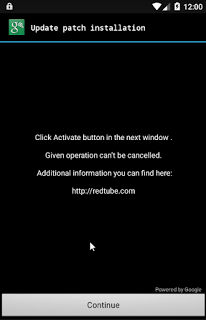
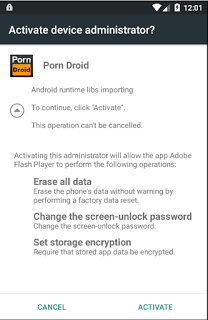
Recently, we came across a new variant of Porn Droid - an Android ransomware variant claiming to be from the FBI, which accuses people of watching child porn and then demands a fine of USD 500.
File information:
- Dropped URL : hxxp://sbqujqosyw[.]offer-mobi.com/mmesuofyqq1/pornvideo[.]apk
- MD5 : 857b887982f11493b4a1db953161e627
- Virustotal Detection : 5/56
After clicking "Continue", the malware asks for administrator access to the device requesting permissions such as "Erase all data", "Set storage encryption", "Change the screen-unlock password" as shown in screenshot below.
Once the user clicks on the "ACTIVATE" button, the malware gets administrator control of the device and locks it while displaying a fake FBI warning as seen below. It locks the user's phone by disabling keyguard and sets top priority for the malware application which ensures that no other application or user activity can override the malware application's activity.
 |
| FBI warning message |
 |
| FBI warning - Payment tab |
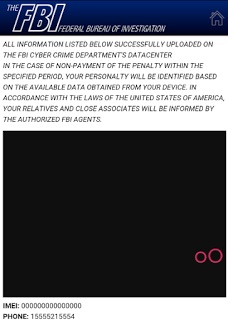 |
| FBI warning screen with user information |
The FBI warning screen also contains dynamic information relevant to the infected device such as the browser history, IMEI number, phone number and victim's picture, which has been taken by the malicious app. This is done to intimidate the end user as a warning message suggests that the information will be used by the FBI to identify the user if the fine is not paid.
Porn Droid Static Analysis
The screenshot below shows the malicious app accessing the browser history and bookmarks to display on the ransom screen.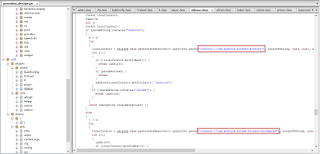 |
| Browser history |
It then appends the hard coded fake FBI warning message asking for ransom.
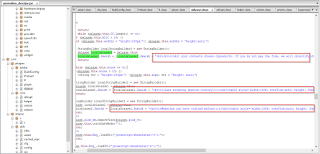 |
| Ransom screen text code |
The code below shows the malware author's attempt to evade string pattern matching based antivirus (AV) heuristic detection by leveraging a string concatenate function. This is one of the reasons why this sample has a very low (5/56) AV detection rate at the time of our analysis.
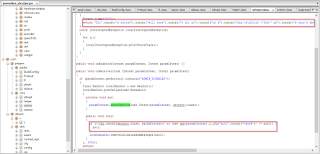 |
| "concate" usage to evade AV detection |
Another unique functionality that we observed in this mobile ransomware, that we more commonly see in PC malware, involves checking for the presence of installed AV applications such as ESET, Avast and DrWeb. It then attempts to terminate any AV applications identified.
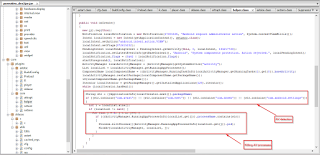 |
| AV Application check & terminate |
In order to stay active on the screen and lock out the phone, it disables the keyguard so the user cannot exit the application.
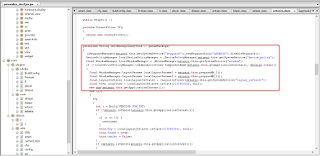 |
| Disable keyguard |
- destroy - wipe all user data
- unlock - deactivate the Admin access and unlock the device
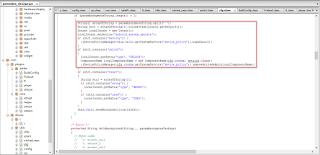 |
| Commands |
The app is also capable of taking pictures using the front facing camera that it can then display on the ransom screen:
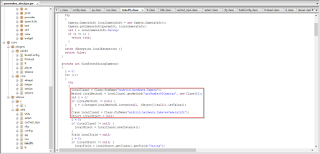 |
| Front facing camera picture |
The malware's Command & Control (C&C) server information is hardcoded in the configuration class as seen below.
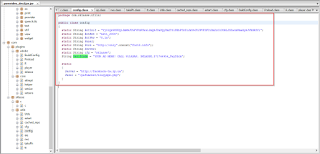 |
| Bot configuration |
C&C message parameters
- Server : facebook-tw.zp.ua
- URI: "/pafumokat/bloqyxpn.php"
- paramString1 : random number in the range of 1 to 3
- paramString2 : String made of BotID, network, location, phone number, bot version, SDK.
- paramString3 : "Protection"
- paramStrong4 : "Bot"
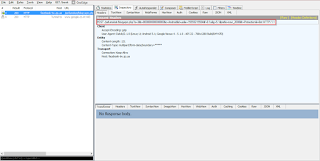 |
| C&C request |
The best way to avoid such malware is to stick with installing Android apps only from 'official' app stores such as Google Play or the Amazon Appstore.