Read more posts like this on Zscaler's CXO REvolutionaries.
L’utilisation de plus en plus répandue et intensive de la technologie dans presque tous les aspects de notre vie exige de toute urgence des solutions de sécurité qui assurent la protection de nos réseaux et de nos données. Si certaines sociétés suivent le rythme, beaucoup s’efforcent de mettre leurs infrastructures à niveau et peuvent passer à côté de failles importantes en matière de cybersécurité. La dernière vague d’attaques par ransomware contre de grandes entreprises aux moyens financiers importants et des organismes publics semble indiquer que personne n’est à l’abri.
And this is not the time to make an error. In 2020 alone, data breaches due to ransomware attacks had an average price tag of $4.4 million. This number does not include the impact of ransomware, destructive malware, or hijacked logins and identities. Firms scrambling to ward off attacks from tech-savvy and tactical hackers are driving a booming investment in cybersecurity consulting and solutions. The market is expected to reach $418 billion by 2028. The increase in cybersecurity spending is a reaction to the increase in cyberattacks. In the last year, 43% of businesses were targeted. And data isn’t the only thing on the line.
Comment a, selon vous, évolué la menace en ligne à l’encontre de votre entreprise ?
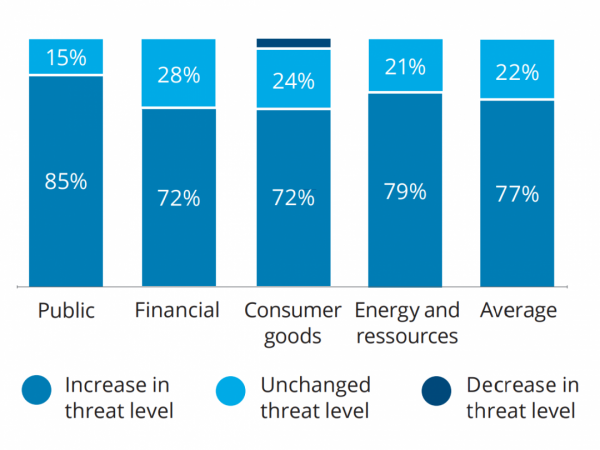 2020 Deloitte Cyber Survey: Cyber Security Leadership Chart
2020 Deloitte Cyber Survey: Cyber Security Leadership Chart
Quels sont les risques réels en matière de cybersécurité ?
The threat of data corruption and privacy infractions grows with each passing day. The increased reliance on remote and hybrid work only expedited the damage from security flaws previously exploited on cloud systems and open networks. Companies implementing 5G networks or leveraging the Internet of Things (IoT) approach stand to lose much if they succumb to a cyberattack.
But by no means should corporations halt progress due to security fears. And they aren’t: Nearly 80% of companies are rolling out new tech innovation without the means to secure it, and a system breach brings a breach of trust with customers and stakeholders. The result is almost always the same: business operations are disrupted, data is lost or stolen, and the bottom line suffers.
Qui est vraiment responsable des violations de la cybersécurité ?
L’époque où l’on confiait les problèmes techniques aux équipes informatiques est révolue. La technologie est au cœur de la plupart des entreprises modernes, et cette dépendance ne cesse de s’accentuer au fil du temps.
While we need knowledgeable IT teams in place to implement, monitor, and maintain these systems, the responsibility for their purchase and efficacy falls largely on management. This does not preclude publicly traded companies with a board of director oversight.
In fact, as was the case with Target and Equifax, leadership has had to take responsibility for data breaches and their repercussions. The Target legal settlement required an implementation of a security program, independent security assessment, AND executive responsibility moving forward.
While the Business Judgment Rule provides comprehensive protections, the courts have considered personal liability for improper security measures and the failure of board members or directors to take reasonable action and responsibility for the prevention of what are often considered preventable situations.
And the penalties can be steep and damaging. On top of data loss and a detrimental economic toll on the company, litigation and change management can be costly and time consuming. Cybersecurity regulators, such as the Office of the Comptroller on Currency, are also imposing fines on a massive financial scale for infractions.
Comment aborder la gouvernance de la cybersécurité
With risk management cascading from directors down to implementation teams, staying informed and being proactive is critical. But how can a board of directors, which is most likely not composed of cybersecurity experts, approach cybercrime risk mitigation from a leadership perspective? In one survey of enterprises, only slightly more than a third of respondents reported reviewing security concerns at least monthly.
À quelle fréquence la cybersécurité figure-t-elle à l’ordre du jour des dirigeants ?
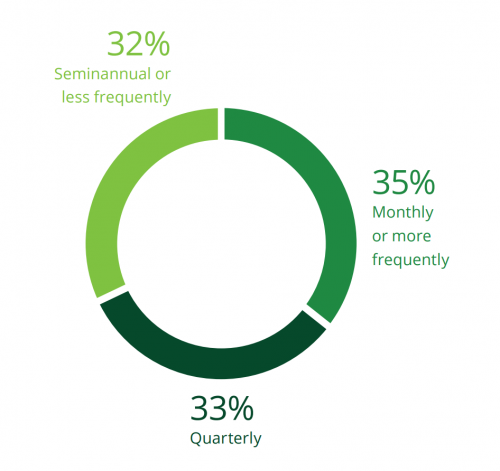 2020 Deloitte Cyber Survey: Cyber Security Leadership Chart
2020 Deloitte Cyber Survey: Cyber Security Leadership Chart
Proactive demonstration of due diligence is a great starting point. Tapping into experts and (somewhat ironically) technology solutions to fill knowledge gaps is another. PwC recommends that boards explore the benefits of NIST CSF to foster effective communication and processes among all stakeholders.
Here, we’ll explore a few ways directors can seek and achieve better cybersecurity governance for their organizations. The key is to approach this largely like other content areas where directors may not be specific thought leaders. Education, information, and dissemination can counter previously inadequate, hands-off, and even lackluster efforts.
Prenez connaissance de la situation dans son ensemble
Vous ne pouvez pas savoir ce que vous ne savez pas. Un conseil d’administration devrait commencer par examiner les rapports des responsables informatiques et des parties prenantes de l’entreprise. Faites appel à des experts et demandez une évaluation complète des failles connues ainsi que des changements en cours au sein de votre pile technologique.
You may need to design or implement additional reporting to ensure that your understanding is formed on a data- and fact-based level. From there, you can use the information to gain better knowledge of challenges, achievements, and recommended actions for improved cybersecurity policies moving forward.
Assignez un responsable de la supervision de la sécurité
Un membre du conseil d’administration (un membre seul ou un comité) doit être chargé de prendre connaissance des tenants et aboutissants des besoins et de l’état de la sécurité de la société. Ces personnes peuvent assurer des mises à jour permanentes et soumettre des questions plus importantes à l’évaluation et au vote de l’ensemble du conseil.
Committee members don’t have to be experts, but they can evolve into specialists. They can rely on internal specialists, third-party consultants, vendors, and technology solutions to plan ahead and better understand the landscape.
Tirez parti de mesures objectives
Risk assessment is an ongoing process with new vulnerabilities surfacing daily. Bringing in third parties to identify loopholes in security compliance through methods like ethical hacking can be quite insightful. Security consultants and supporting software applications can give great insight into the potential risks for your network.
Envisagez une mentalité zero trust (confiance zéro)
As the name implies, the zero trust model assumes that anything attempting to enter, leave, or relocate within a network cannot be trusted and should be verified or cleared by a governing system. This can give companies a significant advantage given the patchwork of on-premise and cloud solutions, proprietary and third-party applications, and closed networks and shared access.
Add remote work and innumerable devices to the mix, and the idea of trusting nothing can suddenly seem like the safest route. Companies can plug existing holes in their infrastructure and reduce long-term risk with this approach, and boards stand to learn much by researching this option.
Instaurez une culture de la transparence
While you certainly do not want to share details about any outstanding gaps in your cybersecurity protocols, transparency can still present benefits. In the event of a breach, disclose anything that should be declared to stakeholders and customers. This instills faith and trust that the board is doing everything in its power to address issues, protect data, and take ownership of any failings.
La voie à suivre est en constante mutation
Le conseil d’administration doit avant tout comprendre que la cybersécurité est une discipline dynamique qui exige une surveillance et une innovation permanentes. Il est indispensable de faire le nécessaire pour réduire les risques, tout en sachant que les risques seront toujours présents.
Les sociétés doivent également évaluer leurs polices d’assurance actuelles et déterminer si celles-ci couvrent de manière adéquate la valeur des actifs en cas de violation, et si une cyber-assurance dédiée peut contribuer à atténuer davantage les risques. Mais indépendamment de la taille de votre police d’assurance, les dirigeants doivent rester impliqués et formés en matière de cybersécurité appliquée à l’entreprise et élaborer des politiques et des procédures en cas de violation, dans un souci de responsabilité.






