Thanksgiving is once again upon us, followed by "Black Friday," which typically means one of two things: you will either be spending time with family as you recover from a food hangover, or you will be fighting the crowds for deals at retail stores.
But wait! There is a way you can have your pumpkin pie and eat it too.
These days most shopping outlets promote their Black Friday/Cyber Monday deals on their websites in advance of the holiday; many offer great online deals and perks like free shipping to entice shoppers to avoid the crowds and shop online. But beware: malware authors anticipate the increase in online shopping and use the season to manipulate users to their own ends.
As shopping increases, so do risks
Today’s bad actors use a variety of methods to lure users into clicking malicious links or opening infected files. They use phishing to attempts to harvest credentialsor lead victims to less-than-reputable stores. They send opaquely named files and create websites designed to confuse recipients. They can even use your CPU resources when you visit their shop to mine Crypto Currency without consent. In this blog, we will describe in further detail how some of these techniques are being used, and how to avoid them.
When does it all start?
In the Zscaler cloud, we start to see an increase in shopping activity as early as November 1st. No sooner are we putting away our jack-o-lanterns than we start to look forward to the shopping season. It’s really no wonder that Starbucks starts its holiday music onslaught the day after Halloween.
Shoppers tend to do most of their holiday shopping over non-mobile PC devices. While it might be easier to navigate shopping sites on a big screen, PC users are at an added risk of phishing attacks. In Fig. 1, you can see that phishing attempts are high at the onset of the shopping season. Mobile users are actually less prone to phishing attacks, because they tend to use specific trusted apps rather than surfing the open internet. Fig. 2 shows us that there is a slight uptick in shopping activity on mobile devices while phishing attempts start to fall.
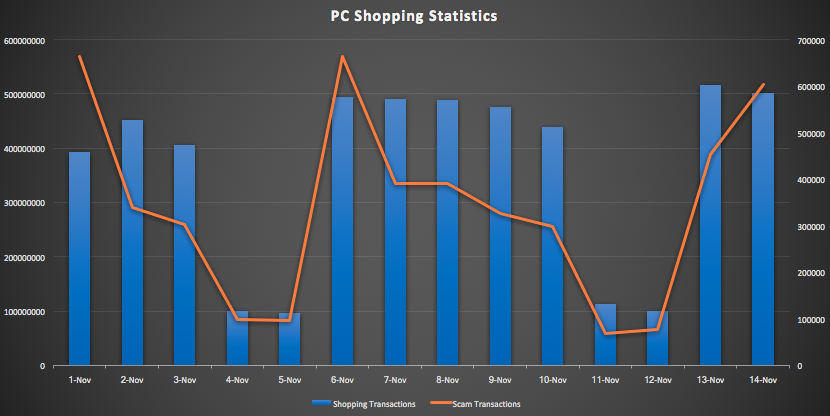
Fig 1: Shopping trends steadily rise closer to black Friday, and so do phishing attempts.
Fig 2: Mobile shopping trends steadily increase while scam attempts dwindle.
Domain Squatting
“Domain squatting” is the act of buying up domain names that are visually similar to the names of legitimate websites or companies, typically with the intent of defrauding users or convincing them that the content on the domain can be trusted. The multitude of new top-level domains (TLDs) that ICANN has made available has given criminals many opportunities to grab up domains that are identical or similar to real company websites, but with a different TLD suffix.
Especially relevant this season is the “.blackfriday” TLD. This domain is meant specifically for pages dealing with Black Friday sales, and is commonly used by various corporations to link to sales on their online stores or to Black Friday marketing content.
We have observed multiple instances of malicious actors domain squatting “.blackfriday” TLDs, such as these examples of domains that are visually similar to Google domains:
- gooogle[.]blackfriday
- guugle[.]blackfriday
Both of these domains were registered earlier this year, and have been seen serving various forms of malicious content. The first domain, “gooogle[.]blackfriday,” was used to deliver a Microsoft Outlook phishing page, as well as infect users with the Fareit Trojan. Fareit is a commodity infostealer that is typically used to harvest stored passwords and credentials from web browsers.
Fareit MD5: 76c016592f189d6de4166c5907f5063b
The second domain, “guugle[.]blackfriday,” was used as a command-and-control server for users infected with the commodity malware Loki. Loki is an infostealer that is capable of stealing stored passwords and cryptocurrency wallet information from a variety of applications. It is believed that this URL was spread through malicious email campaigns.
Loki MD5: ab8f64e3d30ab00518935c1e68617f73
The combination of a familiar-looking domain name with the “.blackfriday” TLD puts online shoppers especially at risk for accidentally visiting a malicious site while browsing for Black Friday deals and sales this season. Users should be careful to inspect the URLs they visit online to make sure they are legitimate, and to avoid clicking on links in emails from untrusted sources.
Crypto currency mining activity
Crypto currency mining has become a popular method of monetization, as reported in this blog. Instead of relying on advertising revenue, site owners will embed a script in their site that will leverage the user’s browser to begin mining crypto currency. This activity is very CPU intensive on victims’ systems and it’s done completely without their knowledge or consent. Furthermore, the only way to stop the activity from continuing after you leave the site is to completely shut down your browser.
The screen capture below shows the number of crypto currency mining attempts we’ve seen since the start of the shopping season (attempts were blocked before they could begin mining activity).
Fig 3: Shopping keywords seen in referer URL of Cyrpto currency mining attempts.
Fake Shops
Finding the best deals can be tricky, and the number of fake shops that seem to crop up around this time of year make things far more difficult. Performing a basic Google search can yield highly suspect shops touting themselves as offering legitimately good deals. The following result was found on the front page of a Google search for “Ray-Ban sunglasses.”
Fig 4: Top search—too good to be true
The above result is convincing; with its legitimate-sounding domain name, it could be a real outlet store offering great deals. But the Whois records tell a different tale.
- Domain Name: rayban-outlet.us
- Registrant Name: Jiang Yongxin
- Registrant Street: Shanghai 1
- Registrant City: Shanghai
- Registrant State/Province: Shanghai
- Registrant Country: CN
- Registrant Email: jyt.832104@gmail.com
Fig 5: Seemingly legitimate page
We checked the registrant email for the site, and the threat intelligence organization DomainTools shows 18 other websites created under the same email address. Running fraudulent stores is yet another way for threat actors to profit from unsuspecting users.
Phishing documents
Malicious documents sent via email are one of the most prevalent threats users face. Often, these documents are distributed in phishing campaigns, where the malicious actor pretends to be a legitimate source or company in an attempt to earn the victim’s trust (and to entice victims to open an attachment or click a link).
More sophisticated “spear-phishing” attacks target individual users or organizations by mimicking a source that is unique to them, such as their employer or business associates. The combination of these spear-phishing techniques with Black Friday branding, especially when linked with phrasing that would suggest sales, bargains, or contests, can significantly increase the likelihood that targeted users will fall victim to the malicious campaign.
Targeted phishing documents like the following are typical of these sorts of attacks. We came across the following malicious document in one of the major security feeds that we monitor where the filename used is “Black Friday Bonus Registration.docx,” suggesting the Black Friday theme as well as a potential reward to incentivize users into opening the document attachment.
Fig 6: Fake “Black Friday Bonus Registration.docx” document with embedded malicious application
The document, with carefully reproduced corporate branding, encourages the user to open an embedded application, which installs malicious software onto the victim’s computer.
Conclusion
The Zscaler ThreatLabZ team is working around the clock to ensure that our customers do not fall prey to the kinds of malicious activities we've described here. To protect yourself this year (and every year), we highly recommend that all online shoppers exercise extreme caution and follow our holiday season shopping security checklist:
- Inspect the source of emails with enticing shopping deals; be wary of any suspicious attachments
- Steer clear of unofficial mobile application stores
- Ensure HTTPS/secure connections to online retailers and banking sites
- Check the authenticity of the URL or website address before clicking on a link
- Stay away from emailed invoices, which is a social engineering technique often used by cyber criminals to download threats like Win32.Trojan.Emotet, reported in this blog
- Do not use unsecured public Wi-Fi for shopping
- Use two-factor authentication whenever possible, especially on sensitive accounts such as those used for banking
- Always ensure that your operating system and web browser are up to date and have the latest security patches installed
- Use browser add-ons like Adblock Plus to block popups and potential malvertisements
- Use browser add-ons like No Coin to block store attempts to use your computer for crypto currency mining
- Back up your documents and media files
- Review the Identity Theft Guide and FAQs from the Federal Trade Commission
Wishing you all a very happy, healthy, and safe Thanksgiving!





