Introduction
Zscaler ThreatLabZ recently came across an attack chain in which cybersquatting was being used to deliver a commercial keylogger, called “AgentTesla,” with an intent to steal confidential information. The keylogger payload was configured to relay the stolen information back to the cyber-squatted domain, which had been registered two months prior to the attack.
The malicious domain in this case was “diodetechs[.]com” trying to imitate diodetech[.]com, which belongs to a legitimate consulting firm that offers a variety of services to global enterprises. We notified Diode technologies about the attack earlier this month and the offending domain has been suspended.
AgentTesla keylogger
AgentTesla is an advanced keylogger with features like clipboard logging, screen keylogging, screen capturing, and extracting stored passwords from different web browsers. It is written in .NET and supports all versions of the Windows operating system. In this blog, we will analyze the AgentTesla payload that was used in the attacks involving cyber-squatted domain ‘diodetechs[.]com’.
Figure 1: Subscription packages of AgentTesla keylogger
The Infection cycle
The infection cycle typically starts with a malicious office document that arrives as an e-mail attachment. The document uses the social engineering tactics covered here to lure the user into running the embedded macro, which will download and install the malware executable. The malware executable is the AgentTesla keylogger that was hosted at the following location:
- diodetechs[.]com/bless/cc.exe [cyber-squatted domain]
- MD5 - e4117e6974363cac8b37e5e3ff5d07a6
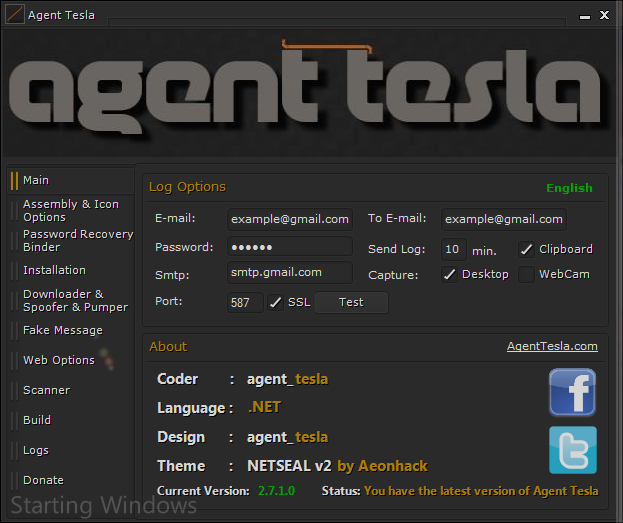
Figure 2: AgentTesla configuration panel
Installation
The AgentTesla payload gets downloaded and executed from location “%temp%\cc.exe”. It makes a copy of itself as “JavaUpdtr.exe” in the “%Application Data%\Java\” directory, pretending to be a Java updater. It also creates the following registry entry to remain persistent upon system reboot:
- HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run @ Java Updtr
The installer then starts a new process ‘MSBuild.exe’ in suspended mode, injects itself into this new process before resuming execution. This is where the keylogging, screen capturing, and other information collection modules are started. The author leveraged legitimate password recovery tools like IEPasswordDump and MailPassView to steal user credentials from Internet Explorer & Microsoft Outlook.
Figure 3: Embedded IEPasswordDump utility
The logged keystroke information is saved at “%temp%\log.tmp” in plain-text and the screenshots are saved in the folder “%appdata%\ScreenShot\.” The information collected from the victim’s machine is relayed to the remote C&C server every 20 minutes.
Bot configuration
The configuration file contains a full list of modules that were configured by the attacker. This version has multiple modules, including keylogging, screenshot capturing, password stealing, etc., enabled as shown below:
Figure 4: AgentTesla bot configuration
Module information
What follows is a brief overview of the modules that are supported by this payload.
USB Spreader – Capable of spreading through USB drives
Melt – Capable of uninstalling itself from the victim’s machine
Webcam – Capable of taking screenshots through the victim machine’s webcam
ScreenShot – Capable of taking screenshots capturing user activity
Keylogger – Capable of logging keystrokes from traditional as well as virtual keyboard; it can also log data from the clipboard
Password stealing – Capable of stealing stored password from various applications, like Chrome, Opera, Yandex, Firefox, IE, SeaMonkey, Comodo, Chromium, dyndns, Filezilla, FlashFXP, Outlook, Netscape, and others
Anti-Analysis – Capable of terminating multiple antivirus, security, and analysis programs running on the victim machine; it is also capable of detecting popular sandboxes and virtual environments
Additionally, AgentTesla is capable of disabling UAC, Taskmgr, CMD, Run, Control Panel, Regedit, SystemRestore, etc., on a victim’s machine.
Figure 5: AgentTesla disabling system features
Network activity
The payloads that we analyzed were all connecting to agenttesla[.]com upon successful installation to check for keylogger software update as seen below:
Figure 6: AgentTesla C&C activity
The malware then starts sending collected information and screenshots to the remote server.
Format of data it sends
- type={0}&hwid={1}&time={2}&pcname={3}&logdata={4}&screen={5}&ipadd={6}&wbscreen={7}&client={8}&link={9}&username={10}&password={11}&screen_name={12}&site_username={13}
|
Command |
Description |
|
webcam |
Send images collected via webcam to C&C server |
|
screenshots |
Send screenshots to C&C |
|
keylog |
Send keystroke logs to C&C |
|
update |
Update keylogger binary |
|
info |
Send victim’s machine information to C&C |
|
uninstall |
Uninstall binary |
|
passwords |
Send stolen password to C&C |
Conclusion
Our investigation of this attack chain started with the keylogger payload getting flagged in the cloud sandbox for an enterprise customer. Further analysis revealed usage of cybersquatting for delivering the malware executable. The malicious domain was registered on the same day that the malicious documents, which were claiming to be “Purchase Orders,” were modified for the attack.
Zscaler ThreatLabZ will continue to monitor and ensure coverage against these malware payloads.
Blog by: Abhaykant Yadav, Deepen Desai










