Nintendo recently released Super Mario Run for the iOS platform. In no time, the game became a sensational hit on the iTunes store. However, there is not yet an Android version and there has been no official news on such a release. Attackers are taking advantage of the game's popularity, spreading malware posing as an Android version of Super Mario Run.
The ThreatLabZ team wrote about a similar scam that occurred during the release of another wildly popular Niantic game, Pokemon GO. Like that scam, the new Android Marcher Trojan is disguised as the Super Mario Run app and attempts to trick users with fake finance apps and a credit card page in an effort to capture banking details.
Marcher history
Marcher is a sophisticated banking malware strain that targets a wide variety of banking and financial apps and credit cards by presenting fake overlay pages. Once the user's mobile device has been infected, the malware waits for victims to open one of its targeted apps and then presents the fake overlay page asking for banking details. Unsuspecting victims will provide the details that will be harvested and sent out to to the malware's command and control (C&C) server. We have seen this malware evolve and take advantage of recent trends in order to target a large number of users. We have covered similar campaigns in the past related to Marcher malware here and here.
Technical details
In this new strain, the Marcher malware is disguised as the Super Mario Run app for Android. Knowing that Android users are eagerly awaiting this game, the malware will attempt to present a fake web page promoting its release.
Marcher malware details:
-
Name : Super Mario Run
-
Package Name : uiq.pizfbwzbvxmtkmtbhnijdsrhdixqwd
-
MD5 : d332560f1fc3e6dc58d94d6fa0dab748
-
Detections : 12/55(at time of analysis)
Upon installation, the malware asks for multiple permissions including administrative rights as shown below.
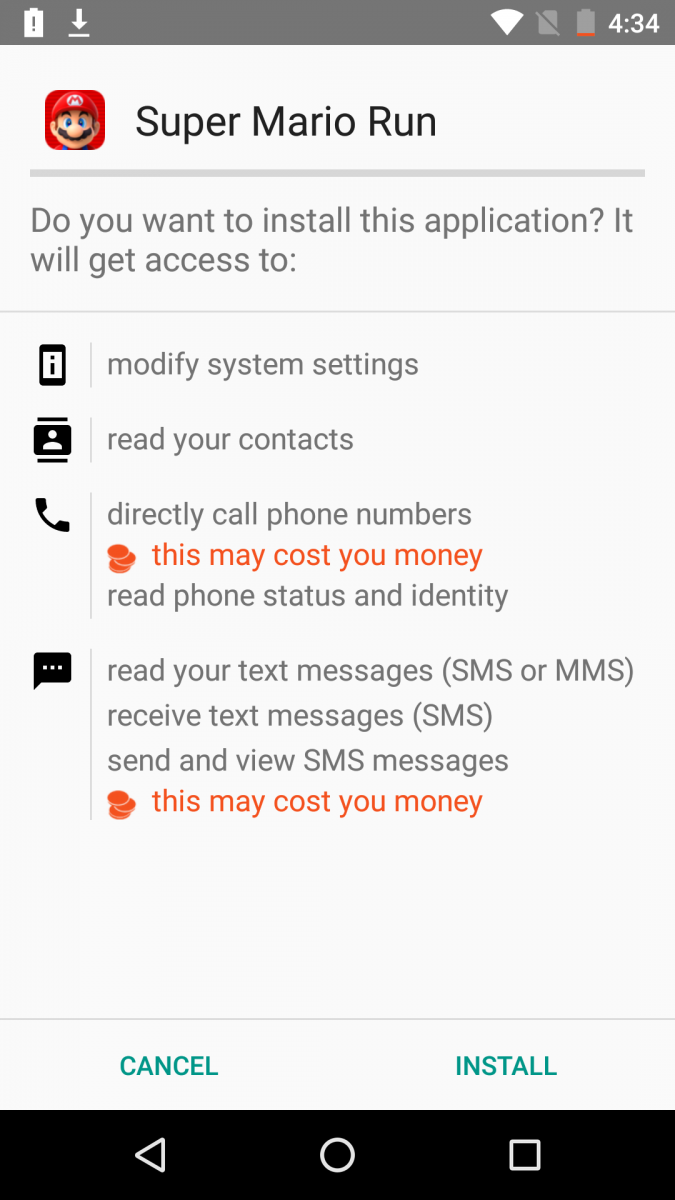

Fig. 1: Permissions
In previous variants of Marcher, we observed this malware family targeting well-known Australian, UK, and French banks. The current version is targeting account management apps as well as well-known banks. The following is a code snippet showing sample targeted apps:
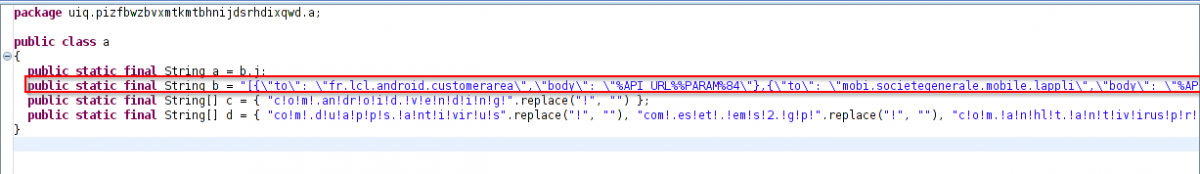
Fig. 2: Targeted apps
The following is the full list of targeted apps by this variant:
- fr.lcl.android.customerarea - https://play.google.com/store/apps/details?id=fr.lcl.android.customerarea
- mobi.societegenerale.mobile.lappli - https://play.google.com/store/apps/details?id=mobi.societegenerale.mobile.lappli
- com.cic_prod.bad - https://play.google.com/store/apps/details?id=com.cic_prod.bad
- net.bnpparibas.mescomptes - https://play.google.com/store/apps/details?id=net.bnpparibas.mescomptes
- com.rbs.mobile.android.ubr - https://play.google.com/store/apps/details?id=com.rbs.mobile.android.ubr
- com.grppl.android.shell.halifax - https://play.google.com/store/apps/details?id=com.grppl.android.shell.halifax
- com.fullsix.android.labanquepostale.accountaccess - https://play.google.com/store/apps/details?id=com.fullsix.android.labanquepostale.accountaccess
- com.barclays.android.barclaysmobilebanking - https://play.google.com/store/apps/details?id=com.barclays.android.barclaysmobilebanking
- com.caisseepargne.android.mobilebanking - https://play.google.com/store/apps/details?id=com.caisseepargne.android.mobilebanking
- com.rbs.mobile.android.rbs - https://play.google.com/store/apps/details?id=com.rbs.mobile.android.rbs
- fr.banquepopulaire.cyberplus - https://play.google.com/store/apps/details?id=fr.banquepopulaire.cyberplus
- com.htsu.hsbcpersonalbanking - https://play.google.com/store/apps/details?id=com.htsu.hsbcpersonalbanking
- fr.creditagricole.androidapp - https://play.google.com/store/apps/details?id=fr.creditagricole.androidapp
- uk.co.tsb.mobilebank - https://play.google.com/store/apps/details?id=uk.co.tsb.mobilebank
- com.grppl.android.shell.CMBlloydsTSB73 - https://play.google.com/store/apps/details?id=com.grppl.android.shell.CMBlloydsTSB73
- com.grppl.android.shell.BOS - https://play.google.com/store/apps/details?id=com.grppl.android.shell.BOS
- com.rbs.mobile.android.natwest - https://play.google.com/store/apps/details?id=com.rbs.mobile.android.natwest
- uk.co.santander.santanderUK - https://play.google.com/store/apps/details?id=uk.co.santander.santanderUK
Like previous Marcher variants, the current version also presents fake credit card pages once an infected victim opens the Google Play store. The malware locks out Google Play until the user supplies the credit card information as shown below:
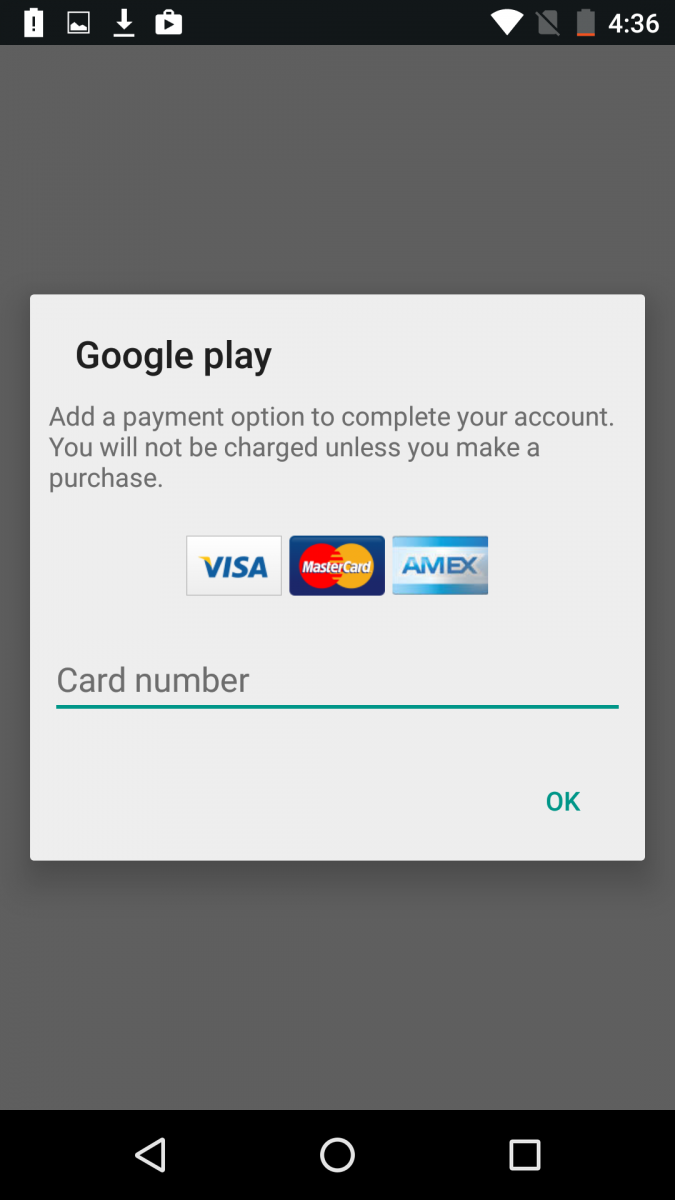
Fig. 3: Fake credit card page
However, the banking overlay pages served by the C&C were not functioning properly at the time of this writing. We suspect that the malware variant is still under development.

Fig. 4: Error page
In the current variant, we have observed a new obfuscation technique, in which all important string characters are delimited with '>' as shown below.
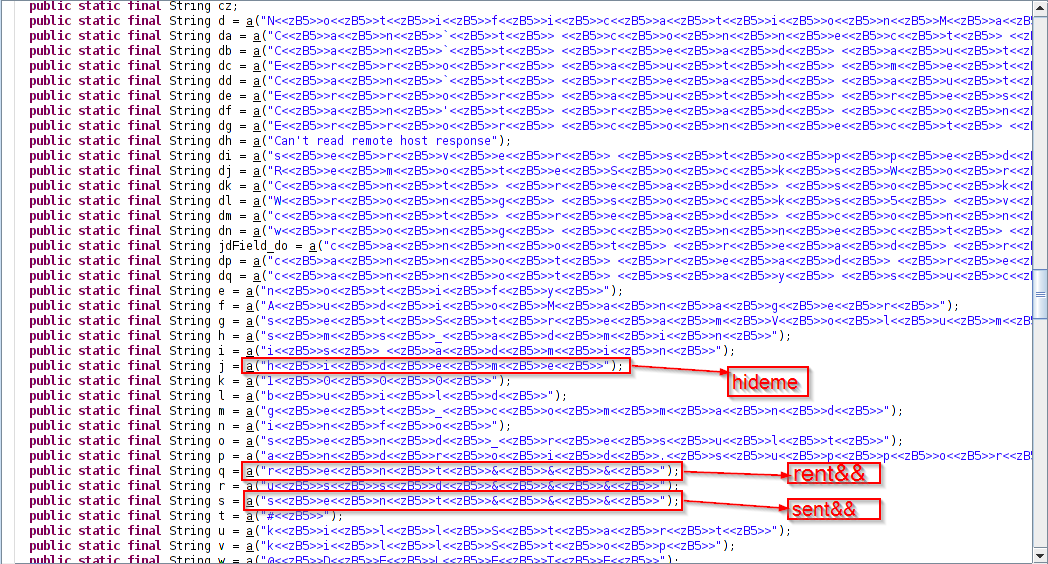
Fig. 5: Encoded strings
The code snippet below shows the hardcoded C&C location.
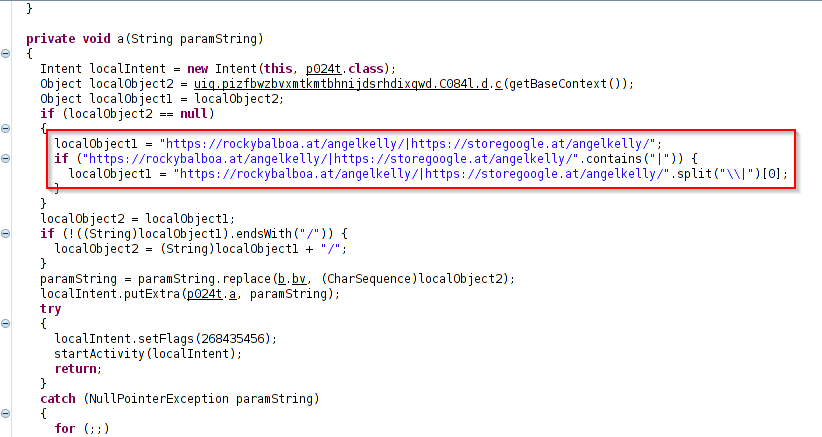
Fig. 6: C&C location
Conclusion
Android Marcher has been around since 2013 and continues to actively target mobile users' financial information. To avoid becoming a victim of such malware, it is a good practice to download apps only from trusted app stores such as Google Play. This practice can be enforced by unchecking the "Unknown Sources" option under the "Security" settings of your device.
Zscaler ThreatLabZ is actively monitoring this variant of the Android Marcher malware to ensure that Zscaler customers are protected.




