Blog de Zscaler
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Suscríbase
WebSockets Unveiled: Powering Immersive and Interactive Web Experiences
WebSockets have transformed real-time communication on the web, breaking down the barriers of traditional one-way HTTP connections. WebSockets transform websites into dynamic, interactive experiences by establishing persistent, full-duplex channels that allow for seamless, bidirectional data exchange. WebSockets power some of today's most engaging web applications, including collaborative workspaces and immersive gaming platforms.
Bringing WebSockets to the forefront
To fully comprehend the significance of WebSockets, it is necessary to first understand the limitations of traditional HTTP-based communication mechanisms, as well as how WebSockets cleverly address these challenges.
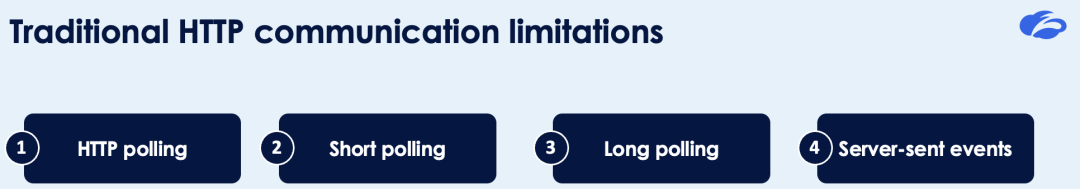
Traditional HTTP communication limitations
HTTP, the underlying protocol of the World Wide Web, has inherent limitations for real-time data exchange. Traditional methods, such as polling, long polling, and server-sent events (SSE), each have their own set of limitations.
- HTTP polling: The client sends repeated HTTP GET requests to the server to check for updates. This method, while simple, is inherently inefficient due to the overhead of creating a new connection for each individual request, resulting in an increase in network traffic and resource consumption on both the client and server sides.
- Short polling: This is similar to HTTP polling, but the server returns an empty response if no updates are available. Despite slight improvements, short polling remains inefficient due to the ongoing need for frequent requests and the associated overhead of establishing new connections.
- Long polling: Here, the server takes a more patient approach, keeping the connection open until an update arrives or a predefined timeout occurs. While long polling is undeniably more efficient than short polling, it can still cause noticeable delays due to timeouts and the constant overhead of maintaining connections.
- Server-sent events (SSE): With SSE, the server takes the initiative and sends updates to the client via a persistent connection. However, SSE has a fundamental limitation: it only allows one-way communication, from server to client.
Web Sockets: A Solution for Real-Time Communication
WebSockets rise to the occasion, expertly overcoming the limitations of traditional methods by establishing a bidirectional, persistent connection. This means that the client and server can exchange messages at any time, eliminating the need for repeated polling and significantly lowering overhead.
Key Advantages of WebSockets
- Low latency: Receive real-time updates with minimal delay, resulting in a smooth and responsive user experience.
- Reduced overhead: Because WebSocket connections are persistent, they eliminate the repetitive setup and teardown costs associated with traditional HTTP requests, resulting in more efficient resource utilization.
- Scalability: Web sockets' efficient use of resources enables applications to scale effectively, even with high user engagement and demanding real-time interactions.
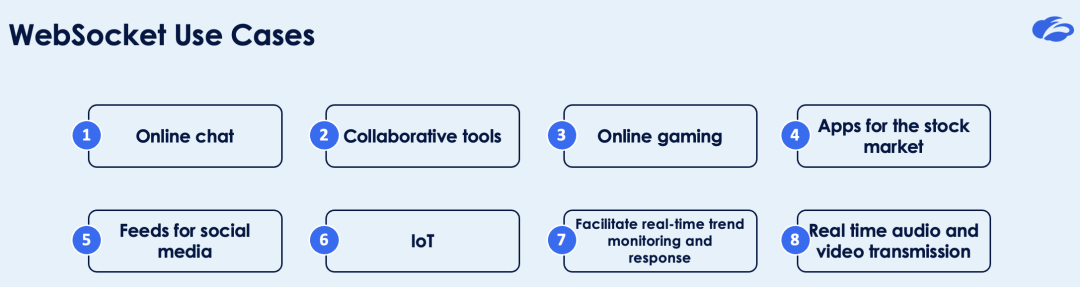
WebSocket Use Cases
WebSockets demonstrate their capabilities in a variety of applications that require real-time communication.
- Online chat: Allows users to communicate in real time without the need for page refreshes, resulting in seamless and dynamic conversations.
- Collaborative tools: Teams can work in harmony with the help of collaborative tools that allow for the real-time editing of documents, spreadsheets, or code.
- Online gaming: provide immersive and responsive experiences by updating the game state, player movements, and interactions in real-time.
- Apps for the stock market: Help traders stay up-to-date with the latest stock prices, market trends, and news stories so they can make informed decisions efficiently.
- Feeds for social media: instant alerts whenever there are new likes, comments, or posts, which keeps users interested and up-to-date.
- Internet of things (IoT): Make it possible for a wide variety of sensors and devices to transmit data in real time, opening the door to IoT applications such as smart homes and industrial automation.
- Facilitate real-time trend monitoring and response with real-time analytics by providing users with quick visualizations of data streams.
- Transmit audio and video in real-time; this technology is changing the way we watch and listen to shows, concerts, and other live events.
The WebSocket Handshake: Establishing a Connection
A crucial handshake takes place between the client and server before the real-time conversation starts. This carefully planned process sets up the WebSocket connection and sets the rules for how to talk to each other in the future.
How the WebSocket Handshake Works
HTTP upgrade request: The client starts the handshake by sending a specially crafted HTTP GET request to the server. This request contains the Upgrade header, which indicates the client's desire to elevate the connection to a WebSocket.
Example Request:
| GET /example HTTP/1.1 Host: example.com Upgrade: websocket Connection: Upgrade Sec-WebSocket-Key: ZsmgBhxYEJxnKDLlwfllSDhlIHNhbXBsZSB Origin: http://example.com |
- Server response: If the server accepts the upgrade, it returns an HTTP 101 Switching Protocols status code, indicating its readiness to transition to a WebSocket connection. To complete the handshake, the server also sends its own headers, which include ‘Upgrade’, ‘Connection’, and the critical ‘Sec-WebSocket-Accept’ header.
Example Response:
| HTTP/1.1 101 Switching Protocols Upgrade: websocket Connection: Upgrade Sec-WebSocket-Accept: mXCTYHGDGDGRYBF456ASCRTEYR3pPLMBiTxaQ= |
Decoding the WebSocket Headers
- Upgrade: Indicates that the connection is being upgraded to a WebSocket.
- Connection: indicates that the connection should be sustained and preserved.
- Sec-WebSocket-Key: The client creates a random base64-encoded key that adds an extra layer of security to the handshake.
- Sec-WebSocket-Accept: The server's response, which is also base64-encoded and based on the client's key, makes the handshake even safer.
- Sec-WebSocket-Protocol: Selects the specific subprotocol to be used for the connection, providing more control and customization options.
Breaking Down the Data Packets: How WebSocket Frames Work
Data exchange occurs through WebSocket frames once the connection is firmly established. In essence, these frames are small, independent data packets that travel between the server and the client.
Structure of WebSocket Frames
There is a header and a payload that make up each WebSocket frame. The payload stores the actual data that is being transmitted, while the header stores metadata that is crucial to the frame.
Key Components of a WebSocket Frame
- FIN (Final frame): A flag that lets you know if this is the last frame in a series of frames, which makes it easier to handle messages that are broken up.
- RSV1-3: Bits that have been set aside for possible future additions to the protocol.
- Opcode: A 4-bit field that tells you what kind of data is contained in the frame, like text, binary, or control frames like ping and pong.
- Mask: A single bit that tells you if the payload has been hidden to make it safer.
- Payload length: The amount of data in the payload that helps the receiver understand the message correctly.
- Masking key: When used with the mask bit, the masking key decodes the payload, protecting the data's integrity and stopping possible attacks.
- Payload data: This is the most important part of the frame; it holds the message data, which could be text, binary data, or control signals.
A Perfect Match: WebSockets and TCP
The transmission control protocol (TCP) is the strong base on which WebSockets are built. TCP provides a dependable, well-organized, and flow-controlled byte stream that makes sure data gets where it needs to go in the right order and without any errors.
How WebSockets and TCP Work Together
To make a persistent, full-duplex connection between the client and server, WebSockets basically use a TCP's features. TCP is responsible for the actual network communication, and WebSockets are the application-level protocols that make it possible to send and receive data in real time. The error recovery, flow control, and congestion avoidance mechanisms in TCP are very important for keeping the WebSocket connection stable and reliable.
How WebSockets Really Work
In order for WebSockets to work, a persistent TCP connection must be made between the client and server. Both parties will be able to send and receive messages wrapped in WebSocket frames once the connection is made.
The Fundamental Mechanisms of WebSocket Communication
- Ping/pong frames: These specialized control frames act as heartbeats, keeping the connection alive and responsive by periodically exchanging messages between the client and server.
- Close frames: When it is time to say goodbye, close frames enable a graceful termination of the WebSocket connection, allowing both client and server to end communication in a clean and orderly manner.
- Error handling: Robust error handling mechanisms are in place to deal with protocol errors and unexpected disconnections, increasing the resilience of WebSocket applications.
Understanding TCP Ports and the Reuse of Ports in Networking
- Common ports: WebSockets typically operate on TCP port 80 (the standard port for HTTP traffic) or port 443. This port selection enables WebSockets to integrate seamlessly into existing web infrastructure, reducing configuration complexity and potential conflicts.
- Port reuse: One notable feature of WebSockets is their ability to reuse TCP ports. This capability stems from their position as a layer above TCP, which allows multiple WebSocket connections to coexist peacefully on the same port. Port reuse helps to maximize resource utilization, especially when multiple WebSocket connections need to be established.
Web Proxies, Man-in-the-Middle Attacks (MITM), and WebSockets: The Dilemma of Encryption
Web proxies that can perform man-in-the-middle (MiTM) attacks are extremely useful tools for security practitioners, allowing them to intercept and analyze network traffic. These web proxies, however, face a formidable challenge when dealing with WebSocket traffic, especially when it is encrypted. This has significant implications for network security and SOC monitoring efforts.
The Challenge of Encryption
WebSockets, particularly when combined with TLS (WSS), provide end-to-end encryption. This means that the data sent between the client and the server is scrambled using cryptographic algorithms, making it indecipherable to any unauthorized party. Even if an MiTM proxy intercepts WebSocket traffic, it cannot decrypt the messages unless it has the necessary keys.
- Limited visibility: The inability to decrypt WebSocket traffic translates to proxies having a restricted view into the actual content of these communications. This hampers their ability to detect malicious activities, such as the undetected exfiltration of sensitive data or the discreet command-and-control (C2) communications that might be invisible within WebSocket messages.
- Filtering and blocking: Usually, proxies use deep packet inspection to filter and block certain types of traffic by looking at the content of traffic. However, because WebSockets is encrypted, this method does not work. This makes it hard to find and block malicious payloads or enforce content policies.
- Finding and stopping threats: When security systems that use traffic analysis cannot see WebSocket traffic, it can be harder for them to find and stop threats. This can create blind spots in the network security posture, potentially allowing malicious actors to exploit WebSockets for nefarious purposes.

Enabling Future-Ready Security, Visibility, and Control with Zscaler
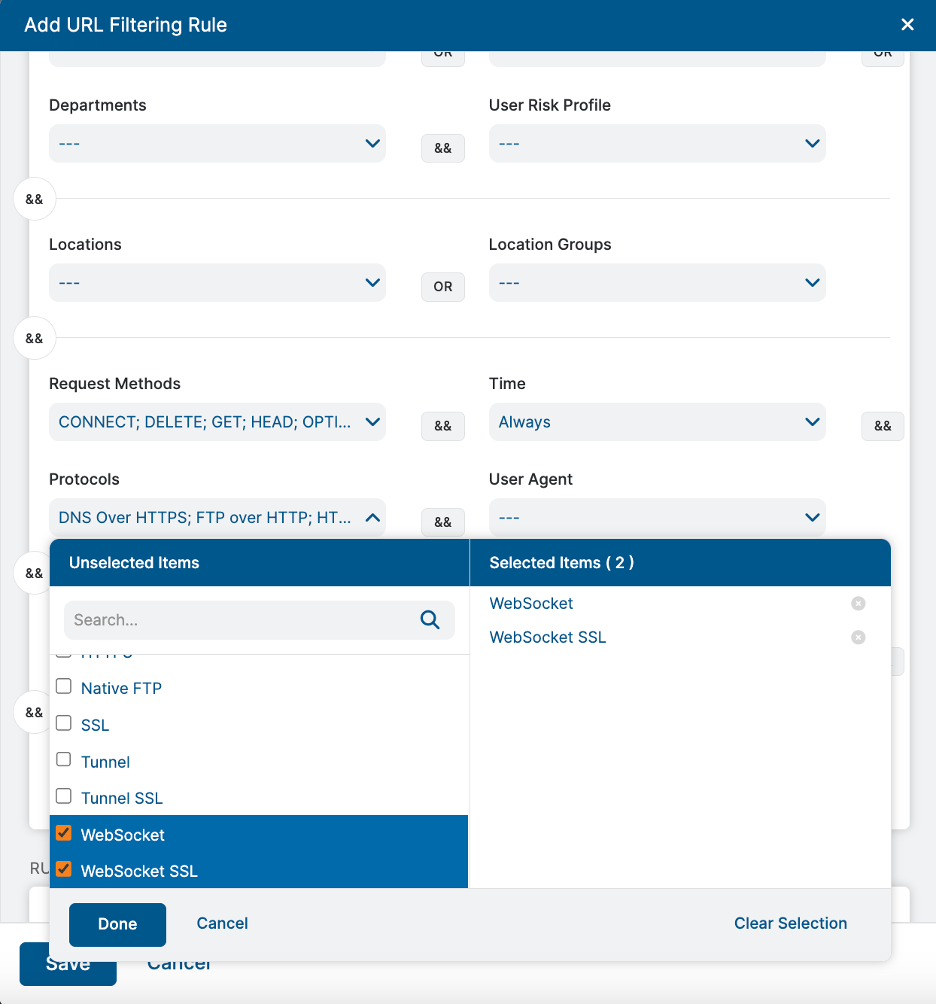
In the rapidly evolving realm of web technologies, it is essential to remain at the forefront of the industry. WebSockets, a protocol that facilitates real-time, bidirectional communication between web browsers and servers, has experienced a significant increase in popularity. Zscaler has proactively incorporated WebSocket support into its secure web gateway (SWG) and Cloud Firewall offerings, acknowledging this trend and its potential impact on network security.
- Accurate identification: Zscaler's Cloud Firewall and SWG now seamlessly identify WebSocket and WebSocket SSL traffic, thereby enabling unparalleled visibility into real-time web applications and services within your network.
- Granular access control: WebSocket identification is seamlessly integrated with Zscaler's existing granular access control policies, enabling administrators to enforce fine-grained security measures that are specifically designed for WebSocket traffic.
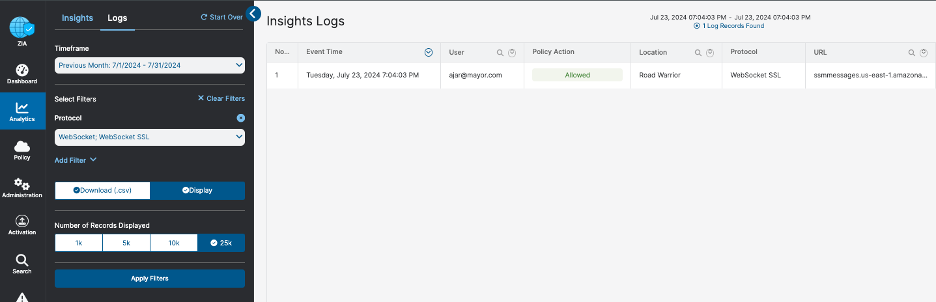
- Comprehensive logging and reporting: WebSocket transactions are meticulously logged and easily accessible for analysis within web insights or firewall insights, allowing for proactive threat detection and informed policy refinement.
- A look ahead: Zscaler is actively researching new techniques to improve its WebSocket capabilities even further. Stay tuned for advancements that will provide even more visibility into WebSocket transactions while protecting against data exfiltration and other emerging threats in real-time communication channels.
Benefits of WebSockets Identification
Simplified network monitoring and analysis is made possible by the easy identification and distinction of WebSocket-enabled traffic.
- Administrators can reduce risks related to real-time applications by precisely enforcing tailored access control policies that are exclusive to WebSocket traffic.
- WebSocket traffic is logged and reported in detail, allowing for in-depth analysis. facilitating the identification of potential security threats and anomalies.
- With Zscaler's unwavering dedication to WebSocket security, organizations can remain one step ahead of ever-changing threats and uphold a proactive security posture in the era of real-time web applications.
To Conclude
WebSockets are used in a lot of different areas to improve user experiences and allow for real-time interactions. They are used in smart chatbots, immersive online games, collaborative productivity tools, and advanced IoT platforms. Real-time communication on the web has changed a lot because of WebSockets. There are a lot of technical details about WebSockets that all of us need to know in order to get the most out of this technology. These include the handshake process, headers, frames, how they work with TCP, and how to get around proxy issues. With WebSockets, the future of web communication goes beyond real-time chat; it will be instant, immersive, and infinitely interactive.
Zscaler's addition of WebSocket support, combined with its commitment to continuous innovation, demonstrates its dedication to comprehensive network security in the age of real-time communication. By providing precise identification, granular control, in-depth analysis, and future-ready security measures for WebSocket traffic, Zscaler enables organizations to reap the benefits of real-time technologies while confidently mitigating potential risks.
¿Este post ha sido útil?
Reciba en su bandeja de entrada las últimas actualizaciones del blog de Zscaler
Al enviar el formulario, acepta nuestra política de privacidad.




