Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
New ThreatLabz Report: Mobile remains a top threat vector with 111% spyware growth while IoT attacks rise 45%
The role of the CISO continues to expand, driven by the rising number of breaches and cyberattacks like ransomware, as well as SEC requirements for public organizations to disclose material breaches.
Among the fastest-moving frontiers in enterprise cybersecurity: mobile, the internet of things (IoT), and operational technology (OT) systems. Today, 96.5% of people access the internet with a mobile device, while 59% of internet traffic is generated by mobile devices. Meanwhile, OT and cyber-physical systems, once air-gapped and isolated from the internet, have rapidly become integrated into enterprise networks, where threats can proliferate.
To shed light on this burgeoning threat landscape, the Zscaler ThreatLabz research team conducted a detailed analysis of mobile and IoT/OT attack trends from June 2023 to May 2024.
Overall, ThreatLabz tracked a rise in financially motivated mobile attacks—with 111% growth in spyware and 29% growth in banking malware—most of which can bypass multifactor authentication (MFA). Meanwhile, IoT attacks grew 45% year-over-year, and ThreatLabz identified pervasive security risks in OT environments.
This blog post will summarize key findings from the report. For a comprehensive understanding of mobile and IoT/OT trends, case studies, and best practices to secure your organization, download the Zscaler ThreatLabz 2024 Mobile, IoT, and OT Threat Report.
6 key mobile and IoT/OT findings
Top Mobile and IoT/OT trends
1. Rise in financially-motivated mobile threats, including a 111% rise in spyware and 29% growth in banking malware.
- Despite an overall decrease in Android attacks, financially-motivated mobile threats are growing, with the majority able to bypass MFA.
2. IoT attacks increased by 45% based on blocked attempts in the Zscaler cloud compared to our 2023 report.
- Zscaler blocked 45% more IoT malware transactions than the previous year. ThreatLabz also observed a 12% rise in the number of attempts to deliver malware (payload deliveries) to IoT devices.
3. ThreatLabz discovered 200+ fake apps discovered on the Google Play Store.
- This includes Anatsa, a known Android banking malware that uses PDF and QR code readers to distribute malware, which has targeted more than 650 financial institutions.
4. Legacy and end-of-life operating systems (OS) leave OT systems vulnerable.
- Once air-gapped and isolated from the internet, OT and cyber-physical systems have rapidly become integrated into enterprise networks, enabling threats to proliferate.
- ThreatLabz found that 50% or more of OT systems use end-of-life OS, many with known vulnerabilities, in an analysis of large-scale OT deployments. Meanwhile, risky protocols and services in east-west OT traffic abound.
Top mobile and IoT/OT targets
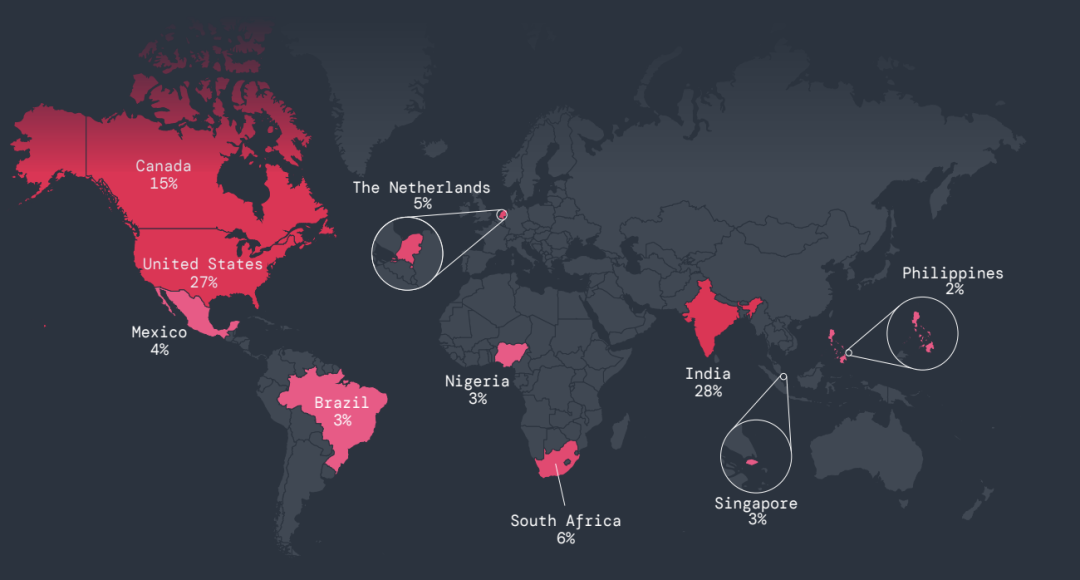
5. India was the top target for mobile attacks, experiencing 28% of all attacks, followed by the US, Canada, South Africa, and the Netherlands. Meanwhile, the United States remains the top target of IoT attacks, experiencing 81% of overall attacks, followed by Singapore, the UK, Germany, and Canada.
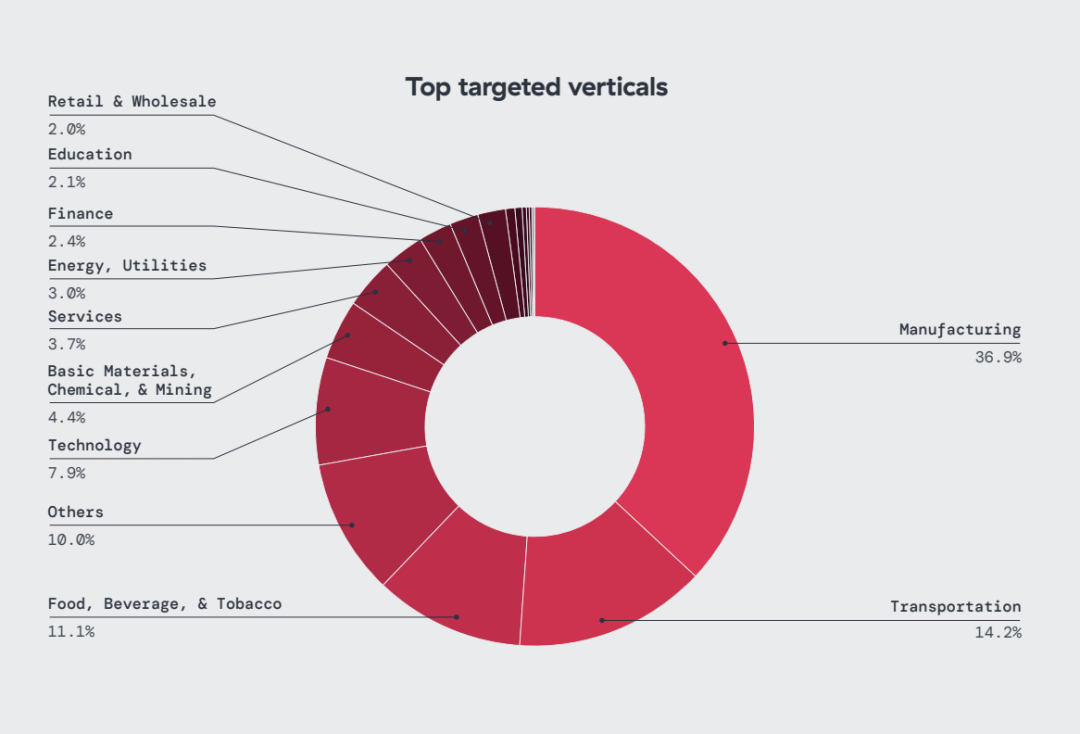
6. Manufacturing experienced the highest volume of IoT attacks, accounting for 36% of all IoT malware blocks observed, followed by transportation (14%) and food, beverage & tobacco (11%). Meanwhile, the technology and education sectors were most targeted by mobile threats.
Securing mobile, IoT, and OT with zero trust
As cyberattacks that target mobile and IoT/OT assets become more sophisticated, enterprises need a way to reduce cyber risk while, at the same time, embracing IoT and OT connectivity to drive business. Indeed, not only are IoT attacks growing, but threat actors are actively targeting OT devices and critical infrastructure, about which CISA has warned. Meanwhile, enterprises need a way to robustly secure mobile connectivity to any SaaS or private application, whether in the cloud or in the data center. To protect these devices and systems, enterprises should adopt a zero trust approach that mitigates cyberthreats and improves their security posture:
- Discover, classify, and inventory IoT and OT assets: Work to gain full visibility into your IoT and OT attack surface; this includes discovering, classifying, and inventorying both managed and unmanaged or “shadow” devices. With this kind of holistic view, defenders can prioritize their efforts, identify key vulnerabilities, and develop a proactive approach to securing these assets.
- Enable zero trust connectivity: Leverage a robust zero trust architecture that enables adaptive access decisions based on the real-time security and posture of user devices, risk factors, and device telemetry, ensuring secure direct connectivity between endpoints and applications—never to the underlying network.
- Enforce zero trust device segmentation: Apply least-privileged access controls for device-to-application, user-to-application, and application-to-application segmentation. This granular level of segmentation eliminates lateral movement, minimizes data exposure, and strengthens your overall security posture by reducing the potential for a single compromised device to jeopardize the entire network. This should include isolating and fully segmenting agentless IoT/OT devices into a secure “network of one”, including legacy servers and headless machines.
- Maintain consistent zero trust security policies: Ensure that zero trust access policies are consistently enforced across all environments, whether users are at headquarters, brand locations, or accessing applications remotely.
Get your copy of the Zscaler ThreatLabz 2024 Mobile, IoT, and OT Threat Report today. As mobile and IoT/OT threats proliferate, it’s critial to understand the latest trends, the implications of these kinds of attacks, and the best-practice strategies you can adopt to secure your organization against a full range of threats.
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



