Leverage risk signals from Zscaler in Identity Threat Protection with Okta AI to detect and enable automated responses to risk events in real-time.
Over the last several years, organizations have become more effective at threat defense in certain areas. Endpoint detection and response (EDR) solutions are now more commonplace, which has led to a decrease in malware-based attacks – 71% of attacks are now malware-free. At the same time, Zero Trust adoption is on the rise. Zero Trust architecture hides exposed assets from the Internet and connects users directly to applications and resources they need access to based on policy. This architecture approach has made it difficult for attackers to find resources on the Internet to go after – the external attack surface has shrunk.
While these shifts have made security effective overall, it has had unintended consequences – attacks have become more targeted, breaches have become more expensive, and identity-based attacks have become the preferred method of compromise. Moreover, threats after initial access often evade defenses focused on malware and external attacks.
These threats warrant a holistic and collaborative approach to identity security that leverages high-fidelity identity risk signals, identity risk correlation, and automated countermeasures at the identity layer to respond to threats without impacting productivity and user experience.
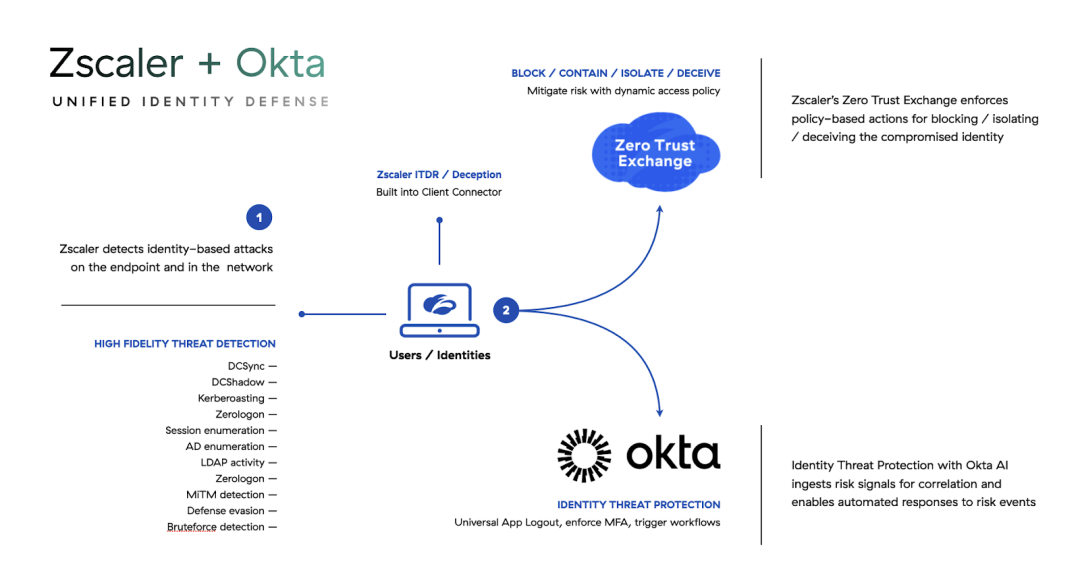
To address this new reality, Zscaler has partnered with Okta to stream Zscaler’s high-fidelity risk signals into Identity Threat Protection with Okta AI. This enables policy-based actions and workflow-driven responses in Okta for identity-related risk events in real-time, empowering organizations to configure countermeasures that can mitigate further risk.
Identity Threat Protection FROM OKTA
Identity Threat Protection provides continuous risk evaluation and enables automated responses throughout a user’s entire session. It analyzes identity signals and ingests third-party alerts from an organization’s security ecosystem in a vendor-neutral manner via the Shared Signals Framework (SSF) to constantly assess risk. This enables Identity Threat Protection to take instant actions like Universal Logout, revoking sessions that could be compromised by token theft and not visible to network security tools. It can also trigger adaptive workflows, such as altering a user’s application access or custom API actions, neutralizing threats across the identity lifecycle.
Zscaler + Okta – Closing the loop on identity attacks
Zscaler's Deception and Identity Threat Detection solutions have the ability to detect identity-based attacks with a high degree of certainty. Through this integration, Identity Threat Protection from Okta can ingest risk signals from Zscaler as a partner and take policy-based actions to contain the threat. Here are some examples of how this works.
Mitigating a DCSync attack by enforcing MFA and Universal Logout
DCSync is a popular and effective identity-based attack that enables Active Directory domain replication. The attack is possible because the domain replication permission is enabled for the identity in Active Directory.
In this scenario, Zscaler’s Identity Posture capability flags this user as a potential risk that would allow an attacker to run a DCSync attack if the identity is compromised. The Active Directory admin consumes this information and decides not to revoke the permission until they can gather enough information to determine that the change will not break anything.
To mitigate the risk of a possible DCSync attack while this information is gathered, the SOC team turns on the DCSync detector in Zscaler as a compensating control.
An attacker compromises this user and attempts to replicate the Active Directory domain that would allow them to escalate privileges and move laterally. Zscaler detects this attempt, the risk level changes to ‘High,’ pushing the alert to Identity Threat Protection where a policy has been configured to enforce MFA for this user and log them out of all active Okta sessions as well as supported applications.
Responding to defense evasion with Universal Logout
A second example is where an attacker on a compromised endpoint attempts to kill the EDR process to evade any detections. Zscaler Deception is running a decoy EDR process as a compensating control to detect such evasion techniques.
When the Kernel driver kills the decoy EDR process along with the real one, the identity’s risk level changes to ‘High’ and the alert is pushed to Identity Threat Protection where an Entity Risk Policy for Universal Logout is enforced for supported applications with functionality enabled. This immediately revokes the user’s Okta and application sessions, containing the threat from potentially stolen tokens invisible to network security tools.
Investigating a potential identity compromise by creating a ServiceNow ticket
A third example is where as part of endpoint defenses to detect early attempts at lateral movement, Zscaler Deception plants lures on endpoints as decoy files. These are hidden in file directories and therefore not easily discoverable but if someone goes looking, they will find them. Interaction with a decoy file is a high-confidence indicator of malicious intent – sufficient to warrant investigation but not enough to block the user or quarantine the endpoint.
If one of these files on an endpoint is opened, it generates an alert. This alert assigns the identity a ‘Low’ risk level (meaning it’s supposed to be investigated before an action can be taken), and pushes it to Identity Threat Protection. Based on the configuration, the user’s Okta session can be revoked, and a workflow can be triggered to create a ticket for this incident in ServiceNow and route it to the relevant team to investigate.
In summary
Zscaler and Identity Threat Protection provide a pragmatic and holistic approach to security against identity-based attacks that enhance existing defenses and allow real-time response to limit damage and mitigate risk.
Availability
The integration between Zscaler and Identity Threat Protection with Okta AI will be available in early access starting Q1 CY2024.
To learn more, visit Zscaler Deception, Zscaler ITDR, and Identity Threat Protection with Okta AI. Click here to learn more about the Zscaler and Okta partnership.




