied the patch for the vulnerability CVE-2023-34362 are still vulnerable to CVE-2023-35036. The vulnerability affects MOVEit Transfer before versions 1.0.7, 1.1.5, 14.0.5, 14.1.6, and 15.0.4. It is important for organizations to apply the latest security patches released by the Progress software mentioned here.
Zscaler Coverage:
Zscaler’s ThreatLabZ team has deployed protection as mentioned below:
Zscaler Private Access AppProtection:
- Progress MOVEit Transfer SILCertToUser SQL Injection (CVE-2023-35036): 6000667
Security Advisory – June 09, 2023
Background:
MOVEit is a managed file transfer software produced by Progress(formerly Ipswitch). The MOVEit encrypts files and uses secure File Transfer Protocols to transfer data with automation, analytics and failover options. The software has been heavily used in the healthcare industry as well as thousands of IT departments in financial services and government sectors.
On 31-May-2023, Progress Software disclosed a critical vulnerability CVE-2023-34362 in the MOVEit application. This vulnerability, upon successful exploitation, could allow an unauthenticated attacker to gain access to the MOVEit Transfer's database and allow them to infer information about the internals of the database and alter or delete their elements.
What is the issue?
MOVEit is typically used for file transfer operations by organizations and has a web application that supports different types of databases like MySQL, Microsoft SQL Server, and Azure SQL. The MOVEit vulnerability allows adversaries to implant a remote web shell on the victim's machine.
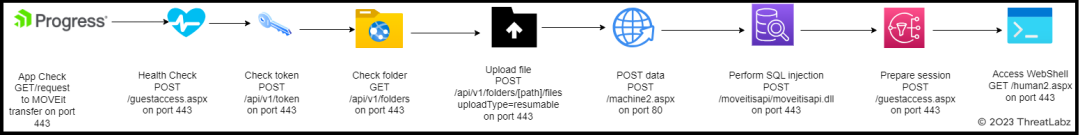
As shown in the diagram above, an adversary performs the following steps to implant a malicious webshell.
- App check - GET / - on port 443
- Health check - POST /guestaccess.aspx - on port 443
- Check token - POST /api/v1/token - on port 443
- Check folder - GET /api/v1/folders - on port 443
- Upload file - POST /api/v1/folders/[PATH]/files uploadType=resumable - on port 443
- Post data - POST /machine2.aspx on port 80
- Perform SQL injection - POST /moveitisapi/moveitisapi.dll - on port 443
- Prepare session - POST /guestaccess.aspx - on port 443
- Upload file - PUT /api/v1/folders/[PATH]/files uploadType=resumable&fileId=[FILEID] - on port 443
- Post data - /machine2.aspx - on port 80
- Access WebShell - GET /human2.aspx - on port 443
The name of the malicious file, human2.aspx, is intentionally used for webshell to masquerade the original, non malicious file, human.aspx, which typically comes with the installations of MOVEit applications. This ASPX file stages an SQL database account to be used for further access. Once the malicious webshell is installed, it creates a random 36 characters long password which later is used for the authentication purpose. The adversary communicates with the webshell over HTTP protocol with specially crafted HTTP request with a custom header in it, named “X-siLock-Comment”. The value of the custom header contains the password generated during the installation of the malicious webshell. The webshell would return a 404 not found response if the incoming HTTP request doesn’t contain the custom header. Once an adversary successfully authenticates, depending on the database engine being used (MySQL, Microsoft SQL Server, or Azure SQL), an adversary may be able to build the understanding about the structure and contents of the database, and also execute SQL statements that can alter or delete database elements.
The moveitisapi.dll is used to perform SQL injection when requested with specific headers, and guestaccess.aspx is used to prepare a session and extract CSRF tokens and other field values to perform further actions. It connects to the database and offers data exfil functionality based on a provided X-siLock-Step1 header.
As of 7 June 2023, there were roughly 2,500 instances of MOVEit Transfer exposed to the public internet. In recent years, File transfer solutions have been a popular target for ransomware groups. As per an advisory published by the Cybersecurity And Infrastructure Security Agency, CISA, threat actors groups like the CL0P Ransomware Gang reportedly started exploiting the same vulnerability and leveraged it to implant a remote web shell on the victim's machine. The Internet facing MOVEit Transfer web applications were infected with a web shell named LEMURLOOT, which was then used to steal data from the victim's machine and underlying MOVEit Transfer databases.
Are Zscaler products affected?
Zscaler does not utilize Progress Software's MOVEit product. The Zscaler platform is not susceptible to this vulnerability. The trust post is published here.
Affected products:
The details regarding the affected versions of MOVEit Transfer are present here. As per Progress Software, this vulnerability affects all versions of MOVEit Transfer. However, it doesn’t affect MOVEit Automation, MOVEit Client, MOVEit Add-in for Microsoft Outlook, MOVEit Mobile, WS_FTP Client, WS_FTP Server, MOVEit EZ, MOVEit Gateway, MOVEit Analytics and MOVEit Freely.
Mitigations:
The Progress Software also released a security advisory mentioning the details related to the patch with the fix and recommended remediations and mitigation steps.
If one is using MOVEit Transfer versions before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1), then it is strongly recommended to upgrade them to the versions in which this vulnerability is patched, as per the details given here.
Investigation Tips:
The IIS access logs can be checked for indicators of compromise on the host in question.
At the endpoint, presence of files named human2.aspx or _human2.aspx in \MOVEitTransfer\wwwroot\ folder.
Based on known cases of exploitation so far, compromise would involve incoming requests to the following endpoints (in this order)
guestaccess.aspx, followed by
moveitisapi.dll, followed by
human2.aspx or _human2.aspx
In case header values are logged, requests/responses with the following HTTP header names are confirmed indicators of compromise :
X-siLock-Comment
X-siLock-Step1
X-siLock-Step2
X-siLock-Step3
Locate MOVEit root directory from
HKEY_LOCAL_MACHINE\SOFTWARE\Standard Networks\siLock->WebBaseDir
Locate MOVEit log file location
HKEY_LOCAL_MACHINE\SOFTWARE\Standard Networks\siLock->LogsBaseDir
Best Practices/Guidelines To follow:
- Safeguard crown jewel applications by limiting lateral movement using Zscaler Private Access, especially with application security modules turned on.
- Route all server traffic through Zscaler Internet Access, which will provide the right visibility to identify and stop malicious activity from compromised systems/servers.
- Restrict traffic to the critical infrastructure from the allowed list of known-good destinations.
- Ensure you are inspecting all SSL traffic.
- Turn on Advanced Threat Protection to block all known command-and-control domains. This will provide additional protection in case the adversary exploits this vulnerability to implant malware.
- Extend command-and-control protection to all ports and protocols with the Advanced Cloud Firewall (Cloud IPS module), including emerging C2 destinations. Again, this will provide additional protection in case if the adversary exploits this vulnerability to implant malware.
- Use Advanced Cloud Sandbox to prevent unknown malware delivered as part of a second stage payload.
Zscaler Coverage:
Zscaler’s ThreatLabZ team has deployed protection as mentioned below:
Zscaler Advanced Threat Protection Signatures:
- WIN32.EXPLOIT.CVE-2023-34362
- APP.EXPLOIT.CVE-2023-34362
- HTML.EXPLOIT.CVE-2023-34362
Zscaler Private Access AppProtection:
- MOVEit Transfer moveitisapi SQL Injection (CVE-2023-34362): 6000662
Details related to the threat signatures released by Zscaler can be found in the Zscaler Threat Library.
Additional References:
- https://www.cisa.gov/news-events/alerts/2023/06/07/cisa-and-fbi-release-stopransomware-cl0p-ransomware-gang-exploits-moveit-vulnerability
- https://nvd.nist.gov/vuln/detail/CVE-2023-34362
- https://www.rapid7.com/blog/post/2023/06/01/rapid7-observed-exploitation-of-critical-moveit-transfer-vulnerability/
- https://www.techrepublic.com/article/zero-day-moveit-vulnerability/
- https://www.mandiant.com/resources/blog/zero-day-moveit-data-theft
Cet article a-t-il été utile ?
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.




