Test to see if you're vulnerable.
Java has a long history of 0-day vulnerabilities being actively exploited. Exploits are usually drive-by attacks: users get infected by navigating to hijacked websites where an invisible Java applet drops a malicious executable on the user's machine. The very popular, Blackhole exploit kit includes numerous Java exploits.
This vulnerability has been exploited very quickly on the Internet. Firefox reacted quickly by flagging all versions of Java as vulnerable plugins. This means Java is disabled by default on Firefox and users get warned if a page requires the use of Java. It would appear that the work they recently did on their Click to Play feature for vulnerable plugins has paid off. Apple took a similar approach by pushing out a new malware definition list that rather than blocking malware, as it generally does, simply disabled the Java Web Start browser plugin altogether.
Are you vulnerable?
The latest iteration of Java is version 1.7 revision 11. This is now the default version on Windows. Although Java 1.6 is not vulnerable to this latest threat, Java 1.6's end of life is February 2013, so you should not downgrade to that version.
One annoying fact with Java is that new versions are installed on top of each other. As such, you are likely to have multiple versions of Java installed on your system. Internet Explorer may not even be using the latest version of Java that you have installed.
We have therefore created a new page to list all of the versions of Java installed on your computer. You can test your browser here.
Disable Java
To be on the safe side, you can disable Java in your browser to prevent malicious applets from running.
Firefox
Go to Tools - Add-ons - Plugins
Look for Java Deployment Toolkit and/or Java Platform SE. Disable them all.
 |
| Java disabled in Firefox |
Chrome
Go to Wrench - Settings and Show advanced settings... - Privacy and Content settings - Plug-ins - Disable individual plug-ins... - Java - disable. It is quite difficult to find!
 |
| Java enabled in Chrome |
Internet Explorer
Go to Tools - Manage Add-ons. Disable Java(tm) Plug-in SSV Helper and Java(tm) Plug-in 2 SSV Helper.
 |
| Java disabled in Internet Explorer 9 |
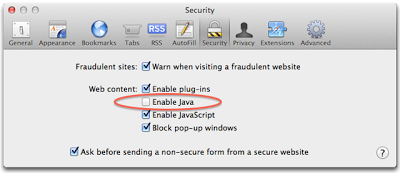
Safari
Go to Safari - Preferences
Look for Web Content: Enable Java and uncheck the option.
Test it
Now go to our Java test page to ensure that Java has indeed been disabled in your browser.
Click to Play
If you need Java occasionally, you can enable it on-demand with Click to Play. I described Click to Play, a way to manually enable plugins only on visible content, in a previous post. This feature is only available in Firefox, Chrome and Opera.
Firefox also offers several browser extensions to easily enable/disable java with one click. I personally like Quick Java.
Take this opportunity to check all the plugins running in your browser and disable the plugins that you do not really need. Don't give the bad guys an attack surface that's any larger than it needs to be!