While there is nothing new or Earth-shattering in this post, I thought I'd share what I have seen as the top abuses of open web proxies - as this is an everyday occurrence involving a large volume of web transactions and is a constant annoyance on the Internet.
An "open proxy" is...
 In other-words a server that anyone on the Internet can forward traffic through. There are various flavors of open proxies:
In other-words a server that anyone on the Internet can forward traffic through. There are various flavors of open proxies:
- Transparent open proxy - includes originating IP address within the headers or a cookie so the traffic can be traced back to the source (common in a caching proxy setup).
- Anonymous open proxy - mask/hide the originating IP address of the traffic. However, there is often a tag from the proxy identifying the proxy version, etc. so that the destination server could identify the traffic as being sent through a proxy.
- "Elite" open proxy - provides no indication to the destination server that the traffic has been forwarded. These are the most desirable form of proxies in the underground.
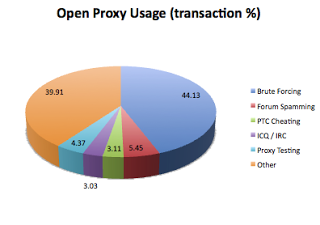
I've analyzed many thousands of transactions on a few "elite" open web proxies, to determine how they are being used (abused). This is the general breakdown of the percentage of the transactions that I analyzed (there were over a quarter of a million total that I reviewed).
 #1: Distributed Brute-Forcing:
#1: Distributed Brute-Forcing:
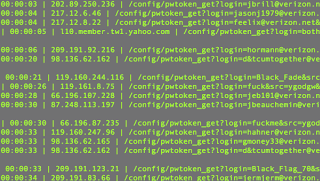
This is the repeated attempt at trying username / password combinations to gain unauthorized access to accounts. Within the abuse of open web proxies, I have seen repeated abuse of the proxies. For example, proxies are often used to brute-force Yahoo! and Rapidshare accounts. As these target sites identify the brute-forcing activity, they block the source IP address from further attempts - so the brute-force attempts are distributed among open proxies to mask and vary the source IP addresses of the attempts.
The Yahoo brute-force attempts primarily appear as HTTP GET requests taking a variety of forms:
- <yahoo>/config/login?login=<username>&passwd=<password>
- <yahoo>/config/pwtoken_get?login=<username>&src=<source>&passwd=<md5_password>&challenge=<challenge_response>&md5=1
- <yahoo>/client/?.intl=us&.src=knowsrch&.done=http://answers.yahoo.com&login=<username>&passwd=<password>
- <yahoo>/client/clogin?login=<username>&challenge=<challenge>&response=<response>
The Rapidshare brute-force attempts appear as HTTP GET requests taking the form:
- <rapidshare>/cgi-bin/rsapi.cgi?sub=getaccountdetails_v1&type=prem&login=<username>&password=<password>
- <rapidshare>/cgi-bin/premium.cgi&accountid=<id>&password=<password>&premiumlogin=1&logout=&fileid=fileid&fimename=filename&ru=<ru>
Note: For both Yahoo and Rapidshare IP addresses and domain names are rotated through. For example:
#2: Comment / Forum Spamming:
This is the mass-posting of "comments" onto blogs, forums, guestbooks, and other sites that allow open interaction with the sites. These comments include the "spam advertisement" variety ranging from porn, pharma, gambling, and pay-per-click affiliates. The other variety is the SEO variety in which the comments include links back to a page they are trying to increase search engine ranking for. Some SEO tools like XRumer include this functionality to include automatic registration and CAPTCHA bypass for posting to sites.
The comment spam HTTP GETs vary depending on the forum setup, but many followed the formats:
- <site_page>.php?act=post&do=new_post&f=<forum_id>
- <site_page>.php?do=newthread&f=<forum_id>
- <site_page>.php?mode=post&f=<forum_id>&sid=<session_id>
- <site_page>comment/reply/<story_id>
 Snippet of logs showing the forum spamming
Snippet of logs showing the forum spammingSample spam message:
WoW auction site:

#3 Pay-to-click (PTC) "Cheating"
PTC/PTP/PTR sites are: pay-to-click, pay-to-promote, pay-to read ads / fill out surveys. These sites are businesses with varying degrees of legitimacy - I doubt the site owners/members pay taxes, in some cases the site owners don't pay out their members, and in many cases the members try to "cheat" the sites using things like botnets or infected machines.
The business model is basic: web site owners and advertisers pay PTC sites to promote their site. In turn, PTC members receive a fraction of a cent for each click they generate to the advertised site. PTC members also receive commissions for referring new members to sign-up. As such, new members fall into a pyramid hierarchy in which a small percentage of their revenue is given to the referring user. PTC sites have varying degrees of memberships and also limit the number of times that a member can generate revenue from a participating site.
PTC members that try to cheat the system attempt to create as many referred users under them as possible to generate a commission, and from each newly created referrer, automatically click through the participating sites, generating a daily revenue stream something along the following lines:
Revenue = ((Commission * Referrer Accounts Created) + (Referrer Accounts Created * Clicks Allowed * Participating Sites * Fraction of a cent payout)) * Number of PTC sites a member of
PTC sites are aware of members attempting to cheat, so they look at things like the source IP of the transactions and identify and ban users when multiple accounts all come from the same IP address. PTC sites also try to identify if the transactions are being forwarded from a proxy - because of these checks, "elite" proxies unknown to the PTC sites are in high demand.
Here is an example of a PTC site that I saw being "cheated":
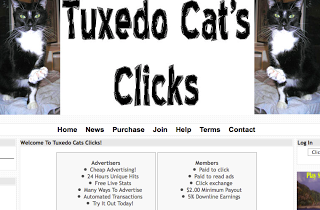 Note: there are many of these PTC sites, and they all look fairly similar to this setup.
Note: there are many of these PTC sites, and they all look fairly similar to this setup.
On the homepage of the site, top earners are displayed:
 The number 3 daily earner for this PTC site is "dominic1102" - looking at logs, I see this PTC member generating a large number of referrals to make commissions and increase their click volume. Example format:
The number 3 daily earner for this PTC site is "dominic1102" - looking at logs, I see this PTC member generating a large number of referrals to make commissions and increase their click volume. Example format:
www.tuxedocatsclicks.info/index.php?ref=dominic1102
The "dominic1102" handle and client IP (123.134.112.84) was used for a number of other PTC sites as well, e.g., www.lakotaptc.info/index.php?ref=dominic1102
#4 IRC / ICQ Masking
Users of chat networks frequently what to hide their source IP address. Whether the user is engaged in illegal activity (e.g., selling stolen credentials) or wanting to remain anonymous in case a flame war erupts followed by a denial of service attack.
# 5 Proxy Testing / Reveal host IP:
It appears that a portion of the traffic analyzed comes from automated checks to identify open proxies. Once connected, the proxy is tested to see which IP address is exposed on the Internet when traffic is forwarded through the proxy.
# 6 Other Browsing and Site Scraping
This includes a variety of things, ranging from general browsing, porn and other "not safe for work" (NSFW) surfing and regular page scraping. Based on the transaction timestamps in the logs, much of the porn surfing appeared to be automated scraping of pornographic images.